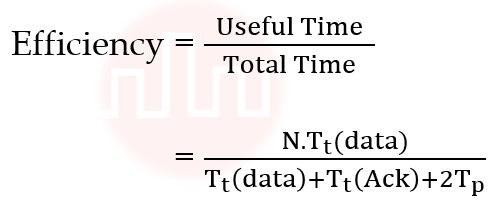GATE 2021 Computer Science and information technology Set-1
gate 2021 cse answer key
[Q1 – Q10 Multiple choice Question(MCQ),carry ONE mark each (for each wrong answer: – 1/3) ]
| Q1➡ | Compiler Design Consider the following statements. S1: Every SLR(1) grammar is unambiguous but there are certain unambiguous grammars that are not SLR(1). S2: For any context-free grammar, there is a parser that takes at most O(n3 ) Which one of the following options is correct? |
| i ➥ S1 is true and S2 is true |
| ii ➥ S1 is true and S2 is false |
| iii ➥ S1 is false and S2 is true |
| iv ➥ S1 is false and S2 is false |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Parser | Help-Line |
| Q2➡ | Digital Logic Design Let the representation of a number in base 3 be 210. What is the hexadecimal representation of the number? |
| i ➥ 528 |
| ii ➥ D2 |
| iii ➥ 15 |
| iv ➥ 21 |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Number System | Help-Line |
| Q3➡ | Data Structure Consider the following statements. S1:The sequence of procedure calls corresponds to a preorder traversal of the activation tree. S2:The sequence of procedure returns corresponds to a postorder traversal of the activation tree. Which one of the following options is correct? |
| i ➥ S1 is false and S2 is true |
| ii ➥ S1 is false and S2 is false |
| iii ➥ S1 is true and S2 is false |
| iv ➥ S1 is true and S2 is true |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Graph and Tree | Help-Line |
| Q4➡ | Algorithms Consider the following three Functions 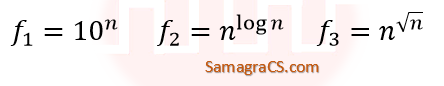 Which one of the following options arranges the functions in the increasing order of asymptotic growth rate? |
| i ➥ f2, f1, f3 |
| ii ➥ f3, f2, f1 |
| iii ➥ f2, f3, f1 |
| iv ➥ f1, f2, f3 |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Asymptotic Complexity | Help-Line |
| Q5➡ | Data Structure A binary search tree T contains n distinct elements. What is the time complexity of picking an element in T that is smaller than the maximum element in T? |
| i ➥ Θ(logn) |
| ii ➥ Θ(nlogn) |
| iii ➥ Θ(1) |
| iv ➥ Θ(n) |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Binary Search Tree | Help-Line |
| Q6➡ | Algorithms Consider the following array: 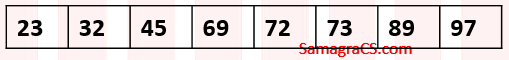 Which algorithm out of the following options uses the least number of comparisons (among the array elements) to sort the above array in ascending order? |
| i ➥ Quicksort using the last element as pivot |
| ii ➥ Selection sort |
| iii ➥ Mergesort |
| iv ➥ Insertion sort |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Time Complexity | Help-Line |
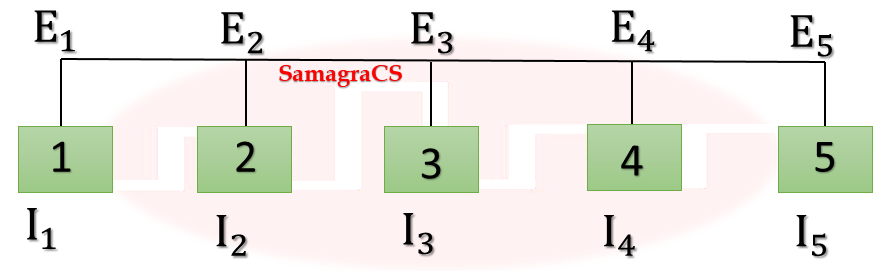
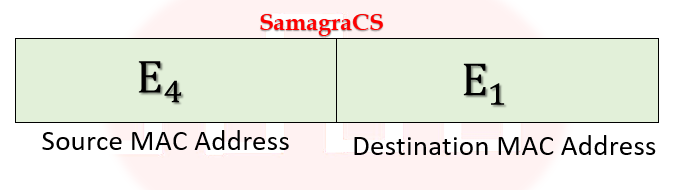
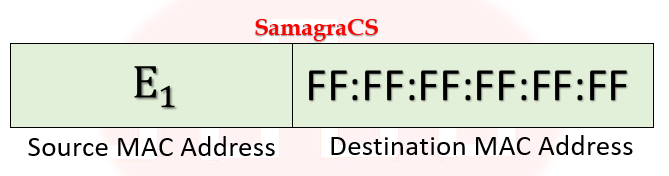
| Q7➡ | Computer Network Consider the following two statements. S1: Destination MAC address of an ARP reply is a broadcast address. S2: Destination MAC address of an ARP request is a broadcast address. Which of the following choices is correct? |
| i ➥ S1 is true and S2 is false. |
| ii ➥ Both S1 and S2 are false. |
| iii ➥ Both S1 and S2 are true. |
| iv ➥ S1 is false and S2 is true. |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Network Protocols | Help-Line |
| Q8➡ | Algorithms Let P be an array containing n integers. Let t be the lowest upper bound on the number of comparisons of the array elements, required to find the minimum and maximum values in an arbitrary array of n elements. Which one of the following choices is correct? |
i ➥ 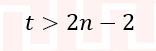 |
ii ➥ 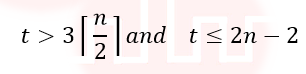 |
iii ➥ 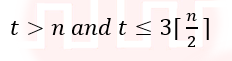 |
iv ➥ 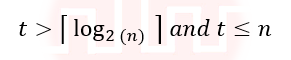 |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Time Complexity | Help-Line |
| Q9➡ | Theory of Computation Suppose that L1is a regular language and L2is a context free language. Which one of the following languages is NOT necessarily context free? |
| i ➥ L1. L2 |
| ii ➥ L1 − L2 |
| iii ➥ L1 ∩ L2 |
| iv ➥ L1 ∪ L2 |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Closure Property | Help-Line |
| Q10➡ | Engineering Mathematics Let p and q be two propositions. Consider the following two formulae in propositional logic. 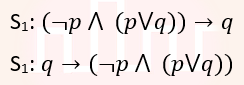 Which one of the following choices is correct? |
| i ➥ S1 is a tautology but S2 is not a tautology. |
| ii ➥ Both S1 and S2 are tautologies. |
| iii ➥ Neither S1 and S2 are tautology. |
| iv ➥ S1 is not a tautology but S2 is a tautology. |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Propositional Logic | Help-Line |
[Q11 – Q15 Multiple choice Question(MCQ),carry ONE mark each (no negative marks) ]
| Q11➡ | Database Management System Suppose a database system crashes again while recovering from a previous crash. Assume checkpointing is not done by the database either during the transactions or during recovery. Which of the following statements is/are correct? |
| i ➥ All the transactions that are already undone and redone will not be recovered again. |
| ii ➥ The same undo and redo list will be used while recovering again. |
| iii ➥ The database will become inconsistent. |
| iv ➥ The system cannot recover any further. |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Transaction management | Help-Line |
| Q12➡ | Operating System Consider a linear list based directory implementation in a file system. Each directory is a list of nodes, where each node contains the file name along with the file metadata, such as the list of pointers to the data blocks.Consider a given directory foo. Which of the following operations will necessarily require a full scan of foo for successful completion? |
| i ➥ Opening of an existing file in foo |
| ii ➥ Renaming of an existing file in foo |
| iii ➥ Deletion of an existing file from foo |
| iv ➥ Creation of a new file in foo |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | File System | Help-Line |
| Q13➡ | Operating System Which of the following standard C library functions will always invoke a system call when executed from a single-threaded process in a UNIX/linux operating system? |
| i ➥ malloc |
| ii ➥ strlen |
| iii ➥ exit |
| iv ➥ sleep |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | System Calls | Help-Line |
| Q14➡ | Theory of Computation Let denote an encoding of an automaton M. Suppose that Σ = {0,1}. Which of the following languages is/are NOT recursive? |
| i ➥ L = { | M is a PDA such that L(M) = ∅} |
| ii ➥ L = { | M is a PDA such that L(M) = Σ*} |
| iii ➥ L = { | M is a DFA such that L(M) = Σ*} |
| iv ➥ L = { | M is a DFA such that L(M) = ∅} |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Recursive Language | Help-Line |
| Q15➡ | Operating System In the context of operating systems, which of the following statements is/are correct with respect to paging? |
| i ➥ Multilevel paging is necessary to support pages of different sizes. |
| ii ➥ Paging helps solve the issue of external fragmentation. |
| iii ➥ Page size has no impact on internal fragmentation. |
| iv ➥ Paging incurs memory overheads. |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Memory Management | Help-Line |
[Q16 – Q25 Numerical Answer Type(NAT),carry ONE mark each (no negative marks) ]
| Q16➡ | Computer Organization Consider a computer system with a byte-addressable primary memory of size 232bytes. Assume the computer system has a direct-mapped cache of size 32 KB (1 KB = 210bytes), and each cache block is of size 64 bytes. The size of the tag field is __ bits. |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Cache | Help-Line |
| Q17➡ | Engineering Mathematics Consider the following expression 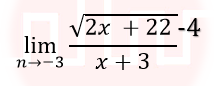 The value of the above expression (rounded to 2 decimal places) is____ |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Calculus | Help-Line |
| Q18➡ | Operating System Three processes arrive at time zero with CPU bursts of 16, 20 and 10 milliseconds. If the scheduler has prior knowledge about the length of the CPU bursts, the minimum achievable average waiting time for these three processes in a non-preemptive scheduler (rounded to nearest integer) is _______ milliseconds. |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | CPU Scheduling | Help-Line |
| Q19➡ | Engineering Mathematics In an undirected connected planar graph G, there are eight vertices and five faces. The number of edges in G is _____. |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Graph Theory | Help-Line |
| Q20➡ | Database Management System A relation r(A, B) in a relational database has 1200 tuples. The attribute A has integer values ranging from 6 to 20, and the attribute B has integer values ranging from 1 to 20. Assume that the attributes A and B are independently distributed. 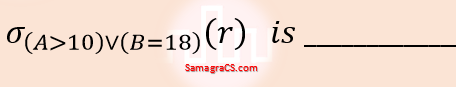 |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Relational Database | Help-Line |
| Q21➡ | Operating System There are 6 jobs with distinct difficulty levels, and 3 computers with distinct processing speeds. Each job is assigned to a computer such that: • The fastest computer gets the toughest job and the slowest computer gets the easiest job. • Every computer gets at least one job. The number of ways in which this can be done is ____ |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | CPU Scheduling | Help-Line |
| Q23➡ | Digital Logic Design Consider the following representation of a number in IEEE 754 single-precision floating point format with a bias of 127. S : 1 E : 10000001 F : 11110000000000000000000 Here S, E and F denote the sign, exponent and fraction components of the floating point representation. The decimal value corresponding to the above representation (rounded to 2 decimal places) is _ |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Number System | Help-Line |
| Q24➡ | Data Structure Consider the following sequence of operations on an empty stack. push(54); push(52); pop(); push(55); push(62); s=pop(); Consider the following sequence of operations on an empty queue. enqueue(21); enqueue(24); dequeue(); enqueue(28); enqueue(32); q = dequeue(); The value of s + q is __ |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Queues and stacks | Help-Line |
| Q25➡ | Algorithm Consider the following undirected graph with edge weights as shown: 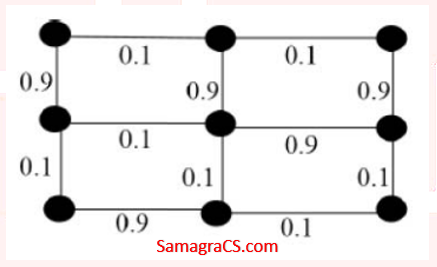 The number of minimum-weight spanning trees of the graph is ______ |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Minimum Spanning Tree | Help-Line |
[Q26 – Q39 Multiple choice Question(MCQ),carry TWO marks each (for each wrong answer: – 2/3) ]
| Q26➡ | Algorithm Consider the following recurrence relation. 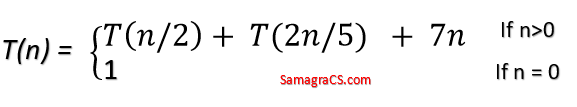 Which one of the following options is correct? |
i ➥ 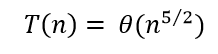 |
| ii ➥ |
| iii ➥ |
iv ➥ 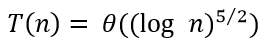 |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Time Complexity | Help-Line |
| Q27➡ | Digital Logic Design Consider a 3-bit counter, designed using T flip-flops, as shown below: 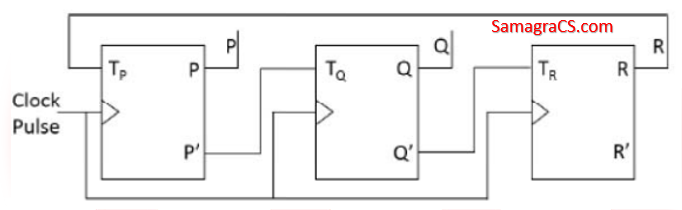 Assuming the initial state of the counter given by PQR as 000, what are the next three states? |
| i ➥ 011, 101, 111 |
| ii ➥ 001, 010, 000 |
| iii ➥ 001, 010, 111 |
| iv ➥ 011, 101, 000 |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Sequential Circuits | Help-Line |
| Q28➡ | Database Management System The following relation records the age of 500 employees of a company, where empNo (indicating the employee number) is the key: 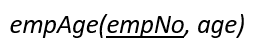 empAge (empNo, age) Consider the following relational algebra expression: 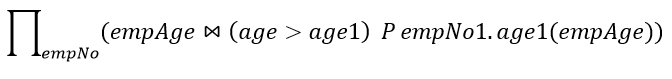 What does the above expression generate? |
| i ➥ Employee numbers of only those employees whose age is more than the age of exactly one other employee |
| ii ➥ Employee numbers of all employees whose age is not the minimum. |
| iii ➥ Employee numbers of all employees whose age is the minimum. |
| iv ➥ Employee numbers of only those employees whose age is the maximum. |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Relational Algebra | Help-Line |
| Q29➡ | Compiler Consider the following grammar (that admits a series of declarations, followed by expressions) and the associated syntax directed translation (SDT) actions, given as pseudo-code: P ⟶ D* E* D ⟶ int ID {record that ID.lexeme is of type int} D ⟶ bool ID {record that ID.lexeme is of type bool} E ⟶ E1 + E2 {check that E1.type = E2.type = int; set E.type := int} E ⟶ !E1 {check that E1.type = bool; set E.type := bool} E ⟶ ID {set E.type := int} With respect to the above grammar, which one of the following choices is correct? |
| i ➥ The actions can be used to type-check syntactically correct boolean variable declarations and boolean expressions |
| ii ➥ The actions can be used to correctly type-check any syntactically correct program. |
| iii ➥ The actions will lead to an infinite loop. |
| iv ➥ The actions can be used to type-check syntactically correct integer variable declarations and integer expressions |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Syntax Directed Translation | Help-Line |
| Q30➡ | Database Management System Let ri(z) and wi(z) denote read and write operations respectively on a data item z by a transaction Ti. Consider the following two schedules. S1: r1(x) r1(y) r2(x) r2(y) w2(y) w1(x) S2: r1(x) r2(x) r2(y) w2(y) r1(y) w1(x) Which one of the following options is correct? |
| i ➥ Both S1 and S2 are conflict serializable. |
| ii ➥ Neither S1 nor S2 is conflict serializable. |
| iii ➥ S1 is conflict serializable, and S2 is not conflict serializable. |
| iv ➥ S1 is not conflict serializable, and S2 is conflict serializable. |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Transaction management | Help-Line |
| Q31➡ | Theory of Computation For a Turing machine M, denotes an encoding of M. Consider the following two languages. L1=〈M〉|M takes more than 2021 steps on all inputs L2=〈M〉|M takes more than 2021 steps on some input Which one of the following options is correct? |
| i ➥ L1 is undecidable and L2 is decidable. |
| ii ➥ Both L1and L2 are decidable. |
| iii ➥ Both L1and L2 are undecidable. |
| iv ➥ L1 is decidable and L2 is undecidable. |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Decidability and Undecidability | Help-Line |
| Q32➡ | Theory of Computation Consider the following language. L={w ∈{0,1}* | ends with the sub-string 011} Which one of the following deterministic finite automata accepts L ? |
i ➥ 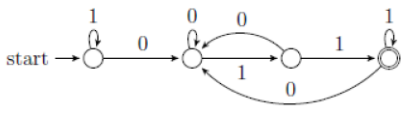 |
ii ➥ 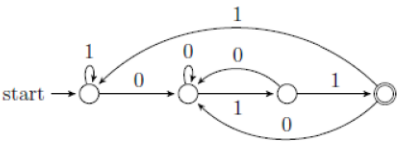 |
iii ➥ 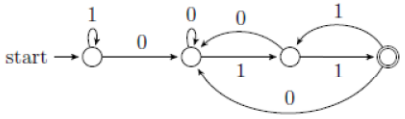 |
iv ➥ 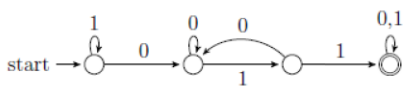 |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | DFA | Help-Line |
Q33➡ | Programming 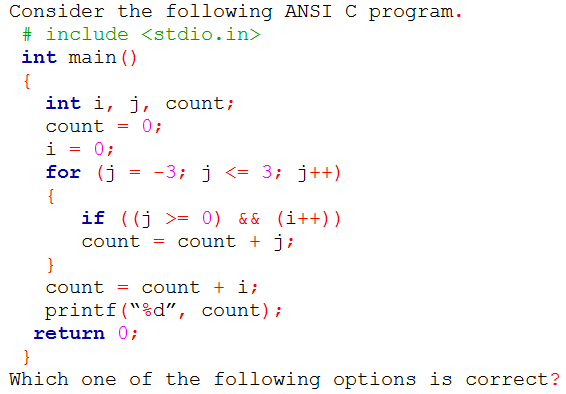 |
| i ➥ The program will compile successfully and output 8 when executed. |
| ii ➥ The program will not compile successfully. |
| iii ➥ The program will compile successfully and output 13 when executed. |
| iv ➥ The program will compile successfully and output 10 when executed. |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | C Programming | Help-Line |
| Q34➡ | Engineering Mathematics Let G = (V, E) be an undirected unweighted connected graph. The diameter of G is defined as:  Let M be the adjacency matrix of G. Define graph G2 on the same set of vertices with adjacency matrix N, where  Which one of the following statements is true? |
i ➥ 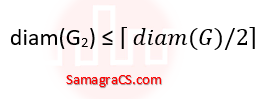 |
ii ➥  |
iii ➥  |
iv ➥ 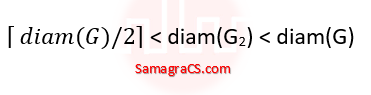 |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Graph Theory | Help-Line |
| Q35➡ | Compiler Design Consider the following context-free grammar where the set of terminals is {a, b, c, d, f} 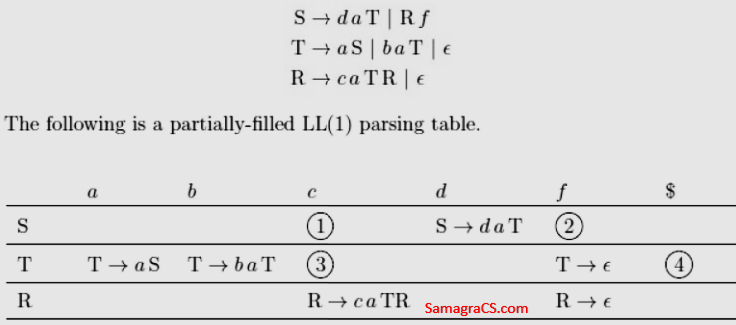 Which one of the following choices represents the correct combination for the numbered cells in the parsing table (“blank” denotes that the corresponding cell is empty)? |
| i ➥ ① S ⟶ Rf ② S ⟶ Rf ③ T ⟶ ∊ ④ T ⟶ ∊ |
| ii ➥ ① blank ② S ⟶ Rf ③ T ⟶ ∊ ④ T ⟶ ∊ |
| iii ➥ ① blank ② S ⟶ Rf ③ blank ④ blank |
| iv ➥ ① S ⟶ Rf ② blank ③ blank ④ T ⟶ ∊ |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Parsers | Help-Line |
| Q36➡ | Engineering Mathematics Consider the two statements. S1: There exist random variables X and Y such that (E[(X-E(X)) (Y-E(Y))])2>Var[X] Var[Y] S2: For all random variables X and Y, Cov[X,Y]=E[|X-E[X]| |Y-E[Y]|] Which one of the following choices is correct? |
| i ➥ Both S1 and S2 are false. |
| ii ➥ S1 is false, but S2 is true. |
| iii ➥ Both S1 and S2 are true. |
| iv ➥ S1 is true, but S2 is false. |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Probability and stattistics | Help-Line |
| Q37➡ | Engineering Mathematics Let G be a group of order 6, and H be a subgroup of G such that 1 < |H| < 6. Which one of the following options is correct? |
| i ➥ G may not be cyclic, but H is always cyclic. |
| ii ➥ Both G and H may not be cyclic. |
| iii ➥ Both G and H are always cyclic. |
| iv ➥ G is always cyclic, but H may not be cyclic. |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Group Theory | Help-Line |
| Q38➡ | Database Management System Consider the relation R(P, Q, S, T, X, Y, Z, W) with the following functional dependencies 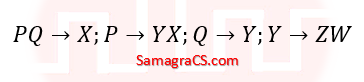 Consider the decomposition of the relation R into the consistent relations according to the following two decomposition schemes. D1: R=[(P,Q,S,T); (P,T,X); (Q,Y); (Y,Z,W)] D2: R=[(P,Q,S);(T,X);(Q,Y);(Y,Z,W)] Which one of the following options is correct? |
| i ➥ Both D1 and D2are lossy decompositions. |
| ii ➥ D1 is a lossless decomposition, but D2 is a lossy decomposition. |
| iii ➥ D1 is a lossy decomposition, but D2 is a lossless decomposition. |
| iv ➥ Both D1 and D2 are lossless decompositions. |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Normalization | Help-Line |
Q39➡ | Digital Logic Design 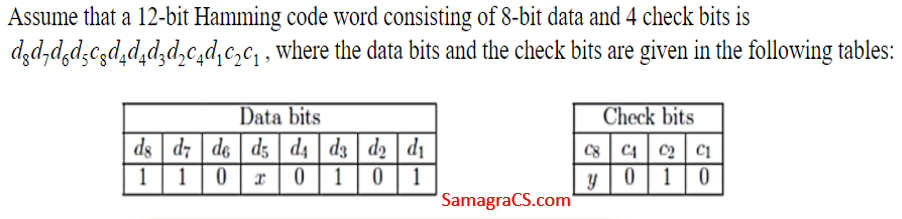 Which one of the following choices gives the correct values of x and y? |
| i ➥ x is 1 and y is 0 |
| ii ➥ x is 0 and y is 0 |
| iii ➥ x is 0 and y is 1 |
| iv ➥ x is 1 and y is 1 |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Number Systems | Help-Line |
[Q40 – Q47 Multiple select Question(MSQ),carry TWO marks each (no negative mark) ]
| Q40➡ | Data Structure Consider a dynamic hashing approach for 4-bit integer keys: 1. There is a main hash table of size 4. 2. The 2 least significant bits of a key is used to index into the main hash table. 3. Initially, the main hash table entries are empty. 4. Thereafter, when more keys are hashed into it, to resolve collisions, the set of all keys corresponding to a main hash table entry is organized as a binary tree that grows on demand. 5. First, the 3rd least significant bit is used to divide the keys into left and right subtrees. 6. To resolve more collisions, each node of the binary tree is further sub-divided into left and right subtrees based on the 4th least significant bit. 7. A split is done only if it is needed, i.e., only when there is a collison. Consider the following state of the hash table. 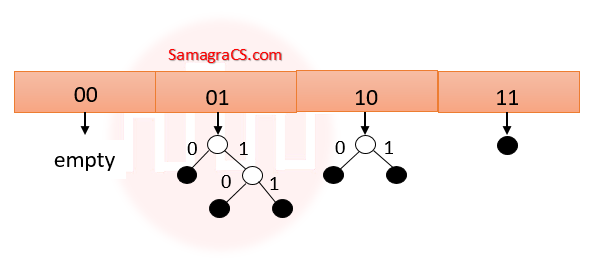 Which of the following sequences of key insertions can cause the above state of the hash table (assume the keys are in decimal notation)? |
| i ➥ 9, 5, 13, 6, 10, 14 |
| ii ➥ 10, 9, 6, 7, 5, 13 |
| iii ➥ 5, 9, 4, 13, 10, 7 |
| iv ➥ 9, 5, 10, 6, 7, 1 |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Hashing | Help-Line |
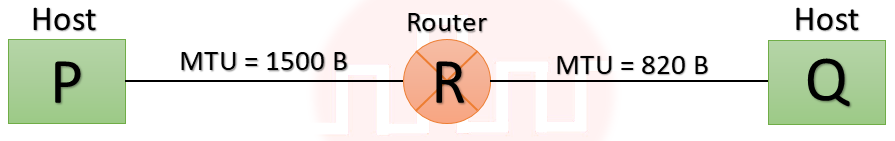
| Q41➡ | Computer Network Consider two hosts P and Q connected through a router R. The maximum transfer unit (MTU) value of the link between P and R is 1500 bytes, and between R and Q is 820 bytes. A TCP segment of size 1400 bytes was transferred from P to Q through R, with IP identification value as 0x1234. Assume that the IP header size is 20 bytes. Further, the packet is allowed to be fragmented, i.e., Don’t Fragment (DF) flag in the IP header is not set by P. Which of the following statements is/are correct? |
| i ➥ If the second fragment is lost, R will resend the fragment with the IP identification value 0x1234. |
| ii ➥ TCP destination port can be determined by analysing only the second fragment. |
| iii ➥ Two fragments are created at R and the IP datagram size carrying the second fragment is 620 bytes. |
| iv ➥ If the second fragment is lost, P is required to resend the whole TCP segment. |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Fragmentation | Help-Line |
| Q42➡ | Computer Network A TCP server application is programmed to listen on port number P on host S. A TCP client is connected to the TCP server over the network. Consider that while the TCP connection was active, the server machine S crashed and rebooted. Assume that the client does not use the TCP keep alive timer. Which of the following behaviours is/are possible? |
| i ➥ If the client sends a packet after the server reboot, it will receive a FIN segment. |
| ii ➥ The TCP server application on S can listen on P after reboot. |
| iii ➥ If the client sends a packet after the server reboot, it will receive a RST segment. |
| iv ➥ If the client was waiting to receive a packet, it may wait indefinitely. |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | TCP | Help-Line |
| Q43➡ | Engineering Mathematics A relation R is said to be circular of aRb and bRc together imply cRa. Which of the following options is/are correct? |
| i ➥ If a relation S is circular and symmetric, then S is an equivalence relation. |
| ii ➥ If a relation S is transitive and circular, then S is an equivalence relation. |
| iii ➥ If a relation S is reflexive and symmetric, then S is an equivalence relation. |
| iv ➥ If a relation S is reflexive and circular, then S is an equivalence relation. |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Set Theory | Help-Line |
Q44➡ | Digital Logic Design 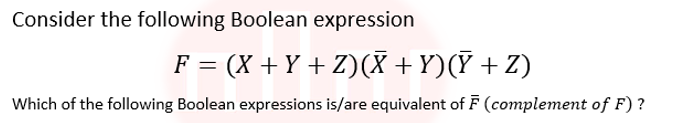 |
| i ➥ |
| ii ➥ |
| iii ➥ |
| iv ➥ |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Boolean Function | Help-Line |
| Q45➡ | Engineering Mathematics An articulation point in a connected graph is a vertex such that removing the vertex and its incident edges disconnects the graph into two or more connected components. Let T be a DFS tree obtained by doing DFS in a connected undirected graph G. Which of the following options is/are correct? |
| i ➥ A leaf of T can be an articulation point in G. |
| ii ➥ If u is an articulation point in G such that x is an ancestor of u in T and y is a descendent of u in T, then all paths from x to y in G must pass through u. |
| iii ➥ Root of T is an articulation point in G if and only if it has 2 or more children |
| iv ➥ Root of T can never be an articulation point in G. |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | BFS and DFS | Help-Line |
| Q46➡ | Algorithms Define Rn to be the maximum amount earned by cutting a rod of length n metres into one or more pieces of integer length and selling them. For i > 0, let p[i] denote the selling price of a rod whose length is i meters. Consider the array of prices: p[1] = 1, p[2] = 5, p[3] = 8, p[4] = 9, p[5] = 10, p[6] = 17, p[7] = 18 Which of the following statements is/are correct about R7? |
| i ➥ R7 cannot be achieved by a solution consisting of three pieces. |
| ii ➥ R7 is achieved by three different solutions. |
| iii ➥ R7=19 |
| iv ➥ R7=18 |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Dynamic Programming | Help-Line |
| Q47➡ | Operating System Consider the following pseudocode, where S is a semaphore initialized to 5 in line#2 and counter is a shared variable initialized to 0 in line#1. Assume that the increment operation in line#7 is not atomic. 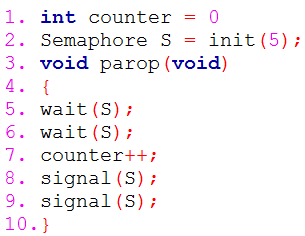 If five threads execute the function parop concurrently, which of the following program behaviour(s) is/are possible? |
| i ➥ The value of counter is 0 after all the threads successfully complete the execution of parop. |
| ii ➥ The value of counter is 5 after all the threads successfully complete the execution of parop. |
| iii ➥ There is a deadlock involving all the threads. |
| iv ➥ The value of counter is 1 after all the threads successfully complete the execution of parop. |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Semaphore | Help-Line |
[Q48 – Q55 Numerical Answer Type(NAT),carry TWO marks each (no negative mark) ]
| Q48➡ | Compiler Consider the following C code segment: a = b + c; e = a + 1; d = b + c; f = d + 1; g = e + f; In a compiler, this code segment is represented internally as a directed acyclic graph (DAG). The number of nodes in the DAG is _______. |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Syntax tree | Help-Line |
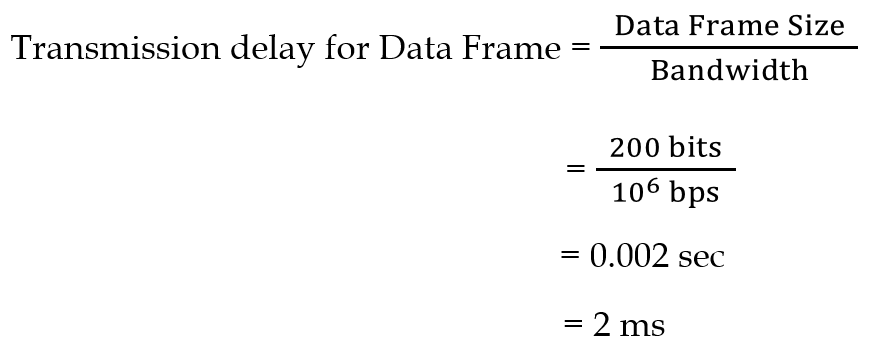
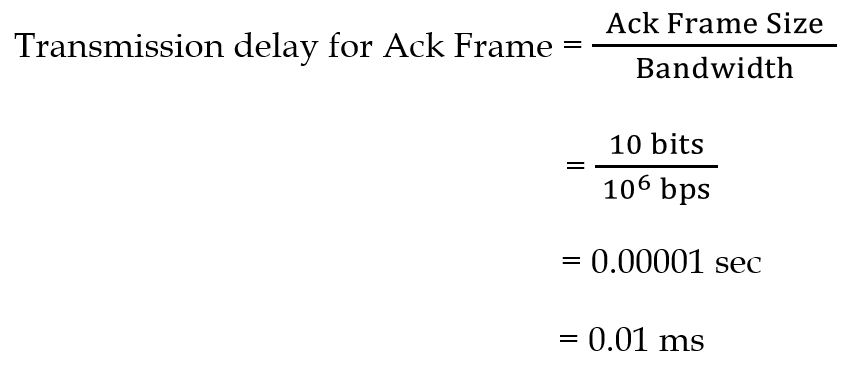
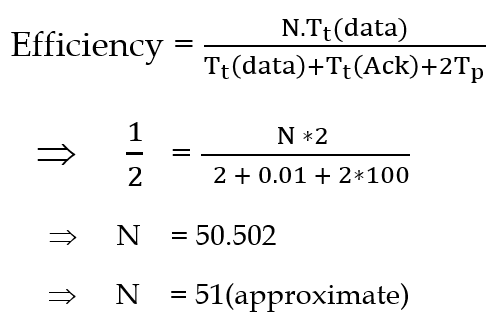
| Q49➡ | Computer Network Consider the sliding window flow-control protocol operating between a sender and a receiver over a full-duplex error-free link. Assume the following: • The time taken for processing the data frame by the receiver is negligible. • The time taken for processing the acknowledgement frame by the sender is negligible. • The sender has an infinite number of frames available for transmission. • The size of the data frame is 2,000 bits and the size of the acknowledgment frame is 10 bits. • The link data rate in each direction is 1 Mbps (=106bits per second). • One way propagation delay of the link is 100 milliseconds. The minimum value of the sender’s window size in terms of the number of frames, (rounded to the nearest integer) needed to achieve a link utilization of 50% is _____. |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Flow Control | Help-Line |
Q50➡ | Programming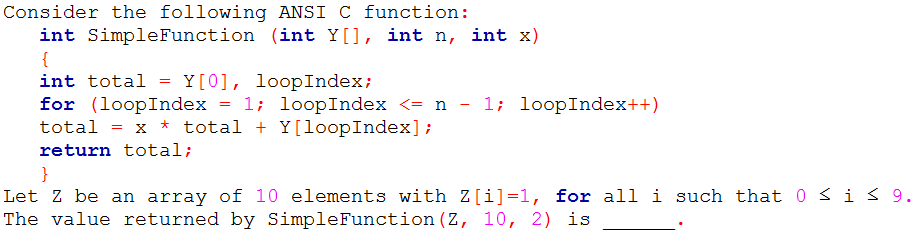 |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Function | Help-Line |
| Q51➡ | Computer Organization Consider the following instruction sequence where registers R1, R2 and R3 are general purpose and MEMORY[X] denotes the content at the memory location X. 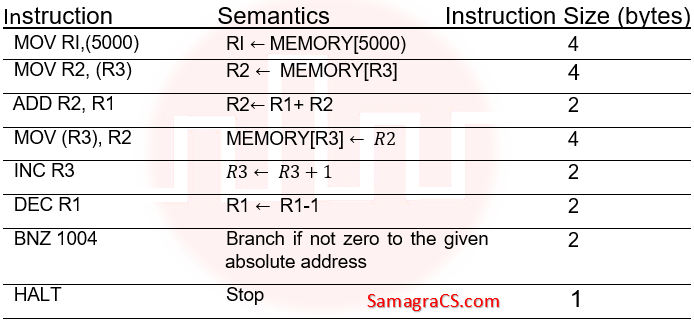 Assume that the content of the memory location 5000 is 10, and the content of the register R3 is 3000. The content of each of the memory locations from 3000 to 3010 is 50. The instruction sequence starts from the memory location 1000. All the numbers are in decimal format. Assume that the memory is byte addressable. After the execution of the program, the content of memory location 3010 is _ |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Machine Instructions | Help-Line |
| Q52➡ | Engineering Mathematics A sender (S) transmits a signal, which can be one of the two kinds: H and L with probabilities 0.1 and 0.9 respectively, to a receiver (R). In the graph below, the weight of edge (u, v) is the probability of receiving v when u is transmitted, where u, v ∈ {H, L}. For example, the probability that the received signal is L given the transmitted signal was H, is 0.7. 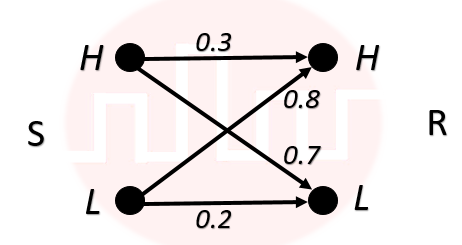 If the received signal is H, the probability that the transmitted signal was H (rounded to 2 decimal places) is ________. |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Probability and statistics | Help-Line |
Q53➡ | Theory of Computation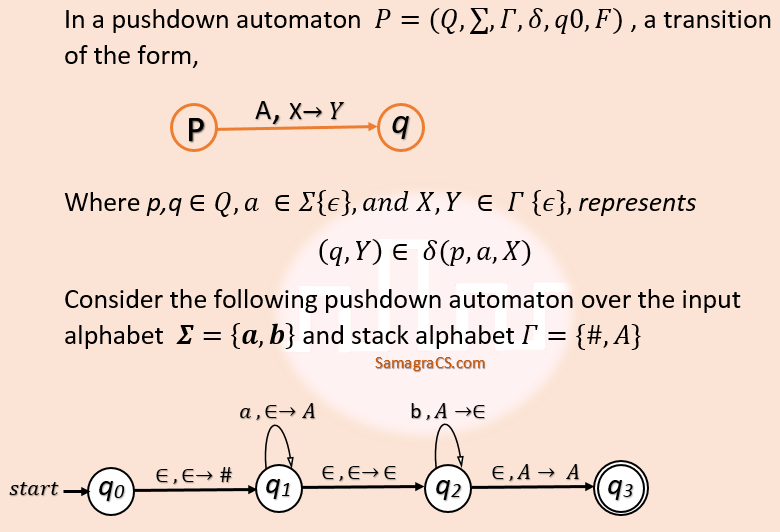 The number of strings of length 100 accepted by the above pushdown automaton is _____. |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Push Down Automata | Help-Line |
| Q54➡ | Engineering Mathematics Consider the following matrix. 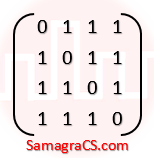 The largest eigenvalue of the above matrix is___________ |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Linear Algebra | Help-Line |
| Q55➡ | Computer Organization A five-stage pipeline has stage delays of 150, 120, 150, 160 and 140 nanoseconds. The registers that are used between the pipeline stages have a delay of 5 nanoseconds each. The total time to execute 100 independent instructions on this pipeline, assuming there are no pipeline stalls, is ___ nanoseconds. |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Pipelinig | Help-Line |