Solution-and-Question-2023-December-Science-Computer-NET -UGC
UGC NET 2023
CGU TEN retupmoC ecneicS rebmeceD 3202 noitseuQ dna noituloS
| Q1➡ | Consider a triangle PQR with coordinates as P(0,0) Q(2, 2) and R(10, 4) If this triangle is to be magnified to four times its size while keeping R(10, 4) fixed, then the coordinates of the magnified triangle are: |
| i ➥ (-20,12), Q(- 20, – 4) and R(10, 4) |
| ii ➥ (-30,12), Q(- 22, – 4) and R(10, 4) |
| iii ➥ (25,10), Q(22, – 4) and R(10, 4) |
| iv ➥ (30,12), Q(- 22, 4) and R(10, 4) |
| Best Explanation: Answer: (II) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
December Exam Solutions
Previous Year Question Papers
!noituloS dna noitseuQ 3202 rebmeceD ecneicS retupmoC TEN CGU
UGC NET 2023 Answer Key
UGC NET 2023 Answer Key
UGC NET Paper Analysis
| Q2➡ | Identify the code sequence : 1010 1011 1001 1000 |
| i ➥ BCD |
| ii ➥ Excess-3 |
| iii ➥ Gray |
| iv ➥ Excess-3 gray |
| Best Explanation: Answer: (III) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
NET December 2023 Exam Solutions
UGC NET December Paper Solutions
Exam Preparation Tips for UGC NET 2023
| Q3➡ | Arrange the following steps in the correct order for a DHCP Client to renew its IP lease with a DHCP server: (A) DHCP client sends a DHCPREQUEST message (B) DHCP server acknowledges the renewal with a DHCPACK message (C) DHCP client checks the local lease timer and initiates renewal (D) DHCP server updates its lease database Choose the correct answer from the options given below: |
| i ➥ (A), (B), (C), (D) |
| ii ➥ (C), (D), (Β), (A) |
| iii ➥ (C), (B), (A), (D) |
| iv ➥ (C), (A), (B), (D) |
| Best Explanation: Answer: (IV) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q4➡ | Given below are two statements: Statement (I): In datagram networks – routers hold state information about connections Statement (II): In virtual circuit network- each virtual circuit requires router table space per connection In the light of the above statements, choose the most appropriate answer from the options given below: |
| i ➥ Both Statement I and Statement II are correct |
| ii ➥ Both Statement I and Statement II are incorrect |
| iii ➥ Statement I is correct but Statement II is incorrect |
| iv ➥ Statement I is incorrect but Statement II is correct |
| Best Explanation: Answer: (IV) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q5➡ | Match List – I with List – II according to input to the compiler phase that process it : List – I (A) Syntax tree (B) Intermediate representation (C) Token stream (D) Character stream List – II (I) Code generator (II) Semantic analyzer (III) Lexical analyze (IV) Syntax analyser Choose the correct answer from the options given below : |
| i ➥ (A)-(IV), (B)-(III), (C)-(I), (D)-(II) |
| ii ➥ (A)-(II), (B)-(I), (C)-(IV), (D)-(III) |
| iii ➥ (A)-(II), (B)-(IV), (C)-(I), (D)-(III) |
| iv ➥ (A)-(IV), (B)-(I), (C)-(II), (D)-(III) |
| Best Explanation: Answer: (II) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q6➡ | Programming Consider the following code segment: int arr[] = {0, 1, 2, 3, 4}; int i = 1, *ptr; ptr = arr + 2; arrange the following printf statements in the increasing order of their output. (A) printf (“%d”, ptr[i]); (B) printf (“%d”, ptr[i+1]); (C) printf (“%d”, ptr[-i]); (D) printf (“%d”, ptr[-i+1]); Choose the correct answer from the options given below : |
| i ➥ (C), (A), (B), (D) |
| ii ➥ (C), (D), (A), (B) |
| iii ➥ (D), (A), (B), (C) |
| iv ➥ (A), (B), (D), (C) |
| Best Explanation: Answer: (II) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q7➡ | Programming What is the output of the following program? include int main() { int i=3; while (i–) { int i=10; i–; printf(“%d”, i); } printf(“%d”, i); } |
| i ➥ 990 |
| ii ➥ 9990 |
| iii ➥ 999-1 |
| iv ➥ 99-1 |
| Best Explanation: Answer: (III) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q8➡ | CG Match List – I with List – II. List – I (A) Bresenham (B) Cohen-Sutherland (C) Sutherland-Hodgeman (D) Z-Buffer List – II (1) Hidden surface removal (II) Line drawing algorithm (III) Line clipping algorithm (IV) Polygon clipping algorithm Choose the correct answer from the options given below : |
| i ➥ (A)-(III), (B)-(II), (C)-(IV), (D)-(I) |
| ii ➥ (A)-(II), (B)-(III), (C)-(I), (D)-(IV) |
| iii ➥ (A)-(II), (B)-(III), (C)-(IV), (D)-(I) |
| iv ➥ (A)-(II), (B)-(IV), (C)-(III), (D)-(1) |
| Best Explanation: Answer: (III) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q9➡ | Which of the following symbol table implementation is best suited if access time is to be minimum? |
| i ➥ Linear list |
| ii ➥ Search tree |
| iii ➥ Hash Table |
| iv ➥ Self organisation list |
| Best Explanation: Answer: (III) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q10➡ | CN Which of the following statement/s is/are NOT CORRECT ? (A) OSPF is based on distance-vector routing protocol. (B) Both link-state and distance-vector routing are based on the least cost goal. (C) BGP4 is based on the path-vector algorithm. (D) The three-node instability can be avoided using split horizon combined with poison reverse. (E) RIP is based on link state algorithm. Choose the correct answer from the options given below : |
| i ➥ (A), (D) and (E) Only |
| ii ➥ (A) and (B) Only |
| iii ➥ (B) and (C) Only |
| iv ➥ (B), (C) and (E) Only |
| Best Explanation: Answer: (I) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q11➡ | Match List – I with List – II. List – I (A) BCNF iff (B) 5 NF iff (C) 1 NF iff (D) 4 NF iff List – II (I) every JD is implied by the candidate keys (II) all underlying domains contain scalar values only (III) every MVD is implied by the candidate keys (IV) every FD is implied by the candidate keys Choose the correct answer from the options given below : |
| i ➥ (A)-(III), (B)-(II), (C)-(I), (D)-(IV) |
| ii ➥ (A)-(IV), (B)-(I), (C)-(II), (D)-(III) |
| iii ➥ (A)-(II), (B)-(III), (C)-(IV), (D)-(I) |
| iv ➥ (A)-(IV), (B)-(I), (C)-(III), (D)-(II) |
| Best Explanation: Answer: (II) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q12➡ |Networking A multiplexes combines for 100 Kbps channels using a time slot of 2 bits. What is the bit rate? |
| i ➥ 100 Kbps |
| ii ➥ 200 Kbps |
| iii ➥ 40 Kbps |
| iv ➥ 1000 Kbps |
| Best Explanation: Answer: (III) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q13➡ | Software engineering Match List – I with List – II. List – I Propositions (A) P ∧(P→Q) (B)¬(P ∨ Q)→(P ∧Q) (C) P→Q (D) P ∨ (Q∧R) List – II Disjunctive Normal Form (DNF) (I) P ∨ Q (II) (P∧¬P) ∨ (P∧Q) (III) (¬P) ∨ Q (IV) (P∧P) ∨ (P∧Q) ∨ (P∧R) ∨ (Q∧R) Choose the correct answer from the options given below : |
| i ➥ (A)-(1), (B)-(II), (C)-(III), (D)-(IV) |
| ii ➥ (A)-(II), (B)-(I), (C)-(III), (D)-(IV) |
| iii ➥ (A)-(III), (B)-(I), (C)-(II), (D)-(IV) |
| iv ➥ (A)-(IV), (B)-(III), (C)-(II), (D)-(I) |
| Best Explanation: Answer: (II) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q14➡ | Programming What is the output of the following program? #include #define SQR(x) (x*x) int main () { int a, b = 3; a = SQR(b+2); printf(“%d”,a); return 0; } |
| i ➥ 25 |
| ii ➥ 11 |
| iii ➥ Garbage value |
| iv ➥ 24 |
| Best Explanation: Answer: (II) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q15➡ | In “bit stuffing”, each frame begins and ends with a bit pattern in hexadecimal? |
| i ➥ Ox8C |
| ii ➥ Ox6F |
| iii ➥ OxFF |
| iv ➥ Ox7E |
| Best Explanation: Answer: (IV) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q16➡ | Which of the following is not a field in TCP header ? |
| i ➥ Sequence Number |
| ii ➥ Checksum |
| iii ➥ Fregmentation offset |
| iv ➥ Window size |
| Best Explanation: Answer: (III) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q17➡ | In most general case, the computer needs to process each instruction with the following sequence of steps: (A) Calculate the effective address (B) Execute the instruction (C) Fetch the instruction from memory (D) Fetch the operand from memory (E) Decode the instruction Choose the correct answer from the options given below: |
| i ➥ (A), (B), (C), (D), (E) |
| ii ➥ (A), (B), (C), (E), (D) |
| iii ➥ (C), (E), (A), (D), (B) |
| iv ➥ (C), (E), (D), (A), (B) |
| Best Explanation: Answer: (III) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q18➡ | Which of the statement are CORRECT ? (A) Constructors are invoked automatically when the objects are created. (B) Constructors do not have return types, not even void and therefore they cannot return values. (C) Constructors cannot be inherited though a derived class can call the base class constructors. (D) Constructors can be declared as virtual. Choose the correct answer from the options given below : |
| i ➥ (A), (B) and (D) Only |
| ii ➥ (A), (B) and (C) Only |
| iii ➥ (B), (C) and (D) Only |
| iv ➥ (A), (C) and (D) Only |
| Best Explanation: Answer: (II) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q19➡ | Test suite is consist of: |
| i ➥ Set of defect cases |
| ii ➥ Set of boundary cases |
| iii ➥ Set of test cases |
| iv ➥ Set of nest cases |
| Best Explanation: Answer: (III) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q20➡ | Given below are two statements: Statement (I): If H is non empty finite subset of a group G and ab∉H ∀ a, b∉H, then H is also a group Statement (II): There is no homomorphism exist from (Z, +) to (Q, +); where Z is set of integers and Q is set of rational number. In the light of the above statements, choose the most appropriate answer from the options given below: |
| i ➥ Both Statement I and Statement II are correct |
| ii ➥ Both Statement I and Statement II are incorrect |
| iii ➥ Statement I is correct but Statement II is incorrect |
| iv ➥ Statement I is incorrect but Statement II is correct |
| Best Explanation: Answer: (III) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q21➡ | Arrange the following phases of a compiler as per their order of execution (start to end) (A) Target code generation (B) Syntax Analysis (C) Code optimization (D) Semantic Analysis (E) Lexical Analysis Choose the correct answer from the options given below : |
| i ➥ (B), (E), (D), (A), (C) |
| ii ➥ (E), (D), (B), (A), (C) |
| iii ➥ (E), (B), (D), (C), (A) |
| iv ➥ (B), (D), (Ε), (A), (C) |
| Best Explanation: Answer: (III) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q22➡ | What is the probability that a positive integer selected at random from the set of positive integer not exceeding 100 is divisible by either 2 or 5? |
| i ➥ 10/5 |
| ii ➥ 3/5 |
| iii ➥ 2/5 |
| iv ➥ 1/5 |
| Best Explanation: Answer: (II) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q23➡ | Given below are two statements: Statement (I): In Reuse Oriented Model, Modification of the old system parts appropriate to the new requirements. Statement (II): In Reuse Oriented Model, Integration of the modified parts are not possible into the new systems. In the light of the above statements, choose the most appropriate answer from the options given below: |
| i ➥ Both Statement I and Statement II are correct |
| ii ➥ Both Statement I and Statement II are incorrect |
| iii ➥ Statement I is correct but Statement II is incorrect |
| iv ➥ Statement I is incorrect but Statement II is correct |
| Best Explanation: Answer: (III) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q24➡ | Arrange the following encoding strategies used in Genetic Algorithms (GAs) in the correct sequence starting from the initial step and ending with the final representation of solutions: (A) Binary Encoding (B) Real valued Encoding (C) Permutation Encoding (D) Gray coding Choose the correct answer from the options given below : |
| i ➥ (D), (B), (A), (C) |
| ii ➥ (B), (D), (A), (C) |
| iii ➥ (C), (D), (A), (B) |
| iv ➥ (B), (C), (A), (D) |
| Best Explanation: Answer: (III) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q25➡ | A system bus in which each data item is transferred during a time slice known in advance to both units source and destination is called: |
| i ➥ MIMD |
| ii ➥ DMA |
| iii ➥ asynchronous bus |
| iv ➥ synchronous bus |
| Best Explanation: Answer: (IV) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q26➡ | The selection of Spiral Model based on characteristics of requirements : (A) Are requirements easily understandable and defined ? (B) Do we change requirements quite often ? (C) Can we define requirements early in the cycle? (D) Requirements are indicating a complex to be built Choose the correct answer from the options given below : |
| i ➥ (C) Only |
| ii ➥ (B) Only |
| iii ➥ (B) and (D) Only |
| iv ➥ (A) and (C) Only |
| Best Explanation: Answer: (III) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q27➡ | An Address in main memory is called : |
| i ➥ Virtual address |
| ii ➥ Memory address |
| iii ➥ Logical address |
| iv ➥ Physical address |
| Best Explanation: Answer: (IV) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q28➡ | A program that is used by other routines to accomplish a particular task, is called: |
| i ➥ Micro program |
| ii ➥ Micro operation |
| iii ➥ Routine |
| iv ➥ Subroutine |
| Best Explanation: Answer: (IV) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q29➡ | Let A={a, b} and L=A*. Let x={anbn, n>0}. The languages L ⋃ X and X are respectively : |
| i ➥ Not regular, Regular |
| ii ➥ Regular, Regular |
| iii ➥ Regular, Not regular |
| iv ➥ Not Regular, Not Regular |
| Best Explanation: Answer: (III) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q30➡ | The statement P(x): “x=x2“. If the universe of disclosure consists of integers, what are the following have truth values : (A) P(0) (B) P(1) (C) P(2) (D) Ǝx P(x) (E) ∀x P(x) Choose the correct answer from the options given below : |
| i ➥ (A), (B) and (E) Only |
| ii ➥ (A), (B) and (C) Only |
| iii ➥ (A), (B) and (D) Only |
| iv ➥ (B), (C) and (D) Only |
| Best Explanation: Answer: (IV) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q31➡ | Given below are two statements: Statement (I): A thread is a dispatchable unit of work that does not executes sequentially and is not interruptible Statement (II): It is not possible to alter the behaviour of a thread by altering its context when thread is suspended In the light of the above statements, choose the most appropriate answer from the options given below: |
| i ➥ Both Statement I and Statement II are correct |
| ii ➥ Both Statement I and Statement II are incorrect |
| iii ➥ Statement I is correct but Statement II is incorrect |
| iv ➥ Statement I is incorrect but Statement II is correct |
| Best Explanation: Answer: (II) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
Q32➡ | 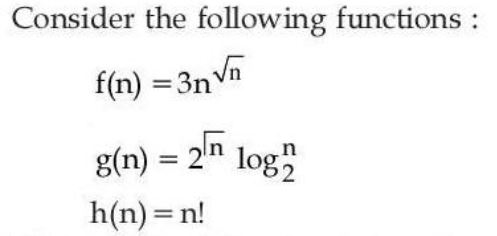 Which of the following is true? |
| i ➥ h(n) is 0(f(n)) |
| ii ➥ h(n) is 0 (g(n)) |
| iii ➥ g(n) is not 0 (f(n)) |
| iv ➥ f(n) is 0(g(n)) |
| Best Explanation: Answer: (IV) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q33➡ | Arrange the following steps in the correct sequence for applying an unsupervised learning technique such as K-means clustering is to a data set: (A) Randomly initialize cluster centroids (B) Assign each data point to nearest cluster centroid (C) Update the cluster centroids based on the mean of data points assigned to each cluster (D) Specify the number of clusters (K) to partation the data into (E) Repeat steps B and C until convergence criteria are met Choose the correct answer from the options given below: |
| i ➥ (D), (A), (B), (C), (Ε) |
| ii ➥ (A), (B), (C), (D), (E) |
| iii ➥ (C), (B), (A), (D), (E) |
| iv ➥ (D), (C), (A), (B), (Ε) |
| Best Explanation: Answer: (I) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q34➡ | Which of the following(s) are main memory ? (A) Virtual memory (B) Cache memory (C) RAM (D) SSD Choose the correct answer from the options given below : |
| i ➥ (A) and (C) Only |
| ii ➥ (B) and (C) Only |
| iii ➥ (C) and (D) Only |
| iv ➥ (A), (B) and (C) Only |
| Best Explanation: Answer: (II) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q35➡ | Which collision resolution technique involves maintaining a linked list of collided keys? |
| i ➥ Linear probing |
| ii ➥ Quadratic probing |
| iii ➥ Chaining |
| iv ➥ Double hashing |
| Best Explanation: Answer: (III) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q36➡ | One of the purposes of using intermediate code in compilers is to: |
| i ➥ make parsing and semantic analysis simpler |
| ii ➥ improve error recovery and error reporting |
| iii ➥ increase the chances of reusing the machine independent code optimizer in other compilers |
| iv ➥ improve the register allocation |
| Best Explanation: Answer: (III) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q37➡ | In Linux, where is the user password stored ? |
| i ➥ /etc/password |
| ii ➥ /root/password |
| iii ➥ /etc/passwd |
| iv ➥ /root/passwd |
| Best Explanation: Answer: (iii) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q38➡ | The sum of minimum and maximum number of final states for a Deterministic Finite Automata (DFA) having ‘P’ state is equal to: |
| i ➥ P |
| ii ➥ p-1 |
| iii ➥ p + 1 |
| iv ➥ p + 2 |
| Best Explanation: Answer: (III) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q39➡ | Which of the following is not a palindromic subsequence of the string “ababcdabba” ? |
| i ➥ abcba |
| ii ➥ abba |
| iii ➥ abbbba |
| iv ➥ adba |
| Best Explanation: Answer: (IV) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q40➡ | A point of fuzzy set A is a point x∈X at which μΑ(x) = 0.5 |
| i ➥ Core |
| ii ➥ Support |
| iii ➥ Crossover |
| iv ➥ α-cut |
| Best Explanation: Answer: (III) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q41➡ | Which of the following are tautology? (A) (P (P∧ Q))→(P→Q) (B) ((PQ)→Q)→(PVQ) (C) ((P V¬P)→Q)→((PV ¬P)→R) (D) (Q→(P∧ ¬P))→(R→(P∧ ¬P)) Choose the correct answer from the options given below : |
| i ➥ (A) Only |
| ii ➥ (B) Only |
| iii ➥ (A) and(B) Only |
| iv ➥ (C) and (D) Only |
| Best Explanation: Answer: (III) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q42➡ | What is the generic structure of Multi Agent System (MAS) ? |
| i ➥ Single agent with multiple objectives |
| ii ➥ Multiagents with a single objectives |
| iii ➥ Multiagents with diverse objectives and communication abilities |
| iv ➥ Multiagent with two objectives |
| Best Explanation: Answer: (III) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q43➡ | Consider the three points P1(1, 2, 0), P2(3, 6, 20) and P3(2, 4, 6) and a view point C(0, 0, 10). Choose the correct options. (A) P1 obscure P2, if viewed from C. (B) P2 obscure P1, if viewed from C. (C) P3 does not obscure P1, if viewed from C. (D) P2 does not obscure P3, if viewed from C. Choose the correct answer from the options given below : |
| i ➥ (A), (B) and (C) Only |
| ii ➥ (A), (C) and (D) Only |
| iii ➥ (B), (C) and (D) Only |
| iv ➥ (A), (B) and (D) Only |
| Best Explanation: Answer: (II) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q44➡ | What is the result of evaluating the postfix expression “43*25*+b-“? |
| i ➥ 8 |
| ii ➥ 14 |
| iii ➥ 10 |
| iv ➥ 5 |
| Best Explanation: Answer: (I) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q45➡ | Which of the following statement/s are CORRECT ? (A) NRZ is a bipolar scheme in which the positive voltage define bit is 0 (zero). (B) NRZ-L and NRZ-I both have an average signal rate of N/2. (C) The idea of RZ and NRZ-L are combined into Manchester scheme. (D) NRZ-L and NRZ-I both have DC component problems. (E) The minimum bandwidth of Manchester and differential Manchester is 3 times that of NRZ. Choose the correct answer from the options given below : |
| i ➥ (A), (B) and (C) Only |
| ii ➥ (A), (C), (D) and (E) Only |
| iii ➥ (B), (C) and (D) Only |
| iv ➥ (A), (B), (C) and (E) Only |
| Best Explanation: Answer: (III) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q46➡ | In a feed forward neural network with the following specifications: Input layer has 4 neurons, hidden layer has 3 neurons and output layer has 2 neurons using the sigmoid activation function for given input values [0.5, 0.8, 0.2, 0.6] as well as the initial weights for the connections. Input layer to hidden layer weights W1: [0.1, 0.3, 0.5, 0.2] W2: [0.2, 0.4, 0.6, 0.2] W3: [0.3, 0.5, 0.7, 0.2] Hidden layer to output layer weights W4: [0.4, 0.1, 0.3] W5: [0.5, 0.2, 0.4] What is the output of the output layer when the given input values are passed through neural network? Round the answer to two decimal places: |
| i ➥ [0.62, 0.68] |
| ii ➥ [0.72, 0.78] |
| iii ➥ [0.82, 0.88] |
| iv ➥ [0.92, 0.98] |
| Best Explanation: Answer: (I) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q47➡ | Which of the following is/are NOT CORRECT statement? (A) The first record in each block of the data file is known as actor record. (B) Dense index has index entries for every search key value in the data file. (C) Searching is harder in the B+ tree than B- tree as the all external nodes linked to each other. (D) In extendible hashing the size of directory is just an array of 2d-1, where d is global depth. Choose the correct answer from the options given below: |
| i ➥ (A), (B) and (C) Only |
| ii ➥ (A), (C) and (D) Only |
| iii ➥ (A), (B) and (D) Only |
| iv ➥ (A), (B), (C) and (D) Only |
| Best Explanation: Answer: (II) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q48➡ | Which of the following are commonly used parsing techniques in NLP (Natural Language Processing) for syntatic analysis. (A) Top down parsing (B) Bottom Up parsing (C) Dependency parsing (D) Statistical machine translation (E) Earley parsing Choose the correct answer from the options given below : |
| i ➥ (A), (C), (D), (E) Only |
| ii ➥ (B), (C), (D), (E) Only |
| iii ➥ (A), (B), (C), (E) Only |
| iv ➥ (A) and (B) Only |
| Best Explanation: Answer: (III) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q49➡ | Which one of the following statements are CORRECT ? (A) Granularity is the size of data item in a database. (B) Two operations in a schedule are said to be conflict if they belong to same transaction. (C) Two schedulers are said to be conflict equivalent if the order of any two conflicting operations is the same in both schedules. (D) Write operations which are performed without performing the write operation are known as Blind Writes. Choose the correct answer from the options given below : |
| i ➥ (A) and (B) Only |
| ii ➥ (A), (B) and (C) Only |
| iii ➥ (A), (B) and (D) Only |
| iv ➥ (B) and (C) Only |
| Best Explanation: Answer: (II) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q50➡ | Consider a Grammar E→E+n | E x n | n for a sentence n+n×n, the handles in the right-sentential form of the reduction are? |
| i ➥ n, E+n and E+n×n |
| ii ➥ n, E+n and E+Exn |
| iii ➥ n, n+n and n+n×n |
| iv ➥ n, E+n and Exn |
| Best Explanation: Answer: (IV) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q51➡ | Which of the following statements is TRUE? |
| i ➥ Virtual functions do not implement polymorphism |
| ii ➥ Virtual functions do not permit calling of derived class functions using a base class pointer |
| iii ➥ We can never build an object from a class containing a pure virtual function |
| iv ➥ Pure virtual functions can never have a body |
| Best Explanation: Answer: (III) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q52➡ | The Hue of a colour is related to its : |
| i ➥ Luminance |
| ii ➥ Saturation |
| iii ➥ Incandescence |
| iv ➥ Wavelength |
| Best Explanation: Answer: (IV) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q53➡ | The head of a moving head disk with 200 tracks, numbered 0 to 199, has just finished a request at track 125, and currently serving a request at track 143. The queue of requests is given in the FIFO order as 86, 147, 91, 177, 94, 150, 102, 175, 130. What will be the total number of head movements required to satisfy these requests for SCAN algorithm? |
| i ➥ 259 cylinders |
| ii ➥ 169 cylinders |
| iii ➥ 154 cylinders |
| iv ➥ 264 cylinders |
| Best Explanation: Answer: (II) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q54➡ | Given as 4 GB (≈ 4.3 × 109 bytes) of virtual space and typical page size of 4 KB and each page table entry is 5 bytes. How many virtual pages would this imply? What is the size of whole page table? |
| i ➥ 107500 and 20480 bytes |
| ii ➥ 215000 and 40960 bytes |
| iii ➥ 10750 and 10240 bytes |
| iv ➥ 43000 and 1024 bytes |
| Best Explanation: Answer: (I) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
UGC NET 2023 Question Paper Discussion
| Q55➡ | Three address codes can be represented in special structures known as: (A) Quadruples (B) Triples (C) Patterns (D) Indirect Triples Choose the correct answer from the options given below : |
| i ➥ (A) and (B) Only |
| ii ➥ (A), (B) and (D) Only |
| iii ➥ (B) and (C) Only |
| iv ➥ (B), (C) and (D) Only |
| Best Explanation: Answer: (III) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
UGC NET 2023 Question Paper Discussion
| Q56➡ | The steps for analysis and design of object oriented system. (A) Draw interaction diagrams (B) Draw state chart and object diagram (C) Draw use case and activity diagram (D) Draw component and deployment diagram (E) Draw class diagram Choose the correct answer from the options given below : |
| i ➥ (E)→(B)→(A)→(C)→(D) |
| ii ➥ (B)→(A)→(E)→(D)→(C) |
| iii ➥ (E)→(C)→(B)→(D)→(A) |
| iv ➥ (C)→(A)→(E)→(B)→(D) |
| Best Explanation: Answer: (IV) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q57➡ | The interface(s) that provide(s) I/O transfer of data directly to and from the memory unit peripheral is/are termed as: (A) DMA (Direct Memory Access) (B) IOP (Input-Output Processor) (C) Serial Interface (D) Parallel Interface Choose the correct answer from the options given below : |
| i ➥ (A) Only |
| ii ➥ (B) Only |
| iii ➥ (A) and (B) Only |
| iv ➥ (C) and (D) Only |
| Best Explanation: Answer: (III) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q58➡ | Which of the following statements is/are NOT CORRECT about NUMA? (A) LOAD and STORE instructions are used to access remote memory. (B) There is a single address space visible to all CPU. (C) Access to local memory is slower than access to remote memory. (D) When the access time to remote memory is hidden, the system is called NC – NUMA. (E) In CC-NUMA, Coherent caches are present. Choose the correct answer from the options given below : |
| i ➥ (A) and (C) Only |
| ii ➥ (B) and (D) Only |
| iii ➥ (A) and (E) Only |
| iv ➥ (C) and (D) Only |
| Best Explanation: Answer: (IV) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q59➡ | Match List – I with List – II. List – I (A) Hill climbing (B) Best first search (C) A* Search (D) Depth first search List – II (I) O(b ^ d) (II) O(bd) (III) O(1) (IV) O(b ^ m) Choose the correct answer from the options given below : |
| i ➥ (A)-(III), (B)-(I), (C)-(IV), (D)-(II) |
| ii ➥ (A)-(II), (B)-(I), (C)-(IV), (D)-(III) |
| iii ➥ (A)-(II), (B)-(IV), (C)-(I), (D)-(III) |
| iv ➥ (A)-(1), (B)-(II), (C)-(II), (D)-(I) |
| Best Explanation: Answer: (I) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q60➡ | Level – 0 DFD is also called as: |
| i ➥ Use case Diagram |
| ii ➥ Sequence Diagram |
| iii ➥ Context Diagram |
| iv ➥ Prototype Diagram |
| Best Explanation: Answer: (III) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q61➡ | In a genetic algorithm optimization problem the fitness function is defined as f(x) = x²-4x +4. Given a population of four individuals with values of x: (1.5, 2.0, 3.0, 4.5} What is the fitness value of the individual that will be selected as the parent for reproduction in one generation? |
| i ➥ 2.25 |
| ii ➥ 6.0 |
| iii ➥ 0.0 |
| iv ➥ 6.25 |
| Best Explanation: Answer: (IV) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q62➡ | Arrange the following in ascending order : (A) Remainder of 4916 when divided by 17 (B) Remainder of 2446 when divided by 9 (C) Remainder of 15517 when divided by 17 (D) Last digits of the number 745 Choose the correct answer from the options given below : |
| i ➥ (A), (B), (C), (D) |
| ii ➥ (A), (B), (D), (C) |
| iii ➥ (A), (C), (B), (D) |
| iv ➥ (D), (C), (B), (A) |
| Best Explanation: Answer: (III) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q63➡ | Indexed/grouped allocation is useful as : (A) It supports both sequential and direct access. (B) Entire block is available for data. (C) It does not require lots of space for keeping pointers. (D) No external fragmentation. Choose the correct answer from the options given below : |
| i ➥ (A) Only |
| ii ➥ (B) and (C) Only |
| iii ➥ (B) Only |
| iv ➥ (A), (B) and (D) Only |
| Best Explanation: Answer: (IV) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q64➡ | The prototyping model has the sequence : (A) Customer Evaluation (B) Quick design (C) Requirements (D) Implement (E) Design Choose the correct answer from the options given below : |
| i ➥ (C) -> (A) -> (D) -> (B) -> (E) |
| ii ➥ (B) -> (C) -> (A) -> (D) -> (E) |
| iii ➥ (C) -> (B) -> (D) -> (A) -> (E) |
| iv ➥ (E) -> (B) -> (C) -> (D) -> (A) |
| Best Explanation: Answer: (III) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q65➡ | Match List – I with List – II. List – I (A) Monoalphabetic Cipher (B) DES (C) Stream Cipher (D) Polyalphabetic Cipher List – II (I) Round key (II) One-to-many relationship (III) One-to-one relationship (IV) Feedback mechanism Choose the correct answer from the options given below : |
| i ➥ (A)-(III), (B)-(I), (C)-(IV), (D)-(II) |
| ii ➥ (A)-(III), (B)-(IV), (C)-(II), (D)-(I) |
| iii ➥ (A)-(I), (B)-(III), (C)-(IV), (D)-(II) |
| iv ➥ (A)-(II), (B)-(I), (C)-(IV), (D)-(III) |
| Best Explanation: Answer: (I) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q66➡ | Which of the following statement are truth statements if universe of disclosure is set of integers: (A) ∀n(n2 >= 0) (B) ∃ n(n 2 = 2) (C) ∀ n(n 2 >= n) (D) ∃ n(n2 < 0) Choose the correct answer from the options given below : |
| i ➥ (A) and (B) Only |
| ii ➥ (B) and (C) Only |
| iii ➥ (C) and (D) Only |
| iv ➥ (A) and (C) Only |
| Best Explanation: Answer: (IV) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q67➡ | “CREATE TABLE T” in SQL is an example of : |
| i ➥ Normalization |
| ii ➥ DML |
| iii ➥ DDL |
| iv ➥ Primary key |
| Best Explanation: Answer: (III) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q68➡ | The microoperation which divides a signed binary number by 2 is: |
| i ➥ Circular shift |
| ii ➥ Logical shift |
| iii ➥ Arithmetic shift right |
| iv ➥ Arithmetic shift left |
| Best Explanation: Answer: (II) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q69➡ | Match List – I with List – II. List – I (A) SZA (B) SKI (C) SNA (D) ISZ List – II (I) Increment M and skip it zero (II) Skip if AC is negative (III) Skip if input flag is on (IV) Skip if AC is Zero Choose the correct answer from the options given below : |
| i ➥ (A)-(II), (B)-(IV), (C)-(I), (D)-(III) |
| ii ➥ (A)-(IV), (B)-(III), (C)-(II), (D)-(I) |
| iii ➥ (A)-(IV), (B)-(II), (C)-(I), (D)-(III) |
| iv ➥ (A)-(III), (B)-(IV), (C)-(II), (D)-(I) |
| Best Explanation: Answer: (II) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q70➡ | If the universe of disclosure is set of integers, then which of the followings are TRUE? (A) ∀n ∃ m(n2 < m) (B) ∃ n ∀ m(n < m2) (C) ∃n ∀ m(nm = m) (D) ∃ n ∃m(n2 + m2 = 6) (E) 3n ∃ m(n + m = 4 ∧ n – m = 1) Choose the correct answer from the options given below : |
| i ➥ (A), (B) and (C) Only |
| ii ➥ (B) and (C) Only |
| iii ➥ (C), (D) and (E) Only |
| iv ➥ (C) and (E) Only |
| Best Explanation: Answer: (II) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q71➡ | Which of the following are example of CSMA channel sensing methods ? (A) 1-persistent (B) 2-persistent (C) p-persistent (D) o-persistent Choose the correct answer from the options given below : |
| i ➥ (A), (B) and (D) Only |
| ii ➥ (A), (C) and (D) Only |
| iii ➥ (B), (C) and (D) Only |
| iv ➥ (A), (B) and (C) Only |
| Best Explanation: Answer: (II) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q72➡ | Which of the following graphs are trees ? 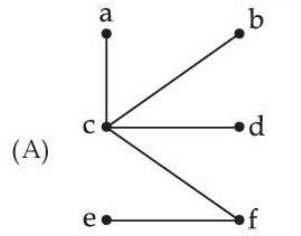 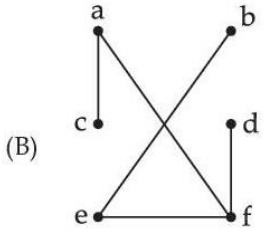 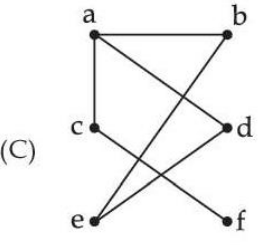 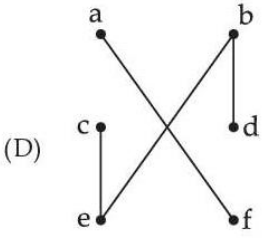 Choose the correct answer from the options given below : |
| i ➥ (A) and (B) Only |
| ii ➥ (A), (B) and (D) Only |
| iii ➥ (A) and (D) Only |
| iv ➥ (A), (B), (C) and (D) Only |
| Best Explanation: Answer: (I) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q73➡ | In the content of Alpha Beta pruning in game trees which of the following statements are correct regarding cut off procedures ? (A) Alpha Beta pruning can eliminate subtrees with certainly when the value of a node exceeds both the alpha and beta bonds. (B) The primarily purpose of Alpha-Beta proning is to save computation time by searching fewer nodes in the same tree. (C) Alpha Beta pruning guarantees the optimal solution in all cases by exploring the entire game tree. (D) Alpha and Beta bonds are initialized to negative and positive infinity respectively at the root note. Choose the correct answer from the options given below: |
| i ➥ (A), (C), (D) Only |
| ii ➥ (B), (C), (D) Only |
| iii ➥ (A), (B), (D) Only |
| iv ➥ (C), (B) Only |
| Best Explanation: Answer: (III) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q74➡ | Which of the following circuit is used to store one bit of data ? |
| i ➥ Encoder |
| ii ➥ Decoder |
| iii ➥ Flip-Flop |
| iv ➥ Register |
| Best Explanation: Answer: (III) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q75➡ | Which of the statement is/are CORRECT ? (A) Moore and Mealy machines are finite state machines with output capabilities. (B) Any given Moore machine has an equivalent Mealy machine. (C) Any given Mealy machine has an equivalent Moore machine. (D) Moore machine is not a finite state machine. Choose the correct answer from the options given below : |
| i ➥ (A) and (B) Only |
| ii ➥ (A), (B) and (C) Only |
| iii ➥ (B) and (D) Only |
| iv ➥ (A), (B) and (D) Only |
| Best Explanation: Answer: (II) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q76➡ | Match List – I with List – II. List – I (A) LRU (B) Demand cleaning (C) Long term scheduling (D) Medium term scheduling List – II (I) A page is written to secondary memory only when it has been selected for replacement (II) A page that has not been referenced for the longest time is replaced (III) The decision to add to the number of processes that are partially or fully in main memory (IV) The decision to add to the pool of processes to be executed Choose the correct answer from the options given below: |
| i ➥ (A)-(1), (B)-(III), (C)-(IV), (D)-(II) |
| ii ➥ (A)-(II), (B)-(I), (C)-(IV), (D)-(III) |
| iii ➥ (А)-(III), (B)-(II), (C)-(1), (D)-(IV) |
| iv ➥ (A)-(IV), (B)-(II), (C)-(II), (D)-(I) |
| Best Explanation: Answer: (II) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
Q77➡ |  Choose the correct answer from the options given below |
| i ➥ (A)-(1), (B)-(II), (C)-(III), (D)-(IV) |
| ii ➥ (A)-(II), (B)-(I), (C)-(III), (D)-(IV) |
| iii ➥ (A)-(II), (B)-(I), (C)-(IV), (D)-(III) |
| iv ➥ (A)-(I), (B)-(II), (C)-(IV), (D)-(III) |
| Best Explanation: Answer: (IV) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q78➡ | If universe of disclosure are all real numbers, then which of the following are true? (A) Ǝx ∀y (x+y=y) (B) ∀x ∀y(((x≥0)∧(y<0))→(x-y>0)) (C) Ǝx Ǝy(((x≤0)∧(y≤0))∧(x-y>0)) (D) ∀x ∀y((x≠0)∧(y≠0)↔(xy≠0)) Choose the correct answer from the options given below : |
| i ➥ (A) and (B) Only |
| ii ➥ (A), (C) and (D) Only |
| iii ➥ (A), (B) and (D) Only |
| iv ➥ (A), (B), (C) and (D) Only |
| Best Explanation: Answer: (IV) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q79➡ | Given below are two statements: Statement (I): The friend function and the member functions of a friend class directly access the private and protected data. Statement (II): The friend function can access the private data through the member functions of the base class In the light of the above statements, choose the most appropriate answer from the options given below: |
| i ➥ Both Statement I and Statement II are correct |
| ii ➥ Both Statement I and Statement II are incorrect |
| iii ➥ Statement I is correct but Statement II is incorrect |
| iv ➥ Statement I is incorrect but Statement II is correct |
| Best Explanation: Answer: (IV) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q80➡ | Arrange the following levels of interrupt protection within the Linux Kernel, in the order of increasing priority. (A) user mode programs (B) bottom half interrupt handlers (C) kernel system service routines (D) top half interrupt handlers Choose the correct answer from the options given below : |
| i ➥ (A), (B), (D), (C) |
| ii ➥ (A), (C), (B), (D) |
| iii ➥ (A), (C), (D), (B) |
| iv ➥ (D), (A), (C), (B) |
| Best Explanation: Answer: (II) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q81➡ | Which data structure is typically used to implement hash table? |
| i ➥ Linked list |
| ii ➥ Array |
| iii ➥ Binary Tree |
| iv ➥ Stack |
| Best Explanation: Answer: (II) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q82➡ | Has functions are used to produce the message digests which are then encrypted with a private key to get : |
| i ➥ Public key |
| ii ➥ Digital signature |
| iii ➥ Cipher text |
| iv ➥ Data Encryption Standard |
| Best Explanation: Answer: (II) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q83➡ | Let L={ab, aa, baa}. Which of the following strings are not in L*. |
| i ➥ abaabaaabaa |
| ii ➥ aaaabaaaa |
| iii ➥ baaaaabaaaab |
| iv ➥ baaaaabaa |
| Best Explanation: Answer: (III) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q84➡ | Which of the following is TRUE? |
| i ➥ The cost of searching an AVL tree is ϴ (log n) but that of binary search is 0(n) |
| ii ➥ The cost of searching an AVL tree in ϴ (log n) but that of complete binary tree is ϴ(n log n) |
| iii ➥ The cost of searching a binary tree is 0(log n) but that of AVL tree is ϴ (n) |
| iv ➥ The cost of searching an AVL tree is ϴ (n log n) but that of binary search tree is 0(n) |
| Best Explanation: Answer: (I) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q85➡ | The work done by UDP is/are: (A) Congestion control (B) Flow control (C) Retransmission (D) Segments transmission Choose the correct answer from the options given below : |
| i ➥ (A) and (D) Only |
| ii ➥ (C) Only |
| iii ➥ (D) Only |
| iv ➥ (B) and (C) Only |
| Best Explanation: Answer: (III) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q86➡ | Match List – I with List – II. List – I (A) Greedy Best first search (B) A* (C) Recursive best first search (D) SMA* List – II (I) The space complexity as O(d) where d = depth of the deepest optimal solution (II) Incomplete even if the search space is finite (III) Optimal if optimal solution is reachable otherwise return the best reachable optimal solution (IV) Computation and space complexity is two light Choose the correct answer from the options given below : |
| i ➥ (A)-(II), (B)-(IV), (C)-(I), (D)-(III) |
| ii ➥ (A)-(II), (B)-(III), (C)-(I), (D)-(IV) |
| iii ➥ (A)-(III), (B)-(II), (C)-(IV), (D)-(I) |
| iv ➥ (A)-(III), (B)-(IV), (C)-(II), (D)-(I) |
| Best Explanation: Answer: (I) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q87➡ | The average time required to search a storage location in memory and obtain its contents is called: |
| i ➥ Access time |
| ii ➥ Latency time |
| iii ➥ Response time |
| iv ➥ Reading time |
| Best Explanation: Answer: (I) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q88➡ | Which of the following statements are CORRECT ? (A) A process always check state of currently executing process to enter critical schema. (B) Spin locks uses busy waiting. (C) Periodically testing a variable until some value appear is known as busy waiting. (D) Critical region is a part of program, where shared memory is kept. (E) Printer daemon, continuously checks to see if there are any file to be printed. Choose the correct answer from the options given below : |
| i ➥ (A) and (B) Only |
| ii ➥ (B) and (C) Only |
| iii ➥ (B) and (D) Only |
| iv ➥ (B) and (E) Only |
| Best Explanation: Answer: (III) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q89➡ | 2-3-4 trees are B – trees of order 4. They are isometric of trees. |
| i ➥ AVL |
| ii ➥ AA |
| iii ➥ 2-3 |
| iv ➥ Red-Black |
| Best Explanation: Answer: (IV) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
Q90➡ |  R R(A) Reflexive (B) Symmetric (C) Transitive (D) Assymmetric Choose the correct answer from the options given below : |
| i ➥ (A) and (B) Only |
| ii ➥ (B) and (C) Only |
| iii ➥ (A), (C) and (D) Only |
| iv ➥ (A), (B) and (C) Only |
| Best Explanation: Answer: (IV) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q91➡ | Comprehension: Food X contains 6 units of Vitamin D per gram and 7 units of Vitamin E per gram and cost is Rs 12 per gram. Food Y contains 8 units of vitamin D per gram and 12 units of Vitamin E per gram and cost is Rs 20 per gram. The daily minimum requirements of vitamin D and E are 100 units and 120 units respectively. Suppose x is quantity (in gram) of food X, y is quantity (in gram) of food Y. Answering the following question based on the above paragraph given. The minimum cost of food is : |
| i ➥ 205 |
| ii ➥ 250 |
| iii ➥ 330 |
| iv ➥ 200 |
| Best Explanation: Answer: (I) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q92➡ | Comprehension: Food X contains 6 units of Vitamin D per gram and 7 units of Vitamin E per gram and cost is Rs 12 per gram. Food Y contains 8 units of vitamin D per gram and 12 units of Vitamin E per gram and cost is Rs 20 per gram. The daily minimum requirements of vitamin D and E are 100 units and 120 units respectively. Suppose x is quantity (in gram) of food X, y is quantity (in gram) of food Y. Answering the following question based on the above paragraph given. Which of the following are quantities (in grams) of food X and Y respectively when the cost of food is minimum: |
| i ➥ |
| ii ➥ |
| iii ➥ |
| iv ➥ 0 and 10 |
| Best Explanation: Answer: (II) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q93➡ | Comprehension: Food X contains 6 units of Vitamin D per gram and 7 units of Vitamin E per gram and cost is Rs 12 per gram. Food Y contains 8 units of vitamin D per gram and 12 units of Vitamin E per gram and cost is Rs 20 per gram. The daily minimum requirements of vitamin D and E are 100 units and 120 units respectively. Suppose x is quantity (in gram) of food X, y is quantity (in gram) of food Y. Answering the following question based on the above paragraph given. Which of the following constrains when formulating the LPP ? |
| i ➥ 6x + 7y <= 100, 8x + 12y <= 120, x, y >= 0 |
| ii ➥ 6x + 8y <= 100, 7x + 12y <= 120, x, y >= 0 |
| iii ➥ 6x + 7y >= 100, 8x + 12y >= 120, x, y >= 0 |
| iv ➥ 6x + 8y >= 100, 7x + 12y >= 120, x, y >= 0 |
| Best Explanation: Answer: (IV) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q94➡ | Comprehension: Food X contains 6 units of Vitamin D per gram and 7 units of Vitamin E per gram and cost is Rs 12 per gram. Food Y contains 8 units of vitamin D per gram and 12 units of Vitamin E per gram and cost is Rs 20 per gram. The daily minimum requirements of vitamin D and E are 100 units and 120 units respectively. Suppose x is quantity (in gram) of food X, y is quantity (in gram) of food Y. Answering the following question based on the above paragraph given. The dual of the formulated LPP is: |
i ➥ 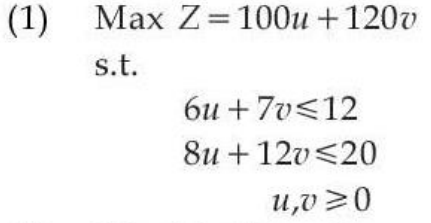 = 0″> = 0″> |
ii ➥ 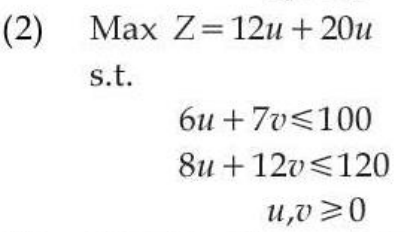 = 0″> = 0″> |
iii ➥ 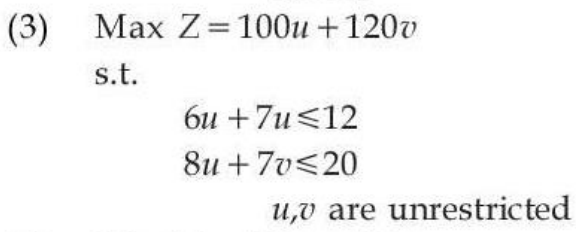 |
iv ➥ 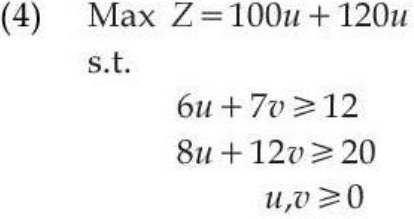 = 12
8u + 12v >= 20
u, v >= 0″> = 12
8u + 12v >= 20
u, v >= 0″> |
| Best Explanation: Answer: (I) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q95➡ | Comprehension: Food X contains 6 units of Vitamin D per gram and 7 units of Vitamin E per gram and cost is Rs 12 per gram. Food Y contains 8 units of vitamin D per gram and 12 units of Vitamin E per gram and cost is Rs 20 per gram. The daily minimum requirements of vitamin D and E are 100 units and 120 units respectively. Suppose x is quantity (in gram) of food X, y is quantity (in gram) of food Y. Answering the following question based on the above paragraph given. The cost function of total food is : |
| i ➥ Z = 6x + 7y |
| ii ➥ Z = 8x + 12y |
| iii ➥ Z = 12x + 20y |
| iv ➥ Z = 20x + 12y |
| Best Explanation: Answer: (III) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
Q96➡ | 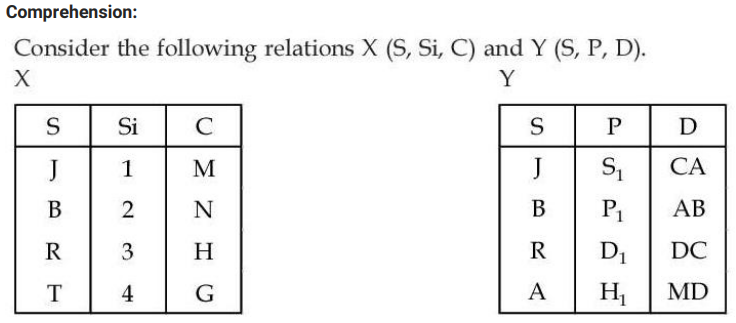 Number of tuples by applying right outer join on relation X and Y is/are: |
| i ➥ 16 |
| ii ➥ 5 |
| iii ➥ 3 |
| iv ➥ 4 |
| Best Explanation: Answer: (IV) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
Q97➡ |  Find the number of tuples by applying the operation |
| i ➥ 1 |
| ii ➥ 3 |
| iii ➥ 4 |
| iv ➥ 6 |
| Best Explanation: Answer: (III) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
Q98➡ |  Which of the following join is used to get all the tuples of relation X and Y with Null values of corresponding missing values? |
| i ➥ Left outer join |
| ii ➥ Right outer join |
| iii ➥ Natural join |
| iv ➥ Full outer join |
| Best Explanation: Answer: (IV) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
Q99➡ |  Number of tuples obtained by applying cartesian product over X and Y are: |
| i ➥ 16 |
| ii ➥ 12 |
| iii ➥ 04 |
| iv ➥ 32 |
| Best Explanation: Answer: (I) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
Q100➡ |  Question- |
i ➥ 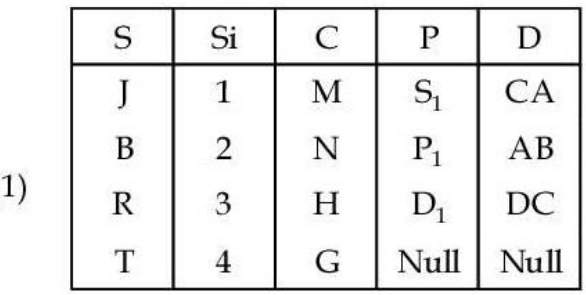 |
ii ➥ 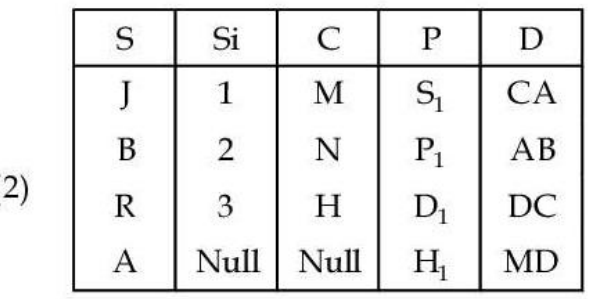 |
iii ➥ 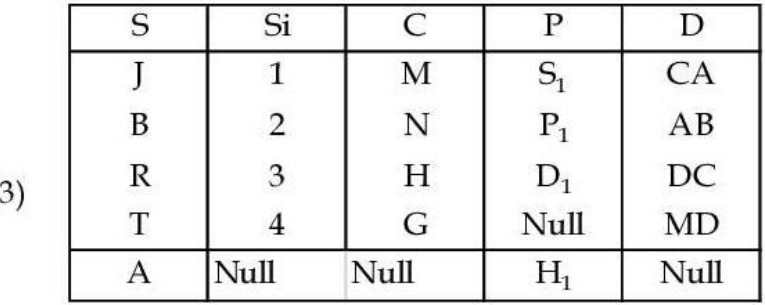 |
| iv ➥ None of these |
| Best Explanation: Answer: (II) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |

