 UGC NET June-2018
UGC NET June-2018
| Q1➡ The definitions in an XML document are said to be __ when the tagging system and definitions in the DTD are all in compliance. |
| A ➥ well-formed |
| B ➥ reasonable |
| C ➥ valid |
| D ➥ logical |
Show Answer With Best Explanation
| Q2➡ Consider the JavaScript Code : var y= ’’12”; function f( ) { var y=’’6”; alert (this.y); function g( ) {alert (y); } g( ); } f( ); If M is the number of alert dialog boxes generated by this JavaScript code and D1, D2, ……, DM represents the content displayed in each of the M dialog boxes, then |
| A ➥ M=3; D1 displays ”12”; D2 displays ”6”; D3 displays ”12”. |
| B ➥ M=3; D1 displays ”6”; D2 displays ”12”; D3 displays ”6”. |
| C ➥ M=2; D1 displays ”6”; D2 displays ”12”. |
| D ➥ M=2; D1 displays ”12”; D2 displays ”6”. |
Show Answer With Best Explanation
| Q3➡ What is the output of the following JAVA program ? class simple { public static void main(String[ ] args) { simple obj = new simple( ); obj.start( ); } void start( ) { long [ ] P= {3, 4, 5}; long [ ] Q= method (P); System.out.print (P[0] + P[1] + P[2]+”:”); System.out.print (Q[0] + Q[1] + Q[2]); } long [ ] method (long [ ] R) { R [1]=7; return R; } } //end of class |
| A ➥ well-formed |
| B ➥ 12 : 12 |
| C ➥ 15 : 12 |
| D ➥ 15 : 15 |
Show Answer With Best Explanation
| Q4➡ What is the output of the following ‘C’ program ? (Assuming little – endian representation of multi-byte data in which Least Significant Byte (LSB) is stored at the lowest memory address.) include include /* Assume short int occupies two bytes of storage / int main ( ) { union saving { short int one; char two[2]; }; union saving m; m.two [0] = 5; m.two [1] = 2; printf(’’%d, %d, %d\n”, m.two [0], m.two [1], m.one); }/ end of main */ |
| A ➥ 5, 2, 1282 |
| B ➥ 5, 2, 52 |
| C ➥ 5, 2, 25 |
| D ➥ 5, 2, 517 |
Show Answer With Best Explanation
| Q5➡ Given below are three implementations of the swap( ) function in C++ : 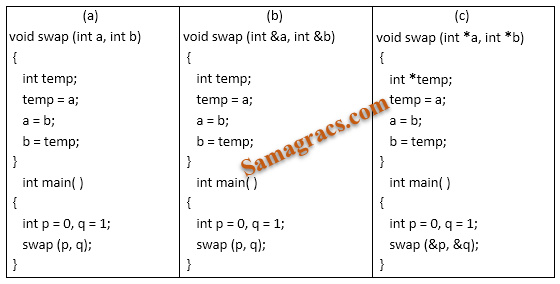 Which of these would actually swap the contents of the two integer variables p and q ? |
| A ➥ (a) only |
| B ➥ (b) only |
| C ➥ (c) only |
| D ➥ (b) and (c) only |
Show Answer With Best Explanation
| Q6➡ In Java, which of the following statements is/are True ? S1 : The ‘final’ keyword applied to a class definition prevents the class from being extended through derivation. S2 : A class can only inherit one class but can implement multiple interfaces. S3 : Java permits a class to replace the implementation of a method that it has inherited. It is called method overloading. Code: |
| A ➥ S1 and S2 only |
| B ➥ S1 and S3 only |
| C ➥ S2 and S3 only |
| D ➥ All of S1, S2 and S3 |
Show Answer With Best Explanation
| Q7➡ Which of the following statements is/are True ? P : C programming language has a weak type system with static types. Q : Java programming language has a strong type system with static types. Code: |
| A ➥ P only |
| B ➥ Q only |
| C ➥ Both P and Q |
| D ➥ Neither P nor Q |
Show Answer With Best Explanation
| Q8➡ | Computer Graphics A graphic display system has a frame buffer that is 640 pixels wide, 480 pixels high and 1 bit of color depth. If the access time for each pixel on the average is 200 nanoseconds, then the refresh rate of this frame buffer is approximately : |
| i ➥ 16 frames per second |
| ii ➥ 19 frames per second |
| iii ➥ 21 frames per second |
| iv ➥ 23 frames per second |
Show Answer With Best Explanation
| i ➥ S1 only |
| ii ➥ S2 only |
| iii ➥ Both S1 and S2 |
| iv ➥ Neither S1 Nor S2 |
Show Answer With Best Explanation
| Q10➡ | Computer Graphics Consider the matrix 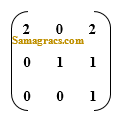 representing a set of planar (2D) geometric transformations in homogeneous coordinates. Which of the following statements about the matrix M is True ? |
| i ➥ M represents first, a scaling of vector (2, 1) followed by translation of vector (1, 1) |
| ii ➥ M represents first, a translation of vector (1, 1) followed by scaling of vector (2, 1) |
| iii ➥ M represents first, a scaling of vector (3, 1) followed by shearing of parameters (−1, 1) |
| iv ➥ M represents first, a shearing of parameters (−1, 1) followed by scaling of vector (3, 1) |
Show Answer With Best Explanation
| Q11➡ Assume the following regarding the development of a software system P: ➤ Estimated lines of code of P : 33, 480 LOC ➤ Average productivity for P : 620 LOC per person-month ➤ Number of software developers : 6 ➤ Average salary of a software developer : 50,000 per month If E, D and C are the estimated development effort (in person-months), estimated development time (in months), and estimated development cost (in Lac) respectively, then (E, D, C) =__________ |
| A ➥ (48, 8, 24) |
| B ➥ (54, 9, 27) |
| C ➥ (60, 10, 30) |
| D ➥ (42, 7, 21) |
Show Answer With Best Explanation
Q12➡ 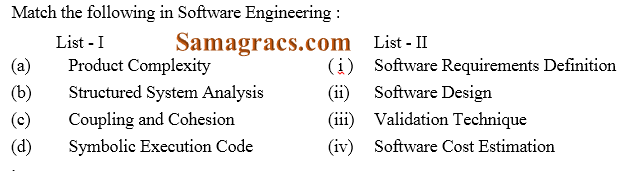 |
| A ➥ (a)-(ii), (b)-(iii), (c)-(iv), (d)-(i) |
| B ➥ (a)-(iii), (b)- (i), (c)-(iv), (d)-(ii) |
| C ➥ (a)-(iv), (b)- (i), (c)-(ii), (d)-(iii) |
| D ➥ (a)-(iii), (b)- (iv), (c)-(i), (d)-(ii) |
Show Answer With Best Explanation
| Q13➡ Which one of the following is not typically provided by Source Code Management Software ? |
| A ➥ Synchronisation |
| B ➥ Versioning and Revision history |
| C ➥ Syntax highlighting |
| D ➥ Project forking |
Show Answer With Best Explanation
| Q14➡ A software system crashed 20 times in the year 2017 and for each crash, it took 2 minutes to restart. Approximately, what was the software availability in that year ? |
| A ➥ 96.9924% |
| B ➥ 97.9924% |
| C ➥ 98.9924% |
| D ➥ 99.9924% |
Show Answer With Best Explanation
| Q15➡ Match the 5 CMM Maturity levels/CMMI staged representations in List- I with their characterizations in List-II :  |
| A ➥ (a)-(iv), (b)-(v), (c)-(i), (d)-(iii), (e)-(ii) |
| B ➥ (a)-(i), (b)-(ii), (c)-(iv), (d)-(v), (e)-(iii) |
| C ➥ (a)-(v), (b)-(iv), (c)-(ii), (d)-(iii), (e)-(i) |
| D ➥ (a)- (iv), (b)-(v), (c)-(ii), (d)-(iii), (e)-(i) |
Show Answer With Best Explanation
| Q16➡ Coupling is a measure of the strength of the interconnections between software modules. Which of the following are correct statements with respect to module coupling ? P : Common coupling occurs when one module controls the flow of another module by passing it information on what to do. Q : In data coupling, the complete data structure is passed from one module to another through parameters. R : Stamp coupling occurs when modules share a composite data structure and use only parts of it. |
| A ➥ P and Q only |
| B ➥ P and R only |
| C ➥ Q and R only |
| D ➥ All of P, Q and R |
Show Answer With Best Explanation
| Q17➡ A software design pattern often used to restrict access to an object is : |
| A ➥ adapter |
| B ➥ decorator |
| C ➥ delegation |
| D ➥ proxy |
Show Answer With Best Explanation
| Q18➡ Reasons to re-engineer a software include : P : Allow legacy software to quickly adapt to the changing requirements Q : Upgrade to newer technologies/platforms/paradigm (for example, object-oriented) R : Improve software maintainability S : Allow change in the functionality and architecture of the software |
| A ➥ P, R and S only |
| B ➥ P and R only |
| C ➥ P, Q and S only |
| D ➥ P, Q and R only |
Show Answer With Best Explanation
| Q19➡ Which of the following is not a key strategy followed by the clean room approach to software development ? |
| A ➥ Formal specification |
| B ➥ Dynamic verification |
| C ➥ Incremental development |
| D ➥ Statistical testing of the system |
Show Answer With Best Explanation
| Q20➡ Which of the following statements is/are True ? P : Refactoring is the process of changing a software system in such a way that it does not alter the external behavior of the code yet improves the internal architecture. Q : An example of refactoring is adding new features to satisfy a customer requirement discovered after a project is shipped. |
| A ➥ A P only |
| B ➥ Q only |
| C ➥ Both P and Q |
| D ➥ Neither P nor Q |
Show Answer With Best Explanation
| Q21➡ The solution of the recurrence relation T(m)=T(3m/4)+1 is : |
| A ➥ θ(lg m) |
| B ➥ θ(m) |
| C ➥ θ(mlg m) |
| D ➥ θ(lglg m) |
Show Answer With Best Explanation
| Q22➡ Consider the array A=<4, 1, 3, 2, 16, 9, 10, 14, 8, 7>. After building heap from the array A, the depth of the heap and the right child of max-heap are__________ and __ respectively. (Root is at level 0). |
| A ➥ 3, 14 |
| B ➥ 3, 10 |
| C ➥ 4, 14 |
| D ➥ 4, 10 |
Show Answer With Best Explanation
| Q23➡ A hash function h defined h(key)=key mod 7, with linear probing, is used to insert the keys 44, 45, 79, 55, 91, 18, 63 into a table indexed from 0 to 6. What will be the location of key 18 ? |
| A ➥ 3 |
| B ➥ 4 |
| C ➥ 5 |
| D ➥ 6 |
Show Answer With Best Explanation
| Q24➡ Which of the following algorithms solves the single-source shortest paths ? |
| A ➥ Prim’s algorithm |
| B ➥ Floyd – Warshall algorithm |
| C ➥ Johnson’s algorithm |
| D ➥ Dijkstra’s algorithm |
Show Answer With Best Explanation
| Q25➡ A text is made up of the characters A, B, C, D, E each occurring with the probability 0.08, 0.40, 0.25, 0.15 and 0.12 respectively. The optimal coding technique will have the average length of : |
| A ➥ 2.4 |
| B ➥ 1.87 |
| C ➥ 3.0 |
| D ➥ 2.15 |
Show Answer With Best Explanation
| Q26➡ A binary search tree in which every non-leaf node has non-empty left and right subtrees is called a strictly binary tree. Such a tree with 19 leaves : |
| A ➥ cannot have more than 37 nodes |
| B ➥ has exactly 37 nodes |
| C ➥ has exactly 35 nodes |
| D ➥ cannot have more than 35 nodes |
Show Answer With Best Explanation
Q27➡ Code: |
| A ➥ (a)-(iv),(b)-(i), (c)-(iii), (d)-(ii) |
| B ➥ (a)-(iv),(b)-(iii), (c)-(i), (d)-(ii) |
| C ➥ (a)-(iii),(b)-(iv), (c)-(ii), (d)-(i) |
| D ➥ (a)-(iv),(b)-(iii), (c)-(ii), (d)-(i) |
Show Answer With Best Explanation
| Q28➡ The maximum number of comparisons needed to sort 9 items using radix sort is (assume each item is 5 digit octal number) : |
| A ➥ 45 |
| B ➥ 72 |
| C ➥ 360 |
| D ➥ 450 |
Show Answer With Best Explanation
| Q29➡ A 5-ary tree is tree in which every internal node has exactly 5 children. The number of left nodes in such a tree with 8 internal nodes will be : |
| A ➥ 30 |
| B ➥ 33 |
| C ➥ 45 |
| D ➥ 125 |
Show Answer With Best Explanation
| Q30➡ Consider a Boolean function of ‘n’ variables. The order of an algorithm that determines whether the Boolean function produces a output 1 is : |
| A ➥ Logarithmic |
| B ➥ Linear |
| C ➥ Quadratic |
| D ➥ Exponential |
Show Answer With Best Explanation
| Q31➡ Two finite state machines are said to be equivalent if they : |
| A ➥ Have the same number of edges |
| B ➥ Have the same number of states |
| C ➥ Recognize the same set of tokens |
| D ➥ Have the same number of states and edges |
Show Answer With Best Explanation
| Q32➡ The finite state machine given in figure below recognizes : 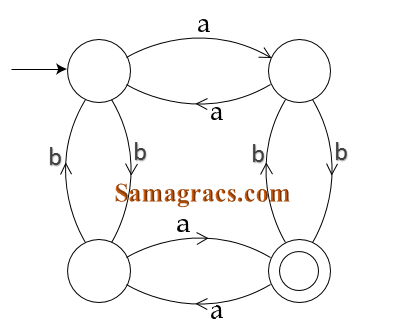 |
| A ➥ any string of odd number of a’s |
| B ➥ any string of odd number of b’s |
| C ➥ any string of even number of a’s and odd number of b’s |
| D ➥ any string of odd number of a’s and odd number of b’s |
Show Answer With Best Explanation
| Q33➡ A pushdown automata behaves like a Turing machine when the number of auxiliary memory is : |
| A ➥ 0 |
| B ➥ 1 |
| C ➥ 1 or more |
| D ➥ 2 or more |
Show Answer With Best Explanation
| Q34➡ Pushdown automata can recognize language generated by . |
| A ➥ Only context free grammar |
| B ➥ Only regular grammar |
| C ➥ Context free grammar or regular grammar |
| D ➥ Only context sensitive grammar |
Show Answer With Best Explanation
| Q35➡ To obtain a string of n Terminals from a given Chomsky normal form grammar, the number of productions to be used is : |
| A ➥ 2n−1 |
| B ➥ 2n |
| C ➥ n+1 |
| D ➥ n 2 |
Show Answer With Best Explanation
| Q36➡ Consider the following two Grammars : G1 : S → SbS|a G2 : S → aB|ab, A→GAB|a, B→ABb|b Which of the following option is correct ? |
| A ➥ Only G1 is ambiguous |
| B ➥ Only G2 is ambiguous |
| C ➥ Both G1 and G2 are ambiguous |
| D ➥ Both G1 and G2 are not ambiguous |
Show Answer With Best Explanation
| Q37➡ Context sensitive language can be recognized by a : |
| A ➥ Finite state machine |
| B ➥ Deterministic finite automata |
| C ➥ Non-deterministic finite automata |
| D ➥ Linear bounded automata |
Show Answer With Best Explanation
| Q38➡ The set A={ 0n 1n 2n | n=1, 2, 3, ……… } is an example of a grammar that is : |
| A ➥ Context sensitive |
| B ➥ Context free |
| C ➥ Regular |
| D ➥ None of the above |
Show Answer With Best Explanation
| Q39➡ A bottom-up parser generates : |
| A ➥ Leftmost derivation in reverse |
| B ➥ Right-most derivation in reverse |
| C ➥ Left-most derivation |
| D ➥ Right-most derivation |
Show Answer With Best Explanation
| Q40➡ Consider the following statements( ) : S1 : There exists no algorithm for deciding if any two Turing machines M1 and M2 accept the same language. S2 : The problem of determining whether a Turing machine halts on any input is undecidable. Which of the following options is correct ? |
| A ➥ Both S1 and S2 are correct |
| B ➥ Both S1 and S2 are not correct |
| C ➥ Only S1 is correct |
| D ➥ Only S2 is correct |
Show Answer With Best Explanation
| Question 41➡ | Computer Network A slotted ALOHA network transmits 200-bit frames using a shared channel with a 200 Kbps bandwidth. Find the throughput of the system, if the system (all stations put together) produces 250 frames per second: |
| i ➥ 49 |
| ii ➥ 368 |
| iii ➥ 149 |
| iv ➥ 151 |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Access Control | Help-Line |
| Question 42➡ | Computer Network The period of a signal is 100 ms. Its frequency is: |
| i ➥ 1003 Hertz |
| ii ➥ 10−2 KHz |
| iii ➥ 10−3 KHz |
| iv ➥ 105 Hertz |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Numerical | Help-Line |
| Question 43➡ | Computer Network The dotted-decimal notation of the following IPV4 address in binary notation is . 10000001 00001011 00001011 11101111 |
| i ➥ 111.56.45.239 |
| ii ➥ 129.11.10.238 |
| iii ➥ 129.11.11.239 |
| iv ➥ 111.56.11.239 |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | IP Address | Help-Line |
| Question 44➡ | Computer Network Which of the following statements are true ? (I) Advanced Mobile Phone System (AMPS) is a second generation cellular phone system. (II) IS – 95 is a second generation cellular phone system based on CDMA and DSSS. (III) The Third generation cellular phone system will provide universal personnel communication. |
| i ➥ (a) and (b) only |
| ii ➥ (b) and (c) only |
| iii ➥ (a), (b) and (c) |
| iv ➥ (a) and (c) only |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Cellular System | Help-Line |
| Question 45➡ | Computer Network Match the following symmetric block ciphers with corresponding block and key sizes : 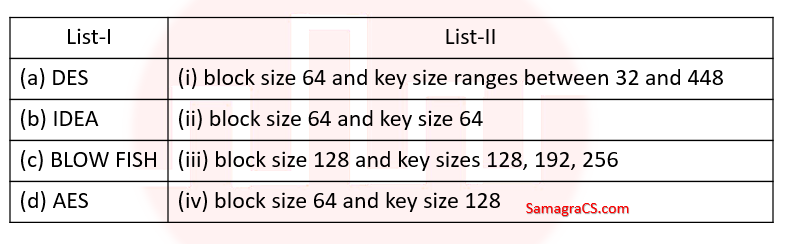 |
| i ➥ (a)-(iv), (b)-(ii), (c)-(i), (d)-(iii) |
| ii ➥ (a)-(ii), (b)-(iv), (c)-(i), (d)-(iii) |
| iii ➥ (a)-(ii), (b)-(iv), (c)-(iii), (d)-(i) |
| iv ➥ (a)-(iv), (b)-(ii), (c)-(iii), (d)-(i) |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Network Security | Help-Line |
| Question 46➡ | Computer Network Which of the following statements are true ? (a) Three broad categories of Networks are (i) Circuit Switched Networks (ii) Packet Switched Networks (iii) Message Switched Networks (b) Circuit Switched Network resources need not be reserved during the set up phase. (c) In packet switching there is no resource allocation for packets. Code: |
| i ➥ (a) and (b) only |
| ii ➥ (b) and (c) only |
| iii ➥ (a) and (c) only |
| iv ➥ (a), (b) and (C) |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Switching | Help-Line |
| Question 47➡ | Computer Network In Challenge-Response authentication the claimant__________ |
| i ➥ Proves that she knows the secret without revealing it |
| ii ➥ Proves that she doesn’t know the secret |
| iii ➥ Reveals the secret |
| iv ➥ Gives a challenge |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Network Security | Help-Line |
| Question 48➡ | Computer Network Decrypt the message “WTAAD” using the Caesar Cipher with key=15. |
| i ➥ LIPPS |
| ii ➥ HELLO |
| iii ➥ OLLEH |
| iv ➥ DAATW |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Network Security | Help-Line |
| Question 49➡ | Computer Network To guarantee correction of upto t errors, the minimum Hamming distance dmin in a block code must be__________. |
| i ➥ t+1 |
| ii ➥ t−2 |
| iii ➥ 2t−1 |
| iv ➥ 2t+1 |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Hamming Distance | Help-Line |
| Question 50➡ | Computer Network Encrypt the Message “HELLO MY DEARZ” using Transposition Cipher with  |
| i ➥ HLLEO YM AEDRZ |
| ii ➥ EHOLL ZYM RAED |
| iii ➥ ELHL MDOY AZER |
| iv ➥ ELHL DOMY ZAER |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Network Security | Help-Line |
| Q51➡ At a particular time of computation, the value of a counting semaphore is 10. Then 12 P operations and “x” V operations were performed on this semaphore. If the final value of semaphore is 7, x will be : |
| A ➥ 8 |
| B ➥ 9 |
| C ➥ 11 |
| D ➥ 10 |
Show Answer With Best Explanation
| Q52➡ In a paged memory, the page hit ratio is 0.40. The time required to access a page in secondary memory is equal to 120 ns. The time required to access a page in primary memory is 15 ns. The average time required to access a page is . |
| A ➥ 105 |
| B ➥ 68 |
| C ➥ 75 |
| D ➥ 78 |
Show Answer With Best Explanation
| Q53➡ In a multi-user operating system, 30 requests are made to use a particular resource per hour, on an average. The probability that no requests are made in 40 minutes, when arrival pattern is a poisson distribution, is __________ |
| A ➥ e-15 |
| B ➥ 1-e-15 |
| C ➥ 1-e-20 |
| D ➥ e-20 |
Show Answer With Best Explanation
| Q54➡ Normally user programs are prevented from handling I/O directly by I/O instructions in them. For CPUs having explicit I/O instructions, such I/O protection is ensured by having the I/O instructions privileged. In a CPU with memory mapped I/O, there is no explicit I/O instruction. Which one of the following is true for a CPU with memory mapped I/O ? |
| A ➥ I/O protection is ensured by operating system routines. |
| B ➥ I/O protection is ensured by a hardware trap. |
| C ➥ I/O protection is ensured during system configuration. |
| D ➥ I/O protection is not possible. |
Show Answer With Best Explanation
| Q55➡ Which UNIX/Linux command is used to make all files and sub-directories in the directory “progs” executable by all users ? |
| A ➥ chmod− R a+x progs |
| B ➥ chmod −R 222 progs |
| C ➥ chmod−X a+x progs |
| D ➥ chmod −X 222 progs |
Show Answer With Best Explanation
| Q56➡ Which of the following statements are true ? (i) External Fragmentation exists when there is enough total memory space to satisfy a request but the available space is contiguous. (ii) Memory Fragmentation can be internal as well as external. (iii) One solution to external Fragmentation is compaction. Code: |
| A ➥ (a) and (b) only |
| B ➥ (a) and (c) only |
| C ➥ (b) and (c) only |
| D ➥ (a), (b) and (c) |
Show Answer With Best Explanation
| Q57➡ Page information in memory is also called as Page Table. The essential contents in each entry of a page table is/are . |
| A ➥ Page Access information |
| B ➥ Virtual Page number |
| C ➥ Page Frame number |
| D ➥ Both virtual page number and Page Frame Number |
Show Answer With Best Explanation
| Q58➡ Consider a virtual page reference string 1, 2, 3, 2, 4, 2, 5, 2, 3, 4. Suppose LRU page replacement algorithm is implemented with 3 page frames in main memory. Then the number of page faults are . |
| A ➥ 5 |
| B ➥ 7 |
| C ➥ 9 |
| D ➥ 10 |
Show Answer With Best Explanation
| Q59➡ Consider the following three processes with the arrival time and CPU burst time given in milliseconds : 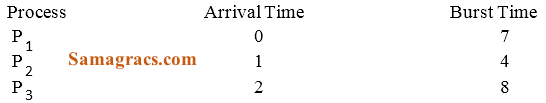 The Gantt Chart for preemptive SJF scheduling algorithm is |
A ➥ 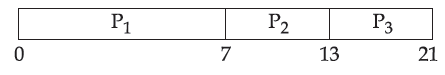 |
B ➥ 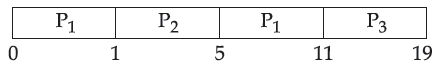 |
C ➥ 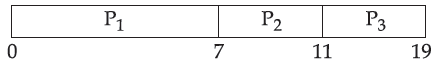 |
D ➥ 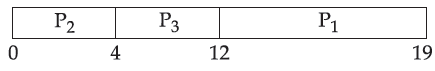 |
Show Answer With Best Explanation
| Q60➡ In which of the following scheduling criteria, context switching will never take place ? |
| A ➥ ROUND ROBIN |
| B ➥ Preemptive SJF |
| C ➥ Non-preemptive SJF |
| D ➥ Preemptive priority |
Show Answer With Best Explanation
| Q61➡ In RDBMS, which type of Join returns all rows that satisfy the join condition ? |
| A ➥ Inner Join |
| B ➥ Outer Join |
| C ➥ Semi Join |
| D ➥ Anti Join |
Show Answer With Best Explanation
| Q62➡ Consider a relation book(title, price) which contains the titles and prices of different books. Assuming that no two books have the same price, what does the following SQL query list ? SELECT title FROM book AS B WHERE(SELECT COUNT(*) FROM book AS T WHERE T.price > B.price) < 7 |
| A ➥ Titles of the six most expensive books. |
| B ➥ Title of the sixth most expensive books. |
| C ➥ Titles of the seven most expensive books. |
| D ➥ Title of the seventh most expensive books. |
Show Answer With Best Explanation
| Q63➡ In a Hierarchical database, a hashing function is used to locate the________ |
| A ➥ Collision |
| B ➥ Root |
| C ➥ Foreign Key |
| D ➥ Records |
Show Answer With Best Explanation
| Q64➡ Relations produced from E-R Model will always be in________ |
| A ➥ 1 NF |
| B ➥ 2 NF |
| C ➥ 3 NF |
| D ➥ 4 NF |
Show Answer With Best Explanation
| Q65➡ Consider the following schedules involving two transactions. S1: r1(X) ; r1(Y) ; r2(X) ; r2(Y) ; w2(Y) ; w1(X) S2 : r1(X) ; r2(X) ; r2(Y) ; w2(Y) ; r1(Y) ; w1(X) Which one of the following statements is correct with respect to above ? |
| A ➥ Both S1 and S2 are conflict serializable. |
| B ➥ Both S1 and S2 are not conflict serializable. |
| C ➥ S1 is conflict serializable and S2 is not conflict serializable. |
| D ➥ S1 is not conflict serializable and S2 is conflict serializable. |
Show Answer With Best Explanation
| Q66➡ For a database relation R(a, b, c, d) where the domains of a, b, c and d include only atomic values, and only the following functional dependencies and those that can be inferred from them hold : a → c b → d The relation is in______ |
| A ➥ First normal form but not in second normal form |
| B ➥ Second normal form but not in third normal form |
| C ➥ Third normal form |
| D ➥ BCNF |
Show Answer With Best Explanation
| Q67➡ A many-to-one relationship exists between entity sets r1 and r2. How will it be represented using functional dependencies if Pk(r) denotes the primary key attribute of relation r? |
| A ➥ Pk(r1 ) → Pk(r2 ) |
| B ➥ Pk(r2 ) → Pk(r1 ) |
| C ➥ Pk(r2 ) → Pk(r1 ) and Pk(r1 ) → Pk(r2 ) |
| D ➥ Pk(r2 ) → Pk(r1 ) or Pk(r1 ) → Pk(r2 ) |
Show Answer With Best Explanation
| Q68➡ Database systems that store each relation in a separate operating system file may use the operating system’s authorization scheme, instead of defining a special scheme themselves. In this case, which of the following is false ? |
| A ➥ The administrator enjoys more control on the grant option. |
| B ➥ It is difficult to differentiate among the update, delete and insert authorizations. |
| C ➥ Cannot store more than one relation in a file |
| D ➥ Operations on the database are speeded up as the authorization procedure is carried out at the operating |
Show Answer With Best Explanation
| Q69➡ Let R1(a,b,c) and R2(x,y,z) be two relations in which a is the foreign key of R1 that refers to the primary key of R2 . Consider following four options. (i) Insert into R1 (ii) Insert into R2 (iii) Delete from R1 (iv) Delete from R2 Which of the following is correct about the referential integrity constraint with respect to above ? |
| A ➥ Operations (a) and (b) will cause violation. |
| B ➥ Operations (b) and (c) will cause violation. |
| C ➥ Operations (c) and (d) will cause violation. |
| D ➥ Operations (d) and (a) will cause violation. |
Show Answer With Best Explanation
| Q70➡ Consider a hash table of size seven, with starting index zero, and a hash function (7x+3) mod 4. Assuming the hash table is initially empty, which of the following is the contents of the table when the sequence 1, 3, 8, 10 is inserted into the table using closed hashing ? Here “__ ” denotes an empty location in the table. |
| A ➥ 3, 10, 1, 8,__,___,__ |
| B ➥ 1, 3, 8, 10,__,___,__ |
| C ➥ 1,__,3,__,8,__,10 |
| D ➥ 3,10,___,___,8,___,___, |
Show Answer With Best Explanation
| Q71➡ In Artificial Intelligence (AI), an environment is uncertain if it is________ |
| A ➥ Not fully observable and not deterministic |
| B ➥ Not fully observable or not deterministic |
| C ➥ Fully observable but not deterministic |
| D ➥ Not fully observable but deterministic |
Show Answer With Best Explanation
| Q72➡ In Artificial Intelligence (AI), a simple reflex agent selects actions on the basis of_______ |
| A ➥ current percept, completely ignoring rest of the percept history. |
| B ➥ rest of the percept history, completely ignoring current percept. |
| C ➥ both current percept and complete percept history. |
| D ➥ both current percept and just previous percept. |
Show Answer With Best Explanation
| Q73➡ In heuristic search algorithms in Artificial Intelligence (AI), if a collection of admissible heuristics h1 …….hm is available for a problem and none of them dominates any of the others, which should we choose ? |
| A ➥ h(n)=max{h1 (n),….,hm(n)} |
| B ➥ h(n)=min{h1 (n),….,hm(n)} |
| C ➥ h(n)=avg{h1 (n),….,hm(n)} |
| D ➥ h(n)=sum{h1 (n),….,hm(n)} |
Show Answer With Best Explanation
| Q74➡ Consider following sentences regarding A, an informed search strategy in Artificial Intelligence (AI). (A) A expands all nodes with f(n) < C*. (B) A expands no nodes with f(n) /C*. (C) Pruning is integral to A*. Here, C* is the cost of the optimal solution path. Which of the following is correct with respect to the above statements ? |
| A ➥ Both statement (a) and statement (b) are true. |
| B ➥ Both statement (a) and statement (c) are true. |
| C ➥ Both statement (b) and statement (c) are true. |
| D ➥ All the statements (a), (b) and (c) are true. |
Show Answer With Best Explanation
| Q75➡ Consider a vocabulary with only four propositions A, B, C and D. How many models are there for the following sentence ? |
| A ➥ 10 |
| B ➥ 12 |
| C ➥ 15 |
| D ➥ 16 |
Show Answer With Best Explanation
| Q76➡ Consider the following statements : (A) False |= True (B) If α |= (β ∧ γ) then α |= β and α |= γ. Which of the following is correct with respect to the above statements ? |
| A ➥ Both statement (a) and statement (b) are false. |
| B ➥ Statement (a) is true but statement (b) is false. |
| C ➥ Statement (a) is false but statement (b) is true. |
| D ➥ Both statement (a) and statement (b) are true. |
Show Answer With Best Explanation
| Q77➡ Consider the following English sentence : “Agra and Gwalior are both in India”. A student has written a logical sentence for the above English sentence in First-Order Logic using predicate In(x, y), which means x is in y, as follows : In(Agra, India) ⋁ In(Gwalior, India) Which one of the following is correct with respect to the above logical sentence ? |
| A ➥ It is syntactically valid but does not express the meaning of the English sentence. |
| B ➥ It is syntactically valid and expresses the meaning of the English sentence also. |
| C ➥ It is syntactically invalid but expresses the meaning of the English sentence. |
| D ➥ It is syntactically invalid and does not express the meaning of the English sentence. |
Show Answer With Best Explanation
| Q78➡ Consider the following two sentences : (I) The planning graph data structure can be used to give a better heuristic for a planning problem. (II) Dropping negative effects from every action schema in a planning problem results in a relaxed problem. Which of the following is correct with respect to the above sentences ? |
| A ➥ Both sentence (a) and sentence (b) are false. |
| B ➥ Both sentence (a) and sentence (b) are true. |
| C ➥ Sentence (a) is true but sentence (b) is false |
| D ➥ Sentence (a) is false but sentence (b) is true. |
Show Answer With Best Explanation
| Q79➡ A knowledge base contains just one sentence, ∃x AsHighAs (x, Everest). Consider the following two sentences obtained after applying existential instantiation. (I) AsHighAs (Everest, Everest) (II) AsHighAs (Kilimanjaro, Everest) Which of the following is correct with respect to the above sentences ? |
| A ➥ Both sentence (a) and sentence (b) are sound conclusions. |
| B ➥ Both sentence (a) and sentence (b) are unsound conclusions |
| C ➥ Sentence (a) is sound but sentence (b) is unsound. |
| D ➥ Sentence (a) is unsound but sentence (b) is sound. |
Show Answer With Best Explanation
| Q80➡ Consider the set of all possible five-card poker hands dealt fairly from a standard deck of fifty-two cards. How many atomic events are there in the joint probability distribution ? |
| A ➥ 2,598,960 |
| B ➥ 3,468,960 |
| C ➥ 3,958,590 |
| D ➥ 2,645,590 |
Show Answer With Best Explanation
| Q81➡ E is the number of edges in the graph and f is maximum flow in the graph. When the capacities are integers, the runtime of Ford-Fulkerson algorithm is bounded by : |
| A ➥ O(E∗f) |
| B ➥ O(E2 ∗ f) |
| C ➥ O(E ∗ f2 ) |
| D ➥ O(E2 ∗ f2 ) |
Show Answer With Best Explanation
| Q82➡ Which of the following statements is false about convex minimization problem ? |
| A ➥ If a local minimum exists, then it is a global minimum |
| B ➥ The set of all global minima is convex set |
| C ➥ The set of all global minima is concave set |
| D ➥ For each strictly convex function, if the function has a minimum, then the minimum is unique |
Show Answer With Best Explanation
| Q83➡ The following LPP Maximize z=100x1+2x2 +5x3 Subject to 14x1+x2 −6x3 +3x4 =7 32x1 +x2 −12x3 ≤10 3x1 −x2 −x3 ≤0 x1 , x2 , x3 , x4 ≥ 0 has |
| A ➥ x1 =100, x2 =0, x3 =0 |
| B ➥ Unbounded solution |
| C ➥ No solution |
| D ➥ x1 =50, x2 =70, x3 =60 |
Show Answer With Best Explanation
| Q84➡ Digital data received from a sensor can fill up 0 to 32 buffers. Let the sample space be S={0, 1, 2, ………., 32} where the sample j denote that j of the buffers are full and P (i) = (1/561)(33 − i ) . Let A denote the event that the even number of buffers are full. Then p(A) is: |
| A ➥ 0.515 |
| B ➥ 0.785 |
| C ➥ 0.758 |
| D ➥ 0.485 |
Show Answer With Best Explanation
| Q85➡ The equivalence of ¬∃ x Q(x) is : |
| A ➥ ∃x ¬Q(x) |
| B ➥ ∀x ¬Q(x) |
| C ➥ ¬∃x ¬Q(x) |
| D ➥ ∀x Q(x) |
Show Answer With Best Explanation
| Q86➡ If A i = {−i, … −2,−1, 0, 1, 2, . . . . . i} then 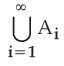 is: is: |
| A ➥ Z |
| B ➥ Q |
| C ➥ R |
| D ➥ C |
Show Answer With Best Explanation
| Q87➡ Match the following in List – I and List – II, for a function f : 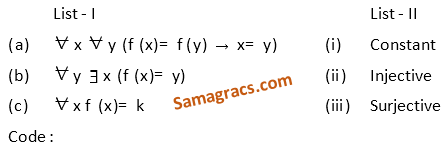 |
| A ➥ (a)-(i), (b)-(ii), (c)-(iii) |
| B ➥ (a)-(iii), (b)-(ii), (c)-(i) |
| C ➥ (a)-(ii), (b)-(i), (c)-(iii) |
| D ➥ (a)- (ii), (b)-(iii), (c)-(i) |
Show Answer With Best Explanation
| Q88➡ Which of the relations on {0, 1, 2, 3} is an equivalence relation ? |
| A ➥ { (0, 0) (0, 2) (2, 0) (2, 2) (2, 3) (3, 2) (3, 3) } |
| B ➥ { (0, 0) (1, 1) (2, 2) (3, 3) } |
| C ➥ { (0, 0) (0, 1) (0, 2) (1, 0) (1, 1) (1, 2) (2, 0) } |
| D ➥ { (0, 0) (0, 2) (2, 3) (1, 1) (2, 2) } |
Show Answer With Best Explanation
| Q89➡ Which of the following is an equivalence relation on the set of all functions from Z to Z ? |
| A ➥ { (f , g ) | f (x) − g (x) = 1 ∀ x ∈ Z } |
| B ➥ { (f , g ) | f (0) = g (0) or f (1) = g (1)} |
| C ➥ { (f , g ) | f (0) = g (1) and f (1) = g (0)} |
| D ➥ { (f , g ) | f (x) − g (x) = k f or some k ∈ Z } |
Show Answer With Best Explanation
| Q90➡ Which of the following statements is true ? |
| A ➥ (Z, ≤ ) is not totally ordered |
| B ➥ The set inclusion relation ⊆ is a partial ordering on the power set of a set S |
| C ➥ (Z, ≠ ) is a poset |
| D ➥ The directed graph |
Show Answer With Best Explanation
| Q91➡ CMOS is a Computer Chip on the motherboard, which is : |
| A ➥ RAM |
| B ➥ ROM |
| C ➥ EPROM |
| D ➥ Auxiliary storage |
Show Answer With Best Explanation
| Q92➡ In RS flip-flop, the output of the flip-flop at time (t+1) is same as the output at time t, after the occurrence of a clock pulse if : |
| A ➥ S=R=1 |
| B ➥ S=0, R=1 |
| C ➥ S=1, R=0 |
| D ➥ S=R=0 |
Show Answer With Best Explanation
| Q93➡ Match the terms in List – I with the options given in List – II :  |
| A ➥ (a)-(ii), (b)-(i), (c)-(iii) |
| B ➥ (a)-(ii), (b)-(iii), (c)-(i) |
| C ➥ (a)-(ii), (b)-(i), (c)-(iv) |
| D ➥ (a)-(iv), (b)-(ii), (c)-(i) |
Show Answer With Best Explanation
| Q94➡ What does the following logic diagram represent ? 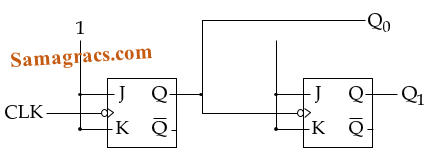 |
| A ➥ Synchronous Counter |
| B ➥ Ripple Counter |
| C ➥ Combinational Circuit |
| D ➥ Mod 2 Counter |
Show Answer With Best Explanation
| Q95➡ The hexadecimal equivalent of the binary integer number 110101101 is : |
| A ➥ D24 |
| B ➥ 1 B D |
| C ➥ 1 A E |
| D ➥ 1 A D |
Show Answer With Best Explanation
| Q96➡ Perform the following operation for the binary equivalent of the decimal numbers (-14)10+(15)10 The solution in 8 bit representation is : |
| A ➥ 11100011 |
| B ➥ 00011101 |
| C ➥ 10011101 |
| D ➥ 11110011 |
Show Answer With Best Explanation
| Q97➡ Match the items in List – I and List – II :  |
| A ➥ (a)-(ii), (b)-(i), (b)-(iv) |
| B ➥ (a)-(ii), (b)-(iv), (b)-(iii) |
| C ➥ (a)-(iii), (b)-(i), (b)-(ii) |
| D ➥ (a)-(iii), (b)-(iv), (b)-(ii) |
Show Answer With Best Explanation
| Q98➡ Which of the following mapping is not used for mapping process in cache memory? |
| A ➥ Associative mapping |
| B ➥ Direct mapping |
| C ➥ Set-Associative mapping |
| D ➥ Segmented – page mapping |
Show Answer With Best Explanation
| Q99➡ Simplify the following using K-map : F (A, B, C, D) = Σ (0, 1, 2, 8, 9, 12, 13) d (A, B, C, D) = Σ (10, 11, 14, 15) d stands for don’t care condition. |
| A ➥ A+B’ D’ + BC |
| B ➥ A+B’ D’ + B’ C’ |
| C ➥ A’+B’ C’ |
| D ➥ A’+B’ C’+B’ D’ |
Show Answer With Best Explanation
| Q100➡ In 8085 microprocessor, what is the output of following program? LDA 8000H MVI B, 30H ADD B STA 8001H |
| A ➥ Read a number from input port and store it in memory |
| B ➥ Read a number from input device with address 8000H and store it in memory at location 8001H |
| C ➥ Read a number from memory at location 8000H and store it in memory location 8001H |
| D ➥ Load A with data from input device with address 8000H and display it on the output device with address 8001H |

 = 10-3 second = 1 millisecond
= 10-3 second = 1 millisecond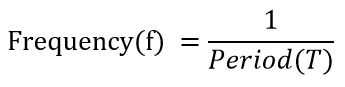
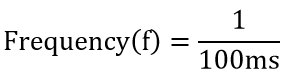
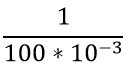 second
second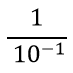 second
second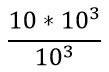 Hz
Hz