Previous Year Question Papers for UGC NET Jan 2025 Computer Science with Solutions
| Q1➡ | Computer Network The network using CSMA/CD has a bandwidth of 20 Mbps. If the maximum propagation time is 25µ sec (microsecond), what is the minimum size of the frame? |
| i ➥ 500 bits |
| ii ➥ 1000 bits |
| iii ➥ 1500 bits |
| iv ➥ 2000 bits |
| Best Explanation: Answer: II Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q2➡ | Artificial Intelligence Which of the following is not a component of the classic Planning Definition? |
| i ➥ Init |
| ii ➥ Domain |
| iii ➥ Action |
| iv ➥Goal |
| Best Explanation: Answer: II Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q3➡ | Theory of Computation Which of the following CFG(s) is/are in Chomsky Normal Form (All capital letters are variables & lower case are terminals)? a) 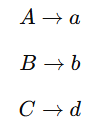 b) 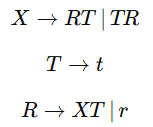 c) 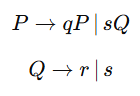 d) 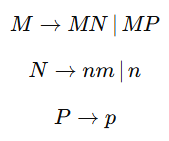 Choose the correct answer from the options given below |
| i ➥ A & B only |
| ii ➥ B only |
| iii ➥ C only |
| iv ➥ B & D only |
| Best Explanation: Answer: II Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q4➡ | Artificial Intelligence What is the correct sequence of steps used by knowledge base designing? A. Ask questions about the intended interpretation. B. Choose task domain or world to represent. C. Select atoms to represent propositions of Interest. D. Tell the system propositions that are true in the intended interpretation/axiomatizing the domain. Choose the correct answer from the options given below: |
| i ➥ B, C, D, A |
| ii ➥ B, C, D, A |
| iii ➥C, D, A, B |
| iv ➥ D, A, B, C |
| Best Explanation: Answer: II Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q5➡ | Software Engineering Which one of the following is not a part of requirement management? |
| i ➥ Features Traceability Table |
| ii ➥ Dependency Traceability Table |
| iii ➥ Interface Traceability Table |
| iv ➥Page Traceability Table |
| Best Explanation: Answer: IV Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q6➡ | DBMS What will be the right sequence of the phases of database design? A. Physical Design B. Conceptual Design C. Logical Design D. Requirement Collection and Analysis Choose the correct answer from the options given below: |
| i ➥ D, A, B, C |
| ii ➥ D, B, C, A |
| iii ➥ D, B, A, C |
| iv ➥ D, A, C, B |
| Best Explanation: Answer: II Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q7➡ | Match the LIST-I with LIST-II 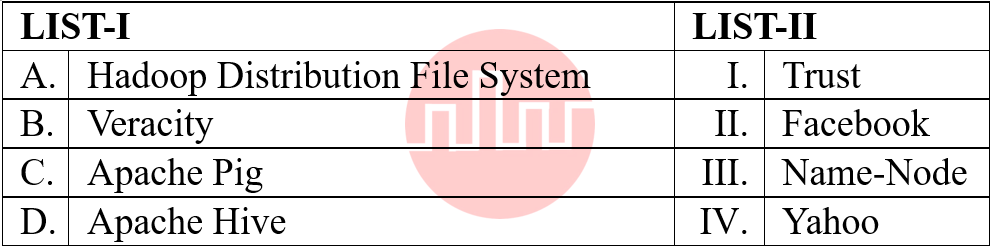 Choose the correct answer from the options given below: |
| i ➥ A-IV, B-III, C-I, D-II |
| ii ➥A-III, B-I, C-IV, D-II |
| iii ➥ A-III, B-I, C-II, D-IV |
| iv ➥A-II, B-III, C-I, D-IV |
| Best Explanation: Answer: III Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q8➡ | Discrete Math Which of the following statements are true about the sets? A. 0∈∅ B. ∅∈{0} C. ∅∈{∅} D. {∅}∈{∅} E. {∅}⊆{∅,{∅}} Choose the correct answer from the options given below: |
| i ➥ A, B, C, D, and E |
| ii ➥ A, B, C, and E only |
| iii ➥ A, C only |
| iv ➥ C and E only |
| Best Explanation: Answer: IV Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q9➡ | Programming Match the LIST-I with LIST-II 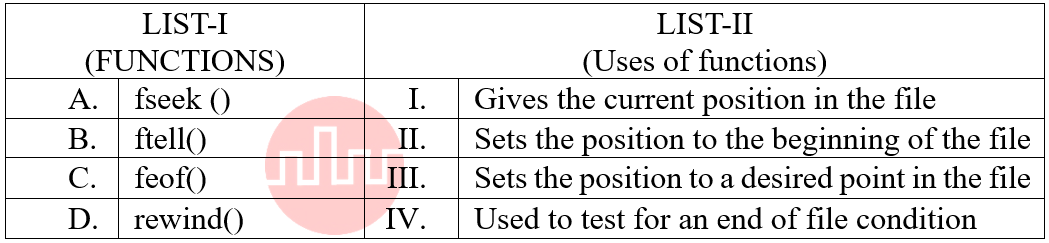 Choose the correct answer from the options given below: |
| i ➥ A-II, B-III, C-I, D-IV |
| ii ➥ A-III, B-I, C-IV, D-II |
| iii ➥ A-III, B-I, CII-, D-IV |
| iv ➥A-II, B-IV, C-III, D-I |
| Best Explanation: Answer: II Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q10➡ | DBMS In concurrency control, phantom problem may occur, when- |
| i ➥ records are inserted |
| ii ➥ records are deleted |
| iii ➥ records are modified |
| iv ➥ records are indexed |
| Best Explanation: Answer: I Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q11➡ | DBMS Which of the following/s is/are FALSE statement? A. An all key relation is always in BCNF since it has no FDs. B. A relation that is not in 4NF due to nontrivial MVD must be decomposed to convert it into a set of relations in 4NF. C. The decomposition removes the redundancy by the MVD. D. 3NF is stronger than BCNF. Choose the correct answer from the options given below: |
| i ➥ A only |
| ii ➥ A. B only |
| iii ➥D only |
| iv ➥ C only |
| Best Explanation: Answer: III Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q12➡ | Computer architecture Correct the order of instruction cycle: A. Read the effective address B. Fetch the information C. Execute the instruction D. Decode the instruction Choose the correct answer from the options given below: |
| i ➥ A, B, C, D |
| ii ➥ B, D, A, С |
| iii ➥ B, A, D, C |
| iv ➥A, B, D, C |
| Best Explanation: Answer: II Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q13➡ | Computer architecture Match the LIST-I with LIST-II 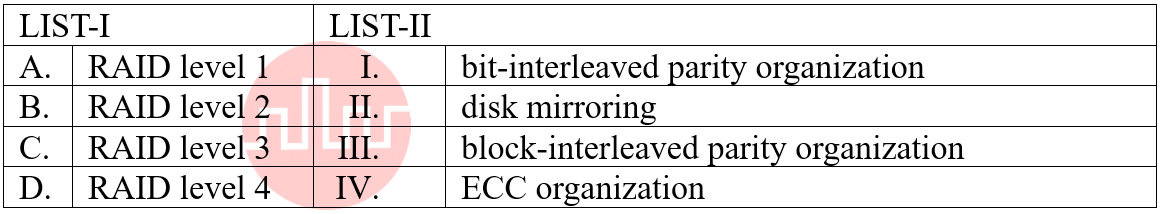 Choose the correct answer from the options given below: |
| i ➥ A-II, B-I, C-IV, D-III |
| ii ➥ A-II, B-IV, C-I, D-III |
| iii ➥ A-III, B-IV, C-I, D-II |
| iv ➥ A-IV, B-III, C-II, D-I |
| Best Explanation: Answer: II Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q14➡ | Computer architecture The entire set of parameters, including return address that is stored for a procedure invocation is referred to |
| i ➥ stack frame |
| ii ➥ stack base |
| iii ➥ stack limit |
| iv ➥ stack record |
| Best Explanation: Answer: I Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q15➡ | Theory of Computation Which of the following is TRUE about the Pumping Lemma for regular language? |
| i ➥ It applies to all regular language |
| ii ➥ It applies only to infinite regular languages |
| iii ➥ It applies to all context free languages |
| iv ➥It applies to all recursively enumerable languages |
| Best Explanation: Answer: II Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q16➡ | Algorithm Choose the correct statement(s) A. A problem which is NP-Complete will have the property that it can be solved in polynomial time iff all other NP-complete problems can also be solved in polynomial time. B. All NP-complete problem are NP-hard problems. C. If an NP-hard problem can be solved in polynomial time, then all NP-complete problem can be solved in polynomial time D. All NP-hard-problems are not NP-complete. Choose the correct answer from the options given below: |
| i ➥ A, C only |
| ii ➥ B, D only |
| iii ➥ A, B, C only |
| iv ➥ A, B, C, D |
| Best Explanation: Answer: IV Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q17➡ | Computer Network Which of the following are key features of Mobile Adhoc Networks (MANETS) A. Self – Organizing and decentralized. B. High Mobility of nodes. C. Requires fixed Infrastructure for operation. D. Network Topology is dynamic and constantly changing. E. It requires a central controller to manage network traffic. Choose the correct answer from the options given below: |
| i ➥ A, B & E only |
| ii ➥ B, C, D & E only |
| iii ➥A, B & D only |
| iv ➥ A, B & C only |
| Best Explanation: Answer: III Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q18➡ | Data Structure Which of the following description(s) is/are true: A. Red Black Tree – Guarantees worst case of O(log n) time for search, insert & delete. B. Trie Used for efficient prefix – based searches. C. AVL Tree – self balancing binary search tree with stricker balance criteria. D. B- Tree Allows efficient search, inert, delete operations in disk-based system. Choose the correct answer from the options given below: |
| i ➥ A & B only |
| ii ➥ C & D only |
| iii ➥ B only |
| iv ➥ A, B & D only |
| Best Explanation: Answer: IV Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
Q19➡ | Data Structure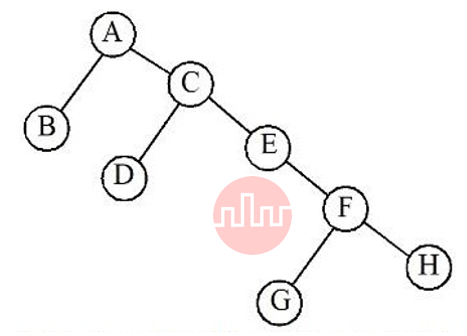 Considering below binary tree, what will be the inorder traversal |
| i ➥ BADCEGFH |
| ii ➥GHFEDCBA |
| iii ➥ BACDEGFH |
| iv ➥GHFDEBCA |
| Best Explanation: Answer: I Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q20➡ | Computer Network The primary function of firewall in network security is |
| i ➥ To monitor network traffic and detect anomalies |
| ii ➥ To create virtual private networks for secure communication |
| iii ➥ To filter incoming and outgoing network traffic based on security rules |
| iv ➥ To encrypt data before Transmission |
| Best Explanation: Answer: III Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q21➡ | Programming The characteristics of modern programming are: A. Each module should do only one thing. B. Communication between modules is allowed only by a calling module. C. Communication can take place directly between modules that do not have calling – called relationship. D. All modules are designed as single-entry, single exit systems using control structure. Choose the correct answer from the options given below: |
| i ➥ A, B & C only |
| ii ➥ A, B & D only |
| iii ➥ A, C & D only |
| iv ➥C & D only |
| Best Explanation: Answer: II Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q22➡ | Computer Architecture Arrange the following in the increasing order with respect to access time. A. Solid State Drive B. Optical Disks C. DRAMS D. SRAMS E. Registers Choose the correct answer from the options given below: |
| i ➥ D, C, A, B, E |
| ii ➥ B, D, C, A, E |
| iii ➥ A, E, B, D, C |
| iv ➥ E, D, C, A, B |
| Best Explanation: Answer: IV Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q23➡ | Computer Architecture Which of the following are not data manipulation instructions? A. Call B. Load C. And D. Increment E. Shift Choose the correct answer from the options given below: |
| i ➥ C & E only |
| ii ➥ A & B only |
| iii ➥ D & E only |
| iv ➥ A & C only |
| Best Explanation: Answer: II Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q24➡ | Discrete Math Arrange the following graph on the basis of number of edges in increasing order [for n > 3] A. Kn (Complete Graph) B. Cn (Cycle graph) C. Wn (Wheel graph) D. Kn,n (Complete Bipartite Graphs) E. Qn (n-cubes graph) Choose the correct answer from the options given below: |
| i ➥ A, B, C, D, E |
| ii ➥B, A, C, D, E |
| iii ➥ A, B, C, E, D |
| iv ➥E, D, C, A, В |
| Best Explanation: Answer: II Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q25➡ | Data Structure Match the LIST-I with LIST-II 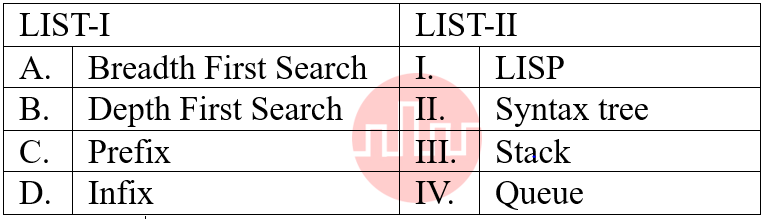 Choose the correct answer from the options given below: |
| i ➥ A-III, B-IV, C-I, D-II |
| ii ➥ A-III, B-IV, C-II, D-I |
| iii ➥ A-IV, B-II, C-III, D-I |
| iv ➥ A-IV, B-III, C-I, D-II |
| Best Explanation: Answer: IV Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q26➡ | DBMS Which of the following command can be used to modify data in an SQL Table? A. INSERT B. DELETE C. UPDATE D. SELECT Choose the correct answer from the options given below: |
| i ➥ A, B, D only |
| ii ➥ A, C, D only |
| iii ➥ B, C, D only |
| iv ➥ A, B, C only |
| Best Explanation: Answer: IV Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q27➡ | Computer Network Sequence the following stages of the sliding window protocol for flow control. A. Sender move the window to the next set of frames. B. Sender sends a window of frames. C. Receiver acknowledge the received frames. D. If acknowledgment is not received, Sender retransmits the frame. Choose the correct answer from the options given below: |
| i ➥ B, A, C, D |
| ii ➥ B, C, D, A |
| iii ➥ B, D, C, A |
| iv ➥B, C, A, D |
| Best Explanation: Answer: II Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q28➡ | DBMS Which of the following table contains the primary information in the data warehouse? |
| i ➥ Dimension table |
| ii ➥ Fact table |
| iii ➥ Lookup table |
| iv ➥ Primary table |
| Best Explanation: Answer: II Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q29➡ | Operating System Consider the following Graph of disk scheduling and identify the disk scheduling algorithm representing by this graph. Queue 84, 125, 11, 36, 170, 20, 172, 45 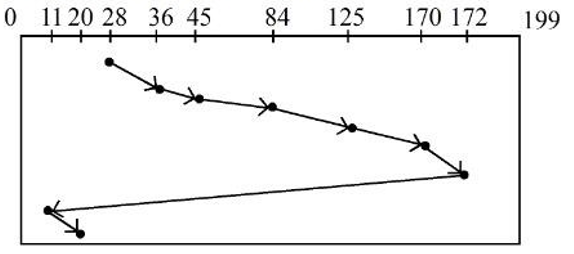 |
| i ➥ SSTF |
| ii ➥ SCAN |
| iii ➥ C-SCAN |
| iv ➥ C-LOOK |
| Best Explanation: Answer: IV Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q30➡ | Computer Network Choose the correct statements from the following A. In connection oriented service, the destination address is to be specified only during the setup. B. Packet sequencing is not guaranteed in connection oriented service C. Flooding is method in which every incoming packet is sent out on every outgoing line except the one by which it arrived. D. Presentation layer performs detection and recovery from errors in the transmitted data. Choose the correct answer from the options given below: |
| i ➥ A, B & C only |
| ii ➥B, C & D only |
| iii ➥ A & C only |
| iv ➥A, C & D only |
| Best Explanation: Answer: III Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q31➡ | Computer Graphics The major adverse side effects of scan conversion are: – A. Staircase appearance B. Unequal brightness of slanted lines C. Picket fence problem D. Rasterization E. Pre-filtering and post-filtering Choose the correct answer from the options given below: |
| i ➥ A & B only |
| ii ➥ A, B & C only |
| iii ➥ B, C & D only |
| iv ➥ C, D & E only |
| Best Explanation: Answer: II Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q32➡ | Discrete Math The kind of symbols for basic syntactic elements of first-order logic are A. Constant B. Domain C. Predicate D. Temporal E. Function Choose the correct answer from the options given below: |
| i ➥ B, D only |
| ii ➥ A, B, C only |
| iii ➥ A, C, E only |
| iv ➥C, D only |
| Best Explanation: Answer: III Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q33➡ | DBMS The degree of a relation in database is |
| i ➥ the number of tuples in the relation |
| ii ➥ the number of attributes in the relation |
| iii ➥ the number of values in domain |
| iv ➥ the number of keys in a relation |
| Best Explanation: Answer: II Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q34➡ | Computer Architecture Consider a pipeline unit for fixed point multiplication of 8-bit integers. Arrange the following stages in a correct sequence. Stage A: Consists of two CSAs and it merges four numbers from previous stage. Stage B: is a CPA, which adds up the two numbers Stage C: is made upto two level of four CSAs. Stage D: Generates eight partial products. Choose the correct answer from the options given below: |
| i ➥ C, A, B, D |
| ii ➥ D, C, A, B |
| iii ➥ B, D, C, A |
| iv ➥ A, C, D, B |
| Best Explanation: Answer: II Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q35➡ | Computer Architecture Which of the following is the correct sequence with regard to service routine? A. Save contents of processor registers B. Turn the interrupt facility on C. Service the device whose flag is set D. Check which flag is set E. Restore contents of processor registers Choose the correct answer from the options given below: |
| i ➥ A, B, C, D, E |
| ii ➥ D, B, C, A, E |
| iii ➥ D, C, B, E, A |
| iv ➥A, D, C, E, B |
| Best Explanation: Answer: IV Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q36➡ | Software Engineering Find the correct sequence of prototype software development model. A. Start B. Develop Prototype C. Deliver to customer D. Quick Design E. Quick Play Choose the correct answer from the options given below: |
| i ➥ A, B, C, D, E |
| ii ➥ A, E, D, B, C |
| iii ➥ A, B, D, E, C |
| iv ➥ A, B, E D, C |
| Best Explanation: Answer: II Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q37➡ | Programming Which of the following statement is not True? |
| i ➥ A data member of a class can be declared as static and is normally used to maintain values common to the entire class. |
| ii ➥ A friend function can be invoked like a normal function without the help of any object. |
| iii ➥ The scope resolution operator (::) can be overloaded like normal operators. |
| iv ➥ Multiple inheritance may lead to duplication of inherited members from a “Grandparent” base class. This may be avoided by making the common base class a virtual base class. |
| Best Explanation: Answer: III Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q38➡ | Computer Graphics Arrange the 2-D viewing transformation pipeline. A. Convert world-coordinates to viewing coordinates B. Map viewing coordinates to normalized viewing coordinates using window – viewpoint specifications C. Construct world – coordinates scene using modeling coordinates transformations D. Map normalized viewpoint to device coordinates Choose the correct answer from the options given below: |
| i ➥ D, C, B, A |
| ii ➥ D, C, A, B |
| iii ➥ D. A, B, D |
| iv ➥B, C, A, D |
| Best Explanation: Answer: III Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q39➡ | Artificial Intelligence Definition’s of _____organized into following four categories namely, Thinking Humanly, Thinking Rationally, Acting Humanly, Acting Rationally |
| i ➥ Machine Learning |
| ii ➥ Deep Learning |
| iii ➥ Artificial Intelligence |
| iv ➥ Neural Network |
| Best Explanation: Answer: III Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q40➡ | Digital Logic Design Which of the following is the complement of the boolean function. A’B+CD’+A’B+CD’ |
| i ➥ A’B+CD’ |
| ii ➥ (A’+B)(C+D’) |
| iii ➥ (A+B’)(C’+D) |
| iv ➥ AB’+CD’ |
| Best Explanation: Answer: III Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q41➡ | Software Engineering Software Testability is simply how easily a software program can be tested. Which one characteristics does not lead to testable software? |
| i ➥ Observability |
| ii ➥ Controllability |
| iii ➥ Repairability |
| iv ➥ Understandability |
| Best Explanation: Answer: III Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q42➡ | Discrete Math If x and y are elements in a group G and if x = y³ = e, where e is the identity of G, then the inverse of x²yx⁴y² must be |
| i ➥ y2xy2x4 |
| ii ➥ уху2х3 |
| iii ➥ yx6y6x3 |
| iv ➥xy2x2y4 |
| Best Explanation: Answer: II Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q43➡ | Programming Which of the following is not true about Global Variables: |
| i ➥ The values of the Global variables which are sent to the called function may be changed inadvertently by the called function. |
| ii ➥ Functions are supposed to be independent and isolated modules. This character is lost, if they use global variables. |
| iii ➥ It is not immediately apparent to the reader which values are being sent to the called function |
| iv ➥ A function that uses global variables does not suffer from reusability. |
| Best Explanation: Answer: IV Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q44➡ | Computer Architecture Which table for a dynamic pipeline become more interesting when a nonlinear pattern is follows? |
| i ➥ Reservation Table |
| ii ➥ Confusion Table |
| iii ➥ Inverted Table |
| iv ➥ Greedy Table |
| Best Explanation: Answer: I Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q45➡ | DBMS Which of the following is the simplified form of the given function. f(A,B,C)=∑m(0,1,3,7) |
| i ➥ A’B’C’+A’B’C+A’BC+ABC |
| ii ➥ A’B’+A’BC+ABC |
| iii ➥ A’B’+BC |
| iv ➥A’B’+BC’ |
| Best Explanation: Answer: III Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q46➡ | LPP A linear programming problem (LPP) is as follows: Min z=30x-18y, subject to the constraints; 3x+4y ≤ 60, 5x-3y ≥ 20 and x,y ≥ 0. In this feasible region, the solution of LPP is/are A. (4, 0) Β. (2, 0) C. (7,5) D. (0, 15) Ε. (8,5) Choose the correct answer from the options given below: |
| i ➥ A and C only |
| ii ➥ B only |
| iii ➥ E only |
| iv ➥ D only |
| Best Explanation: Answer: I Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q47➡ | Operating System If the virtual memory size is 32 MB and a physical memory size is 4MB with a page size of 2KB, Calculate the number of frames available in physical memory |
| i ➥ 1024 |
| ii ➥ 2048 |
| iii ➥ 3072 |
| iv ➥ 4096 |
| Best Explanation: Answer: II Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q48➡ | Software Engineering Which of the following algorithms are based on the Breadth First Search (BFS)? A. Prim’s algorithms B. Kruskal algorithms C. Dijkstra algorithms D. Greedy algorithms E. Dynamic Programming Choose the correct answer from the options given below: |
| i ➥ A & B only |
| ii ➥ A, C & D only |
| iii ➥ D & E only |
| iv ➥ A & C only |
| Best Explanation: Answer: IV Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q49➡ | Theory of Computation Match the LIST-I with LIST-II 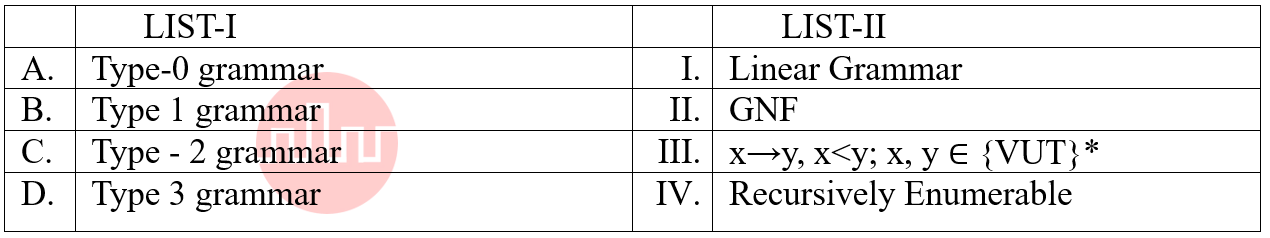 Choose the correct answer from the options given below: |
| i ➥ A-I, B-II, C-III, D-IV |
| ii ➥ A-II, B-I, C-III, D-IV |
| iii ➥ A-III, B-II, C-IV, D-I |
| iv ➥A-IV, B-III, C-I, D-II |
| Best Explanation: Answer: IV Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q50➡ | LPP Which one of the following is not a basic solution of system of linear equation |
| i ➥ |
| ii ➥ |
| iii ➥ |
| iv ➥ |
| Best Explanation: Answer: I Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q51➡ | Software Engineering Match the LIST-I with LIST-II 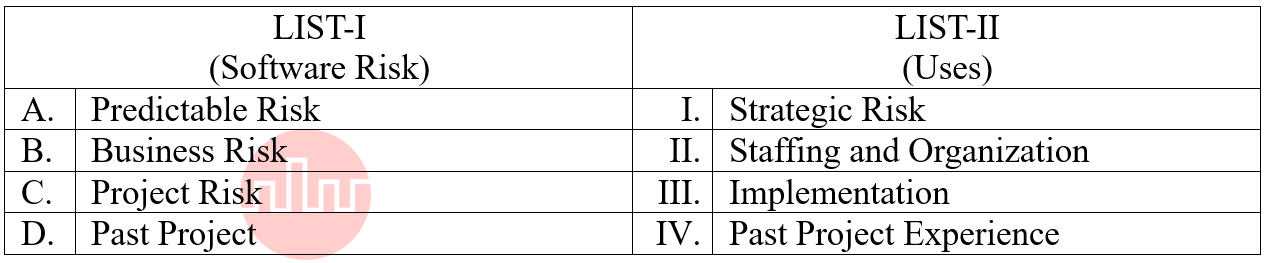 Choose the correct answer from the options given below: |
| i ➥ A-IV, B-III, C-I, D-II |
| ii ➥ A-III, B-II, C-I, D-IV |
| iii ➥ A-I, B-IV, C-III, D-II |
| iv ➥ A-IV, B-I, CII-, D-III |
| Best Explanation: Answer: IV Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q52➡ | Artificial Intelligence Which of the following are correct for the neural network? A. The training time depends upon the size of network. B. Neural network can be simulated on the conventional computer. C. Neural network mimic the same way as that of the humans brain. D. A neural network include feedback. Choose the correct answer from the options given below: |
| i ➥ A and B only |
| ii ➥ A, C and D only |
| iii ➥ A, B and C only |
| iv ➥A and C only |
| Best Explanation: Answer: II Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q53➡ | Computer Graphics The light given off by the phosphor during exposure to the electron beam is known as |
| i ➥ Fluorescence |
| ii ➥ Phosphorescence |
| iii ➥ Persistence |
| iv ➥ Retracing |
| Best Explanation: Answer: I Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q54➡ | Algorithm Which of the following is not a divide and conquer method |
| i ➥ Binary Search |
| ii ➥ Merge Sort |
| iii ➥ Quick Sort |
| iv ➥Heap Sort |
| Best Explanation: Answer: IV Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q55➡ | Compiler Design Yacc is which of the following parsers? |
| i ➥ Predictive Parser |
| ii ➥ SLR Parser |
| iii ➥ CLR Parser |
| iv ➥ LALR Parser |
| Best Explanation: Answer: IV Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q56➡ | Software Engineering Which one of the following is the correct estimation model based on software equation? |
| i ➥ E = [LOCxB0.222/P]2 x (1/t4) |
| ii ➥ E = [LOCxB0.333/P]3 x (1/t4) |
| iii ➥ E = [LOCxB0.444/P]4 x (1/t3) |
| iv ➥ E = [LOC×B0.111/p]6 x (1/t3) |
| Best Explanation: Answer: II Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q57➡ | Computer Network Arrange the following steps of the DHCP (Dynamic Host Control Protocol) process in the correct sequence. A. DHC PACK B. DHCP DISCOVER C. DHCP OFFER D. DHCP REQUEST E. Client receives IP configuration Choose the correct answer from the options given below: |
| i ➥ A, B, C, D, E |
| ii ➥ B, C, D, A, E |
| iii ➥ C, B, A, E, D |
| iv ➥ D, A, E, C, В |
| Best Explanation: Answer: II Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q58➡ | Emerging Technologies Match the LIST-I with LIST-II 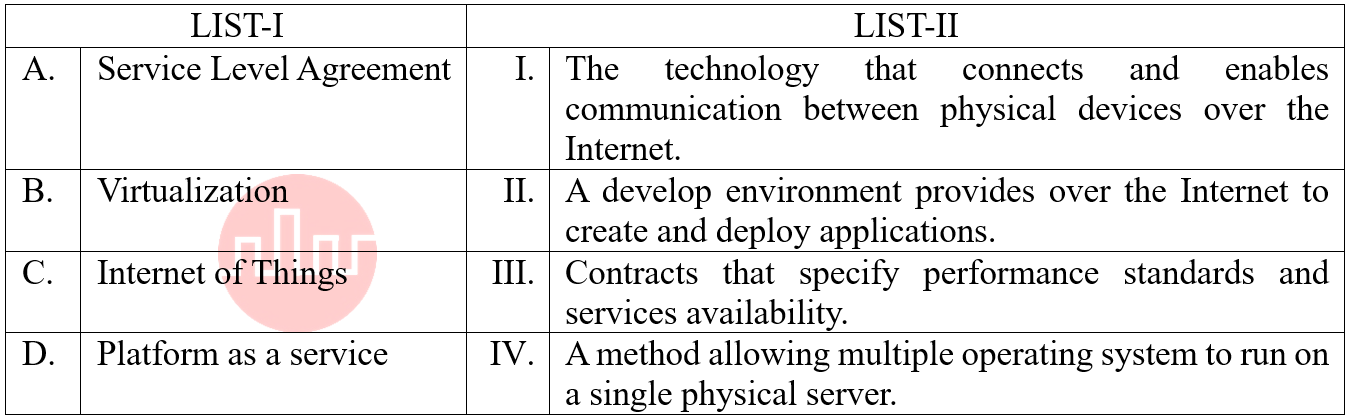 Choose the correct answer from the options given below: |
| i ➥ A-III, В-II, C-I, D-IV |
| ii ➥ A-III, B-IV, C-I, D-II |
| iii ➥ A-III. B-I. C-IV, D-I |
| iv ➥A-I, B-IV, C-III, D-II |
| Best Explanation: Answer: II Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q59➡ | Operating System Given the following processes with their times and priority (lower number indicates higher priority) 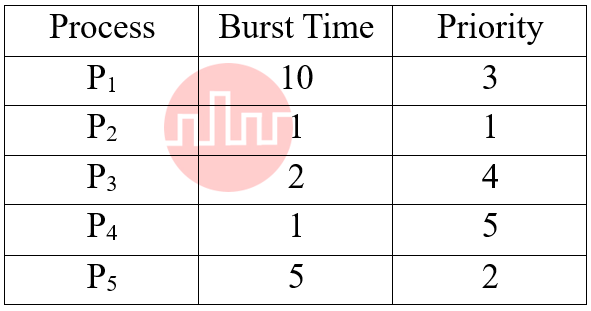 Which of the following is a value of average waiting time using priority scheduling algorithm? |
| i ➥ 9.2 |
| ii ➥ 6.8 |
| iii ➥ 7.6 |
| iv ➥ 8.2 |
| Best Explanation: Answer: IV Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q60➡ | Computer Network Match the LIST-I with LIST-II 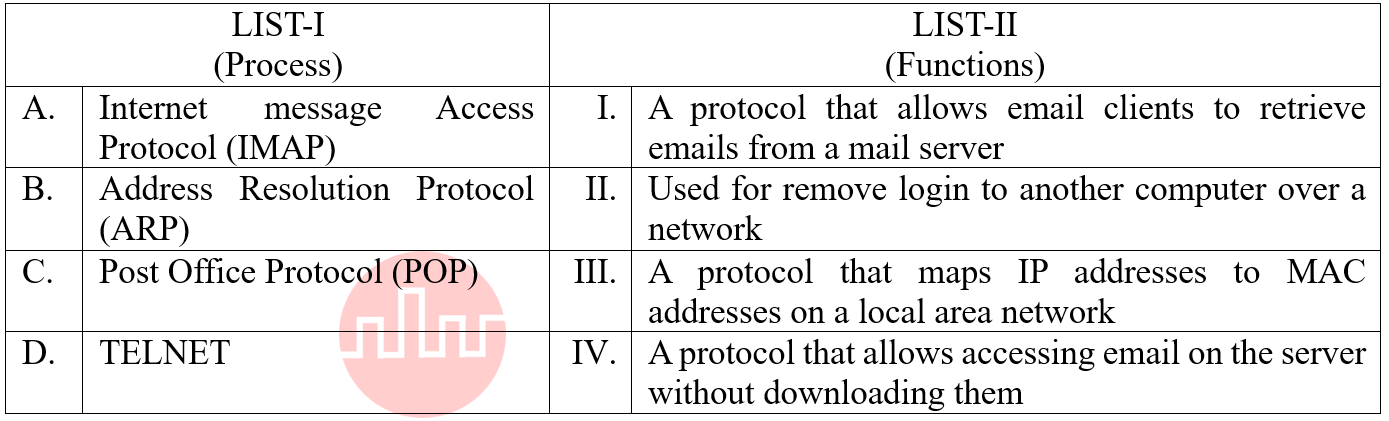 Choose the correct answer from the options given below: |
| i ➥ A-II. В-I, C-III, D-IV |
| ii ➥ A-III, B-IV, C-I, D-II |
| iii ➥ A-IV, B-III, C-I, D-II |
| iv ➥A-IV, B-III, C-II, D-I |
| Best Explanation: Answer: III Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q61➡ | Digital Logic Design Match the LIST-I with LIST-II 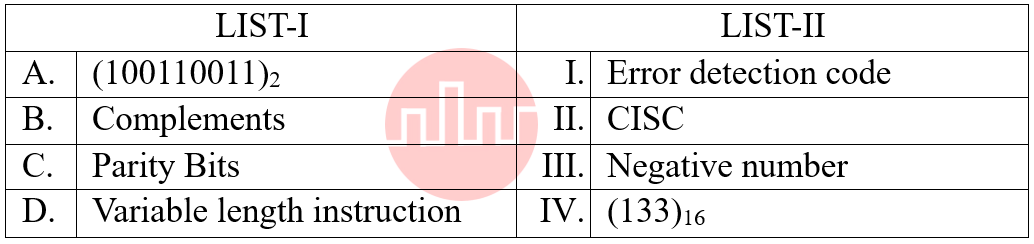 Choose the correct answer from the options given below: |
| i ➥ A-IV, B-I, C-III, D-II |
| ii ➥ A-IV, B-III, C-I, D-II |
| iii ➥ A-IV, B-II, C-III, D-I |
| iv ➥A-I, B-IV, C-II, D-III |
| Best Explanation: Answer: II Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q62➡ | Operating System Which of the following does not interrupt a running process? |
| i ➥ Device |
| ii ➥ Timer |
| iii ➥ Scheduler |
| iv ➥ Power Failure |
| Best Explanation: Answer: III Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q63➡ | Discrete math The mathematical notation to describe logical entailment of a sentence ” α entails another sentence β” is |
| i ➥ α ⊨ β |
| ii ➥ α ⊆ β |
| iii ➥ β ⊨ α |
| iv ➥β ⊆ α |
| Best Explanation: Answer: I Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q64➡ | Algorithm Which of the following is the solution of the following recurrence relation T(n) = T(2n/3) + 1? |
| i ➥ θ (n²) |
| ii ➥ θ (log n) |
| iii ➥ θ (n log n) |
| iv ➥θ (n3/2) |
| Best Explanation: Answer: II Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q65➡ | Programming Consider following conditional statements if (m=20-10 || n > 10). The order of execution of the following operations is A. == B. – C. || D. > Choose the correct answer from the options given below: |
| i ➥ D, B, A, C |
| ii ➥ B, D, C, A |
| iii ➥ B, D, A, C |
| iv ➥ A, B, D, C |
| Best Explanation: Answer: III Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q66➡ | Software Engineering Collaborative document inspection technique used for? |
| i ➥ Requirement Validation Process |
| ii ➥ Requirement Verification Process |
| iii ➥ Integration Testing |
| iv ➥Blackbox Testing |
| Best Explanation: Answer: I Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q67➡ | Data Structure Arrange the following steps of the Inorder Traversal of Binary Tree in the correct order. A. Visit the Left subtree B. Visit the Root node C. Visit the Right subtree D. Start traversing by visiting the nodes in rooted tree E. Repeat the above three steps. Choose the correct answer from the options given below: |
| i ➥ A, B, C, D, E |
| ii ➥ E, A, B, C, D |
| iii ➥ D, A, B, C, E |
| iv ➥D, A, E, B, C |
| Best Explanation: Answer: III Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q68➡ | DBMS INSERT command is used to A. add a single tuple to a relation B. add multiple tuples to a relation C. add values to specific attributes D. insert new table Choose the correct answer from the options given below: |
| i ➥ A only |
| ii ➥ A, B only |
| iii ➥ A, B, C only |
| iv ➥ B, C, D only |
| Best Explanation: Answer: III Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q69➡ | Discrete math Which of the following Graph is/are planer? 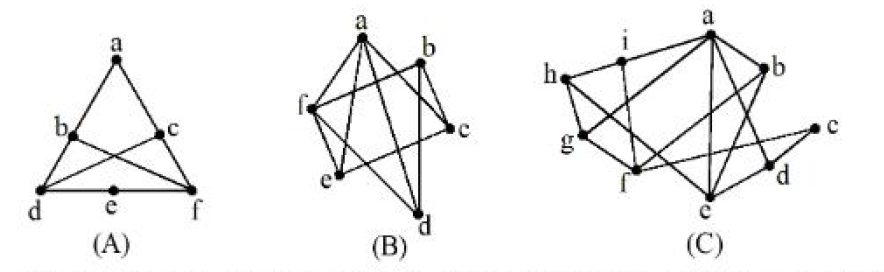 Choose the most appropriate answer from the options given below: |
| i ➥ A and C only |
| ii ➥ B only |
| iii ➥ A only |
| iv ➥A and B only |
| Best Explanation: Answer: III Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q70➡ | Computer Network Consider a noiseless channel with a bandwidth of 5000Hz transmitting a signal with two signal levels. The maximum bit rate is |
| i ➥ 2500 bps |
| ii ➥ 10000 bps |
| iii ➥ 5000 bps |
| iv ➥ 20000 bps |
| Best Explanation: Answer: II Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q71➡ | Digital Logic Design The hamming distance between 10101 and 11110 is |
| i ➥ 2 |
| ii ➥ 3 |
| iii ➥ 4 |
| iv ➥5 |
| Best Explanation: Answer: I Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q72➡ | Discrete Math Match the LIST-I with LIST-II: Match the logical equivalence propositions 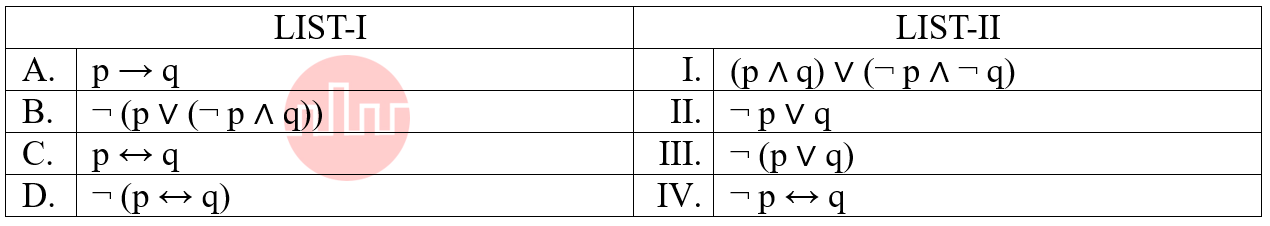 Choose the correct answer from the options given below: |
| i ➥ A-I, B-III, C-II, D-IV |
| ii ➥ A-I, B-II, C-III, D-IV |
| iii ➥ A-II, B-III, C-I, D-IV |
| iv ➥A-II, B-III, C-IV, D-I |
| Best Explanation: Answer: III Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q73➡ | Algorithm Match the LIST-I with LIST-II 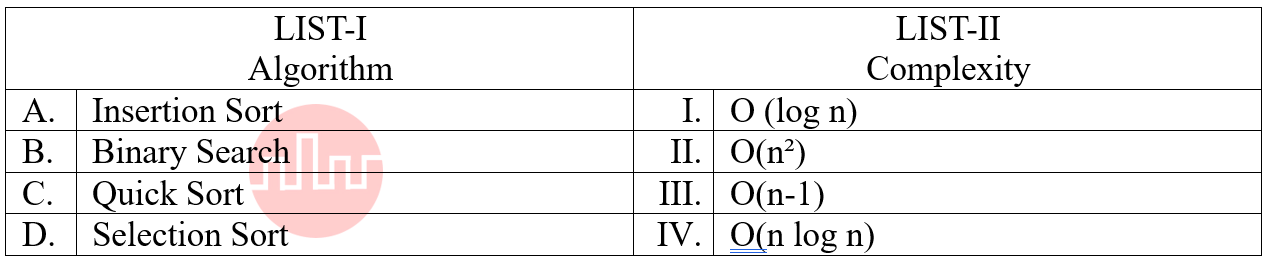 Choose the correct answer from the options given below: |
| i ➥ A-III, B-I, C-IV, D-II |
| ii ➥ A-II, B-III, C-I, D-IV |
| iii ➥ A-I, B-II, C-IV, D-III |
| iv ➥ A-II, B-III, C-IV, D-I |
| Best Explanation: Answer: I Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q74➡ | Programming Consider the following statements int x = 10, y = 15; x = ((x = y)? (y + x): (y – x)); What will be the value of x after executing these statements? |
| i ➥ 5 |
| ii ➥ 25 |
| iii ➥ 15 |
| iv ➥30 |
| Best Explanation: Answer: IV Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q75➡ | DBMS Match the LIST-I with LIST-II 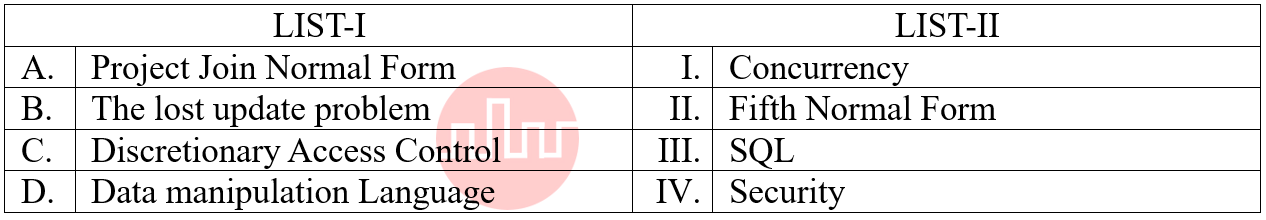 Choose the correct answer from the options given below: |
| i ➥ A-II, B-I, C-IV, D-III |
| ii ➥ A-I, B-II, C-IV, D-III |
| iii ➥ A-I, B-II, C-III, D-IV |
| iv ➥ A-IV, B-II, C-III, D-I |
| Best Explanation: Answer: I Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q76➡ | Computer Architecture Which of the following do not represent memory reference instruction. 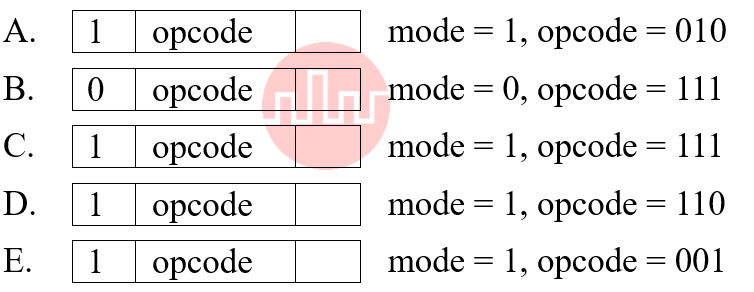 Choose the correct answer from the options given below: |
| i ➥ B & C only |
| ii ➥ B & D only |
| iii ➥ A & D only |
| iv ➥A & E only |
| Best Explanation: Answer: II Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q77➡ | Software Engineering In Software Engineering Jackson’s Principle based on A. Designation B. Definitions C. Refutable Assertions D. Formal Review E. Requirement Elicitation Choose the correct answer from the options given below: |
| i ➥ A, B & C Only |
| ii ➥ B, C & D Only |
| iii ➥ C, D & E Only |
| iv ➥ B, D & C Only |
| Best Explanation: Answer: I Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q78➡ | Theory of Computation Which of the following represents the output of the transition function(δ) δ (q0, a) = (q1, x, R) δ (q1, a) = (q1, a, R) δ (q1, y1) = (q1, y, R) δ (q1, b) = (q2, y, L) δ (q2, y) = (q2, y, L) δ (q2, a) = (q2, a, L) δ (q2, x) = (q0, x, R) δ (q0, y) = (q3, y, R) δ (q3, y) = (q3, y, R) δ (q3, □)=( qf, □, R) |
| i ➥ L={ an bn |n≥0} |
| ii ➥ L={ an bn |n≥1} |
| iii ➥ L={ an bn |n>0} |
| iv ➥L={ an bn |n>1} |
| Best Explanation: Answer: II Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q79➡ | Compiler Design Match the LIST-I with LIST-II 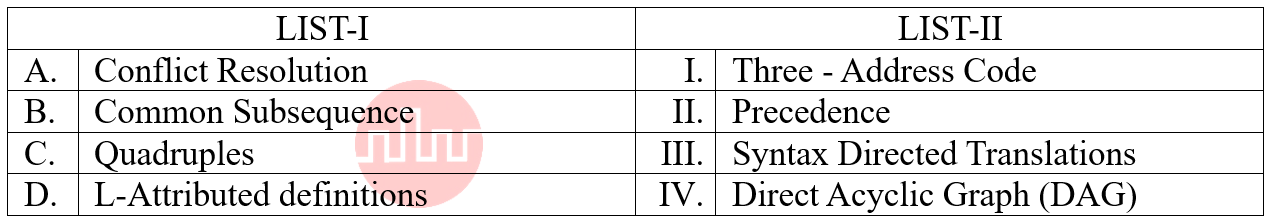 Choose the correct answer from the options given below: |
| i ➥ A-III, B-II, C-IV, D-I |
| ii ➥ A-II, B-IV, C-I, D-III |
| iii ➥ A-II, B-III, C-I, D-IV |
| iv ➥A-IV, B-I, C-II, D-III |
| Best Explanation: Answer: II Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q80➡ | Computer Network Consider the following statements regarding multiple access techniques & identify the CORRECT ones. A. ALOHA is used for multiple access on a shared medium B. TDMA uses WALSH TABLES for time slot allocation C. CSMA/CD was invented for wireless networks D. CDMA codes are sequence of number generated by orthogonal codes Choose the correct answer from the options given below: |
| i ➥ A & B only |
| ii ➥ B & C only |
| iii ➥ C & D only |
| iv ➥ A & D only |
| Best Explanation: Answer: IV Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q81➡ | Discrete Math The probability that A hits a target is 1/4, and the probability that B hits the target is 2/5. Both shoot at the target, what is the probability that at least one of them hits the target, i.e., that A or B (or both) hit the target? |
| i ➥ 3/5 |
| ii ➥ 11/9 |
| iii ➥ 2/20 |
| iv ➥11/20 |
| Best Explanation: Answer: IV Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q82➡ | Compiler Design Regarding the code optimization, choose the correct sequence A. Algebraic Simplification B. Use of machine idioms C. Redundant – instruction elimination D. Flow of control optimization E. Improved target code Choose the correct answer from the options given below: |
| i ➥ A, C, B, D, E |
| ii ➥ B, C, D, A, E |
| iii ➥ C, D, A, B, E |
| iv ➥ D, B, A, C, E |
| Best Explanation: Answer: III Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q83➡ | Software Engineering As per the Software Engineering Institute (SEI), the correct sequence is A. Initial B. Repeatable C. Managed D. Optimizing E. Defined Choose the correct answer from the options given below: |
| i ➥ A, B, C, D, E |
| ii ➥ A, B, E, C, D |
| iii ➥ A, E, C, D, B |
| iv ➥A, E, B, C, D |
| Best Explanation: Answer: II Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q84➡ | Digital Logic Design Match the LIST-I with LIST-II 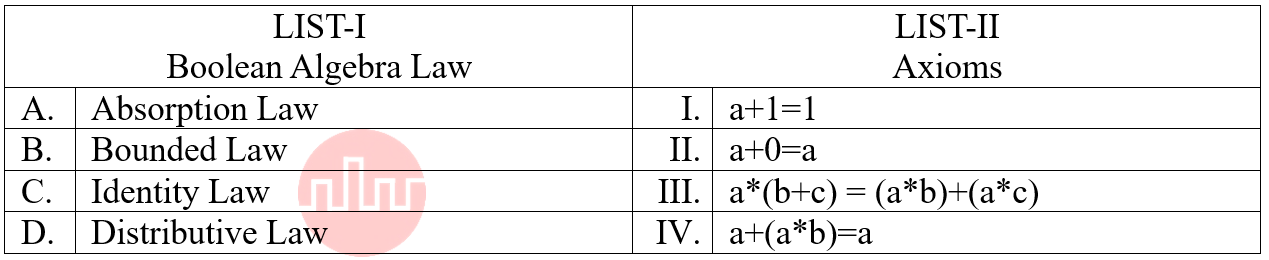 Choose the correct answer from the options given below: |
| i ➥ A-IV, B-I, C-II, D-III |
| ii ➥ A-IV, B-III, C-I, D-II |
| iii ➥ A-III, B-IV, C-II, D-I |
| iv ➥ A-II, B-III, C-IV, D-I |
| Best Explanation: Answer: I Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q85➡ | Data Structure Which of the following uses only increment operations for adding and removing element at either end? |
| i ➥ Queues |
| ii ➥ Stacks |
| iii ➥ Priority Queues |
| iv ➥Deques |
| Best Explanation: Answer: II Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q86➡ | Artificial Intellegence Which one of the following is not related to the feed forward networks on the Backpropagation Algorithm? |
| i ➥ Boolean function |
| ii ➥ Continuous function |
| iii ➥ Arbitrary function |
| iv ➥Greedy function |
| Best Explanation: Answer: IV Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q87➡ | Computer Architecture Which are often needed to evaluate the cache performance? |
| i ➥ Hit Ratio |
| ii ➥ Latency |
| iii ➥ Cache Traces |
| iv ➥Transfer Rate |
| Best Explanation: Answer: III Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q88➡ | Artificial Intelligence Match the LIST-I with LIST-II 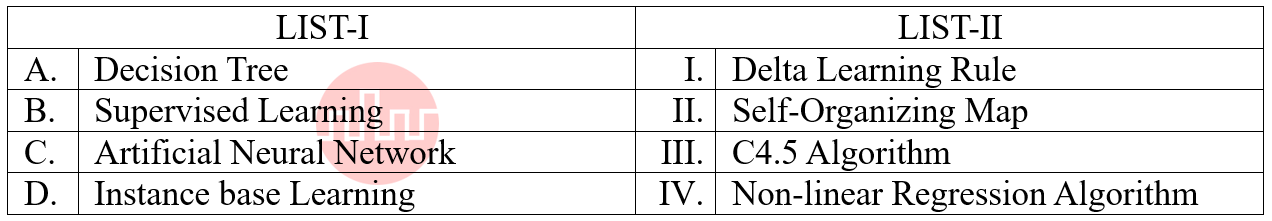 Choose the correct answer from the options given below: |
| i ➥ A-I, B-II, C-III, D-IV |
| ii ➥ A-II, B-III, C-IV, D-I |
| iii ➥ A-III, B-IV, C-I, D-II |
| iv ➥ A-IV, B-I, C-II, D-III |
| Best Explanation: Answer: III Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q89➡ | Data Structure Identify the correct statements from the following regarding spiral model. A. Spiral model is an incremental process model. B. Spiral model is a risk – driven process mode. C. Spiral model is an acyclic balancing approach. D. Spiral model involves a set of anchor point milestone. Choose the correct answer from the options given below: |
| i ➥ A & B Only |
| ii ➥ B & C Only |
| iii ➥ A & D Only |
| iv ➥B & D Only |
| Best Explanation: Answer: IV Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q90➡ | DBMS An alternate key in database table is also called |
| i ➥ Primary key |
| ii ➥ Candidate key |
| iii ➥ Super key |
| iv ➥ Foreign key |
| Best Explanation: Answer: II Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q91➡ | Theory of Computation Comprehension: A machine is represented by states Q, input alphabet ∑, transition function δ. Initial state q and final state F. The machine accepts all the strings over ∑ = {a, b}, which start and ended with any combination of all alphabet and abb works /lies as substring in all the strings to be accepted. 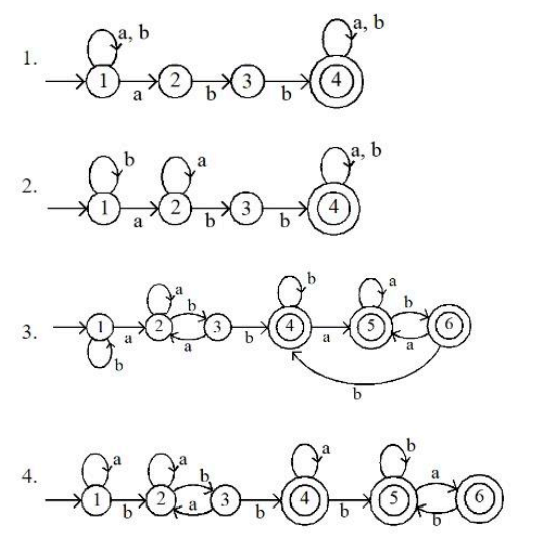 For the above specified passage, which of the following is DFA for the language represented/accepeted by machine? |
| i ➥ 1 |
| ii ➥ 2 |
| iii ➥ 3 |
| iv ➥4 |
| Best Explanation: Answer: III Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q92➡ | Theory of Computation Comprehension: A machine is represented by states Q, input alphabet ∑, transition function δ. Initial state q and final state F. The machine accepts all the strings over ∑ = {a, b}, which start and ended with any combination of all alphabet and abb works /lies as substring in all the strings to be accepted. For the above specified passage, which of the following represents the regular expression? |
| i ➥ (a+b)*aab |
| ii ➥ aba(a+b)* |
| iii ➥ b(a+b)*b(a+b)*a(a+b)* |
| iv ➥(a+b)*abb(a+b)* |
| Best Explanation: Answer: IV Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q93➡ | Theory of Computation Comprehension: A machine is represented by states Q, input alphabet ∑, transition function δ. Initial state q and final state F. The machine accepts all the strings over ∑ = {a, b}, which start and ended with any combination of all alphabet and abb works /lies as substring in all the strings to be accepted. For the above mentioned passage which of the following is correct? 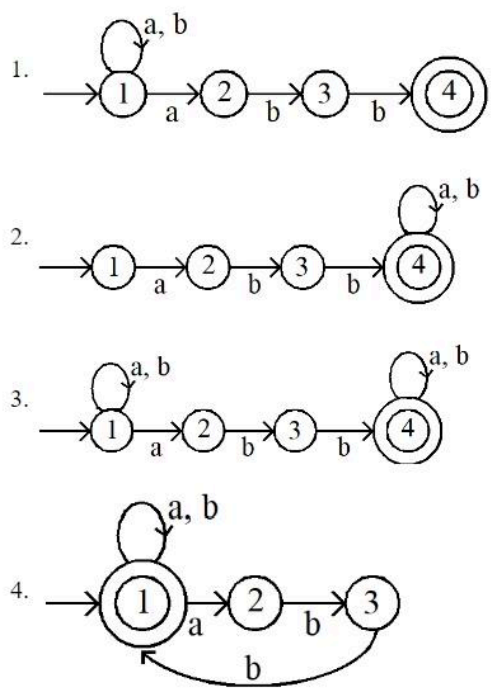 |
| i ➥ 1 |
| ii ➥ 2 |
| iii ➥ 3 |
| iv ➥4 |
| Best Explanation: Answer: III Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q94➡ | Theory of Computation Comprehension: A machine is represented by states Q, input alphabet ∑, transition function δ. Initial state q and final state F. The machine accepts all the strings over ∑ = {a, b}, which start and ended with any combination of all alphabet and abb works /lies as substring in all the strings to be accepted. Which of the following represented the minimum state DFA for the above specified passage? 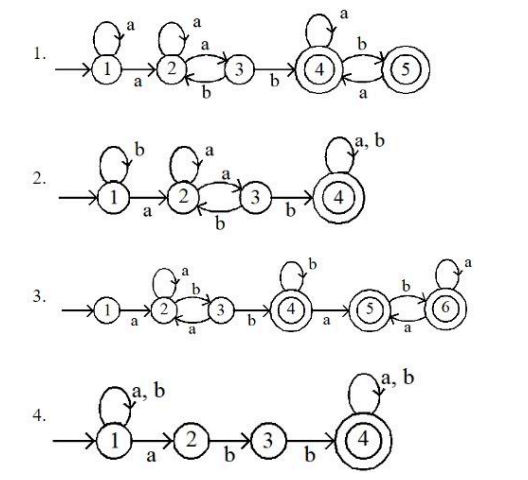 |
| i ➥ 1 |
| ii ➥ 2 |
| iii ➥ 3 |
| iv ➥4 |
| Best Explanation: Answer: IV Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q95➡ | Theory of Computation Comprehension: A machine is represented by states Q, input alphabet ∑, transition function δ. Initial state q and final state F. The machine accepts all the strings over ∑ = {a, b}, which start and ended with any combination of all alphabet and abb works /lies as substring in all the strings to be accepted. For the above specified passage, which of the following represent the grammar for the language accepted the machine? |
| i ➥ S→AabbB, A→aA|∈, B→bB|∈ |
| ii ➥ S→abbA, A→aA|∈|bA |
| iii ➥ S→AabbA, A→aA|bA|∈ |
| iv ➥S→Aabb, A→aA|bA|∈ |
| Best Explanation: Answer: III Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q96➡ | Operating System Comprehension: Consider the following set of processes with the arrival time and length of CPU Burst time given in milli-seconds (ms): 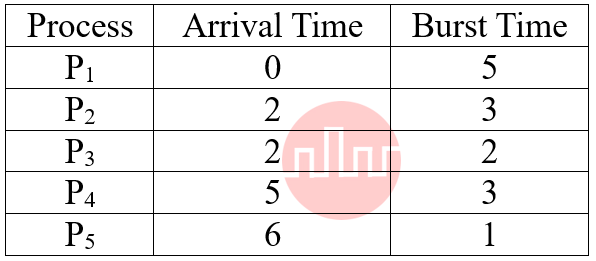 What is the average turnaround time for these Processes with First Come First Serve (FCFS) scheduling Algorithm? |
| i ➥ 5.3 ms |
| ii ➥ 6.4 ms |
| iii ➥ 7.0 ms |
| iv ➥ 8.2 ms |
| Best Explanation: Answer: III Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q97➡ | Operating System Comprehension: Consider the following set of processes with the arrival time and length of CPU Burst time given in milli-seconds (ms):  Find the average weighted turnaround time for these process using Highest Response Ratio Next (HRN) Algorithm? |
| i ➥ 3.2 ms |
| ii ➥ 2.834 ms |
| iii ➥ 1.632 ms |
| iv ➥ 6.721 ms |
| Best Explanation: Answer: II Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q98➡ | Operating System Comprehension: Consider the following set of processes with the arrival time and length of CPU Burst time given in milli-seconds (ms):  Calculate the average response time for these processes with non-preemptive priority Scheduling algorithm? Priority of the process are as follows and consider that all the processes came at zero (0) time. (Note low numbers represent high priority). 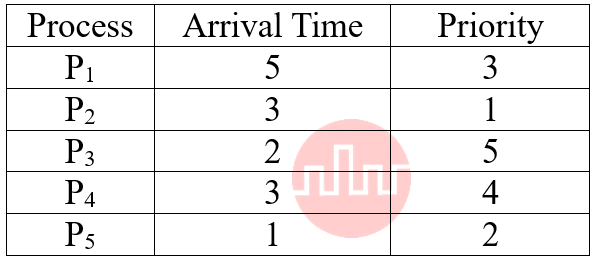 |
| i ➥ 5.6 ms |
| ii ➥ 5.2 ms |
| iii ➥ 4.7 ms |
| iv ➥ 3.8 ms |
| Best Explanation: Answer: I Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q99➡ | Operating System Comprehension: Consider the following set of processes with the arrival time and length of CPU Burst time given in milli-seconds (ms):  What is the average waiting time for these processes with non-preemptive Shortest Job First (SJF) scheduling Algorithm? |
| i ➥ 3.0 ms |
| ii ➥ 2.1 ms |
| iii ➥ 4.6 ms |
| iv ➥ 3.2 ms |
| Best Explanation: Answer: IV Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q100➡ | Operating System Comprehension: Consider the following set of processes with the arrival time and length of CPU Burst time given in milli-seconds (ms):  When we apply Shortest Job First (SJF) scheduling Policy/algorithm, Process (P2) faces partial starvation and waits for the longer time to execute. Which one of the following algorithms addresses this problem? |
| i ➥ Round Robin |
| ii ➥ Priority |
| iii ➥ Highest Response ratio Next |
| iv ➥ Least Completed next |
| Best Explanation: Answer: III Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
