| Q1➡ | Software engineering Alpha and Beta testing are forms of |
| i ➥ White -Box Testing |
| ii ➥ Black-Box Testing |
| iii ➥ Acceptance Testing |
| iv ➥ System Testing |
| Best Explanation: Answer: (iii) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q2➡ | Algorithm The solution of the recurrence relation T(n)=3T(n/4)+nlgn is |
| i ➥ θ(n2logn) |
| ii ➥ θ(nlogn) |
| iii ➥ θ(nlogn)2 |
| iv ➥ θ(nloglogn) |
| Best Explanation: Answer: (ii) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q3➡ | Data Logic Design Consider a logic gate circuit, with 8 input lines (D0, D1………..D7) and 3 input Lines (A0, A1, A2) specified by following operations A2=D4+D5+D6+D7 A1=D2+D3+D6+D7 A0=D1+D3+D5+D0 Where + indicates logical OR operation. This circuit is |
| i ➥ 3×8 multiplexer |
| ii ➥ Decimal to BCD Converter |
| iii ➥ Octal to Binary encoder |
| iv ➥ Priority encoder |
| Best Explanation: Answer: (iv) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q4➡ | TOC Consider the Properties of recursively enumerable sets: (A) Finiteness (B) Context freedom (C) Emptiness Which of the following is true? |
| i ➥ Only (A) and (B) are not decidable |
| ii ➥ Only (B) and (C) are not decidable |
| iii ➥ Only (C) and (A) are not Decidable |
| iv ➥ All (A), (B) and (C) are not decidable |
| Best Explanation: Answer: (iv) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q5➡ | TOC Consider the production rules of grammar G: S→ AbB A→ aAb/λ B→ bB/λ Which of the following language L is generated by grammar G? |
| i ➥ L={ anbm : n≥0, m>n} |
| ii ➥ L={ anbm : n≥0, m≥0} |
| iii ➥ L={ anbm : n≥m} |
| iv ➥ L={ anbm : n≥m, m>0} |
| Best Explanation: Answer: (i) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q6➡ | Software engineering If every requirment can be checked bye a cost-effective process, then SRS is called |
| i ➥ Verifiable |
| ii ➥ Tracable |
| iii ➥ Modifiable |
| iv ➥ Complete |
| Best Explanation: Answer: (i) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q7➡ | TOC Consider the language L= {anbm: n≥4, m≤3} Which of the following regular expression represents language L? |
| i ➥ aaaa*(λ+b+bb+bbb) |
| ii ➥ aaaaa*(b+bb+bbb) |
| iii ➥ aaaaa*(λ+b+bb+bbb) |
| iv ➥ aaaa*(b+bb+bbb) |
| Best Explanation: Answer: (iii) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
Q8➡ | Artificial Intelligence |
| i ➥ (A) and (D) only |
| ii ➥ (B) and (C) only |
| iii ➥ (A) and (C) only |
| iv ➥ (B) and (C) only |
| Best Explanation: Answer: (iii) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q9➡ | Computer Network match List I with List II: 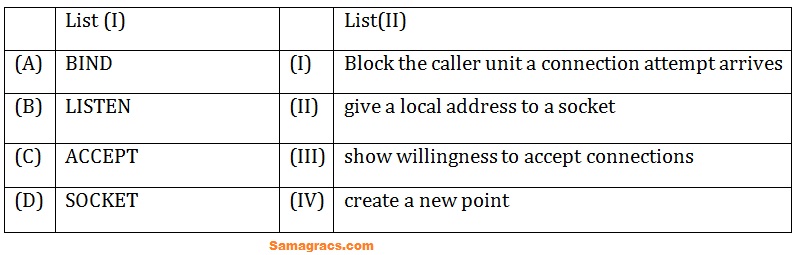 Choose the correct answer from the options given below: |
| i ➥ (A)-(I),(B)-(III),(C)-(II),(D)-(IV) |
| ii ➥ (A)-(II),(B)-(III),(C)-(I),(D)-(IV) |
| iii ➥ (A)-(III),(B)-(II),(C)-(I),(D)-(IV) |
| iv ➥ (A)-(I),(B)-(II),(C)-(III),(D)-(IV) |
| Best Explanation: Answer: (ii) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q10➡ | Software engineering Size and complexity are a part of |
| i ➥ People Metrics |
| ii ➥ Project Metrics |
| iii ➥ Process Metrics |
| iv ➥ Product Metrics |
| Best Explanation: Answer: (iv) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q11➡ | Discrete Mathematics Let ({a,b}, ) be a semigroup , where a*a = b. (A) a*a = b*a (B) b*b = b Choose the most appropriate answer from the options given below: |
| i ➥ (A) only true |
| ii ➥ (B) only true |
| iii ➥ Both (A) and (B) true |
| iv ➥ Neither (A) not (B) true |
| Best Explanation: Answer: (iii) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q12➡ | Computer Architecture In a cache memory , if address has 9 bits in Tag field and 12 bits in index field, the size of main memory and cache memory would be respectively |
| i ➥ 2K, 4K |
| ii ➥ 1024K, 2K |
| iii ➥ 4K, 2048K |
| iv ➥ 2048K, 4K |
| Best Explanation: Answer: (iv) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q13➡ | Compiler Design Consider the grammar S—>SbS|a. Consider the following statements: (A) Two Parse tree (B) Two left most derivation (C) Two right most derivation Which of the following is correct? |
| i ➥ All (A), (B) and (C) are true |
| ii ➥ Only (B) is true |
| iii ➥ Only (C) is true |
| iv ➥ Only (A) is true |
| Best Explanation: Answer: (iv) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q14➡ | Programming Match List (I) with List (II) : 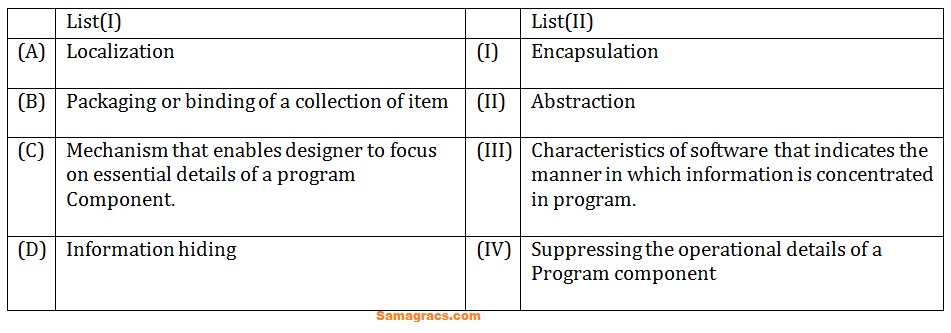 Choose the correct answer from the options given below: |
| i ➥ (A)-(I),(B)-(II),(C)-(III),(D)-(IV) |
| ii ➥ (A)-(II),(B)-(I),(C)-(III),(D)-(IV) |
| iii ➥ (A)-(III),(B)-(I),(C)-(II),(D)-(IV) |
| iv ➥ (A)-(III),(B)-(I),(C)-(IV),(D)-(II) |
| Best Explanation: Answer: (iii) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q15➡ | Programming pointers cannot be used to |
| i ➥ Find the address of a variable in memory |
| ii ➥ Reference value directly |
| iii ➥ Simulate dynamic data structure |
| iv ➥ Manipulate dynamic data structure |
| Best Explanation: Answer: (ii) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q16➡ | Software engineering RAD software process model stand for |
| i ➥ Rapid application Development |
| ii ➥ Relative application development |
| iii ➥ Rapid application design |
| iv ➥ Recent application development |
| Best Explanation: Answer: (i) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q17➡ | Programming The condition num!=65 cannot be replaced by |
| i ➥ num>65 | | num < 65 |
| ii ➥ !(num = = 65) |
| iii ➥ num – 65 |
| iv ➥ !(num – 65) |
| Best Explanation: Answer: (iv) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q18➡ | Computer Network which one is a connectionless transport layer protocol that belongs to the internet protocol family? |
| i ➥ Transmission control protocol (TCP) |
| ii ➥ User Datagram Protocol (UDP) |
| iii ➥ Routing Protocol (RP) |
| iv ➥ Datagram Control Protocol (DCP) |
| Best Explanation: Answer: (ii) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q19➡ | Programming Of the following, which is Not a logical error? |
| i ➥ Using the ‘=’ , instead of ‘==’ to determine if two values are equal |
| ii ➥ Divide by Zero |
| iii ➥ Failing to initialize counter and total variables before the body of loop |
| iv ➥ Using commas instead of two required semicolon in a for loop header |
| Best Explanation: Answer: (iv) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q20➡ | DBMS Consider the following statements: Statement I: Composite attributes cannot be divided into smaller subparts. Statement II: complex attributes is formed by nesting Composite attributes and multi-valued attributes in an arbitrary way. Statement III : A derived attribute is an attribute whose value are computed from other attribute. Which of the following is correct? |
| i ➥ Statement I, statement II and statement III are true |
| ii ➥ Statement I true and statement II , statement III are false |
| iii ➥ Statement I, statement II true and Statement III false |
| iv ➥ Statement I false and statement II, statment III true |
| Best Explanation: Answer: (iv) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q21➡ | TOC Match List (I) with List (II): 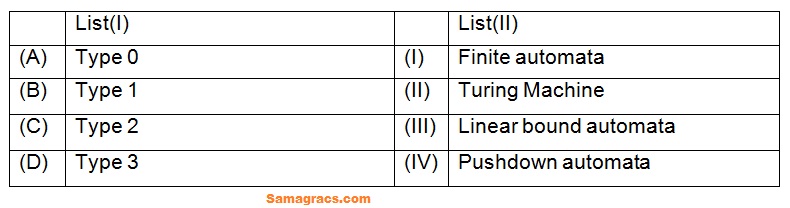 Choose the correct answer from the options given below: |
| i ➥ (A)-(III),(B)-(IV),(C)-(II),(D)-(I) |
| ii ➥ (A)-(II),(B)-(III),(C)-(IV),(D)-(I) |
| iii ➥ (A)-(III),(B)-(IV),(C)-(I),(D)-(II) |
| iv ➥ (A)-(II),(B)-(III),(C)-(I),(D)-(IV) |
| Best Explanation: Answer: (ii) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q22➡ | Software engineering The Process to gather the software requirement from client, analyze and document is known as – |
| i ➥ Software Engineering Process |
| ii ➥ User Engineering Process |
| iii ➥ Requirement Elicitation Process |
| iv ➥ Requirement Engineering Process |
| Best Explanation: Answer: (iv) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q23➡ | Software engineering A good software requirement specification does NOT have the characteristic |
| i ➥ Completeness |
| ii ➥ Consistency |
| iii ➥ Clarity |
| iv ➥ Reliability |
| Best Explanation: Answer: (iv) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q24➡ | Operating System If an operating system does not allow a child process to exist when the parent process has been terminated, this phenomenon is called as – |
| i ➥ Threading |
| ii ➥ Cascading termination |
| iii ➥ Zombie termination |
| iv ➥ Process killing |
| Best Explanation: Answer: (ii) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q25➡ | Software engineering Modules X and Y operate on the same input and output, then the cohesion is |
| i ➥ Logical cohesion |
| ii ➥ Sequential cohesion |
| iii ➥ Procedural cohesion |
| iv ➥ Communication cohesion |
| Best Explanation: Answer: (iv) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q26➡ | Computer Network which of the following is correct for the destination address 4A : 30 : 10 : 21 : 10 : 1A? |
| i ➥ Unicast address |
| ii ➥ Multicast address |
| iii ➥ Broadcast address |
| iv ➥ Unicast and broadcast address |
| Best Explanation: Answer: (i) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q27➡ | Computer Network which mode is a block cipher implementation as a self synchronizing stream cipher? |
| i ➥ Cipher Block chaining mode |
| ii ➥ Cipher feedback mode |
| iii ➥ Electronic codebook mode |
| iv ➥ Output feedback mode |
| Best Explanation: Answer: (ii) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q28➡ | Discrete Mathematics Consider the primal problem: Maximize z = 5x1 + 12x2 + 4x3 Subject to x1 + 2x2 + x3 = 10 2x1 – x2 + 3x3 = 8 x1, x2, x3 ≥ 0 It’s dual problem is Minimize w = 10y1 + 8y2 Subject to y1 + 2y2 ≥ 5 2y1 – y2 ≥ 12 y1 + 3y2 ≥ 4 Which of the following is correct? |
| i ➥ y1≥ 0 , y2 unrestricted |
| ii ➥ y1≥ 0 , y2≥ 0 |
| iii ➥ y1 is unrestricted, y2 ≥ 0 |
| iv ➥ y1 is unrestricted, y2 is restricted |
| Best Explanation: Answer: (i) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q29➡ | Discrete Mathematics There are three boxes. First box has 2 white, 3 black and 4 red balls. Second box has 3 white, 2 Black and 2 red balls. Third box has 4 white, 1 black and 3 red balls. A box is chosen at random and 2 balls are drawn out of which 1 is white , and 1 is red. What is the probability that the balls came from first box? |
| i ➥ 0.237 |
| ii ➥ 0.723 |
| iii ➥ 0.18 |
| iv ➥ 0.452 |
| Best Explanation: Answer: (i) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q30➡ | Algorithm Which of the following algorithm design approach is used in Quick sort algorithm? |
| i ➥ Dynamic programming |
| ii ➥ Back tracking |
| iii ➥ Divide and conquer |
| iv ➥ Greedy approach |
| Best Explanation: Answer: (iii) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q31➡ | Operating System For the following page reference string 4, 3, 2, 1, 4, 3, 5, 4, 3, 2, 1, 5 the number of page faults that occur in Least Recently Used (LRU) page replacement algorithm with frame size 3 is |
| i ➥ 6 |
| ii ➥ 8 |
| iii ➥ 10 |
| iv ➥ 12 |
| Best Explanation: Answer: (iii) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
Q32➡ | Algorithm 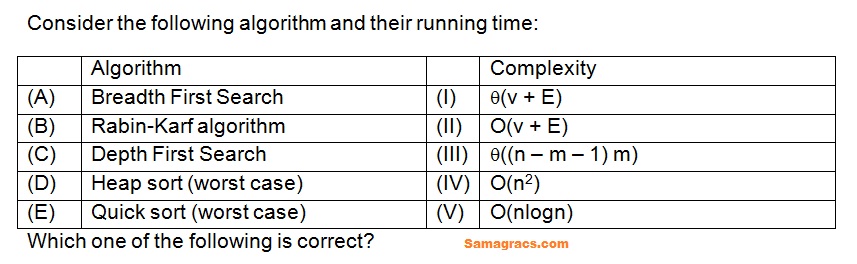 |
| i ➥ (A)-(III),(B)-(II),(C)-(I),(D)-(IV), (E)-(V) |
| ii ➥ (A)-(II),(B)-(III),(C)-(I),(D)-(IV),(E)-(V) |
| iii ➥ (A)-(II),(B)-(III),(C)-(I),(D)-(V),(E)-(IV) |
| iv ➥ (A)-(III),(B)-(I),(C)-(II),(D)-(IV), (E)-(V) |
| Best Explanation: Answer: (iii) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q33➡ | Data Logic Design The number of gate inputs, required to realize expression ABC+AB̅CD+E Fbar+AD is |
| i ➥ 12 |
| ii ➥ 13 |
| iii ➥ 14 |
| iv ➥ 15 |
| Best Explanation: Answer: (iv) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q34➡ | Programming which mechanism in XML allows organizations to specify globally unique names as element tags in documents? |
| i ➥ root |
| ii ➥ Header |
| iii ➥ Schema |
| iv ➥ Namespace |
| Best Explanation: Answer: (iv) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
Q35➡ | TOC |
| i ➥ L = {a2nbn : n≥0} |
| ii ➥ L = {anb2n : n≥0} |
| iii ➥ L = {a2nbn : n>0} |
| iv ➥ L = {anb2n : n>0} |
| Best Explanation: Answer: (ii) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q36➡ | TOC Consider L = {ab, aa, baa} Which of the following string is NOT in L? |
| i ➥ baaaaabaaaaa |
| ii ➥ abaabaaabaa |
| iii ➥ aaaabaaaa |
| iv ➥ baaaaabaa |
| Best Explanation: Answer: (i) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q37➡ | Computer Architecture Consider the following related to Fourth Generation Technique (4GT): (A) It controls efforts (B) It controls resources (C) It controls cost of development. Choose the correct answer from the options given below: |
| i ➥ (A) and (B) only |
| ii ➥ (B) and (C) only |
| iii ➥ (C) and (A) only |
| iv ➥ All (A), (B) and (C) |
| Best Explanation: Answer: (iv) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q38➡ | DBMS A trigger is |
| i ➥ A statement that enables to start DBMS. |
| ii ➥ A statement that is executed by the user when debugging an application program. |
| iii ➥ A condition the system tests for the validity of the database user. |
| iv ➥ A statement that is executed automatically by the system as a side effect of modification to the database. |
| Best Explanation: Answer: (iv) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q39➡ | Computer Network The representation of 4 bits code 1101 into 7 bit, even parity Hamming code is |
| i ➥ (1010101) |
| ii ➥ (1111001) |
| iii ➥ (1011101) |
| iv ➥ (1110000) |
| Best Explanation: Answer: (i) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q40➡ | Data Structure How many rotations are required during the construction of an AVL tree if the following elements are to be added in the given sequence? 35, 50, 40, 25, 30, 60, 78, 20, 28 |
| i ➥ 2 left rotation, 2 right rotation |
| ii ➥ 2 left rotation, 3 right rotation |
| iii ➥ 3 left rotation, 2 right rotation |
| iv ➥ 3 left rotation, 1 right rotation |
| Best Explanation: Answer: (iii) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q41➡ | Data Structure Consider the hash table of size 11 that uses open addressing with linear probing. Let h(k) = k mod 11 be the hash function. A sequence of records with keys 43, 36, 92, 87, 11, 47, 11, 13, 14 is inserted into an initially empty hash table. The bins of which are indexed from 0 to 10. What is the index of the bin into which the last record is inserted? |
| i ➥ 8 |
| ii ➥ 7 |
| iii ➥ 10 |
| iv ➥ 4 |
| Best Explanation: Answer: (ii) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q42➡ | Compiler Design Consider the following statements: Statement (I) : LALR Parser is more powerful than canonical LR parser Statement (II) : SLR parser is more powerful that LALR Which of the following is correct? |
| i ➥ Statement (I) true and statement (II) false |
| ii ➥ Statement (I) false and statement (II) true |
| iii ➥ Both statement (I) and Statement (II) false |
| iv ➥ Both statement (I) and statement (II) true |
| Best Explanation: Answer: (iii) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q43➡ | Programming which statement is false? |
| i ➥ All function calls in C pass arguments using call by value |
| ii ➥ Call by reference enables a called function to modify a variable in calling function |
| iii ➥ Call by value always more efficient that call by reference |
| iv ➥ Programmers use pointers and indirection operation to simulate call by references |
| Best Explanation: Answer: (iii) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q44➡ | Computer Architecture Consider a memory system having address spaced at a distance of m , T = Bank cycle time and n number of banks , then the average data access time per word access in synchronous organization is |
| i ➥ |
ii ➥ 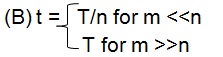 |
iii ➥  |
iv ➥  |
| Best Explanation: Answer: (i) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q45➡ | Computer Architecture The total storage capacity of a floppy disk having 80 tracks and storing 128 bytes/sector is 163,840 bytes . How many sectors does this disk have ? |
| i ➥ 27 |
| ii ➥ 2048 |
| iii ➥ 4K |
| iv ➥ 16 |
| Best Explanation: Answer: (iv) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q46➡ | Computer Network which layer divides each message into packets at the source and re-assembles them at the destination? |
| i ➥ Network layer |
| ii ➥ Transport layer |
| iii ➥ Data link layer |
| iv ➥ Physical layer |
| Best Explanation: Answer: (ii) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q47➡ | Data Structure Consider a B-tree of height h , minimum degree t≥2 that contains any n-key, where n≥1 which of the following is correct? |
| i ➥ h≥logt(n+1\2) |
| ii ➥ h≤ logt(n+1\2) |
| iii ➥ h≥ logt(n-1\2) |
| iv ➥ h≤ logt(n-1\2) |
| Best Explanation: Answer: (ii) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q48➡ | Computer Graphics This transformation is called: 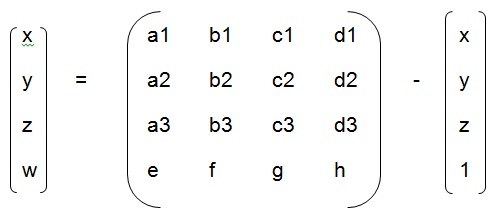 |
| i ➥ Scaling |
| ii ➥ Shear |
| iii ➥ Homography |
| iv ➥ Steganography |
| Best Explanation: Answer: (iii) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q49➡ | TOC The reduced grammar equivalent to the grammar, whose production rules are given below is S—> AB | CA B—> BC | AB A—> a C—> aB | b |
| i ➥ S—> CA , A—> a, C—> b |
| ii ➥ S—> CA | B , B—> BC | B, A—> a , C—> aB | b |
| iii ➥ S—> CA | B, B —> BC , A—> a , C—> aB | b |
| iv ➥ S—> AB | AC, B —> BC | BA, A—> a , C —> aB | b |
| Best Explanation: Answer: (i) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q50➡ | Match the List (I) with List (II) : 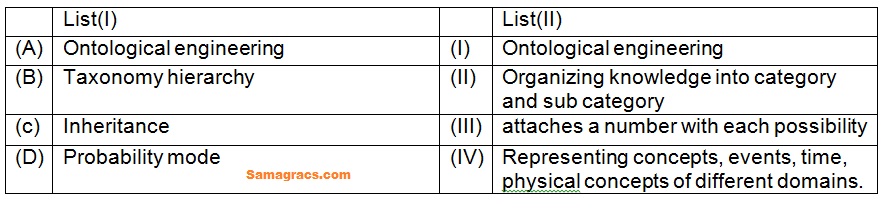 Choose the correct answer from the options given below. |
| i ➥ (A)-(II),(B)-(I),(C)-(IV),(D)-(III) |
| ii ➥ (A)-(I),(B)-(II),(C)-(III),(D)-(IV) |
| iii ➥ A)-(IV),(B)-(III),(C)-(I),(D)-(II) |
| iv ➥ (A)-(IV),(B)-(I),(C)-(II),(D)-(III) |
| Best Explanation: Answer: (iv) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q51➡ | Software engineering Which of the following an indirect measure of product? |
| i ➥ Quality |
| ii ➥ Complexity |
| iii ➥ Reliability |
| iv ➥ All of these |
| Best Explanation: Answer: (iv) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
Q52➡ | TOC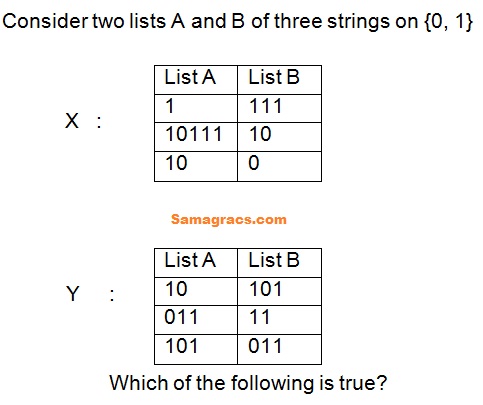 |
| i ➥ Only PCP in X has solution |
| ii ➥ Only PCP in Y has solution |
| iii ➥ PCP in both X and Y has solution |
| iv ➥ PCP neither in X nor in Y has solution |
| Best Explanation: Answer: (iii) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q53➡ | Computer Network Consider an error free 64 kbps satellite channel used to sent 512 byte data frames I one direction with very short acknowledgements coming back the other way. What is the maximum throughput for window size of 15? |
| i ➥ 32 kbps |
| ii ➥ 48 kbps |
| iii ➥ 64 kbps |
| iv ➥ 70 kbps |
| Best Explanation: Answer: (iii) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q54➡ | Discrete Mathematics Let ∈ = 0.0005 and let Re be the relation { (x, y) ∈ R2 : |x-y| <∈} , Re could be interpreted as the relation approximately equal Re is (A) Reflexive (B) Symmetric (C) Transitive Choose the correct answer from the option given below : |
| i ➥ (A) and (B) only True |
| ii ➥ (B) and (C) only True |
| iii ➥ (A) and (C) only True |
| iv ➥ (A), (B) and (C) True |
| Best Explanation: Answer: (i) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
Q55➡ | Computer Architecture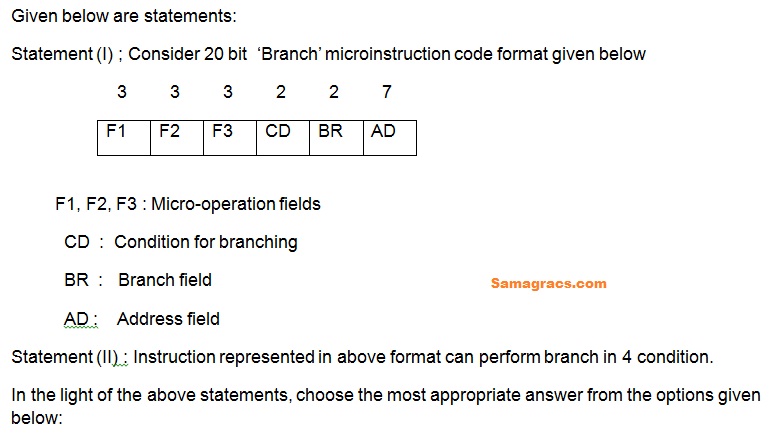 |
| i ➥ Both statement (I) and Statement (II) are correct |
| ii ➥ Both statement (I) and Statement (II) are incorrect |
| iii ➥ Statement (I) is correct and Statement (II) are incorrect |
| iv ➥ Statement (I) is incorrect and Statement (II) are correct |
| Best Explanation: Answer: (i) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q56➡ | Computer Network For multiprocessor system , interconnection network – cross bar switch is an example of |
| i ➥ Non blocking network |
| ii ➥ Blocking network |
| iii ➥ That varies from connection to connection |
| iv ➥ Recurrent network |
| Best Explanation: Answer: (i) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q57➡ | Computer Architecture A 4-stage pipeline has the delay as 150, 120, 160 and 140 ns respectively . registers that are used between the stage have delay of 5 ns. Assuming constant locking rate , the total time required to process 1000 data items on this pipeline is |
| i ➥ 160.5 ns |
| ii ➥ 165.5 ns |
| iii ➥ 120.5 ns |
| iv ➥ 590.5 ns |
| Best Explanation: Answer: (ii) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q58➡ | Data Structure Consider the following graph: 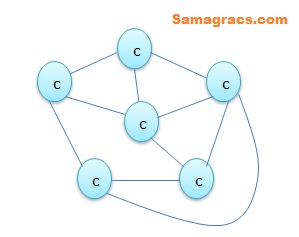 For the graph : the following sequences of depth first search (DFS) are given (A) abcghf (B) abfchg (C) abfhgc (D) afghbc Which of the following is correct? |
| i ➥ (A), (B) and (D) only |
| ii ➥ (A) ,(B) and (D) only |
| iii ➥ (B), (C) and (D) only |
| iv ➥ (A), (C) and (D) only |
| Best Explanation: Answer: (iv) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q59➡ | Data Structure The Number of nodes of height h in any n-element heap is atmost : |
| i ➥ n/2h+1 |
| ii ➥ n/2h-1 |
| iii ➥ n/2h |
| iv ➥ n-1/2h-1 |
| Best Explanation: Answer: (i) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q60➡ | Computer Network Using ‘RSA’ algorithm, if p = 13, q = 5 and e = 7 . the value of d and cipher value of ‘6’ with (e,n) key are |
| i ➥ 7, 4 |
| ii ➥ 7, 1 |
| iii ➥ 7, 46 |
| iv ➥ 55, 1 |
| Best Explanation: Answer: (iii) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q61➡ | Computer Architecture A magnetic tape drive has transport speed of 200 inches per second and a recording density of 1600 bytes per inch. The time required to write 600000 bytes of date grouped in 100 charaters record with a blocking factor 10 is |
| i ➥ 2.0625 sec |
| ii ➥ 2.6251 sec |
| iii ➥ 2.0062 sec |
| iv ➥ 2.6150 sec |
| Best Explanation: Answer: (i) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q62➡ | Artificial Intelligence The logic expression (P̃∧Q)∨(P∧Q̃)∨(P∧Q) is equivalent to |
| i ➥ P̃∨Q |
| ii ➥ P∨Q̃ |
| iii ➥ P∨Q |
| iv ➥ P̃∨Q̃ |
| Best Explanation: Answer: (iii) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q63➡ | Artificial Intelligence Given below are two statements : one is labelled as assertion (A) and the other is labelled as Reason (R): Assertion (A) : p̃ Reason (R) : (r→q̃ , r→s , s→q̃ , p→q) In the light of the above statements, choose the correct answer from the options given below: |
| i ➥ Both (A) and (R) are true and (R) is the correct explanation of (A) |
| ii ➥ Both (A) and (R) are true but (R) is NOT correct explanation of (A) |
| iii ➥ (A) is true but (R) is false |
| iv ➥ (A) is false but (R) is true |
| Best Explanation: Answer: (i) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q64➡ | Operating System what is called journaling in Linux operating system? |
| i ➥ Process scheduling |
| ii ➥ File saving as transaction |
| iii ➥ A type of thread |
| iv ➥ An editor |
| Best Explanation: Answer: (ii) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q65➡ | Algorithm Assume that f(n) and g(n) are asymptotically positive. Which of the following is correct? |
| i ➥ f(n) = O(g(n)) and g(n) = O(h(n))⇒f(n) = ω(h(n)) |
| ii ➥ f(n) =Ω(g(n)) and g(n) = Ω(h(n)) ⇒ f(n) = O(h(n)) |
| iii ➥ f(n) = o(g(n)) and g(n) = o(h(n))⇒f(n) = O(h(n)) |
| iv ➥ f(n) = ω(g(n)) and g(n) =ω(h(n))⇒f(n) = Ω(h(n)) |
| Best Explanation: Answer: (iii) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q66➡ | Algorithm Consider the following statements of approximation algorithm : Statement (I) : Vertex-cover is a polynomial time 2-approximation algorithm Statement (II) : TSP-tour is a polynomial time 3 –approximation algorithm for travelling salesman problem with the triangle inequality. Which of the following is correct? |
| i ➥ Statement (I) true and Statement (II) false |
| ii ➥ Statement (I) and Statement (II) true |
| iii ➥ Statement (I) and Statement (II) true |
| iv ➥ Statement (I) and Statement (II) true |
| Best Explanation: Answer: (i) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
Q67➡ | Operating System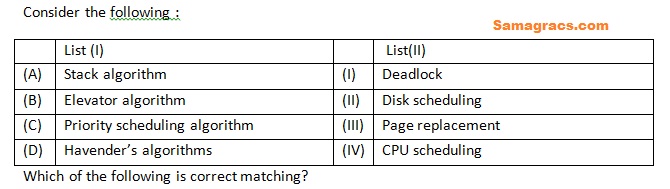 |
| i ➥ (A)-(III),(B)-(II),(C)-(IV),(D)-(I) |
| ii ➥ (A)-(II),(B)-(III),(C)-(IV),(D)-(I) |
| iii ➥ (A)-(III),(B)-(II),(C)-(I),(D)-(IV) |
| iv ➥ (A)-(II),(B)-(III),(C)-(I),(D)-(IV) |
| Best Explanation: Answer: (i) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q68➡ | Computer Graphics Hidden surface removal problem with minimal 3 D pipeline can be solved with |
| i ➥ Painter’s algorithm |
| ii ➥ Window clipping algorithm |
| iii ➥ Brute force rasterization algorithm |
| iv ➥ Flood fill algorithm |
| Best Explanation: Answer: (i) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q69➡ | Given below are two statements : one is labelled as Assertion (A) and the other is labelled as Reason(R): Assertion (A) : A load and go assembler avoids the overhead of writing the object program out and reading it back in Reason (R) : This can be done with either one-pass or two pas assembler. In the light of the above statements, choose the correct answer from the options given below: |
| i ➥ Both (A) and (R) are true and (R) is the correct explanation of (A) |
| ii ➥ Both (A) and (R) are true but (R) is NOT correct explanation of (A) |
| iii ➥ (A) is true but (R) is false |
| iv ➥ (A) is false but (R) is true |
| Best Explanation: Answer: (i) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q70➡ | Artificial Intelligence In a game playing search tree, upto which depth α-β pruning can be applied? (A) Root (0) level (B) 6 level (C) 8 level (D) Depends on utility value in a breadth order Choose the correct answer from the options given below : |
| i ➥ (B) and (C) only |
| ii ➥ (A) and (B) only |
| iii ➥ (A) , (B) and (C) only |
| iv ➥ (A) and (D) only |
| Best Explanation: Answer: (i) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
Q71➡ | 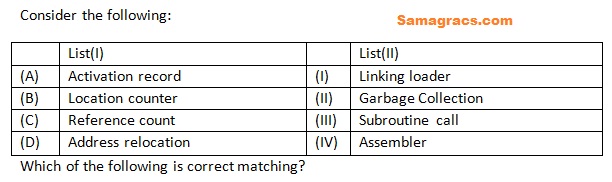 |
| i ➥ (A)-(III),(B)-(IV),(C)-(I),(D)-(II) |
| ii ➥ (A)-(IV),(B)-(III),(C)-(I),(D)-(II) |
| iii ➥ (A)-(IV),(B)-(III),(C)-(II),(D)-(I) |
| iv ➥ (A)-(II),(B)-(III),(C)-(I),(D)-(IV) |
| Best Explanation: Answer: Mark to All Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
Q72➡ | Computer Network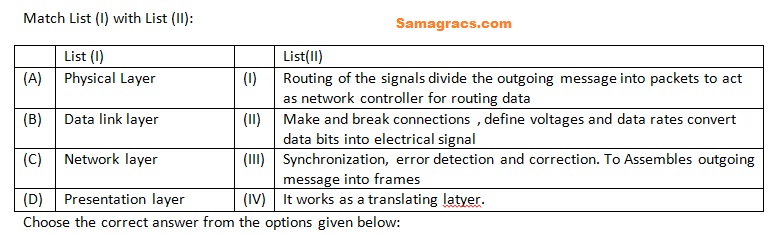 |
| i ➥ (A)-(IV),(B)-(III),(C)-(II),(D)-(I) |
| ii ➥ (A)-(II),(B)-(III),(C)-(IV),(D)-(I) |
| iii ➥ (A)-(IV),(B)-(III),(C)-(I),(D)-(II) |
| iv ➥ (A)-(II),(B)-(III),(C)-(I),(D)-(IV) |
| Best Explanation: Answer: (iv) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q73➡ | In reference to big data , consider the following database : (A) Memcached (B) Couch DB (C) Infinite graph Choose the most appropriate answer from the options given below: |
| i ➥ (A) and (B) only |
| ii ➥ (B) and (C) only |
| iii ➥ (C) and (A) only |
| iv ➥ (A), (B) and (C) |
| Best Explanation: Answer: (iv) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
Q74➡ | DBMS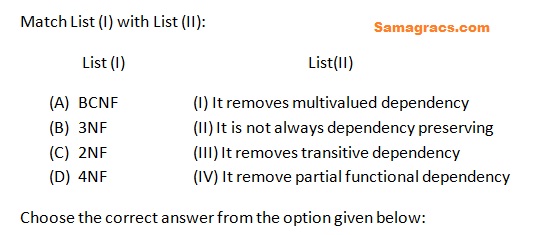 |
| i ➥ (A)-(III),(B)-(II),(C)-(IV),(D)-(I) |
| ii ➥ (A)-(II),(B)-(IV),(C)-(I),(D)-(III) |
| iii ➥ (A)-(II),(B)-(III),(C)-(IV),(D)-(I) |
| iv ➥ (A)-(II),(B)-(I),(C)-(IV),(D)-(III) |
| Best Explanation: Answer: (iii) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q75➡ | DBMS Consider the following statements : statement (I) : Conservative 2 PL is a deadlock free protocol Statement (II) : Thomas’s write rule enforces conflict serializablity Statement (III) : Timestamp ordering protocol ensures serializability based on the order of transaction timestamps. Which of the following is correct ? |
| i ➥ Statement (I), statement (II) true and Statement (III) false |
| ii ➥ Statement (I), Statement (III) true and Statement (II) false |
| iii ➥ Statement (I), Statement (II) false and Statement (III) true |
| iv ➥ Statement (I), statement (II) and Statement (III) true |
| Best Explanation: Answer: (ii) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
Q76➡ | Operating System |
| i ➥ (A)-(III),(B)-(II),(C)-(IV),(D)-(I) |
| ii ➥ (A)-(I),(B)-(II),(C)-(III),(D)-(IV) |
| iii ➥ (A)-(II),(B)-(III),(C)-(I),(D)-(IV) |
| iv ➥ (A)-(II),(B)-(I),(C)-(III),(D)-(IV) |
| Best Explanation: Answer: (iii) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
Q77➡ | Discrete Mathematics |
| i ➥ X is true |
| ii ➥ Y is true |
| iii ➥ Both X and Y are True |
| iv ➥ It does not depend on X and Y |
| Best Explanation: Answer: (iii) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q78➡ | In a database, a rule is defined as (P1 and P2) or P3? R1 (0.8) and R2 (0.3), where P1, P2, P3 are premises and R1, R2 are conclusions of rules with certainty factors (CF) 0.8 and 0.3 respectively. If any running program has produced P1, P2, P3 with CF as 0.5, 0.8, 0.2 respectively , find the CF of results on the basis of premises. |
| i ➥ CF(R1 = 0.8), CF(R2 = 0.3) |
| ii ➥ CF(R1 = 0.40), CF(R2 =0.15) |
| iii ➥ CF(R1 = 0.15), CF(R2 =0.35) |
| iv ➥ CF(R1 = 0.8), CF(R2 =0.35) |
| Best Explanation: Answer: (ii) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q79➡ | Data Structure Consider the traversal of a tree Preorder → ABCEIFJDGHKL Inorder → EICFJBGDKHLA Which of the following is correct post order traversal ? |
| i ➥ EIFJCKGLHDBA |
| ii ➥ FCGKLHDBUAE |
| iii ➥ FCGKLHDBAEIJ |
| iv ➥ IEJFCGKLHDBA |
| Best Explanation: Answer: (iv) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q80➡ | Software engineering Which Metrics are derived by normalizing quality and /or productivity measures by considering the size of the software that he been produced ? |
| i ➥ Function – Oriented Metrics |
| ii ➥ Function – Point Metrics |
| iii ➥ Line of code Metrics |
| iv ➥ Size Oriented Metrics |
| Best Explanation: Answer: (iv) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
Q81➡ | Computer Network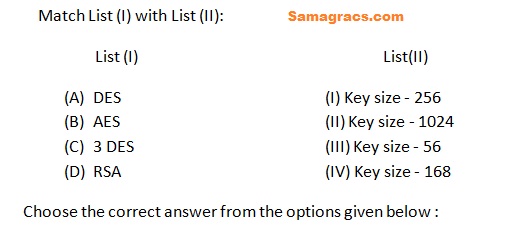 |
| i ➥ (A)-(I),(B)-(II),(C)-(IV),(D)-(III) |
| ii ➥ (A)-(III),(B)-(I),(C)-(IV),(D)-(II) |
| iii ➥ (A)-(III),(B)-(IV),(C)-(II),(D)-(I) |
| iv ➥ (A)-(IV),(B)-(II),(C)-(III),(D)-(I) |
| Best Explanation: Answer: (ii) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q82➡ | Programming A top down approach to programming calls for : Statement (I) : Working from the general to the specific Statement (II) : Postpone the minor decisions Statement (III) : A systematic approach Statement (IV) Intermediate coding of the problem Which of the following is true ? |
| i ➥ Statement (I) only |
| ii ➥ Statement (I) and Statement (II) only |
| iii ➥ Statement (I) , Statement (II) and Statement (III) only |
| iv ➥ Statement (I) , Statement (II) and Statement (IV) only |
| Best Explanation: Answer: (iii) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q83➡ | DBMS Let R (ABCDEFGH) be a relation schema and F be the set of dependencies F = { A→ B, ABCD→E, EF→ G, EF→ H and ACDF→EG} the minimal cover of a set of functional dependencies is |
| i ➥ A→B, ACD→E, EF→ G, and EF→H |
| ii ➥ A→B, ACD→ E, EF→ G, EF→ H and ACDF → G |
| iii ➥ A→B, ACD→ E, EF→G, EF→H and ACDF→E |
| iv ➥ A→B, ABCD→E, EF→H and EF→G |
| Best Explanation: Answer: (i) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q84➡ | Software engineering The model in which the requirements are implemented by its category is |
| i ➥ Evolutionary Development Model |
| ii ➥ Waterfall Model |
| iii ➥ Prototype Model |
| iv ➥ Iterative Enhancement Model |
| Best Explanation: Answer: (i) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q85➡ | TOC Consider the following statements about Context Free Language ( CFL) : Statement (I) : CFL is closed under homomorphism Statement (II) : CFL is closed under complement Which of the following is correct? |
| i ➥ Statement (I) is true and statement (II) is false |
| ii ➥ Statement (II) is true and statement (I) is false |
| iii ➥ Both statement (I) and statement (II) are true |
| iv ➥ Both statement (I) and statement (II) are false |
| Best Explanation: Answer: (i) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q86➡ | Computer Network A classless address is given as 167.199.170.82/27. The number of addresses in the network is |
| i ➥ 64 addresses |
| ii ➥ 32 addresses |
| iii ➥ 28 addresses |
| iv ➥ 30 addresses |
| Best Explanation: Answer: (ii) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
Q87➡ | |
| i ➥ (A)-(I),(B)-(II),(C)-(III),(D)-(IV) |
| ii ➥ (A)-(II),(B)-(III),(C)-(I),(D)-(IV) |
| iii ➥ (A)-(I),(B)-(II),(C)-(IV),(D)-(III) |
| iv ➥ (A)-(II),(B)-(III),(C)-(IV),(D)-(I) |
| Best Explanation: Answer: (iv) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q88➡ | Software engineering Fault base testing technique is |
| i ➥ Unit testing |
| ii ➥ Beta testing |
| iii ➥ Stress testing |
| iv ➥ Mutation testing |
| Best Explanation: Answer: (iv) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
Q89➡ | Artificial Intelligence |
| i ➥ Both statement (I) and statement (II) are correct |
| ii ➥ Both statement (I) and statement (II) are incorrect |
| iii ➥ Statement (I) is correct and statement (II) is incorrect |
| iv ➥ Statement (I) is incorrect and statement (II) is correct |
| Best Explanation: Answer: (i) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
Q90➡ | Operating System |
| i ➥ (A)-(II),(B)-(I),(C)-(IV),(D)-(III) |
| ii ➥ (A)-(II),(B)-(I),(C)-(III),(D)-(IV) |
| iii ➥ (A)-(IV),(B)-(II),(C)-(I),(D)-(III) |
| iv ➥ (A)-(IV),(B)-(I),(C)-(II),(D)-(III) |
| Best Explanation: Answer: (iii) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
Q91➡ | DBMS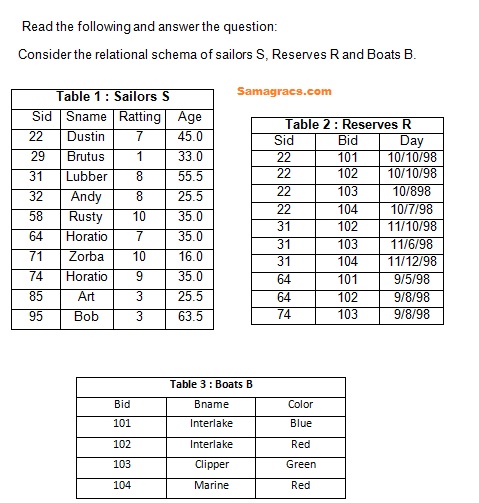 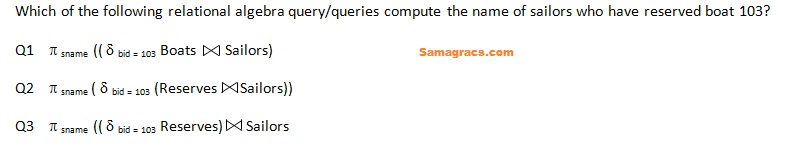 |
| i ➥ Both Q1 and Q3 |
| ii ➥ Both Q2 and Q3 |
| iii ➥ Only Q3 |
| iv ➥ Only Q2 |
| Best Explanation: Answer: (ii) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
Q92➡ | DBMS Which of the following relational algebra query computes the names of sailors who have reserved a red and a green boat? |
i ➥ 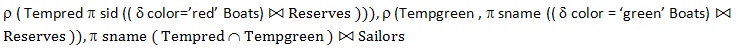 |
| ii ➥ |
| iii ➥ |
| iv ➥ |
| Best Explanation: Answer: (i) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
Q93➡ | DBMS  |
| i ➥ Both Q1 and Q2 |
| ii ➥ Both Q2 and Q3 |
| iii ➥ Only Q1 |
| iv ➥ Only Q2 |
| Best Explanation: Answer: (i) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
Q94➡ | DBMS Which of the following relational algebra query computes to Sid ‘s of Sailors with age over 20 who have not reserved a red boat? |
| i ➥ |
ii ➥  |
| iii ➥ |
iv ➥ 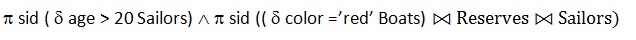 |
| Best Explanation: Answer: (i) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
Q95➡ | DBMS Which of the following relational algebra query computes the names of sailor who have reserved all boats ? |
| i ➥ |
ii ➥ 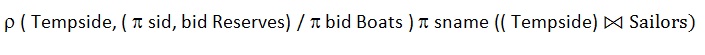 |
iii ➥  |
| iv ➥ |
| Best Explanation: Answer: (ii) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q96➡ | Computer Network Based on following passage, answer the questions : A 300 km long truck operates at 1.536 mbps and is used to transmit 64 bytes frames and uses sliding window protocol. the propagation speed is 6 µ sec/km. If only 6 bits are reserved for sequence number field , then the efficiency of the system is |
| i ➥ 0.587 |
| ii ➥ 0.875 |
| iii ➥ 0.578 |
| iv ➥ 0.50 |
| Best Explanation: Answer: (i) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q97➡ | Computer Network Based on following passage , answer the questions : A 300 km long truck operates at 1.536 mbps and is used to transmit 64 bytes frames and uses sliding window protocol. the propagation speed is 6 μ sec/km. The minimum number of bits required in sequence number fields of the packet is |
| i ➥ 6 bits |
| ii ➥ 7 bits |
| iii ➥ 5 bits |
| iv ➥ 4 bits |
| Best Explanation: Answer: (ii) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q98➡ | Computer Network Based on following passage , answer the questions : A 300 km long truck operates at 1.536 mbps and is used to transmit 64 bytes frames and uses sliding window protocol. the propagation speed is 6 µ sec/km. The maximum achievable throughput is |
| i ➥ 0.768 |
| ii ➥ 0.678 |
| iii ➥ 0.901 |
| iv ➥ 0.887 |
| Best Explanation: Answer: (ii) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q99➡ | Computer Network Based on following passage , answer the questions : A 300 km long truck operates at 1.536 mbps and is used to transmit 64 bytes frames and uses sliding window protocol. the propagation speed is 6 µ sec/km. The transmission and propagation delays are respectively |
| i ➥ Tt = 333.33 µ sec, Tp = 18000 µ sec |
| ii ➥ Tt = 300 µ sec, Tp = 15360 µ sec |
| iii ➥ Tt = 33.33 µ sec, Tp = 1800 µ sec |
| iv ➥ Tt = 1800 µ sec, Tp = 33.33 µ sec |
| Best Explanation: Answer: (i) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q100➡ | Computer Network Based on following passage , answer the questions : A 300 km long truck operates at 1.536 mbps and is used to transmit 64 bytes frames and uses sliding window protocol. the propagation speed is 6 µ sec/km. The Sender window size to get the maximum efficiency is |
| i ➥ 108 |
| ii ➥ 109 |
| iii ➥ 55 |
| iv ➥ 56 |
| Best Explanation: Answer: (ii) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
