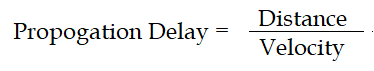UGC NET Computer Science Question Solution June- 2019 -Paper -II
UGC NET Computer Science Question Solution June- 2019 -Paper -II
| Q1 ➥ Which data structure is used by the compiler for managing variables and their attributes? |
| A ➥ Binary tree |
| B ➥ Link list |
| C ➥ Symbol table |
| D ➥ Parse table |
Show Answer With Best Explanation
| Q2 ➥ In relational database, if a relation R is in BCNF, then which of the following is true about relation R? |
| A ➥ R is in 4NF |
| B ➥ R is not in 1NF |
| C ➥ R is in 2Nf and not in 3NF |
| D ➥ R is in 2NF and 3NF |
Show Answer With Best Explanation
| Q3 ➥ Consider that a process has been allocated 3 frames and has a sequence of page referencing 1,2,1,3,7,4,5,6,3,1 What shall be the difference i page faults for the above string using the algorithm of LRU and Optimal page replacement for referencing the string? |
| A ➥ 2 |
| B ➥ 0 |
| C ➥ 1 |
| D ➥ 3 |
Show Answer With Best Explanation
| Q4 ➥ Which of the following are not shared by the threads of the same process? (a) Stack (b) Registers (c) Address Space (d) Message Queue |
| A ➥ (a) and (d) |
| B ➥ (b) and (c) |
| C ➥ (a) and (b) |
| D ➥ (a), (b) and (c) |
Show Answer With Best Explanation
Q5 ➥  |
| 1 ➥ x1=5/2, x2=0, x3=0, Z=5 |
| 2 ➥ x1=0, x2=0, x3=5/2, Z=5 |
| 3➥ x1=0, x2=5/2, x3=0, Z= -5/2 |
| 4 ➥ x1=0, x2=0, x3=10, Z=20 |
Show Answer With Best Explanation
| Q6➡ | Computer Network In the TCP/IP model, encryption and decryption are functions of _________ layer |
| i ➥ Data link |
| ii ➥ Network |
| iii ➥ Transport |
| iv ➥ Application |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | TCP/IP Model | Help-Line |
Q7 ➥  |
| A ➥ 255 |
| B ➥ 256 |
| C ➥ 257 |
| D ➥ 258 |
Show Answer With Best Explanation
| Q8 ➡ Consider three intensive processes, which requires 10,20 and 30 units of time and arrive at times 0,2 and 6 respectively. how many context switches are needed if the operating system implements a shortest remaining time first scheduling algorithm? Do not count the context switches at time zero ad at the end |
| A ➥ 4 |
| B ➥ 2 |
| C ➥ 3 |
| D ➥ 1 |
Show Answer With Best Explanation
| Q9➡ Software Reuse is |
| A ➥ The process of analysing software with the objective of recovering its design and specification |
| B ➥ The process of existing software artifacts and knowledge to build new software |
| C ➥ Concerned with re implementing legacy system to make them more maintainable |
| D ➥ The process of analysing software to create a representation of a higher level of abstraction and breaking software down into its parts to see how it works |
Show Answer With Best Explanation
| Q10➡ Shift-reduce parser consists of (a) input buffer (b) stack (c) parse table choose the correct option from those given below: |
| A ➥ (a) and (b) only |
| B ➥ (a) and (c) only |
| C ➥ (c) only |
| D ➥ (a), (b) and (c) |
Show Answer With Best Explanation
Question 11➡ | Computer Network 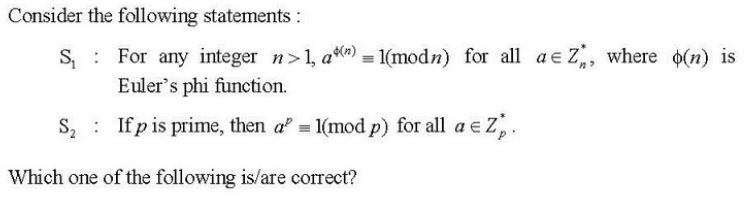 |
| i ➥ Only S1 |
| ii ➥ Only S2 |
| iii ➥ Both S1 and S2 |
| iv ➥ Neither S1 nor S2 |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Network Security | Help-Line |
| Q12➡ How many address lines and data lines are required to provide a memory capacity of 16K x 16? |
| A ➥ 10,4 |
| B ➥ 16,16 |
| C ➥ 14,16 |
| D ➥ 4,16 |
Show Answer With Best Explanation
| Q13➡ Match List-I with List-II: 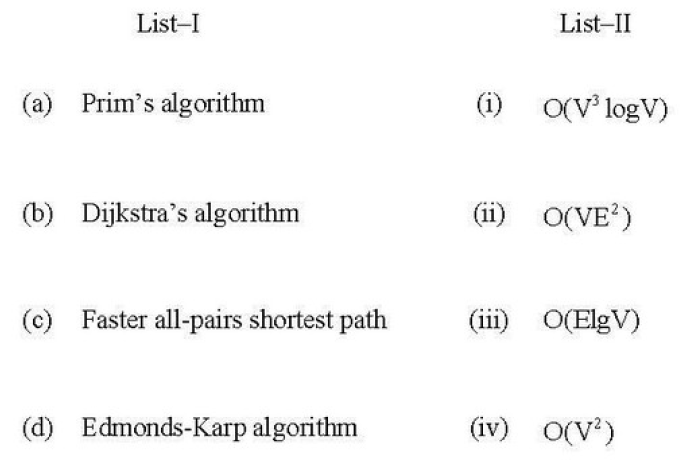 Choose the correct option from those given below |
| A ➥ (a)-(ii); (b)-(iv); (c)-(i); (d)-(iii) |
| B ➥ (a)-(iii); (b)-(iv); (c)-(i); (d)-(ii) |
| C ➥ (a)-(ii); (b)-(i); (c)-(iv); (d)-(iii) |
| D ➥ (a)-(iii); (b)-(i) (c)-(iv); (d)-(ii) |
Show Answer With Best Explanation
Q14➡ |
| A ➥ (a)-(ii); (b)-(i); (c)-(iii) |
| B ➥ (a)-(ii); (b)-(iii); (c)-(i) |
| C ➥ (a)-(iii); (b)-(i); (c)-(ii) |
| D ➥ (a)-(i); (b)-(ii); (c)-(iii) |
Show Answer With Best Explanation
| Q15➡ Consider the equation (146)b + (313)b-2 = (246)8 . Which of the following is the value of b? |
| A ➥ 8 |
| B ➥ 7 |
| C ➥ 10 |
| D ➥ 16 |
Show Answer With Best Explanation
| Q16➡ Suppose that a connected planar graph has six vertices, each of degrees four. Into how many regions is the plane divided by a planar representation of this graph? |
| A ➥ 6 |
| B ➥ 8 |
| C ➥ 12 |
| D ➥ 10 |
Show Answer With Best Explanation
| Q17➡ Which of the following is principal conjunctive normal form for [(pVq) ∧ ~p → ~q]? |
| A ➥ p V ~q |
| B ➥ p V q |
| C ➥ ~p V q |
| D ➥ ~p V ~q |
Show Answer With Best Explanation
| Q18➡ Which of the following features is supported in the relational database model? |
| A ➥ Complex data-types |
| B ➥ Multivalued attributes |
| C ➥ Association with multiplicities |
| D ➥ Generalization relationship |
Show Answer With Best Explanation
| Q19➡ Which of the following UNIX/Linux pipes will count the number of lines in all the files having .c and .h as their extension in the current working directory? |
| A ➥ cat *.ch | wc -l |
| B ➥ cat *.[c-h] | wc -l |
| C ➥ cat *.[ch] | ls -l |
| D ➥ cat *.[ch] | wc -l |
Show Answer With Best Explanation
| Q20➡ | Computer Network A fully connected network topology is a topology in which there is a direct link between all pairs of nodes. Given a fully connected network with n nodes, the number of direct links as a function of n can be expressed as |
| i ➥ n(n+1)/2 |
| ii ➥ (n+1)/2 |
| iii ➥ n/2 |
| iv ➥ n(n-1)/2 |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | IP Address | Help-Line |
| Q21➡ A processor can support a maximum memory of 4 GB where memory is word addressable and a word is 2 bytes. What will be the size of the address bus of the processor? |
| A ➥ At least 28 bits |
| B ➥ At least 2 bytes |
| C ➥ At least 31 bits |
| D ➥ Minimum 4 bytes |
Show Answer With Best Explanation
Q22➡ |
| A ➥ (a) and (b) only |
| B ➥ (a) only |
| C ➥ (a), (b) and (c) |
| D ➥ (c) only |
Show Answer With Best Explanation
| Q23➡ Which of the following is an example of unsupervised neural network? |
| A ➥ Back propagation network |
| B ➥ Hebb network |
| C ➥ Associative memory network |
| D ➥ Self-organizing feature map |
Show Answer With Best Explanation
| Q24➡ Which of the following statements is/are true with regard to various layers in the Internet stack? P: At the link layer, a packet of transmitted information is called a frame Q: At the network layer, a packet of transmitted information is called a segment |
| A ➥ P only |
| B ➥ Q only |
| C ➥ P and Q |
| D ➥ Neither P nor Q |
Show Answer With Best Explanation
Q25➡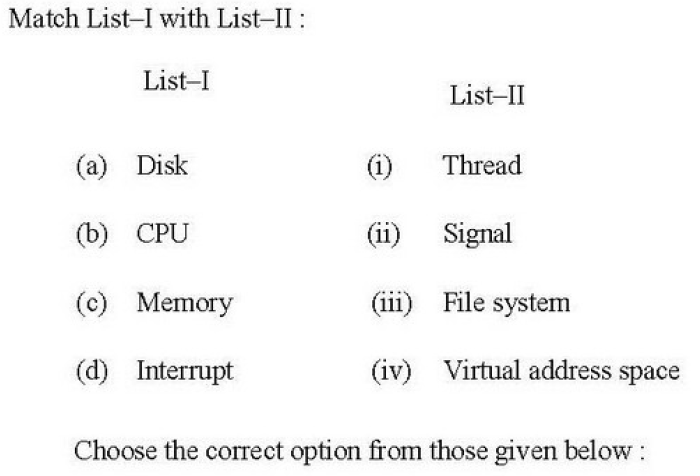 |
| A ➥ (a)-(i); (b)-(ii); (c)-(iii); (d)-(iv) |
| B ➥ (a)-(iii); (b)-(i); (c)-(iv); (d)-(ii) |
| C ➥ (a)-(ii); (b)-(i); (c)-(iv); (d)-(iii) |
| D ➥ (a)-(ii); (b)-(iv); (c)-(iii);(d)-(i) |
Show Answer With Best Explanation
| Q26➡ Consider the following C++ function f() : unsigned int f(unsigned int n) { unsigned int b=0; while(n) { b+=n&1; n>>=1; } return b; } The function f() returns the int that represents the___p___in the binary representation of positive integer n, where P is |
| A ➥ number of 0’s |
| B ➥ number of bits |
| C ➥ number of consecutive 1’s |
| D ➥ number of 1’s |
Show Answer With Best Explanation
| Q27➡ Which of the following key constraints is required for functioning of foreign key in the context of relational database? |
| A ➥ Unique key |
| B ➥ Primary key |
| C ➥ candidate key |
| D ➥ Check key |
Show Answer With Best Explanation
Q28➡ |
| A ➥ x=pn |
| B ➥ m=pn |
| C ➥ p=xn |
| D ➥ p=mn |
Show Answer With Best Explanation
| Q29➡ For a statement A language L ⊆ Σ* is recursive if there exists some Turing machine M Which of the following conditions is satisfied for any string w? |
| A ➥ If w ε L, then m accepts w and M will not halt |
| B ➥ If w ∉ L, then M accepts w and M will halt by reaching at final state |
| C ➥ If w ∉ L, then M halts without reaching to acceptable state |
| D ➥ If w ε L, then M halts without reaching to an acceptable state |
Show Answer With Best Explanation
| Q30➡ Which of the following is best running time to sort n integers in the range 0 to n2-1 |
| A ➥ O(log n) |
| B ➥ O(n) |
| C ➥ O(n log n) |
| D ➥ O(n2) |
Show Answer With Best Explanation
| Q31➡ Which of the following are the primary objectives of risk monitoring in software project tracking? P: To assess whether predicted risks do, in fact, occur Q: To ensure that risk aversion steps defined for the risk are being properly applied R: To collect information that can be used for future risk analysis |
| A ➥ Only P and Q |
| B ➥ Only P and R |
| C ➥ Only Q and R |
| D ➥ All the P,Q,R |
Show Answer With Best Explanation
| Q32➡ How can the decision algorithm be constructed for deciding whether context-free language L is finite? (a) By Constructing redundant CFG in CNF generating language L (b) By constructing non-redundant CFG G in CNF generating language L (c) By constructing non-redundant CFG in CNF generating language L-{∧} (∧ stands for null) Which of the following is correct? |
| A ➥ (a) only |
| B ➥ (b) only |
| C ➥ (c) only |
| D ➥ None of(a),(b) and (c) |
Show Answer With Best Explanation
| Q33➡ How many states are there in a minimum state automata equivalent to regular expression given below? Regular expression is a*b(a+b) |
| A ➥ 1 |
| B ➥ 2 |
| C ➥ 3 |
| D ➥ 4 |
Show Answer With Best Explanation
| Q34➡ With respect to relational algebra, which of the following operations are included from mathematical set theory (a) join (b) Intersection (c) Cartisian product (d) Project |
| A ➥ (a) and (b) |
| B ➥ (b) and (c) |
| C ➥ (c) and (d) |
| D ➥ (b) and (d) |
Show Answer With Best Explanation
| Q35➡ For which values of m and n does the complete bipartite graph Km,n have a Hamilton circuit? |
| A ➥ m≠n, m, n≥2 |
| B ➥ m≠n, m, n≥3 |
| C ➥ m=n, m, n≥2 |
| D ➥ m=2, m, n≥3 |
Show Answer With Best Explanation
Q36➡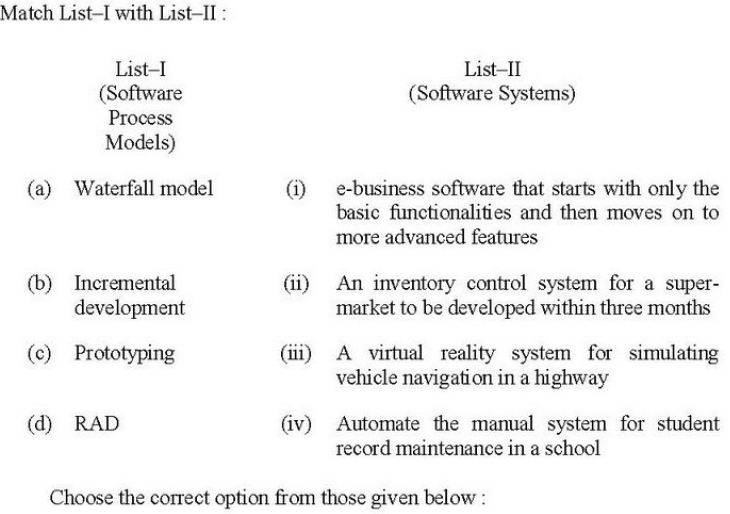 |
| A ➥ (a)-(ii),(b)-(iv),(c)-(i),(d)-(iii) |
| B ➥ (a)-(i),(b)-(iii),(c)-(iv),(d)-(ii) |
| C ➥ (a)-(iii),(b)-(ii),(c)-(iv),(d)-(i) |
| D ➥ (a)-(iv),(b)-(i),(c)-(iii),(d)-(ii) |
Show Answer With Best Explanation
| Q37➡ In relational database management, which of the following is/are property/properties of candidate key? P:Uniqueness Q: Irreducibility |
| A ➥ P only |
| B ➥ Q only |
| C ➥ Both P and Q |
| D ➥ Neither P nor Q |
Show Answer With Best Explanation
| Q38➡ In the context of software testing, which of the following statements is/are NOT correct? P: A minimal test set that achieves 100% path coverage will also achieve 100% statement coverage. Q: A minimal test set that achieves 100% path coverage will generally detect more faults than one that achieves 100% statement coverage R: A minimal test set that achieves 100% statement coverage will generally detect more faults than one that achieves 100% branch coverage |
| A ➥ R only |
| B ➥ Q only |
| C ➥ P and Q only |
| D ➥ Q and R only |
Show Answer With Best Explanation
| Q39➡ Software products need are adaptive maintenance for which of the following reasons? |
| A ➥ To rectify bugs observed while the system is in use. |
| B ➥ When the customers need the product to run on new platforms |
| C ➥ To support the new features that users want it to support |
| D ➥ To overcome wear and tear caused by the repeated use of the software. |
Show Answer With Best Explanation
| Q40➡ Which of the following terms best describes Git? |
| A ➥ Issue Tracking System |
| B ➥ Integrated Development Environment |
| C ➥ Distributed Version Control System |
| D ➥ Web-Based Repository Hosting Service |
Show Answer With Best Explanation
| Q41➡ Consider the complexity class CO-NP as the set of languages L such that L’ ε NP, and the following two statements: S1 : P ⊆ CO-NP S2 : If NP ≠ CO-NP, then P ≠ NP Which of the following is/are correct? |
| A ➥ Only S1 |
| B ➥ Only S2 |
| C ➥ Both S1 and S2 |
| D ➥ Neither S1 nor S2 |
Show Answer With Best Explanation
| Q42➡ For a magnetic disk with concentric circular tracks, the seek latency is not linearly proportional to the seek distance due to |
| A ➥ Non-Uniform distribution of requests |
| B ➥ arm starting or stopping inertia |
| C ➥ higher capacity of tracks on the periphery of the plate |
| D ➥ use of unfair arm scheduling policies |
Show Answer With Best Explanation
| Q43➡ A web application and its support environment has not been fully fortified against attack. Web engineers estimate that the likelihood of repelling an attack is only 30 percent. The application does not contain sensitive or controversial information, so the threat probability is 25 percent. What is the integrity of the web application? |
| A ➥ 0.625 |
| B ➥ 0.725 |
| C ➥ 0.775 |
| D ➥ 0.825 |
Show Answer With Best Explanation
| Q44➡ Following table has two attributes Employee_id and Manager_id, where Employee_id is a primary key and manager_id is a foreign key referencing Employee_id with on-delete cascade: 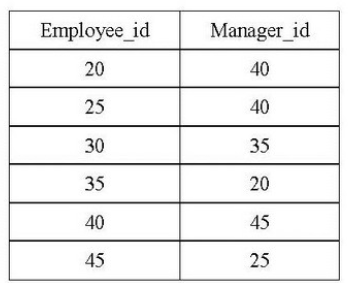 On deleting the table (20,40), the set of other tuples that must be deleted to maintain the referential integrity of table is |
| A ➥ (30,35) only |
| B ➥ (30,35) and (35,20) only |
| C ➥ (35,20) only |
| D ➥ (40,45) and (25,40) only |
Show Answer With Best Explanation
| Q45➡ How many are there to place 8 indistinguishable balls into four distinguishable bins? |
| A ➥ 70 |
| B ➥ 165 |
| C ➥ 8C4 |
| D ➥ 8P4 |
Show Answer With Best Explanation
| Q46➡ Match List-I with List-II: 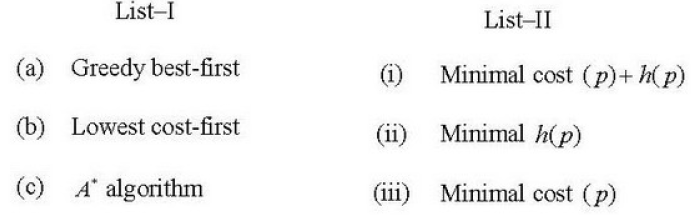 Choose the correct option from those given below: |
| A ➥ (a)-(i); (b)-(ii); (c)-(iii) |
| B ➥ (a)-(iii);(b)-(ii); (c)-(i) |
| C ➥ (a)-(i); (b)-(iii); (c)-(ii) |
| D ➥ (a)-(ii); (b)-(iii); (c)-(i) |
Show Answer With Best Explanation
| Q47➡ A computer has six tapes drives with n processes competing for them. Each process may need two drives. What is the maximum value of n for the system to be deadlock free? |
| A ➥ 5 |
| B ➥ 4 |
| C ➥ 3 |
| D ➥ 6 |
Show Answer With Best Explanation
Q48➡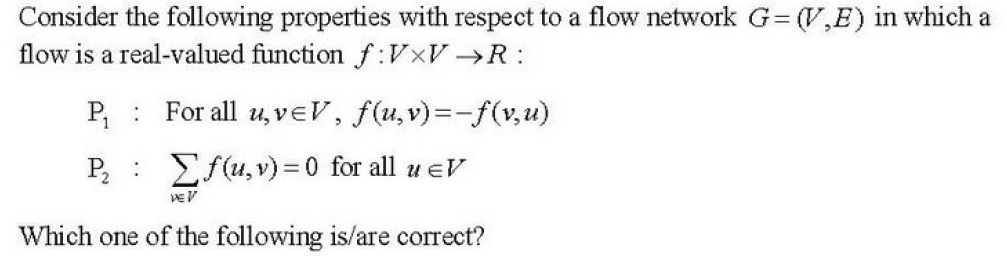 |
| A ➥ Only P1 |
| B ➥ Only P1 |
| C ➥ Both P1 and 2 |
| D ➥ Neither P1 nor P2 |
Show Answer With Best Explanation
| Q49➡ The component in MVC is responsible for |
| A ➥ User interface |
| B ➥ Security of the system |
| C ➥ Business logic and domain objects |
| D ➥ Translating between user interface actions/events and operation on the domain objects |
Show Answer With Best Explanation
| Q50➡ Which of the following statements is/are TRUE? P: In software engineering, defects that are discovered earlier are more expensive to fix Q: A software design is said to be a good design, if the components are strongly cohesive and weakly coupled Select the correct answer from the options given below: |
| A ➥ P only |
| B ➥ Q only |
| C ➥ P and Q |
| D ➥ Neither P nor Q |
Show Answer With Best Explanation
| Q51➡ Reinforcement learning can be formalized in terms of _____ in which the agent initially only knows the set of possible_____ and the set of possible actions. |
| A ➥ Markov decision processes, objects |
| B ➥ Hidden states,Objects |
| C ➥ Markov decision Processes , States |
| D ➥ Objects, States |
Show Answer With Best Explanation
| Q52➡ On translating the expression given below into quadruple representation, how many operations are required? (i*j)+(e+f)(a*b+c) |
| A ➥ 5 |
| B ➥ 6 |
| C ➥ 3 |
| D ➥ 7 |
Show Answer With Best Explanation
| Q53➡ There are many sorting algorithms based on comparison. The running time of heap sort algorithm is O(nlogn). Let P, but unlike Q, heapsort sorts in place where (P,Q) is equal to |
| A ➥ Merge sort, Quick sort |
| B ➥ Quick sort, Insertion sort |
| C ➥ Insertion sort, Quick sort |
| D ➥ insertion sort, Merge sort |
Show Answer With Best Explanation
Q54➡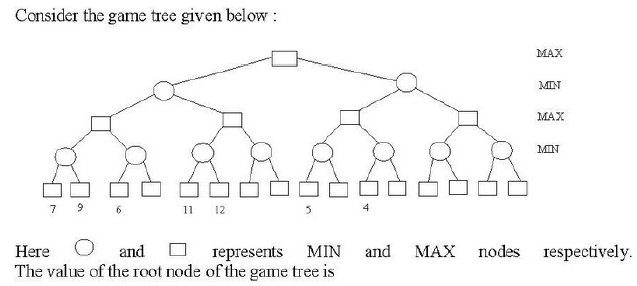 |
| A ➥ 4 |
| B ➥ 7 |
| C ➥ 11 |
| D ➥ 12 |
Show Answer With Best Explanation
| Q55➡ Suppose that the register A and register K have the bit configuration. Only the three leftmost bits of A are compared with memory words because K has 1’s in these positions. Because of its organization, this type of memory is uniquely suited to parallel seches by data association. This type of memory is known as |
| A ➥ RAM |
| B ➥ ROM |
| C ➥ Content addressable memory |
| D ➥ Secondary memory |
Show Answer With Best Explanation
| Q56➡ Consider the following C-code fragment running on a 32-bit x86 machine: typedef struct { union { Unsigned char a; unsigned short b; } unsigned char c; }S; ________________________________ S B[10]; Sp=&B[4]; Sq=&B[5]; p→ U.b=0x1234; /* structure S takes 32-bits */ If M is the value of q-p and N is the value of ((int) & (p→ c))-((int)p), then (M,N) is |
| A ➥ (1,1) |
| B ➥ (3,2) |
| C ➥ (1,2) |
| D ➥ (4,4) |
Show Answer With Best Explanation
| Q57➡ Consider the following grammar: S→ XY X→ YaY | a and y → bbX Which of the following statements is/are true about the above grammar? (a) Strings produced by the grammar can have consecutive three a’s (b) Every string produced by the grammar have alternate a and b (c) Every string produced by the grammar have at least two a’s (d) Every string produced by the grammar have b’s in multiple of 2. |
| A ➥ (a) only |
| B ➥ (b) and (c) only |
| C ➥ (d) only |
| D ➥ (c) and (d) only |
Show Answer With Best Explanation
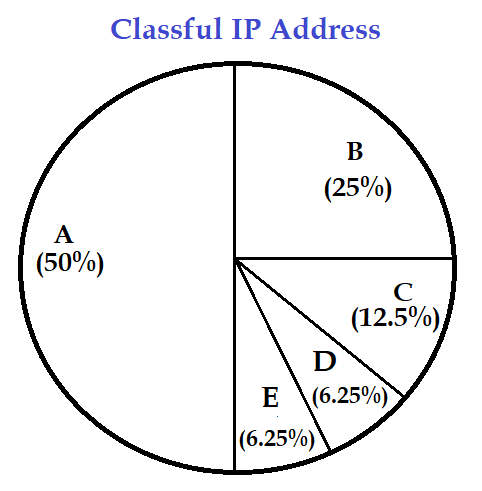
| Q58➡ | Computer Network What percentage(%) of the IPv4, IP address space do all class C addresses consume? |
| i ➥ 12.5% |
| ii ➥ 25% |
| iii ➥ 37.5% |
| iv ➥ 50% |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | IP Address | Help-Line |
| Q59➡ How many cards must be selected from a standard deck of 52 cards to guarantee that at least three hearts are present among them? |
| A ➥ 9 |
| B ➥ 13 |
| C ➥ 17 |
| D ➥ 42 |
Show Answer With Best Explanation
| Q60➡ How many bit strings of length ten either start with a 1 bit or end with two bits 00? |
| A ➥ 320 |
| B ➥ 480 |
| C ➥ 640 |
| D ➥ 768 |
Show Answer With Best Explanation
| Q61➡ A fuzzy conjunction operator denoted as t(x,y) and fuzzy disjunction operator denoted as s(x,Y) form dual pair if they satisfy the condition: |
| A ➥ t(x,y)= 1-s(x,y) |
| B ➥ t(x,y)=s(1-x,1-y) |
| C ➥ t(x,y)=1-s(1-x,1-y) |
| D ➥ t(x,y)=s(1+x,1+y) |
Show Answer With Best Explanation
| Q62➡ | Computer Network The ability to inject packets into the internet with false source address is known as : |
| i ➥ Man-in-the-Middle attack |
| ii ➥ IP phishing |
| iii ➥ IP sniffing |
| iv ➥ IP Spoofing |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Network Security | Help-Line |
| Q63➡ | Computer Network The RSA encryption algorithm also works in reverse, that is, you can encrypt a message with the private key and decrypt it using the public key. This property is used in |
| i ➥ Intrusion detection systems |
| ii ➥ Digital signatures |
| iii ➥ Data Compression |
| iv ➥ Certification |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Network Security | Help-Line |
| Q64➡ K-mean clustering algorithm has clustered the given 8 observations into 3 clusters after 1st iteration as follows: C1 : {(3,3), (5,5), (7,7)} C2 : {(0,6), (6,0), (3,0)} C3 : {(8,8),(4,4)} What will be the Manhattan distance for observation (4,4) from cluster centroid C1 in second iteration? |
| A ➥ 2 |
| B ➥ √2 |
| C ➥ 0 |
| D ➥ 18 |
Show Answer With Best Explanation
| Q65➡ The STRIPS representation is |
| A ➥ a feature-centric representation |
| B ➥ an action-centric representation |
| C ➥ a combination of feature-centric and action-centric representation |
| D ➥ a hierarchical feature-centric representation |
Show Answer With Best Explanation
| Q66➡ The minimum number of page frames that must be allocated to a running process in a virtual memory environment is determined by |
| A ➥ Page size |
| B ➥ Physical size of memory |
| C ➥ The instruction set architecture |
| D ➥ Number of processes in memory |
Show Answer With Best Explanation
Q67➡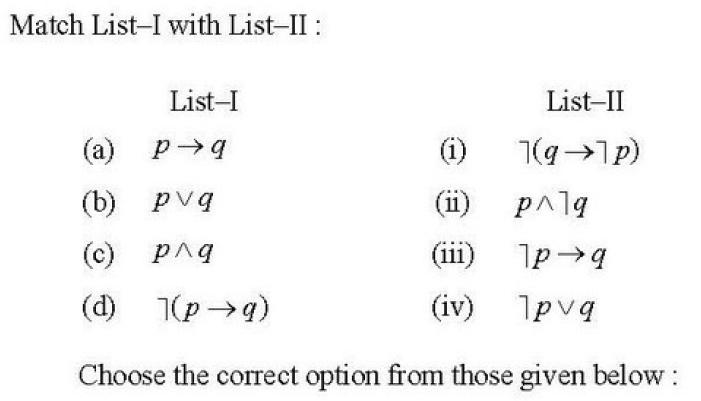 |
| A ➥ (a)-(ii);(b)-(iii);(c)-(i);(d)-(iv) |
| B ➥ (a)-(ii);(b)-(i);(c)-(iii);(d)-(iv) |
| C ➥ (a)-(iv);(b)-(i);(c)-(iii);(d)-(ii) |
| D ➥ (a)-(iv);(b)-(iii);(c)-(i);(d)-(ii) |
Show Answer With Best Explanation
| Q68➡ How many different Boolean functions of degree n are there? |
A ➥  |
B ➥ 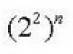 |
C ➥ 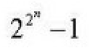 |
| D ➥ |
Show Answer With Best Explanation
| Q69➡ The fault can be easily diagnosed in the microprogram control unit using diagnostic tools by maintaining the contents of |
| A ➥ Flags and Counters |
| B ➥ Registers and counters |
| C ➥ Flags and registers |
| D ➥ Flags, registers and counters |
Show Answer With Best Explanation
| Q70➡ | Computer Graphics Using the phong reflectance model, the strength of the specular highlight is determined by the angle between |
| i ➥ The view vector and the normal vector |
| ii ➥ The light vector and the normal vector |
| iii ➥ The light vector and the reflected vector |
| iv ➥ the reflected vector and the view vector |
Show Answer With Best Explanation
| Q71➡ Which of the following statements is/are true? P: In a scripting language like javaScript, types are typically associated with values, not variables. Q: It is not possible to show images on a web page without the tag of HTML Select the correct answer from the given below: |
| A ➥ P only |
| B ➥ Q only |
| C ➥ Both P and Q |
| D ➥ neither P nor Q |
Show Answer With Best Explanation
| Q72➡ Which of the following statements are DML statements? (a) Update [table_name] Set [ column_name] = VALUE (b) Delete [table_name] (c) Select * from [table_name] |
| A ➥ (a) and (b) |
| B ➥ (a) and (d) |
| C ➥ (a), (b) and (c) |
| D ➥ (b) and (c) |
Show Answer With Best Explanation
| Q73➡ Let Aα0 denotes the α-cut of a fuzzy set A at α0. If α1 < α2 , then |
| A ➥ Aα1 ⊇ Aα2 |
| B ➥ Aα1 ⊃ Aα2 |
| C ➥ Aα1 ⊆ Aα2 |
| D ➥ Aα1 ⊂ Aα2 |
Show Answer With Best Explanation
| Q74➡ The parallel bus arbitration technique uses an external priority encoder and a decoder. Suppose, a parallel arbiter has 5 bus arbiters. What will be the size of priority encoder and decoder respectively? |
| A ➥ 4×2, 2×4 |
| B ➥ 2×4, 4×2 |
| C ➥ 3×8, 8×3 |
| D ➥ 8×3, 3×8 |
Show Answer With Best Explanation
| Q75➡ Which type of addressing mode, less number of memory references are required? |
| A ➥ Immediate |
| B ➥ Implied |
| C ➥ register |
| D ➥ indexed |
Show Answer With Best Explanation
| Q76➡ | Computer Network You need 500 subnets, each with about 100 usable host addresses per subnet. What network mask will you assign using a class B network address? |
| i ➥ 255.255.255.252 |
| ii ➥ 255.255.255.128 |
| iii ➥ 255.255.255.0 |
| iv ➥ 255.255.254.0 |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | IP Address | Help-Line |
| Q77➡ Which of the following has the same expressive power with regard to relational query language? (a) Relational algebra and Domain relational calculus (b) Relational algebra and Tuple relational calculus (c) Relational algebra and Domain relational calculus restricted to safe expression (d) Relational algebra and Tuple relational calculus restricted to safe expression |
| A ➥ (a) and (b) only |
| B ➥ (c) and (d) only |
| C ➥ (a) and (c) only |
| D ➥ (b) and (d) only |
Show Answer With Best Explanation
| Q78➡ At a particular time of computation, the value of a counting semaphore is 7. Then 20 P(wait) operations and 15 V(signal) operations are completed on this semaphore. What is the resulting value of the semaphore? |
| A ➥ 28 |
| B ➥ 12 |
| C ➥ 2 |
| D ➥ 42 |
Show Answer With Best Explanation
| Q79➡ Which of the following statements is/are true P: An XML document with correct as specified by W3C is called “well formed”. Q: An XML documented validated against a DTD is both “Well-Formed” and “valid”. R: is syntactically correct declaration for the version of an XML document. Select the correct answer from the options given below: |
| A ➥ P and Q only |
| B ➥ P and R only |
| C ➥ Q and R only |
| D ➥ All of P,Q and R |
Show Answer With Best Explanation
| Q80➡ Which of the following is an application of depth-first search? |
| A ➥ Only topological sort |
| B ➥ Only strongly connected components |
| C ➥ Both topological sort and strongly connected components |
| D ➥ Neither topological sort not strongly connected components |
Show Answer With Best Explanation
| Q81➡ What will be the number of states when a MOD-2 counter is followed by a MOD-5 counter? |
| A ➥ 5 |
| B ➥ 10 |
| C ➥ 15 |
| D ➥ 20 |
Show Answer With Best Explanation
| Q82➡ Replacing the expression 4*2.14 by 8.56 is known as |
| A ➥ Constant folding |
| B ➥ Induction variable |
| C ➥ Strength reduction |
| D ➥ Code reduction |
Show Answer With Best Explanation
| Q83➡ Hadoop(a big data tool) works with number of related tools. Choose from the following, the common tools included into Hadoop: |
| A ➥ MySQl, Google API and Map reduce |
| B ➥ Map reduce, Scala and hummer |
| C ➥ Map reduce, H base and Hive |
| D ➥ Map reduce, hummer and Heron |
Show Answer With Best Explanation
| Q84➡ | Computer Network What is the name of the protocol that allows a client to send a broadcast message with its MAC address and receive an IP address in reply? |
| i ➥ ARP |
| ii ➥ DNS |
| iii ➥ RARP |
| iv ➥ ICMP |
Show Answer With Best Explanation
| Q85➡ Consider the following methods: M 1 : mean of maximum M 2 : Centre of area M 3 : Height method Which of the following is/are defuzzification method(s)? |
| A ➥ Only M 1 |
| B ➥ Only M 1 and M 2 |
| C ➥ Only M 2and M 3 |
| D ➥ M 1 , M 2 and M 3 |
Show Answer With Best Explanation
Q86➡ | Computer Graphics |
| i ➥ Both S1 and S2 are true |
| ii ➥ Only S1 is true |
| iii ➥ Only S2 is true |
| iv ➥ Both S1 and S2 are false |
Show Answer With Best Explanation
| Q87➡ Suppose that a computer program takes 100 seconds of execution time on a computer with multiplication operation responsible for 80 seconds of this time. How much do you have to improve the speed of multiplication operation if you are asked to execute this program four times faster. |
| A ➥ 14 times faster |
| B ➥ 15 times faster |
| C ➥ 16 times faster |
| D ➥ 17 times faster |
Show Answer With Best Explanation
| Q88➡ Consider a disk system with 100 cylinders. The requests to access the cylinders occur in the following sequence: 4,34,10,7,19,73,2,15,6,20 Assuming that the head is current at cylinder 50, what is the time taken to satisfy all requests if it takes 1ms to move from the cylinder to adjacent one and the shortest seek time first policy is used? |
| A ➥ 357 ms |
| B ➥ 238 ms |
| C ➥ 276 ms |
| D ➥ 119 ms |
Show Answer With Best Explanation
Q89➡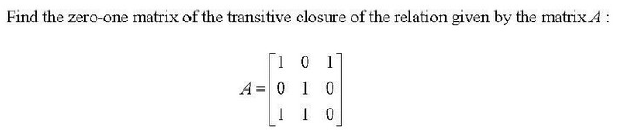 |
A ➥  |
B ➥  |
C ➥  |
D ➥ 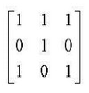 |
Show Answer With Best Explanation
Q90➡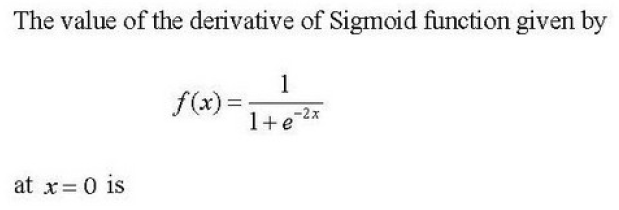 |
| A ➥ 0 |
| B ➥ 1/2 |
| C ➥ 1/4 |
| D ➥ ∞ |
Show Answer With Best Explanation
| Q91➡ | Computer Network Consider the following two statements with respect to IPv4 in computer networking: P: The loopback(IP) address is a member of class B network Q: The loopback(IP) address is used to send a packet from host to itself What can you say about the statements P and Q? |
| i ➥ P-True; Q-False |
| ii ➥ P-False; Q-True |
| iii ➥ P-True; Q-True |
| iv ➥ P-False; Q-false |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | IP Address | Help-Line |
| Q92➡ Consider the following: (a) Evolution (b) Selection (c) reproduction (d) Mutation Which of the following are found in genetic algorithms? |
| A ➥ (b),(c) and (d) only |
| B ➥ (b) and (d) only |
| C ➥ (a),(b),(c) and (d) |
| D ➥ (a),(b) and (d) only |
Show Answer With Best Explanation
| Q➡ | Computer Graphics Consider a raster system with resolution 640 by 480. What size is frame buffer (in bytes) for this system to store 12 bits per pixel? |
| i ➥ 450 kilobytes |
| ii ➥ 500 Kilobytes |
| iii ➥ 350 kilobytes |
| iv ➥ 400 kilobytes |
Show Answer With Best Explanation
| Q94➡ Consider the following steps: S1 : Characterize the structure of an optimal solution S2 : Computer the value of an optimal solution in bottom-up fashion Which of the step(s) is/are common to both dynamic programming and greedy algorithms? |
| A ➥ Only S1 |
| B ➥ Only S2 |
| C ➥ Both S1 and S2 |
| D ➥ Neither S1 nor S2 |
Show Answer With Best Explanation
| Q95➡ | Computer Graphics In the context of 3D computer graphics, which of the following statements is/are TRUE? P: Orthographic transformations keep parallel lines parallel Q: Orthographic transformations are affine transformations Select the correct answer from the options given below: |
| A ➥ Both P and Q |
| B ➥ Neither P and Q |
| C ➥ Only P |
| D ➥ Only Q |
Show Answer With Best Explanation
| Q96➡ Consider the poset ({3,5,9,15,24,45},|). Which of the following is correct for the given poset? |
| A ➥ There exists a greatest element and a least element |
| B ➥ There exists a greatest element but not a least element |
| C ➥ There exists a least element but not a greatest element |
| D ➥ There does not exist a greatest element and a least element |
Show Answer With Best Explanation
| Q97➡ | Computer Network You are designed a link layer protocol for a link with bandwidth of 1 Gbps (109 bits/second) over a fiber link with length of 800 km. Assume the speed of light in this medium is 200000 km/second. What is the propagation delay in this link? |
| i ➥ 1 millisecond |
| ii ➥ 2 millisecond |
| iii ➥ 3 millisecond |
| iv ➥ 4 millisecond |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Delay | Help-Line |
| Q98➡ What is the output of the following JAVA program? public class Good{ Private int m; Public Good(int m){this.m=m;} public Boolean equals(Good n){return n.m=m;} public static void main(String args [ ]){ Good m1=new Good(22); Good m2=new Good(22); Object S1=new Good(22); Object S2=new good(22); System.out.println(m1.equals(m2)); System.out.println(m1.equals(s2)); System.out.println(m1.equals(s2)); System.out.println(s1.equals(m2)); } } |
| A ➥ True, True, False, False |
| B ➥ True, false, True, false |
| C ➥ True, True, False, True |
| D ➥ true, False, False, False |
Show Answer With Best Explanation
| Q99➡ Software validation mainly checks for inconsistencies between |
| A ➥ Use cases and user requirements |
| B ➥ Implementation and system design blueprints |
| C ➥ Detailed specifications and user requirements |
| D ➥ Function specifications and use cases |
Show Answer With Best Explanation
Q100➡ | Computer Network 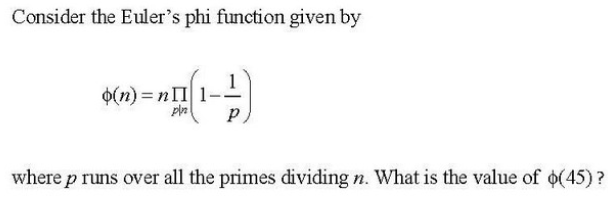 |
| i ➥ 3 |
| ii ➥ 12 |
| iii ➥ 6 |
| iv ➥ 24 |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Network Security | Help-Line |