GATE 2014 SET-2 CS Computer Science and information technology
[Q1 – Q25 carry ONE mark each ]
| Q1➡ | Engineering Mathematics The security system at an IT office is composed of 10 computers of which exactly four are working. To check whether the system is functional, the officials inspect four of the computers picked at random (without replacement). The system is deemed functional if at least three of the four computers inspected are working. Let the probability that the system is deemed functional be denoted by p. Then 100p =__________. |
Show Answer With Best Explanation
Answer: 11.85 to 11.95
Explanation: Upload Soon
| More Discussion | Explanation On YouTube | Probability | Help-Line |
| Q2➡ | Engineering Mathematics Each of the nine words in the sentence “The quick brown fox jumps over the lazy dog” is written on a separate piece of paper. These nine pieces of paper are kept in a box. One of the pieces is drawn at random from the box. The expected length of the word drawn is _____________. (The answer should be rounded to one decimal place.) |
Show Answer With Best Explanation
Answer: 3.8 to 3.9
Explanation: Upload Soon
| More Discussion | Explanation On YouTube | Probabbility | Help-Line |
| Q3➡ | Engineering Mathematics The maximum number of edges in a bipartite graph on 12 vertices is_____. |
Show Answer With Best Explanation
Answer: 36
Explanation: Upload Soon
| More Discussion | Explanation On YouTube | Graph-Theory | Help-Line |
| Q4➡ | Engineering Mathematics If the matrix A is such that then the determinant of A is equal to . |
Show Answer With Best Explanation
Answer: 0
Explanation: Upload Soon
| More Discussion | Explanation On YouTube | Linear-Algebra | Help-Line |
| Q5➡ | Engineering Mathematics A non-zero polynomial ƒ(x) of degree 3 has roots at x = 1, x = 2 and x = 3. Which one of the following must be TRUE? |
| i ➥ ƒ(0)ƒ(4) < 0 |
| ii ➥ ƒ(0)ƒ(4) > 0 |
| iii ➥ ƒ(0) + ƒ(4) > 0 |
| iv ➥ ƒ(0) + ƒ(4) < 0 |
Show Answer With Best Explanation
Answer: I
Explanation: Upload Soon
| More Discussion | Explanation On YouTube | Calculus | Help-Line |
| Q6➡ | Digital Logic Design The dual of a Boolean function F(x1, x2,…, xn, +, ∙ , ′ ), written as FD, is the same expression as that of F with + and ⋅ swapped. F is said to be self-dual if F = FD. The number of self-dual functions with n Boolean variables is |
| i ➥ 2n |
| ii ➥ 2n–1 |
| iii ➥ 22^n |
| iv ➥ 22^n—1 |
Show Answer With Best Explanation
Answer: IV
Explanation: Upload Soon
| More Discussion | Explanation On YouTube | Boolean Algebra | Help-Line |
| Q7➡ | Digital Logic Design Let k = 2n. A circuit is built by giving the output of an n-bit binary counter as input to an n-to-2n bit decoder. This circuit is equivalent to a |
| i ➥ k-bit binary up counter. |
| ii ➥ k-bit binary down counter. |
| iii ➥ k-bit ring counter. |
| iv ➥ k-bit Johnson counter. |
Show Answer With Best Explanation
Answer: 612 to 613
Explanation: Upload Soon
| More Discussion | Explanation On YouTube | Sequential Circuits | Help-Line |
| Q8➡ | Digital Logic Design Consider the equation (123)5 = (x8)y with x and y as unknown. The number of possible solutions is_______. |
Show Answer With Best Explanation
Answer: 3
Explanation: Upload Soon
| More Discussion | Explanation On YouTube | Number Systems | Help-Line |
| Q9➡ | Computer Organization A 4-way set-associative cache memory unit with a capacity of 16 KB is built using a block size of 8 words. The word length is 32 bits. The size of the physical address space is 4 GB. The number of bits for the TAG field is |
Show Answer With Best Explanation
Answer: 20
Explanation: Upload Soon
| More Discussion | Explanation On YouTube | cache memory | Help-Line |
| Q10➡ | Programming in C Consider the function func shown below: 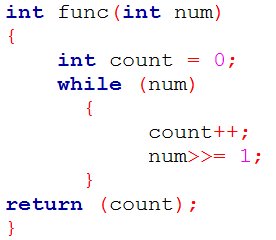 The value returned by func(435)is______. |
Show Answer With Best Explanation
Answer: 9
Explanation: Upload Soon
| More Discussion | Explanation On YouTube | Programming in C | Help-Line |
| Q11➡ | Programming in C Suppose n and p are unsigned int variables in a C program. We wish to set p to nC3. If n is large, which one of the following statements is most likely to set p correctly? |
| i ➥ p = n * (n-1) * (n-2) / 6; |
| ii ➥ p= n * (n-1) / 2 * (n-2) / 3; |
| iii ➥ p = n * (n-1) / 3 * (n-2) / 2; |
| iv ➥ p = n * (n-1) * (n-2) / 6.0; |
Show Answer With Best Explanation
Answer: II
Explanation: Upload Soon
| More Discussion | Explanation On YouTube | Programming | Help-Line |
| Q12➡ | Data Structure A priority queue is implemented as a Max-Heap. Initially, it has 5 elements. The level-order traversal of the heap is: 10, 8, 5, 3, 2. Two new elements 1 and 7 are inserted into the heap in that order. The level-order traversal of the heap after the insertion of the elements is: |
| i ➥ 10, 8, 7, 3, 2, 1, 5 |
| ii ➥ 10, 8, 7, 2, 3, 1, 5 |
| iii ➥ 10, 8, 7, 1, 2, 3, 5 |
| iv ➥ 10, 8, 7, 5, 3, 2, 1 |
Show Answer With Best Explanation
Answer: I
Explanation: Upload Soon
| More Discussion | Explanation On YouTube | Max-Heap | Help-Line |
| Q13➡ | Algorithms Which one of the following correctly determines the solution of the recurrence relation with T(1) = 1? |
| i ➥ Θ(n) |
| ii ➥ Θ(n log n) |
| iii ➥ Θ(n2) |
| iv ➥ Θ(log n) |
Show Answer With Best Explanation
Answer: I
Explanation: Upload Soon
| More Discussion | Explanation On YouTube | recurrence relation | Help-Line |
| Q14➡ | Engineering Mathematics Consider the tree arcs of a BFS traversal from a source node W in an unweighted, connected, undirected graph. The tree T formed by the tree arcs is a data structure for computing |
| i ➥ the shortest path between every pair of vertices. |
| ii ➥ the shortest path from W to every vertex in the graph. |
| iii ➥ the shortest paths from W to only those nodes that are leaves of T |
| iv ➥ the longest path in the graph. |
Show Answer With Best Explanation
Answer: II
Explanation: Upload Soon
| More Discussion | Explanation On YouTube | graph | Help-Line |
| Q15➡ | Theory of Computation If L1 = {an| n ≥ 0} and L2= {bn| n ≥ 0}, consider (I) L1.L2 is a regular language (II) L1.L2 = {anbn|n ≥ 0} Which one of the following is CORRECT? |
| i ➥ Only (I) |
| ii ➥ Only (II) |
| iii ➥ Both (I) and (II) |
| iv ➥ Neither (I) nor (II) |
Show Answer With Best Explanation
Answer: I
Explanation: Upload Soon
| More Discussion | Explanation On YouTube | Regular Languages | Help-Line |
| Q16➡ | Theory of Computation Let A ≤N B denotes that language A is mapping reducible (also known as many-to-one reducible) to language B. Which one of the following is FALSE? |
| i ➥ If A ≤N B and B is recursive then A is recursive. |
| ii ➥ If A ≤N B and A is undecidable then B is undecidable. |
| iii ➥ If A ≤N B and B is recursively enumerable then A is recursively enumerable. |
| iv ➥ If A ≤N B and B is not recursively enumerable then A is not recursively enumerable |
Show Answer With Best Explanation
Answer: IV
Explanation: Upload Soon
| More Discussion | Explanation On YouTube | Reducible | Help-Line |
| Q17➡ | Compiler Design Consider the grammar defined by the following production rules, with two operators ∗ and + S ⟶ T ∗ P T ⟶ U | T ∗ U P ⟶ Q + P | Q Q ⟶ Id U ⟶ Id Which one of the following is TRUE? |
| i ➥ + is left associative, while ∗ is right associative |
| ii ➥ + is right associative, while ∗ is left associative |
| iii ➥ Both + and ∗ are right associative |
| iv ➥ Both + and ∗ are left associative |
Show Answer With Best Explanation
Answer: II
Explanation: Upload Soon
| More Discussion | Explanation On YouTube | Precedence And Associativity | Help-Line |
| Q18➡ | Compiler Design Which one of the following is NOT performed during compilation? |
| i ➥ Dynamic memory allocation |
| ii ➥ Type checking |
| iii ➥ Symbol table management |
| iv ➥ Inline expansion |
Show Answer With Best Explanation
Answer: I
Explanation: Upload Soon
| More Discussion | Explanation On YouTube | compile time | Help-Line |
| Q19➡ | Software Engineering Which one of the following is TRUE? |
| i ➥ The requirements document also describes how the requirements that are listed in the document are implemented efficiently. |
| ii ➥ Consistency and completeness of functional requirements are always achieved in practice. |
| iii ➥ Prototyping is a method of requirements validation. |
| iv ➥ Requirements review is carried out to find the errors in system design. |
Show Answer With Best Explanation
Answer: III
Explanation: Upload Soon
| More Discussion | Explanation On YouTube | Models | Help-Line |
| Q20➡ | Operating System A FAT (file allocation table) based file system is being used and the total overhead of each entry in the FAT is 4 bytes in size. Given a 100 x 106 bytes disk on which the file system is stored and data block size is 103 bytes, the maximum size of a file that can be stored on this disk in units of 106 bytes is . |
Show Answer With Best Explanation
Answer: 99.55 To 99.65
Explanation: Upload Soon
| More Discussion | Explanation On YouTube | file system | Help-Line |
| Q21➡ | Database-Management-System The maximum number of superkeys for the relation schema R(E,F,G,H) with E as the key is____. |
Show Answer With Best Explanation
Answer: 8
Explanation: Upload Soon
| More Discussion | Explanation On YouTube | Keys | Help-Line |
| Q22➡ | Database-Management-System Given an instance of the STUDENTS relation as shown below: For (StudentName, StudentAge) to be a key for this instance, the value X should NOT be equal to__________. |
Show Answer With Best Explanation
Answer: 19
Explanation: Upload Soon
| More Discussion | Explanation On YouTube | Keys | Help-Line |
| Q23➡ | Computer Network Which one of the following is TRUE about the interior gateway routing protocols – Routing Information Protocol (RIP) and Open Shortest Path First (OSPF)? |
| i ➥ RIP uses distance vector routing and OSPF uses link state routing |
| ii ➥ OSPF uses distance vector routing and RIP uses link state routing |
| iii ➥ Both RIP and OSPF use link state routing |
| iv ➥ Both RIP and OSPF use distance vector routing |
Show Answer With Best Explanation
Answer: I
Explanation: Upload Soon
| More Discussion | Explanation On YouTube | routing protocols | Help-Line |
| Q24➡ | Computer Network Which one of the following socket API functions converts an unconnected active TCP socket into a passive socket? |
| i ➥ connect |
| ii ➥ bind |
| iii ➥ listen |
| iv ➥ accept |
Show Answer With Best Explanation
Answer: III
Explanation: Upload Soon
| More Discussion | Explanation On YouTube | TCP | Help-Line |
| Q25➡ | Computer Network In the diagram shown below, L1 is an Ethernet LAN and L2 is a Token-Ring LAN. An IP packet originates from sender S and traverses to R, as shown. The links within each ISP and across the two ISPs, are all point-to-point optical links. The initial value of the TTL field is 32. The maximum possible value of the TTL field when R receives the datagram is . |
Show Answer With Best Explanation
Answer: 26
Explanation: Upload Soon
| More Discussion | Explanation On YouTube | Ethernet | Help-Line |
[Q26 – Q55 carry TWO mark each ]
| Q26➡ | Computer Network Consider the store and forward packet switched network given below. Assume that the bandwidth of each link is 106 bytes / sec. A user on host A sends a file of size 103 bytes to host B through routers R1 and R2 in three different ways. In the first case a single packet containing the complete file is transmitted from A to B. In the second case, the file is split into 10 equal parts, and these packets are transmitted from A to B. In the third case, the file is split into 20 equal parts and these packets are sent from A to B. Each packet contains 100 bytes of header information along with the user data. Consider only transmission time and ignore processing, queuing and propagation delays. Also assume that there are no errors during transmission. Let T1, T2 and T3 be the times taken to transmit the file in the first, second and third case respectively. Which one of the following is CORRECT? |
| i ➥ T1 < T2 < T3 |
| ii ➥ T1 > T2 > T3 |
| iii ➥ T2 = T3, T3 < T1 |
| iv ➥ T1 = T3, T3 > T2 |
Show Answer With Best Explanation
Answer: IV
Explanation: Upload Soon
| More Discussion | Explanation On YouTube | Packet switched | Help-Line |
| Q27➡ | Computer Network An IP machine Q has a path to another IP machine H via three IP routers R1, R2, and R3. Q—R1—R2—R3—H H acts as an HTTP server, and Q connects to H via HTTP and downloads a file. Session layer encryption is used, with DES as the shared key encryption protocol. Consider the following four pieces of information: [I1] The URL of the file downloaded by Q [I2] The TCP port numbers at Q and H [I3] The IP addresses of Q and H [I4] The link layer addresses of Q and H Which of I1, I2, I3, and I4 can an intruder learn through sniffing at R2 alone? |
| i ➥ Only I1 and I2 |
| ii ➥ Only I1 |
| iii ➥ Only I2 and I3 |
| iv ➥ Only I3 and I4 |
Show Answer With Best Explanation
Answer: III
Explanation: Upload Soon
| More Discussion | Explanation On YouTube | Network Security | Help-Line |
| Q28➡ | Computer Network A graphical HTML browser resident at a network client machine Q accesses a static HTML webpage from a HTTP server S. The static HTML page has exactly one static embedded image which is also at S. Assuming no caching, which one of the following is correct about the HTML webpage loading (including the embedded image)? |
| i ➥ Q needs to send at least 2 HTTP requests to S, each necessarily in a separate TCP connection to server S |
| ii ➥ Q needs to send at least 2 HTTP requests to S, but a single TCP connection to server S is sufficient |
| iii ➥ A single HTTP request from Q to S is sufficient, and a single TCP connection between Q and S is necessary for this |
| iv ➥ A single HTTP request from Q to S is sufficient, and this is possible without any TCP connection between Q and S |
Show Answer With Best Explanation
Answer: II
Explanation: Upload Soon
| More Discussion | Explanation On YouTube | TCP | Help-Line |
| Q29➡ | Database Management System Consider the following schedule S of transactions T1, T2, T3, T4: Which one of the following statements is CORRECT? |
| i ➥ S is conflict-serializable but not recoverable |
| ii ➥ S is not conflict-serializable but is recoverable |
| iii ➥ S is both conflict-serializable and recoverable |
| iv ➥ S is neither conflict-serializable nor is it recoverable |
Show Answer With Best Explanation
Answer: III
Explanation: Upload Soon
| More Discussion | Explanation On YouTube | Serializable | Help-Line |
| Q30➡ | Database Management System Consider a join (relation algebra) between relations r(R)and s(S) using the nested loop method. There are 3 buffers each of size equal to disk block size, out of which one buffer is reserved for intermediate results. Assuming size(r(R))<size(s(S)), the join will have fewer number of disk block accesses if. |
| i ➥ relation r(R) is in the outer loop. |
| ii ➥ relation s(S) is in the outer loop. |
| iii ➥ join selection factor between r(R) and s(S) is more than 0.5. |
| iv ➥ join selection factor between r(R) and s(S) is less than 0.5. |
Show Answer With Best Explanation
Answer: I
Explanation: Upload Soon
| More Discussion | Explanation On YouTube | Relational Algebra | Help-Line |
| Q31➡ | Operating System Consider the procedure below for the Producer-Consumer problem which uses semaphores: Which one of the following is TRUE? |
| i ➥ The producer will be able to add an item to the buffer, but the consumer can never consume it. |
| ii ➥ The consumer will remove no more than one item from the buffer. |
| iii ➥ Deadlock occurs if the consumer succeeds in acquiring semaphore s when the buffer is empty. |
| iv ➥ The starting value for the semaphore n must be 1 and not 0 for deadlock-free operation. |
Show Answer With Best Explanation
Answer: III
Explanation: Upload Soon
| More Discussion | Explanation On YouTube | Producer-Consumer | Help-Line |
| Q32➡ | Operating System Three processes A, B and C each execute a loop of 100 iterations. In each iteration of the loop, a process performs a single computation that requires tc CPU milliseconds and then initiates a single I/O operation that lasts for tio milliseconds. It is assumed that the computer where the processes execute has sufficient number of I/O devices and the OS of the computer assigns different I/O devices to each process. Also, the scheduling overhead of the OS is negligible. The processes have the following characteristics: . The processes A, B, and C are started at times 0, 5 and 10 milliseconds respectively, in a pure time sharing system (round robin scheduling) that uses a time slice of 50 milliseconds. The time in milliseconds at which process C would complete its first I/O operation is . |
Show Answer With Best Explanation
Answer: 1000
Explanation: Upload Soon
| More Discussion | Explanation On YouTube | Scheduling | Help-Line |
| Q33➡ | |