 UGC NET CSA Previous Year Solution Paper-II-Jan-2017
UGC NET CSA Previous Year Solution Paper-II-Jan-2017
Note: This paper contains Fifty (50) objective type questions of two(2)marks each.All question are compulsory.
| Q1➡ |MATH-Combinatorics Consider a sequence F00 defined as : F00(0) = 1, F00(1) = 1 F00(n) = ((10 ∗ F00(n – 1) + 100)/ F00(n – 2)) for n ≥ 2 Then what shall be the set of values of the sequence F00 ? |
| A ➥ (1, 110, 1200) |
| B ➥ (1, 110, 600, 1200) |
| C ➥ (1, 2, 55, 110, 600, 1200) |
| D ➥ (1, 55, 110, 600, 1200) |
Show Answer With Best Explanation
| Q2➡ | Artificial-intelligence Match the following :  |
| A ➥ a-i, b-ii, c-iii, d-iv |
| B ➥ a-i, b-iii, c-iv, d-ii |
| C ➥ a-ii, b-iii, c-iv, d-i |
| D ➥ a-ii, b-i, c-iii, d-iv |
Show Answer With Best Explanation
| Q3➡ | Mathematics The functions mapping R into R are defined as : f(x) = x3 – 4x, g(x) = 1/(x 2 + 1) and h(x) = x4 . Then find the value of the following composite functions : hog(x) and hogof(x) |
| A ➥ (x2 + 1)4 and [(x3 – 4x)2 + 1]4 |
| B ➥ (x2 + 1)4 and [(x3 – 4x)2 + 1]-4 |
| C ➥ (x2 + 1)-4 and [(x3 – 4x)2 + 1]4 |
| D ➥ (x2 + 1)-4 and [(x3 – 4x)2 + 1]-4 |
Show Answer With Best Explanation
| Q4➡ | Mathematics How many multiples of 6 are there between the following pairs of numbers ? 0 and 100 and –6 and 34 |
| A ➥ 16 and 6 |
| B ➥ 17 and 6 |
| C ➥ 17 and 7 |
| D ➥ 16 and 7 |
Show Answer With Best Explanation
| Q5➡ | Mathematics In propositional logic if (P → Q) ∧ (R → S) and (P ∨ R) are two premises such that 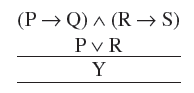 Y is the premise: |
| A ➥ P ∨ R |
| B ➥ P ∨ S |
| C ➥ Q ∨ R |
| D ➥ Q ∨ S |
Show Answer With Best Explanation
| Q6➡ | Graph-Theory Consider a Hamiltonian Graph G with no loops or parallel edges and with |V(G)| = n ≥ 3. Then which of the following is true ? |
| A ➥ deg(v) ≥n/2 for each vertex v. |
| B ➥ |E(G)| ≥1/2(n – 1) (n – 2) + 2 |
| C ➥ deg (v) + deg(w) ≥ n whenever v and w are not connected by an edge |
| D ➥ All of the above |
Show Answer With Best Explanation
| Q7➡ | logic families MP ECL is the fastest of all logic families. High speed in ECL is possible because transistors are used in difference amplifier configuration, in which they are never driven into __. |
| A ➥ Race condition |
| B ➥ Saturation |
| C ➥ Delay |
| D ➥ High impedance |
Show Answer With Best Explanation
| Q8➡ | Digital-Logic-Design A binary 3 bit down counter uses J-K flip-flops, FFi with inputs Ji , Ki and outputs Qi , i=0,1,2 respectively. The minimized expression for the input from following, is I. J0 = K0 = 0 II. J0 = K0 = 1 III. J1 = K1 = Q0 IV. J1 = K1 =Q’0 V. J2 = K2 = Q1 Q 0 VI. J2 = K2 = Q’1 Q’0 |
| A ➥ I,III,V |
| B ➥ I,IV,VI |
| C ➥ II,III,V |
| D ➥ II,IV,VI |
Show Answer With Best Explanation
| Q9➡ | Digital-Logic-Design Convert the octal number 0.4051 into its equivalent decimal number. |
| A ➥ 0.5100098 |
| B ➥ 0.2096 |
| C ➥ 0.52 |
| D ➥ 0.4192 |
Show Answer With Best Explanation
| Q10➡ | Digital-Logic-Design The hexadecimal equivalent of the octal number 2357 is : |
| A ➥ 2EE |
| B ➥ 2FF |
| C ➥ 4EF |
| D ➥ 4FE |
Show Answer With Best Explanation
| Q11➡ |c++ Which of the following cannot be passed to a function in C++ ? |
| A ➥ Constant |
| B ➥ Structure |
| C ➥ Array |
| D ➥ Header file |
Show Answer With Best Explanation
| Q12➡ |c++ Which of the following storage classes have global visibility in C/C++ ? |
| A ➥ Auto |
| B ➥ Extern |
| C ➥ Static |
| D ➥ Register |
Show Answer With Best Explanation
| Q13➡ |c++ Which one of the following is correct for overloaded functions in C++ ? |
| A ➥ Compiler sets up a separate function for every definition of function. |
| B ➥ Compiler does not set up a separate function for every definition of function. |
| C ➥ Overloaded functions cannot handle different types of objects. |
| D ➥ Overloaded functions cannot have same number of arguments. |
Show Answer With Best Explanation
| Q14➡ |c++ Which of the following operators cannot be overloaded in C/C++ ? |
| A ➥ Bitwise right shift assignment |
| B ➥ Address of |
| C ➥ Indirection |
| D ➥ Structure reference |
Show Answer With Best Explanation
| Q15➡ |Number-Systems If X is a binary number which is power of 2, then the value of X & (X – 1) is : |
| A ➥ 11….11 |
| B ➥ 00…..00 |
| C ➥ 100…..0 |
| D ➥ 000……1 |
Show Answer With Best Explanation
| Q16➡ |Database An attribute A of data type varchar (20) has value ‘Ram’ and the attribute B of data type char (20) has value ‘Sita’ in oracle. The attribute A has_______memory spaces and B has_______ memory spaces. |
| A ➥ 20,20 |
| B ➥ 3,20 |
| C ➥ 3,4 |
| D ➥ 20,4 |
Show Answer With Best Explanation
| Q17➡ |Database Integrity constraints ensure that changes made to the database by authorized users do not result into loss of data consistency. Which of the following statement(s) is (are) true w.r.t. the examples of integrity constraints ? (1) An instructor Id. No. cannot be null, provided Instructor Id No. being primary key. (2) No two citizens have same Adhar-Id. (3) Budget of a company must be zero. |
| A ➥ (1), (2) and (3) are true |
| B ➥ (1) false, (2) and (3) are true. |
| C ➥ (1) and (2) are true; (3) false. |
| D ➥ (1), (2) and (3) are false |
Show Answer With Best Explanation
| Q18➡ |Database Let M and N be two entities in an E-R diagram with simple single value attributes. R1 and R2 are two relationship between M and N, where as R1 is one-to-many and R2 is many-to-many. The minimum number of tables required to represent M, N, R1 and R2 in the relational model are ____. |
| A ➥ 4 |
| B ➥ 6 |
| C ➥ 7 |
| D ➥ 3 |
Show Answer With Best Explanation
| Q19➡ |Database Consider a schema R(MNPQ) and functional dependencies M → N, P → Q. Then the decomposition of R into R1 (MN) and R2 (PQ) is________. |
| A ➥ Dependency preserving but not lossless join |
| B ➥ Dependency preserving and lossless join |
| C ➥ Lossless join but not dependency preserving |
| D ➥ Neither dependency preserving nor lossless join. |
Show Answer With Best Explanation
| Q20➡ |Database The order of a leaf node in a B+ tree is the maximum number of children it can have. Suppose that block size is 1 kilobytes, the child pointer takes 7 bytes long and search field value takes 14 bytes long. The order of the leaf node is __. |
| A ➥ 16 |
| B ➥ 63 |
| C ➥ 64 |
| D ➥ 69 |
Show Answer With Best Explanation
| Q21➡ |Data-Structures Which of the following is true for computation time in insertion, deletion and finding maximum and minimum element in a sorted array ? |
| A ➥ Insertion – 0(1), Deletion – 0(1), Maximum – 0(1), Minimum – 0(l) |
| B ➥ Insertion – 0(1), Deletion – 0(1), Maximum – 0(n), Minimum – 0(n) |
| C ➥ Insertion – 0(n), Deletion – 0(n), Maximum – 0(1), Minimum – 0(1) |
| D ➥ Insertion – 0(n), Deletion – 0(n), Maximum – 0(n), Minimum – 0(n) |
Show Answer With Best Explanation
| Q22➡ |Data-Structures The seven elements A, B, C, D, E, F and G are pushed onto a stack in reverse order, i.e., starting from G. The stack is popped five times and each element is inserted into a queue.Two elements are deleted from the queue and pushed back onto the stack. Now, one element is popped from the stack. The popped item is______. |
| A ➥ A |
| B ➥ B |
| C ➥ F |
| D ➥ G |
Show Answer With Best Explanation
| Q23➡ |Data-Structures Which of the following is a valid heap ? |
A ➥ 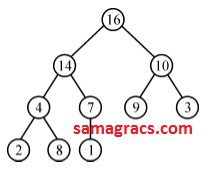 |
B ➥ 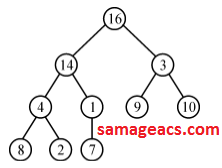 |
C ➥ 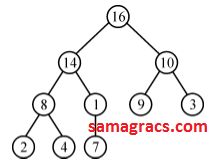 |
D ➥ 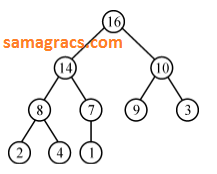 |
Show Answer With Best Explanation
| Q24➡ |Data-Structures If h is chosen from a universal collection of hash functions and is used to hash n keys into a table of size m, where n ≤ m, the expected number of collisions involving a particular key x is less than____. |
| A ➥ 1 |
| B ➥ 1/n |
| C ➥ 1/m |
| D ➥ n/m |
Show Answer With Best Explanation
| Q➡25 |Data-Structures Which of the following statements is false ? (A) (B) Breadth-first search cannot be used to find connected components of a graph. (C) Given the prefix and postfix walks of a binary tree, the tree cannot be re-constructed uniquely. (D) Depth-first-search can be used to find the connected components of a graph. |
| A ➥ Optimal binary search tree construction can be performed efficiently using dynamic programming. |
| B ➥ Breadth-first search cannot be used to find connected components of a graph. |
| C ➥ Given the prefix and postfix walks of a binary tree, the tree cannot be re-constructed uniquely. |
| D ➥ Depth-first-search can be used to find the connected components of a graph. |
Show Answer With Best Explanation
Q26➡ |ComputER NETWORKING  |
| A ➥ a-(iv), b-(i), c-(ii), d-(iii) |
| B ➥ a-(iii), b-(ii), c-(i), d-(iv) |
| C ➥ a-(ii), b-(iii), c-(iv), d-(i) |
| D ➥ a-(iii), b-(i), c-(iv), d-(ii) |
Show Answer With Best Explanation
| Q27➡ |Computer-Network The maximum size of the data that the application layer can pass on to the TCP layer below is_____. |
| A ➥ 216 bytes |
| B ➥ 216 bytes + TCP header length |
| C ➥ 216 bytes – TCP header length |
| D ➥ 215 byte. |
Show Answer With Best Explanation
| Q28➡ |Computer-Network A packet whose destination is outside the local TCP/IP network segment is sent to_______ |
| A ➥ File server |
| B ➥ DNS server |
| C ➥ DHCP server |
| D ➥ Default gateway |
Show Answer With Best Explanation
| Q29➡ |Computer-Networks Distance vector routing algorithm is a dynamic routing algorithm. The routing tables in distance vector routing algorithm are updated |
| A ➥ automatically |
| B ➥ by server |
| C ➥ by exchanging information with neighbor nodes |
| D ➥ with backup database |
Show Answer With Best Explanation
| Q30➡ |Computer-Networks In link state routing algorithm after construction of link state packets, new routes are computed using: |
| A ➥ DES algorithm |
| B ➥ Dijkstra’s algorithm |
| C ➥ RSA algorithm |
| D ➥ Packets |
Show Answer With Best Explanation
| Q31➡ |TOC Which of the following strings would match the regular expression : p+ [3 – 5]∗ [xyz]? I. p443y II. p6y III. 3xyz IV. p35Z V. p353535x VI. ppp5 |
| A ➥ I, III and VI only |
| B ➥ IV, V and VI only |
| C ➥ II, IV and V only |
| D ➥ I, IV and V only |
Show Answer With Best Explanation
| Q32➡ |Machine-Instructions Computer-Organization Consider the following assembly language instructions : mov al, 15 mov ah, 15 xor al, al mov cl, 3 shr ax, cl add al, 90H adc ah, 0 What is the value in ax register after execution of above instructions ? |
| A ➥ 0270H |
| B ➥ 0170H |
| C ➥ 01E0H |
| D ➥ 0370H |
Show Answer With Best Explanation
| Q33➡ |Compiler Consider the following statements related to compiler construction : I. Lexical Analysis is specified by context-free grammars and implemented by pushdown automata. II. Syntax Analysis is specified by regular expressions and implemented by finite-state machine. Which of the above statement(s) is/are correct ? |
| A ➥ Only I |
| B ➥ Only II |
| C ➥ Both I and II |
| D ➥ Neither I nor II |
Show Answer With Best Explanation
| Q34➡ |Microprocessor The contents of Register (BL) and Register (AL) of 8085 microprocessor are 49H and 3AH respectively. The contents of AL, the status of carry flag (CF) and sign flag (SF) after executing ‘SUB AL, BL’ assembly language instruction, are |
| A ➥ AL = 0FH; CF = 1; SF = 1 |
| B ➥ AL = F0H; CF = 0; SF = 0 |
| C ➥ AL = F1H; CF = 1; SF = 1 |
| D ➥ AL = 1FH; CF = 1; SF = 1 |
Show Answer With Best Explanation
| Q35➡ |Operating-System Which of the following statement(s) regarding a linker software is/are true ? I- A function of a linker is to combine several object modules into a single load module. II– A function of a linker is to replace absolute references in an object module by symbolic references to locations in other modules. |
| A ➥ Only I |
| B ➥ Only II |
| C ➥ Both I and II |
| D ➥ Neither I nor II |
Show Answer With Best Explanation
| Q36➡ |Operating-Systems There are three processes P 1 , P 2 and P 3 sharing a semaphore for synchronizing a variable. Initial value of semaphore is one. Assume that negative value of semaphore tells us how many processes are waiting in queue. Processes access the semaphore in following order : (1) P 2 needs to access (2) P 1 needs to access (3) P 3 needs to access (4) P 2 exits critical section (5) P 1 exits critical section The final value of semaphore will be : |
| A ➥ 0 |
| B ➥ 1 |
| C ➥ -1 |
| D ➥ -2 |
Show Answer With Best Explanation
| Q37➡ |Operating-Systems In a paging system, it takes 30 ns to search translation Lookaside Buffer (TLB) and 90 ns to access the main memory. If the TLB hit ratio is 70%, the effective memory access time is : |
| A ➥ 48ns |
| B ➥ 147ns |
| C ➥ 120ns |
| D ➥ 84ns |
Show Answer With Best Explanation
Q38➡ |Operating-Systems 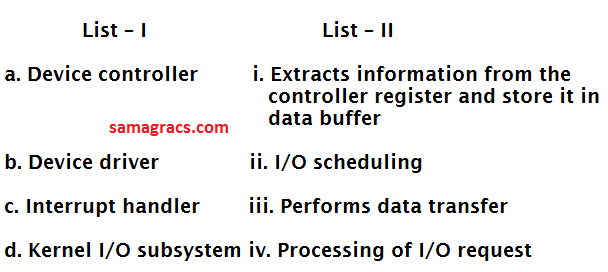 |
| A ➥ a-iii, b-iv, c-i, d-ii |
| B ➥ a-ii, b-i, c-iv, d-iii |
| C ➥ a-iv, b-i, c-ii, d-iii |
| D ➥ a-i, b-iii, c-iv, d-ii |
Show Answer With Best Explanation
| Q39➡ |Operating-Systems Which of the following scheduling algorithms may cause starvation ? 1. First-come-first-served 2. Round Robin 3. Priority 4. Shortest process next 5. Shortest remaining time first |
| A ➥ 1, 3 and 5 |
| B ➥ 3, 4 and 5 |
| C ➥ 2, 4 and 5 |
| D ➥ 2, 3 and 4 |
Show Answer With Best Explanation
| Q40➡ |Distributed operating systems Distributed operating systems consist of: |
| A ➥ Loosely coupled O.S. software on a loosely coupled hardware. |
| B ➥ Loosely coupled O.S. software on a tightly coupled hardware. |
| C ➥ Tightly coupled O.S. software on a loosely coupled hardware. |
| D ➥ Tightly coupled O.S. software on a tightly coupled hardware. |
Show Answer With Best Explanation
| Q41➡ |Software-Engineering Software Engineering is an engineering discipline that is concerned with: |
| A ➥ how computer systems work. |
| B ➥ theories and methods that underlie computers and software systems. |
| C ➥ all aspects of software production |
| D ➥ all aspects of computer-based systems development, including hardware, software and process engineering. |
Show Answer With Best Explanation
| Q42➡ |Software-Engineering Which of the following is not one of three software product aspects addressed by McCall’s software quality factors ? |
| A ➥ Ability to undergo change |
| B ➥ Adaptability to new environments |
| C ➥ Operational characteristics |
| D ➥ Production costs and scheduling |
Show Answer With Best Explanation
| Q43➡ |Software-Engineering Which of the following statement(s) is/are true with respect to software architecture ? S1 : Coupling is a measure of how well the things grouped together in a module belong together logically. S2 : Cohesion is a measure of the degree of interaction between software modules. S3 : If coupling is low and cohesion is high then it is easier to change one module without affecting others. |
| A ➥ Only S1 and S2 |
| B ➥ Only S3 |
| C ➥ All of S1, S2 and S3 |
| D ➥ Only S1 |
Show Answer With Best Explanation
| Q44➡ |Software-Engineering The prototyping model of software development is: |
| A ➥ a reasonable approach when requirements are well-defined |
| B ➥ a useful approach when a customer cannot define requirements clearly. |
| C ➥ the best approach to use for projects with large development teams. |
| D ➥ a risky model that rarely produces a meaningful product. |
Show Answer With Best Explanation
| Q45➡ |Software-Engineering A software design pattern used to enhance the functionality of an object at run-time is: |
| A ➥ Adapter |
| B ➥ Decorator |
| C ➥ Delegation |
| D ➥ Proxy |
Show Answer With Best Explanation
Q46➡ |Artificial-intelligence  |
| A ➥ a-i, b-ii, c-iii, d-iv |
| B ➥ a-i, b-iii, c-ii, d-iv |
| C ➥ a-iii, b-ii, c-iv, d-i |
| D ➥ a-ii, b-iii, c-i, d-iv |
Show Answer With Best Explanation
| Q47➡ |Database _____refers loosely to the process of semi-automatically analyzing large databases to find useful patterns. |
| A ➥ Datamining |
| B ➥ Data warehousing |
| C ➥ DBMS |
| D ➥ Data mirroring |
Show Answer With Best Explanation
| Q48➡ |Mobile-Computing Which of the following is/are true w.r.t. applications of mobile computing ? (A) Travelling of salesman (B) Location awareness services |
| A ➥ (A) true; (B) false. |
| B ➥ Both (A) and (B) are true. |
| C ➥ Both (A) and (B) are false. |
| D ➥ (A) false; (B) true |
Show Answer With Best Explanation
| Q49➡ |Computer-Networks In 3G network, W-CDMA is also known as UMTS. The minimum spectrum allocation required for W-CDMA is______ |
| A ➥ 2 MHz |
| B ➥ 20 KHz |
| C ➥ 5 KHz |
| D ➥ 5 MHz |
Show Answer With Best Explanation
| Q50➡ |Database Which of the following statements is/are true w.r.t. Enterprise Resource Planning (ERP) ? (A) ERP automates and integrates majority of business processes. (B) ERP provides access to information in a Real Time Environment. (C) ERP is inexpensive to implement |
| A ➥ (A), (B) and (C) are false. |
| B ➥ (A) and (B) false; (C) true. |
| C ➥ (A) and (B) true; (C) false. |
| D ➥ (A) true ; (B) and (C) are false. |
