 UGC CBSE NET JAN-III-2017
UGC CBSE NET JAN-III-2017
Note: This paper contains seventy five (75) objective type questions of two(2)marks each.All question are compulsory.
| Q1➡ | Computer-Organization Which of the following is an interrupt according to temporal relationship with system clock? |
| A ➥ Maskable interrupt |
| B ➥ Periodic interrupt |
| C ➥ Division by zero |
| D ➥ Synchronous interrupt |
Show Answer With Best Explanation
| Q2➡ | Operating-Systems Which of the following is incorrect for virtual memory? |
| A ➥ Large programs can be written |
| B ➥ More I/O is required |
| C ➥ More addressable memory available |
| D ➥ Faster and easy swapping of process |
Show Answer With Best Explanation
| Q3➡ | Computer-Organization The general configuration of the micro-programmed control unit is given below: 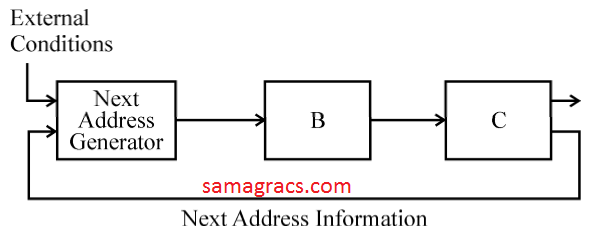 What are blocks B and C in the diagram respectively? |
| A ➥ Block address register and cache memory |
| B ➥ Control address register and control memory |
| C ➥ Branch register and cache memory |
| D ➥ Control address register and random access |
Show Answer With Best Explanation
| Q4➡ |Computer-Organization Match the following :  |
| A ➥ a-(iv), b-(iii), c-(i), d-(ii) |
| B ➥ a-(iv), b-(i), c-(iii), d-(ii) |
| C ➥ a-(iv), b-(ii), c-(i), d-(iii) |
| D ➥ a-(iv), b-(iii), c-(ii), d-(i) |
Show Answer With Best Explanation
| Q5➡ |Computer-Organization In 8085 microprocessor, the digit 5 indicates that the microprocessor needs: |
| A ➥ –5 volts, +5 volts supply |
| B ➥ +5 volts supply only |
| C ➥ –5 volts supply only |
| D ➥ 5 MHz clock |
Show Answer With Best Explanation
| Q6➡ |Computer-Organization In 8085, which of the following performs : load register pair immediate operation? |
| A ➥ LDAX rp |
| B ➥ LHLD addr |
| C ➥ LXI rp, data |
| D ➥ INX rp |
Show Answer With Best Explanation
| Q7➡ | DBMS Consider following schedules involving two transactions: S1 : r1(X); r1(Y); r2(X); r2(Y); w2(Y); w1(X) S2 : r1(X); r2(X); r2(Y); w2(Y); r1(Y); w1(X) Which of the following statement is true? |
| A ➥ Both S1 and S2 are conflict serializable. |
| B ➥ S1 is conflict serializable and S2 is not conflict serializable. |
| C ➥ S1 is not conflict serializable and S2 is conflict serializable. |
| D ➥ Both S1 and S2 are not conflict |
Show Answer With Best Explanation
| Q8➡ | DBMS Which one is correct w.r.t. RDBMS ? |
| A ➥ primary key ⊆ super key ⊆ candidate key |
| B ➥ primary key ⊆ candidate key ⊆ super key |
| C ➥ super key ⊆ candidate key ⊆ primary key |
| D ➥ super key ⊆ primary key ⊆ candidate key |
Show Answer With Best Explanation
| Q9➡ | DBMS Let pk(R) denotes primary key of relation R. A many-to-one relationship that exists between two relations R1 and R2 can be expressed as follows : |
| A ➥ pk(R2) → pk(R1) |
| B ➥ pk(R1) → pk(R2) |
| C ➥ pk(R2) → R1 ∩ R2 |
| D ➥ pk(R1) → R1 ∩ R2 |
Show Answer With Best Explanation
| Q10➡ |DBMS For a database relation R(A, B, C, D) where the domains of A, B, C and D include only atomic values, only the following functional dependencies and those that can be inferred from them are : A → C B → D The relation R is in________. |
| A ➥ First normal form but not in second normal form. |
| B ➥ Both in first normal form as well as in second normal form. |
| C ➥ Second normal form but not in third normal form. |
| D ➥ Both in second normal form as well as in third normal form. |
Show Answer With Best Explanation
| Q11➡ | DBMS Works (emp name, company name, salary) Here, emp_name is primary key. Consider the following SQL query Select emp name From works T Where salary > (select avg (salary) from works S where T.company _ name = S.company _name) The above query is for following : |
| A ➥ Find the highest paid employee who earns more than the average salary of all employees of his company |
| B ➥ Find the highest paid employee who earns more than the average salary of all the employees of all the companies. |
| C ➥ Find all employees who earn more than the average salary of all employees of all the companies. |
| D ➥ Find all employees who earn more than the Average salary of all employees of their company. |
Show Answer With Best Explanation
| Q12➡ | DBMS If following sequence of keys are inserted in a B+ tree with K(=3) pointers: 8, 5, 1, 7, 3, 12, 9, 6 Which of the following shall be correct B+ tree? |
A ➥ 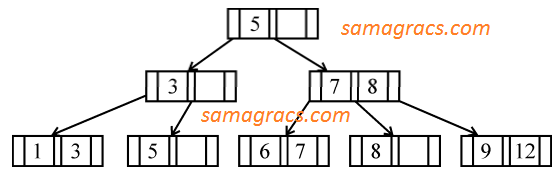 |
B ➥ 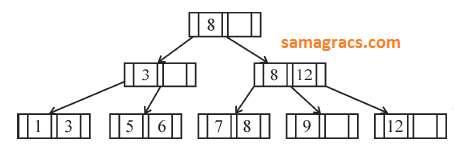 |
C ➥ 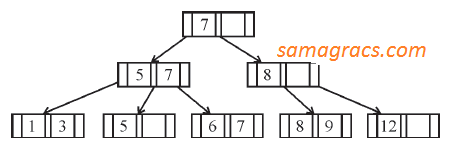 |
D ➥ 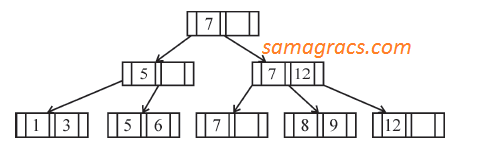 |
Show Answer With Best Explanation
| Q13➡ | Computer Graphics Which of the following statement(s) is/are correct ? |
| i ➥ Persistence is the term used to describe the duration of phosphorescence. |
| ii ➥ The control electrode is used to turn the electron beam on and off. |
| iii ➥ The electron gun creates a source of electrons which are focused into a narrow beam directed at the face of CRT. |
| iv ➥ All of the above |
Show Answer With Best Explanation
| Q14➡ | Computer Graphics A segment is any object described by GKS commands and data that start with CREATE SEGMENT and Terminates with CLOSE SEGMENT command. What functions can be performed on these segments ? |
| i ➥ Translation and Rotation |
| ii ➥ Panning and Zooming |
| iii ➥ Scaling and Shearing |
| iv ➥ Translation, Rotation, Panning and Zooming |
Show Answer With Best Explanation
Q15➡ | Computer Graphics  Code: |
| i ➥ a-i, b-ii, c-iii, d-iv |
| ii ➥ a-i, b-iii, c-ii, d-iv |
| iii ➥ a-iv, b-iii, c-ii, d-i |
| iv ➥ a-iv, b-ii, c-i, d-iii |
Show Answer With Best Explanation
| Q16➡ | Computer Graphics Below are the few steps given for scan-converting a circle using Bresenham’s Algorithm. Which of the given steps is not correct ? |
| i ➥ Compute d = 3 – 2r (where r is radius) |
| ii ➥ Stop if x > y |
| iii ➥ If d < 0, then d = 4x + 6 and x = x + 1 |
| iv ➥ If d ≥, then d = 4 * (x – y) + 10, x = x + 1 and y = y + 1 |
Show Answer With Best Explanation
| Q17➡ | Computer Graphics Which of the following is/are side effects of scan conversion ? 1. Aliasing 2. Unequal intensity of diagonal lines 3. Overstriking in photographic applications 4. Local or Global aliasing |
| i ➥ 1 and 2 |
| ii ➥ 1,2 and 3 |
| iii ➥ 1, 3 and iv |
| iv ➥ i , ii, iii, and iv |
Show Answer With Best Explanation
| Q18➡ | Computer Graphics Consider a line AB with A=(0,0) and B=(8,4). Apply a simple DDA algorithm and compute the first four plots on this line. |
| i ➥ [(0, 0), (1, 1), (2, 1), (3, 2)] |
| ii ➥ [(0, 0), (1, 1.5), (2, 2), (3, 3)] |
| iii ➥ [(0, 0), (1, 1), (2. 2.5), (3, 3)] |
| iv ➥ [(0, 0), (1, 2), (2, 2), (3, 2)] |
Show Answer With Best Explanation
| Q19➡ | TOC Which of the following are not regular? (1) Strings of even number of a’s. (2) Strings of a’s, whose length is a prime number. (3) Set of all palindromes made up of a’s and b’s. (4) Strings of a’s whose length is a perfect square. |
| A ➥ 1 and 2 only |
| B ➥ 1, 2 and 3 only |
| C ➥ 2, 3 and 4 |
| D ➥ 2 and 4 only |
Show Answer With Best Explanation
| Q20➡ | TOC Consider the languages L1 = φ and L2 = {1}. Which one of the following represents L1* ∪ L1*L2* ? |
| A ➥ {∈} |
| B ➥ {∈, 1} |
| C ➥ ϕ |
| D ➥ 1* |
Show Answer With Best Explanation
| Q21➡ | TOC Given the following statements : (i) A class of languages that is closed under union and complementation has to be closed under intersection. (ii) A class of languages that is closed under union and intersection has to be closed under complementation. Which of the following options is correct? |
| A ➥ Both (i) and (ii) are false. |
| B ➥ Both (i) and (ii) are true. |
| C ➥ (i) is true, (ii) is false. |
| D ➥ (i) is false, (ii) is true. |
Show Answer With Best Explanation
| Q22➡ | TOC Let G = (V, T, S, P) be a context-free grammar such that every one of its productions is of the form A → v, with |v| = K > 1. The derivation tree for any W ∈ L(G) has a height h such that. |
| A ➥ logK|W| ≤ h ≤ logK((|W|-1) / k-1) |
| B ➥ logK|W| ≤ h ≤ logK(K|W|) |
| C ➥ logK|W| ≤ h ≤ K logK|W| |
| D ➥ logK|W| ≤ h ≤ ((|W|-1) / k-1) |
Show Answer With Best Explanation
| Q23➡ | TOC Given the following two languages : L1 = {an bn | n ≥ 0, n ≠ 100} L2 = {w ∈ {a, b, c}*| na(w) = nb(w) = nc(w)} Which of the following options is correct ? |
| A ➥ Both L1 and L2 are not context free language |
| B ➥ Both L1 and L2 are context free language. |
| C ➥ L1 is context free language, L2 is not context free language. |
| D ➥ L1 is not context free language, L2 is context free language. |
Show Answer With Best Explanation
| Q24➡ | TOC A recursive function h, is defined as follows : h(m) = k, if m = 0 = 1, if m = 1 = 2 h(m – 1) + 4h(m – 2), if m ≥ 2If the value of h(4) is 88 then the value of k is : |
| A ➥ 0 |
| B ➥ 1 |
| C ➥ 2 |
| D ➥ -1 |
Show Answer With Best Explanation
| Q25➡ | Probability Suppose there are n stations in a slotted LAN. Each station attempts to transmit with a probability P in each time slot. The probability that only one station transmits in a given slot is _. |
| A ➥ nP(1 – P)n – 1 |
| B ➥ nP |
| C ➥ P(1 – P)n – 1 |
| D ➥ nP(1 – P)n – 1 |
Show Answer With Best Explanation
| Q26➡ | CN Station A uses 32 byte packets to transmit messages to station B using sliding window protocol. The round trip delay between A and B is 40 milliseconds and the bottleneck bandwidth on the path between A and B is 64 kbps. The optimal window size of A is_________. |
| A ➥ 20 |
| B ➥ 10 |
| C ➥ 30 |
| D ➥ 40 |
Show Answer With Best Explanation
| Q27➡ | DLD Let G(x) be generator polynomial used for CRC checking. The condition that should be satisfied by G(x) to correct odd numbered error bits, will be: |
| A ➥ (1 + x) is factor of G(x) |
| B ➥ (1 – x) is factor of G(x) |
| C ➥ (1 + x2) is factor of G(x) |
| D ➥ x is factor of G(x) |
Show Answer With Best Explanation
| Q28➡ | CN In a packet switching network, if the message size is 48 bytes and each packet contains a header of 3 bytes. If 24 packets are required to transmit the message, the packet size is __. |
| A ➥ 2 bytes |
| B ➥ 1 bytes |
| C ➥ 4 bytes |
| D ➥ 5 bytes |
Show Answer With Best Explanation
| Q29➡ | CN n RSA public key cryptosystem suppose n = p ∗ q where p and q are primes. (e, n) and (d, n) are public and private keys respectively. Let M be an integer such that o < M < n and φ(n) = (p – 1)(q – 1). Which of the following equations represent RSA public key cryptosystem ? I. C ≡ Me(mod n) M ≡ (C)d(mod n)II. ed ≡ 1(mod n) III. ed ≡ 1(mod φ (n)) IV. C ≡ Me(mod φ (n)) M ≡ Cd(mod φ (n)) |
| A ➥ I and II |
| B ➥ I and III |
| C ➥ II and III |
| D ➥ I and IV |
Show Answer With Best Explanation
| Q30➡ | CN A node X on a 10 Mbps network is regulated by a token bucket. The token bucket is filled at a rate of 2 Mbps. Token bucket is initially filled with 16 megabits. The maximum duration taken by X to transmit at full rate of 10 Mbps is_______ secs. |
| A ➥ 1 |
| B ➥ 2 |
| C ➥ 3 |
| D ➥ 4 |
Show Answer With Best Explanation
| Q31➡ | Algorithms The asymptotic upper bound solution of the recurrence T(n)= 2T(n/2)+(n/lgn) is relation given by |
| A ➥ O(n2) |
| B ➥ O(n lg n) |
| C ➥ O(n lg lg n) |
| D ➥ O(lg lg n) |
Show Answer With Best Explanation
| Q32➡ | Algorithms Any decision tree that sorts n elements has height __. |
| A ➥ Ω(lg n) |
| B ➥ Ω(n) |
| C ➥ Ω(n lg n) |
| D ➥ Ω(n2) |
Show Answer With Best Explanation
| Q33➡ | Algorithms Red-black trees are one of many search tree schemes that are “balanced” in order to guarantee that basic dynamic-set operations take __ time in the worst case. |
| A ➥ O(1) |
| B ➥ O(lg n) |
| C ➥ O(n) |
| D ➥ O(n lg n) |
Show Answer With Best Explanation
| Q34➡ | Algorithms The minimum number of scalar multiplication required, for parenthesization of a matrix-chain product whose sequence of dimensions for four matrices is <5, 10, 3, 12, 5> is |
| A ➥ 630 |
| B ➥ 580 |
| C ➥ 480 |
| D ➥ 405 |
Show Answer With Best Explanation
| Q35➡ |Algorithms Dijkstra’s algorithm is based on |
| A ➥ Divide and conquer paradigm |
| B ➥ Dynamic programming |
| C ➥ Greedy Approach |
| D ➥ Backtracking paradigm |
Show Answer With Best Explanation
Q36➡ |Algorithms  |
| A ➥ a-iii, b-i, c-ii, d-iv |
| B ➥ a-ii, b-i, c-iv, d-iii |
| C ➥ a-ii, b-i, c-iii, d-iv |
| D ➥ b-iii, b-ii, c-i, d-iv |
Show Answer With Best Explanation
| Q37➡ | programming in CPP Abstraction and encapsulation are fundamental principles that underlie the object oriented approach to software development. What can you say about the following two statements ? I. Abstraction allows us to focus on what something does without considering the complexities of how it works. II. Encapsulation allows us to consider complex ideas while ignoring irrelevant detail that would confuse us. |
| A ➥ Neither I nor II is correct. |
| B ➥ Both I and II are correct. |
| C ➥ Only II is correct. |
| D ➥ Only I is correct. |
Show Answer With Best Explanation
| Q38➡ | JAVA Given the array of integers ‘array’ shown below :  What is the output of the following JAVA statements ? int [ ] p = new int [10]; int [ ] q = new int [10]; for (int k = 0; k < 10; k ++) p[k] = array [k];q = p; p[4] = 20; System.out.println (array [4] + “ : ” + q[4]); |
| A ➥ 20 : 20 |
| B ➥ 18 : 18 |
| C ➥ 18 : 20 |
| D ➥ 20 : 18 |
Show Answer With Best Explanation
| Q39➡ | java Consider the following JAVA program : public class First { public static int CBSE (int x) { if (x < 100) x = CBSE (x + 10); return (x – 1); } public static void main (String[] args){ System.out.print(First.CBSE(60)); } } What does this program print ? |
| A ➥ 59 |
| B ➥ 95 |
| C ➥ 69 |
| D ➥ 99 |
Show Answer With Best Explanation
| Q40➡ | JAVA Which of the following statement(s) with regard to an abstract class in JAVA is/are TRUE ? I. An abstract class is one that is not used to create objects. II. An abstract class is designed only to act as a base class to be inherited by other classes. |
| A ➥ Only I |
| B ➥ Only II |
| C ➥ Neither I nor II |
| D ➥ Both I and II |
Show Answer With Best Explanation
| Q41➡ | HTML Which of the following HTML code will affect the vertical alignment of the table content? |
| A ➥ |
| B ➥ |
| C ➥ |
| D ➥ |
Show Answer With Best Explanation
| Q42➡ | XML What can you say about the following statements ? I. XML tags are case-insensitive. II. In JavaScript, identifier names are case-sensitive. III.Cascading Style Sheets (CSS) cannot be used with XML. IV. All well-formed XML documents must contain a document type definition. |
| A ➥ only I and II are false. |
| B ➥ only III and IV are false. |
| C ➥ only I and III are false. |
| D ➥ only II and IV are false. |
Show Answer With Best Explanation
| Q43➡ | Software-Engineering Which of the following statement(s) is/are TRUE with regard to software testing ? I. Regression testing technique ensures that the software product runs correctly after the changes during maintenance. II. Equivalence partitioning is a white-box testing technique that divides the input domain of a program into classes of data from which test cases can be derived. |
| A ➥ only I |
| B ➥ only II |
| C ➥ both I and II |
| D ➥ neither I nor II |
Show Answer With Best Explanation
| Q44➡ | Software-Engineering Which of the following are facts about a top-down software testing approach? I. Top-down testing typically requires the tester to build method stubs. II. Top-down testing typically requires the tester to build test drivers. |
| A ➥ Only I |
| B ➥ Only II |
| C ➥ Both I and II |
| D ➥ Neither I nor II |
Show Answer With Best Explanation
| Q45➡ | Software-Engineering Match the terms related to Software Configuration Management (SCM) in List – I with the descriptions in List – II. 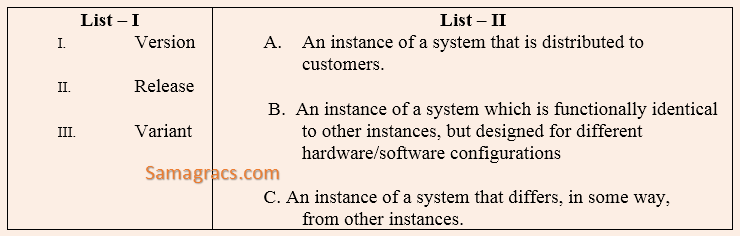 |
| A ➥ I-B, II-C, III-A |
| B ➥ I-C, II-A, III-B |
| C ➥ I-C, II-B, III-A |
| D ➥ I-B, II-A, III-C |
Show Answer With Best Explanation
| Q46➡ | Software-Engineering A software project was estimated at 352 Function Points (FP). A four person team will be assigned to this project consisting of an architect, two programmers, and a tester. The salary of the architect is 80,000 per month, the programmer ₹ 60,000 per month and the tester ₹ 50,000 per month. The average productivity for the team is 8 FP per person month. Which of the following represents the projected cost of the project ? |
| A ➥ ₹ 28,16,000 |
| B ➥ ₹ 20,90,000 |
| C ➥ ₹ 26,95,000 |
| D ➥ ₹ 27,50,000 |
Show Answer With Best Explanation
| Q47➡ | Software-Engineering Complete each of the following sentences in List – I on the left hand side by filling in the word or phrase from the List – II on the right hand side that best completes the sentence : 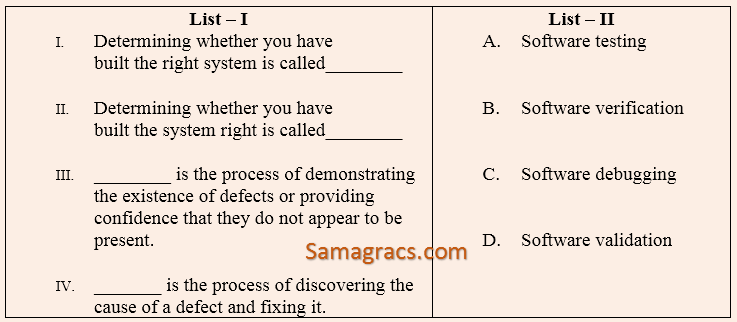 |
| A ➥ I-B, II-D, III-A, IV-C |
| B ➥ I-B, II-D, III-C, IV-A |
| C ➥ I-D, II-B, III-C, IV-A |
| D ➥ I-D, II-B, III-A, IV-C |
Show Answer With Best Explanation
| Q48➡ | Software-Engineering A software company needs to develop a project that is estimated as 1000 function points and is planning to use JAVA as the programming language whose approximate lines of code per function point is accepted as 50. Considering a = 1.4 as multiplicative factor, b = 1.0 as exponential factor for the basic COCOMO effort equation and c = 3.0 as multiplicative factor, d = 0.33 as exponential factor for the basic COCOMO duration equation, approximately how long does the project take to complete ? |
| A ➥ 11.2 months |
| B ➥ 12.2 months |
| C ➥ 13.2 months |
| D ➥ 10.2 months |
Show Answer With Best Explanation
| Q49➡ | Operating-Systems A memory management system has 64 pages with 512 bytes page size. Physical memory consists of 32 page frames. Number of bits required in logical and physical address are respectively: |
| A ➥ 14 and 15 |
| B ➥ 14 and 29 |
| C ➥ 15 and 14 |
| D ➥ 16 and 32 |
Show Answer With Best Explanation
| Q50➡ | Operating-Systems Consider a disk queue with I/O requests on the following cylinders in their arriving order: 6, 10, 12, 54, 97, 73, 128, 15, 44, 110, 34, 45 The disk head is assumed to be at cylinder 23 and moving in the direction of decreasing number of cylinders. Total number of cylinders in the disk is 150. The disk head movement using SCAN-scheduling algorithm is: |
| A ➥ 172 |
| B ➥ 173 |
| C ➥ 227 |
| D ➥ 228 |
Show Answer With Best Explanation
| Q51➡ | Operating-Systems Match the following for Unix file system: 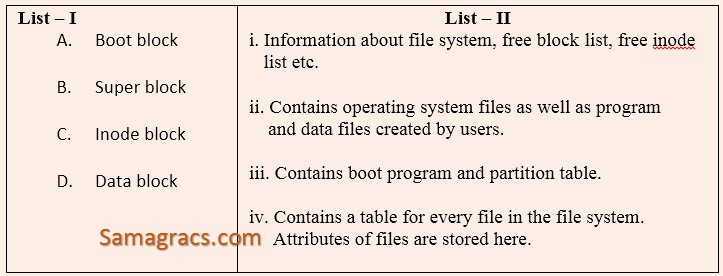 Code: |
| A ➥ A-iii, B-i, C-ii, D-iv |
| B ➥ A-iii, B-i, C-iv, D-ii |
| C ➥ A-iv, B-iii, C-ii, D-i |
| D ➥ A-iv, B-iii, C-i, D-ii |
Show Answer With Best Explanation
| Q52➡ | Operating-System Some of the criteria for calculation of priority of a process are: 1. Processor utilization by an individual process. 2. Weight assigned to a user or group of users. 3. Processor utilization by a user or group of processes In fair share scheduler, priority is calculated based on: |
| A ➥ only (1) and (2) |
| B ➥ only (1) and (3) |
| C ➥ (1), (2) and (3) |
| D ➥ only (2) and (3) |
Show Answer With Best Explanation
| Q53➡ | Operating-System One of the disadvantages of user level threads compared to Kernel level threads is |
| A ➥ If a user level thread of a process executes a system call, all threads in that process are blocked. |
| B ➥ Scheduling is application dependent. |
| C ➥ Thread switching doesn’t require kernel mode privileges. |
| D ➥ The library procedures invoked for thread management in user level threads are local procedures. |
Show Answer With Best Explanation
| Q53➡ | Operating-System Which statement is not correct about “init” process in Unix? |
| A ➥ It is generally the parent of the login shell. |
| B ➥ It has PID 1. |
| C ➥ It is the first process in the system. |
| D ➥ Init forks and execs a ‘getty’ process at every port connected to a terminal. |
Show Answer With Best Explanation
| Q55➡ | Artificial-intelligence Consider following two rules R1 and R2 in logical reasoning in Artificial Intelligence (AI) : R1 : From α ⊃ β and α / Inter β (is known as Modus Tollens (MT) ) R2 : From α ⊃ β and ¬β / Inter ¬α ( is known as Modus Ponens (MP)) |
| A ➥ Only R1 is correct. |
| B ➥ Only R2 is correct. |
| C ➥ Both R1 and R2 are correct. |
| D ➥ Neither R1 nor R2 is correct. |
Show Answer With Best Explanation
| Q56➡ | Artificial-intelligence Consider the following AO graph: 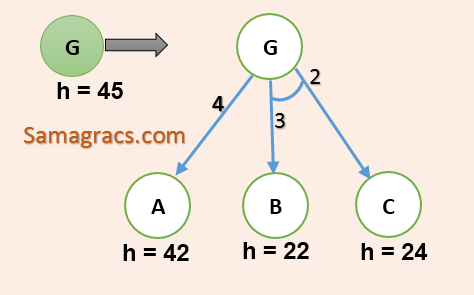 Which is the best node to expand next by AO* algorithm? |
| A ➥ A |
| B ➥ B |
| C ➥ C |
| D ➥ B and C |
Show Answer With Best Explanation
| Q57➡ | Artificial-intelligence In Artificial Intelligence (AI), what is present in the planning graph? |
| A ➥ Sequence of levels |
| B ➥ Literals |
| C ➥ Variables |
| D ➥ Heuristic estimates |
Show Answer With Best Explanation
| Q58➡ | Artificial-intelligence What is the best method to go for the game playing problem? |
| A ➥ Optimal Search |
| B ➥ Random Search |
| C ➥ Heuristic Search |
| D ➥ Stratified Search |
Show Answer With Best Explanation
| Q46➡ | LPP Which of the following statements is true? |
| A ➥ The sentence S is a logical consequence of S1,…., Sn if and only if S1 ∧ S2 ∧…. ∧ Sn → S is satisfiable. |
| B ➥ The sentence S is a logical consequence of S1,…., Sn if and only if S1 ∧ S2 ∧…. ∧ Sn → S is valid. |
| C ➥ The sentence S is a logical consequence of S1,…., Sn if and only if S1 ∧ S2 ∧…. ∧ Sn → S is consistent. |
| D ➥ The sentence S is a logical consequence of S1,…., Sn if and only if S1 ∧ S2 ∧…. ∧ Sn → S is inconsistent. |
Show Answer With Best Explanation
| Q60➡ | Propositional-Logic The first order logic (FOL) statement ((R ∨ Q) ∧ (P ∨ ¬Q)) is equivalent to which of the following ? |
| A ➥ ((R ∨ ¬Q) ∧ (P ∨ ¬Q) ∧ (R ∨ P)) |
| B ➥ ((R ∨ Q) ∧ (P ∨ ¬Q) ∧ (R ∨ P)) |
| C ➥ ((R ∨ Q) ∧ (P ∨ ¬Q) ∧ (R ∨ ¬P)) |
| D ➥ ((R ∨ Q) ∧ (P ∨ ¬Q) ∧ ( ¬R ∨ P)) |
Show Answer With Best Explanation
| Q61➡ | TOC Given the following two statements : A. L = {w|na(w) = nb(w)} is deterministic context free language, but not linear. B. L = {an bn} ∪ {an b2n} is linear, but not deterministic context free language. Which of the following options is correct ? |
| A ➥ Both (A) and (B) are false. |
| B ➥ Both (A) and (B) are true. |
| C ➥ (A) is true, (B) is false. |
| D ➥ (A) is false, (B) is true. |
Show Answer With Best Explanation
| Q62➡ | TOC Which of the following pairs have different expressive power? |
| A ➥ Single-tape-turing machine and multi-dimensional turing machine. |
| B ➥ Multi-tape turing machine and multi-dimensional turing machine. |
| C ➥ Deterministic pushdown automata and non-deterministic pushdown automata. |
| D ➥ Deterministic finite automata and Non-deterministic finite automata |
Show Answer With Best Explanation
| Q63➡ | TOC Which of the following statements is false? |
| A ➥ Every context-sensitive language is recursive. |
| B ➥ The set of all languages that are not recursively enumerable is countable. |
| C ➥ The family of recursively enumerable languages is closed under union. |
| D ➥ The families of recursively enumerable and recursive languages are closed under reversal. |
Show Answer With Best Explanation
| Q64➡ | Number-Systems Let C be a binary linear code with minimum distance 2t + 1 then it can correct upto______bits of error. |
| A ➥ t + 1 |
| B ➥ t |
| C ➥ t – 2 |
| D ➥ t / 2 |
Show Answer With Best Explanation
| Q65➡ | LPP A t-error correcting q-nary linear code must satisfy: 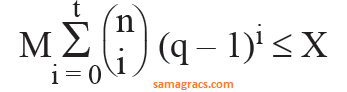 Where M is the number of code words and X is |
| A ➥ qn |
| B ➥ qt |
| C ➥ q-n |
| D ➥ q-t |
Show Answer With Best Explanation
| Q66➡ | Operating-System Names of some of the Operating Systems are given below: (1) MS-DOS (2) XENIX (3) OS/2 In the above list, following operating systems didn’t provide multi user facility. |
| A ➥ (1) only |
| B ➥ (1) and (2) only |
| C ➥ (2) and (3) only |
| D ➥ (1), (2) and (3) |
Show Answer With Best Explanation
| Q67➡ | Image-Processing From the given data below : a b b a a b b a a b which one of the following is not a word in the dictionary created by LZ-coding (the initial words are a, b)? |
| A ➥ a b |
| B ➥ b b |
| C ➥ b a |
| D ➥ b a a b |
Show Answer With Best Explanation
| Q68➡ | LPP With respect to a loop in the transportation table, which one of the following is not correct? |
| A ➥ Every loop has an odd no. of cells and at least 5. |
| B ➥ Closed loops may or may not be square in shape. |
| C ➥ All the cells in the loop that have a plus or minus sign, except the starting cell, must be occupied cells. |
| D ➥ Every loop has an even no. of cells and at least four |
Show Answer With Best Explanation
| Q69➡ | LPP At which of the following stage(s), the degeneracy do not occur in transportation problem ? (m, n represents number of sources and destinations respectively) (1) While the values of dual variables ui and vj cannot be computed. (2) While obtaining an initial solution, we may have less than m + n – 1 allocations. (3) At any stage while moving towards optimal solution, when two or more occupied cells with the same minimum allocation become unoccupied simultaneously. (4) At a stage when the no. of +ve allocation is exactly m + n – 1. |
| A ➥ (a), (b) and (c) |
| B ➥ (a), (c) and (d) |
| C ➥ (a) and (d) |
| D ➥ (a), (b), (c) and (d) |
Show Answer With Best Explanation
| Q70➡ | LPP Consider the following LPP : 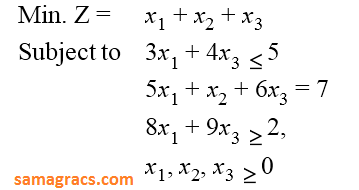 The standard form of this LPP shall be : |
A ➥ 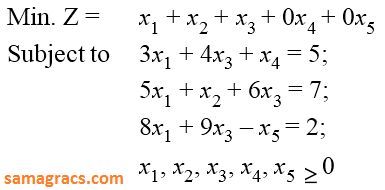 |
B ➥ 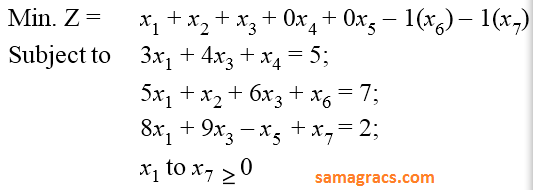 |
C ➥ 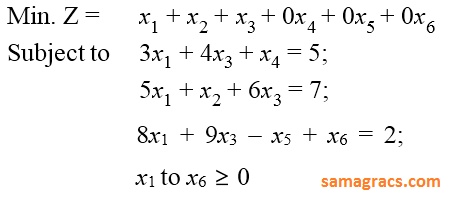 |
D ➥ 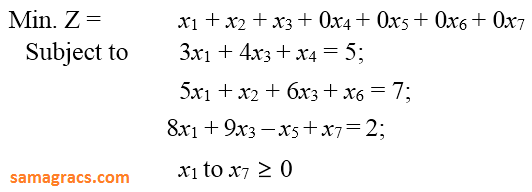 |
Show Answer With Best Explanation
| Q71➡ | Artificial-intelligence Let R and S be two fuzzy relations defined as : 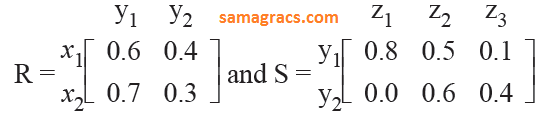 Then, the resulting relation, T, which relates elements of universe x to the elements of universe z using max-min composition is given by : |
A ➥  |
B ➥ 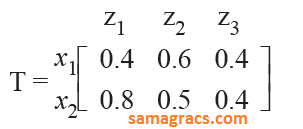 |
C ➥ 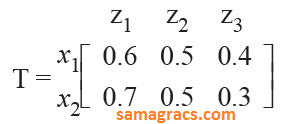 |
D ➥ 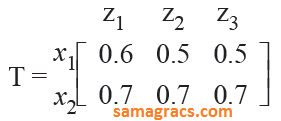 |
Show Answer With Best Explanation
| Q72➡ | Artificial-intelligence A neuron with 3 inputs has the weight vector [0.2 –0.1 0.1]T and a bias θ = 0. If the input vector is X = [0.2 0.4 0.2]T then the total input to the neuron is : |
| A ➥ 0.20 |
| B ➥ 1.0 |
| C ➥ 0.02 |
| D ➥ –1.0 |
Show Answer With Best Explanation
| Q73➡ | Artificial-intelligence Which of the following neural networks uses supervised learning ? (1) Multilayer perceptron (2) Self organizing feature map (3) Hopfield network |
| A ➥ (1) only |
| B ➥ (2) only |
| C ➥ (1) and (2) only |
| D ➥ (1) and (3) only |
Show Answer With Best Explanation
| Q74➡ | UNIX-OS Unix command to change the case of first three lines of file “shortlist” from lower to upper |
| A ➥ $ tr ‘[a – z]’ ‘[A – Z]’ shortlist ¦ head-3 |
| B ➥ $ head -3 shortlist ¦ tr ‘[a – z]’ ‘[A – Z]’ |
| C ➥ $ tr head -3 shortlist ‘[A – Z]’ ‘[a – z]’ |
| D ➥ $ tr shortlist head -3 ‘[a – z]’ ‘[A – Z]’ |
Show Answer With Best Explanation
| Q75➡ | UNIX OS Match the following vi commands in Unix:  |
| A ➥ a-ii, b-iii, c-i, d-iv |
| B ➥ a-iv, b-iii, c-ii, d-i |
| C ➥ a-iii, b-iv, c-i, d-ii |
| D ➥ a-iii, b-i, c-iv, d-ii |
