UGC NET Computer Science Question Solution DEC- 2019 -Paper -II
UGC NET Computer Science Question Solution DEC- 2019 -Paper -II
| Question 1 Consider the following statements: (a) The running time of dynamic programming algorithm is always θ(ρ) where ρ is number of subproblems. (b) When a recurrence relation has cyclic dependency, it is impossible to use that recurrence relation (unmodified) in a correct dynamic program. (c) For a dynamic programming algorithm, computing all values in a bottom-up fashion is asymptotically faster than using recursion and memorization. (d) If a problem X can be reduced to a known NP-hard problem, then X must be NP-hard. Which of the statement(s) is (are) true? |
| A – Only (b) and (a) |
| B – Only (b) |
| C – Only (b) and (c) |
| D – Only (b) and (d) |
Show Answer With Best Explanation
| Question 2 Let G = (V, T, S, P) be any context-free grammar without any λ-productions or unit productions. Let K be the maximum number of symbols on the right of any production P. The maximum number of production rules for any equivalent grammar in Chomsky normal form is given by: |
| A – (K – 1) |P| + |T| – 1 |
| B – (K – 1) |P| +| T| |
| C – K |P| + |T| – 1 |
| D – K |P| + |T| |
Show Answer With Best Explanation
| Question 3➡ | NTA UGC NET December 2019 Which of the following is not needed by an encryption algorithm used in Cryptography? A) KEY B) Message C) Ciphertext D) User details |
| i ➥ (C) only |
| ii ➥ (D) only |
| iii ➥ (B) , (C) and (D) only |
| iv ➥ (C) and (D) only |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Network Security | Help-Line |
| Question 4 A Non-pipelined system takes 30ns to process a task. The same task can be processed in a four-segment pipeline with a clock cycle of 10ns. Determine the speed up of the pipeline for 100 tasks |
| A – 3 |
| B – 4 |
| C – 3.91 |
| D – 2.91 |
Show Answer With Best Explanation
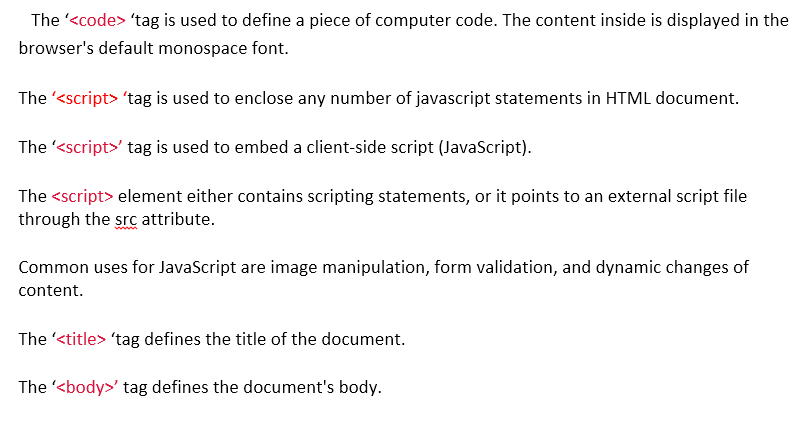
| Question 5 Which tag is used to enclose any number of java script statements in HTML document? |
| A – < code > |
| B – < script > |
| C – < title > |
| D – < body > |
Show Answer With Best Explanation
| Question 6 Consider the following languages: L1 = {anbncm} ∪ {an bm cm}, n. m ≥ o L2 = {ωωR |ω ∈ {a, b}*} Where R represents reversible operation. Which one of the following is (are) inherently ambiguous language(s)? |
| A – only L1 |
| B – only L2 |
| C – both L1 and L2 |
| D – neither L1 nor L2 |
Show Answer With Best Explanation
Question 7 |
| A – (a).(i), (b).(ii), (c).(iii), (d).(iv) |
| B – (a).(ii), (b).(i), (c).(iii), (d).(iv) |
| C – (a).(iv), (b).(iii), (c).(ii), (d).(i) |
| D – (a).(iii), (b).(iv), (c).(ii), (d).(i) |
Show Answer With Best Explanation
| Question 8➡ | Computer Network A network with a bandwidth of 10 Mbps can pass only an average of 12,000 frames per minute with each frame carrying an average of 10,000 bits. What is the throughput of this network? |
| i ➥ 1,000,000 bps |
| ii ➥ 2,000,000 bps |
| iii ➥ 12,000,000 bps |
| iv ➥ 1,200,00,000 bps |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Flow Control | Help-Line |
| Question 9 Consider Σ = {w, x} and T = {x, y, z}. Define homomorphism h by : h(x) = xzy h(w) = zxyy If L is the regular language denoted by T= (w + x*)(ww)*, then the regular language h(L) is given by |
| A – (zxyy + xy) (z x yy) |
| B – (zxyy + (xzy)*) (zxyy zxyy)* |
| C – (zxyy + xyz) (zxyy)* |
| D – (zxyy + (xzy)* (zxyy zxyy) |
Show Answer With Best Explanation
| Question 10 A tree has 2n vertices of degree 1, 3n vertices of degree 2, n vertices of degree 3. Determine the number of vertices and edges in tree. |
| A – 12,11 |
| B – 11,12 |
| C – 10,11 |
| D – 9,10 |
Show Answer With Best Explanation
Question 11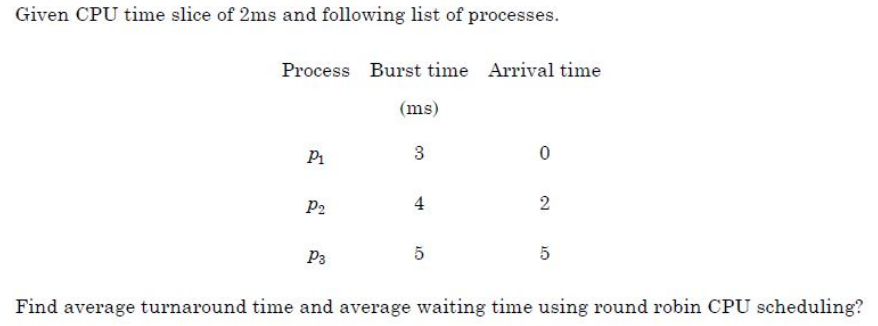 |
| A – 4.0 |
| B – 5.66, 1.66 |
| C – 5.66, 0 |
| D – 7, 2 |
Show Answer With Best Explanation
| Question 12 Consider the following statements: S1: If a group (G,*) is of order n, and a ∈ G is such that am = e for some integer m ≤ n, then m must divide n. S2: If a group (G,*) is of even order , then there must be an element and a ∈ G is such that a ≠ e and a * a = e. Which of the statements is (are) correct? |
| A – Only S1 |
| B – Only S2 |
| C – Both S1 and S2 |
| D – Neither S1 nor S2 |
Show Answer With Best Explanation
| Question 13 What is the worst case running time of Insert and Extract-min, in an implementation of a priority queue using an unsorted array? Assume that all insertions can be accommodated. |
| A – θ(1) , θ(n) |
| B – θ(n) , θ(1) |
| C – θ(1) , θ(1) |
| D – θ(n) , θ(n) |
Show Answer With Best Explanation
| Question 14 Consider the following statements: S1: These exists no algorithm for deciding if any two Turning machine M1 and M2 accept the same language. S2: Let M1 and M2 be arbitrary Turing machines. The problem to determine L(M1)⊆ L(M2)is undecidable. Which of the statements is (are) correct? |
| A – Only S1 |
| B – Only S2 |
| C – Both S1 and S2 |
| D – Neither S1 nor S1 |
Show Answer With Best Explanation
Question 15 |
| A – (p0, p1, p2) |
| B – (p1, p0, p2) |
| C – (p2, p1, p0) |
| D – (p0, p2, p1) |
Show Answer With Best Explanation
| Question 16 Let Wij represents weight between node i at layer k and node j at layer (k – 1) of a given multilayer perceptron. The weight updation using gradient descent method is given by Where α and E represents learning rate and Error in the output respectively? |
| A – 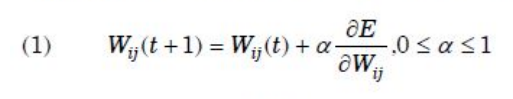 |
B – 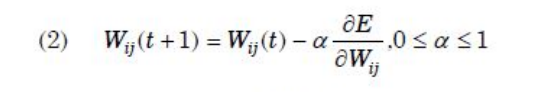 |
C – 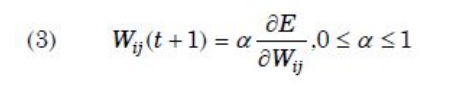 |
D – 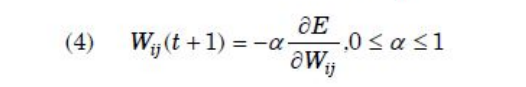 |
Show Answer With Best Explanation
| Question 17 The reduced Instruction Set Computer (RISC) characteristics are: (a) Single cycle instruction execution (b) Variable length instruction formats (c) Instructions that manipulates operands in memory (d) Efficient instruction pipeline Choose the correct characteristics from the options given below: |
| A – (a) and (b) |
| B – (b) and (c) |
| C – (a) and (d) |
| D – (c) and (d) |
Show Answer With Best Explanation
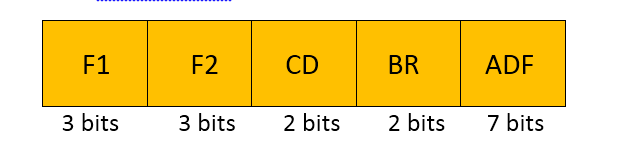
| Question 18 A micro instruction format has micro operation field which is divided into 2 sub fields F1 and F2. Each having 15 distinct micro operations condition field CD for four status bits. Branch field BR having four options used in conjunction with address field AD. The address space is of 128 memory words. The size of micro instruction is |
| A – 19 |
| B – 18 |
| C – 17 |
| D – 20 |
Show Answer With Best Explanation
| Question 19 B-Tree, each node represents a disk block. Suppose one block holds 8192 bytes. Each key uses 32 bytes. In a B-tree of order M there are M – 1 keys. Since each branch is on another disk block, we assume a branch is of 4 bytes. The total memory requirement for a non-leaf node is |
| A – 32 M – 32 |
| B – 36 M – 32 |
| C – 36 M – 36 |
| D – 32 M – 36 |
Show Answer With Best Explanation
| Question 20 Which of the component module of DBMS does rearrangement and possible ordering of operations, eliminate redundancy in query and use efficient algorithms and indexes during the execution of a query? |
| A – Query compiler |
| B – Query optimizer |
| C – Stored data manager |
| D – Database processor |
Show Answer With Best Explanation
| Question 21 Consider the following grammar : S→0A|0BB A→00A| λ B→1B|11C C→B Which language does this grammar generate? |
| A – L(00) * 0+(11)*1) |
| B – L(0(11)* + 1(00)*) |
| C – L((00)*0) |
| D – L(0(11) *1) |
Show Answer With Best Explanation
Question 22 |
| A – x1=750, x2=750, z=1500 |
| B – x1=500, x2=100, z=1500 |
| C – x1=1000, x2=500, z=1500 |
| D – x1=900, x2=600, z=1500 |
Show Answer With Best Explanation
| Question 23 Let A be the base class in C++ and B be the derived class from A with protected inheritance. Which of the following statement is false for class B? |
| A – Member function of class B can access protected data of class A |
| B – Member function of class access public data of class A |
| C – Member function of class B cannot access private data of class A |
| D – Object of derived class B can access public base class data |
Show Answer With Best Explanation
| Question 24 Given two tables EMPLOYEE (EID, ENAME, DEPTNO) DEPARTMENT (DEPTNO. DEPTNAME) Find the most appropriate statement of the given query: Select count (*) ‘total’ from EMPLOYEE where DEPTNO IN (D1, D2) group by DEPTNO having count (*) > 5 |
| A – Total number of employees in each department D1 and D2 |
| B – Total number of employees of department D1 and D2 if their total is >5 |
| C – Display total number of employees in both departments D1 and D2 |
| D – The output of the query must have atleast two rows |
Show Answer With Best Explanation
| Question 25 Which of the following are legal statements in C programming language? (a) int *P = &44; (b) int *P = &r; (c) int P = &a; (d) int P = a: Choose the correct option: |
| A – (a) and (b) |
| B – (b) and (c) |
| C – (b) and (d) |
| D – (a) and (d) |
Show Answer With Best Explanation
| Question 26 Which of the following binary codes for decimal digits are self complementing? (a) 8421 code (b) 2421 code (c) excess-3 code (d) excess-3 gray code Choose the correct option: |
| A – (a) and (b) |
| B – (b) and (c) |
| C – (c) and (d) |
| D – (d) and (a) |
Show Answer With Best Explanation
Question 27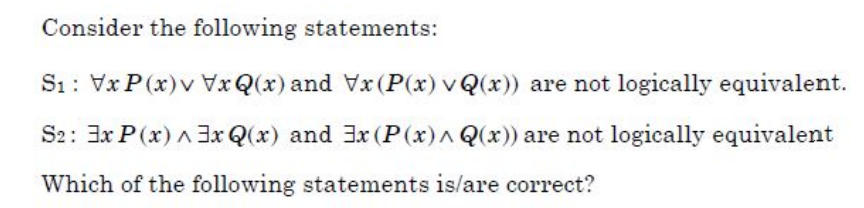 |
| A – Only S1 |
| B – Only S2 |
| C – Both S1 and S2 |
| D – Neither S1 nor S2 |
Show Answer With Best Explanation
| Question 28 Consider a paging system where translation lookaside buffer (TLB) a special type of associative memory is used with hit ratio of 80%. Assume that memory reference takes 80 nanoseconds and reference time to TLB is 20 nanoseconds. What will be the effective memory access time given 80% hit ratio? |
| A – 110 nanoseconds |
| B – 116 nanoseconds |
| C – 200 nanoseconds |
| D – 100 nanoseconds |
Show Answer With Best Explanation
Question 29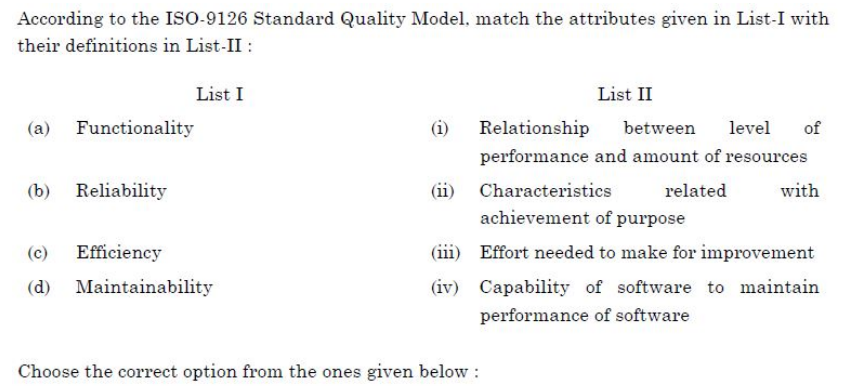 |
| A – (a)-(i), (b)-(ii), (c)-(iii), (d)-(iv) |
| B – (a)-(ii), (b)-(i), (c)-(iv), (d)-(iii) |
| C – (a)-(ii), (b)-(iv), (c)-(i), (d)-(iii) |
| D – (a)-(i), (b)-(ii), (c)-(iv), (d)-(iii) |
Show Answer With Best Explanation
| Question 30 Identify the circumstances under which preemptive CPU scheduling is used : (a) A process switches from Running state to Ready state (b) A process switches from Waiting state to Ready state (c) A process completes its execution (d) A process switches from Ready to Waiting state Choose the correct option: |
| A – (a) and (b) only |
| B – (a) and (d) only |
| C – (c) and (d) only |
| D – (a), (b), (c) only |
Show Answer With Best Explanation
| Question 31 Which of the following interprocess communication model is used to exchange messages among co-operative processes? |
| A – Shared memory model |
| B – Message passing model |
| C – Shared memory and message passing model. |
| D – Queues |
Show Answer With Best Explanation
| Question 32➡ | Computer Network Consider the following statements with respect to network security: (a) Message confidentiality means that the sender and the receiver expect privacy. (b) Message integrity means that the data must arrive at the receiver exactly as they were sent. (c) Message authentication means the receiver is ensured that the message is coming from the intended sender. Which of the statements is (are) correct? |
| i ➥ Only (a) and (b) |
| ii ➥ Only (a) and (c) |
| iii ➥ Only (b) and (c) |
| iv ➥ (a), (b) and (c) |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Network Security | Help-Line |
| Q33➡ | Computer Graphics If we want to resize a 1024 × 768 pixels image to one that is 640 pixels wide with the same aspect ratio, what would be the height of the resized image? |
| i ➥ 420 Pixels |
| ii ➥ 460 Pixels |
| iii ➥ 480 Pixels |
| iv ➥ 540 Pixels |
Show Answer With Best Explanation
| Question 34 The time complexity to multiply two polynomials of degree n using Fast Fourier transform method is: |
| A – θ(n lg n) |
| B – θ(n2) |
| C – θ(n) |
| D – θ(lg lg n ) |
Show Answer With Best Explanation
| Question 35 Consider the following learning algorithms: (a) Logistic regression (b) Back propagation (c) Linear repression Which of the following option represents classification algorithms? |
| A – (a) and (b) only |
| B – (a) and (c) only |
| C – (b) and (c) only |
| D – (a), (b) and (c) |
Show Answer With Best Explanation
| Question 36 The following multi threaded algorithm computes transpose of a matrix in parallel: p Trans (X, Y, N) if N = 1 then Y[1, 1] ← X[1, 1] else partition X into four (N/2) × (N/2) submatrices X11, X12, X21, X22 partition Y into four (N/2) × (N/2) submatrices X11, X12, X21, X22 spawn p Trans (X11, Y11, N/2) spawn p Trans (X12, Y12, N/2) spawn p Trans (X21, Y21, N/2) spawn p Trans (X22, Y22, N/2) What is the asymptotic parallelism of the algorithm? |
A – 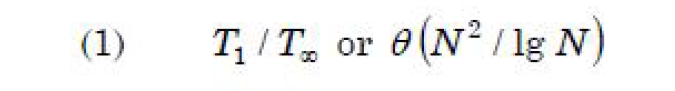 |
B – 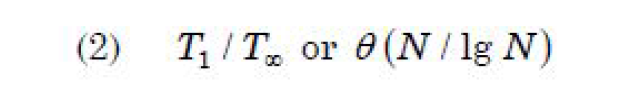 |
C – 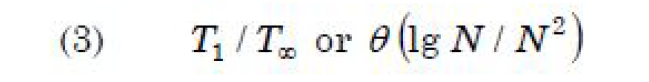 |
D – 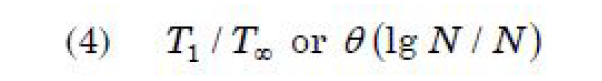 |
Show Answer With Best Explanation
| Question 37 Two concurrent executing transactions T1 and T2 are allowed to update same stock item say ‘A’ in an uncontrolled manner. In such a scenario, following problems may occur: (a) Dirty read problem (b) Lost update problem (c) Transaction failure (d) Inconsistent database state Which of the following option is correct if database system has no concurrency module and allow concurrent execution of above two transactions? |
| A – (a), (b) and (c) only |
| B – (c) and (d) only |
| C – (a) and (b) only |
| D – (a), (b) and (d) only |
Show Answer With Best Explanation
| Question 38 Which of the following statements are true regarding C++? (a) Overloading gives the capacity to an existing operator to operate on other data types. (b) Inheritance in object oriented programming provides support to reusability. (c) When object of a derived class is defined, first the constructor of derived class in executed then constructor of a base class is executed. (d) Overloading is a type of polymorphism. Choose the correct option from those given below: |
| A – (a) and (b) only |
| B – (a), (b) and (c) only |
| C – (a), (b) and (d) only |
| D – (b), (c) and (d) only |
Show Answer With Best Explanation
Question 39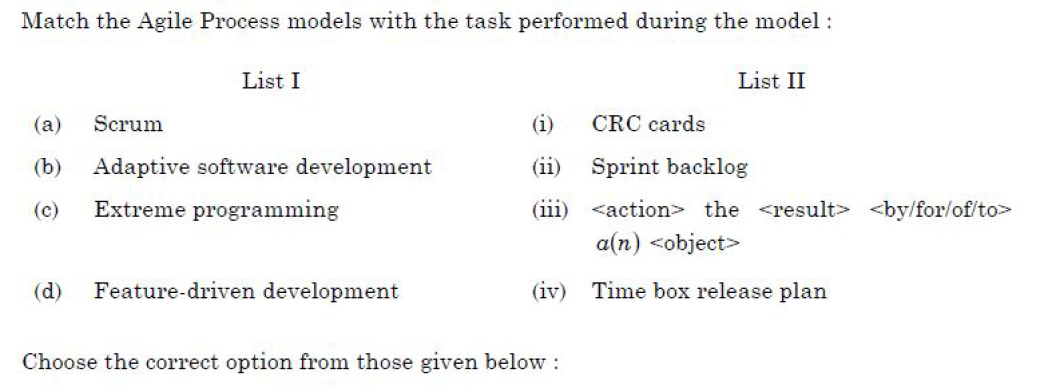 |
| A – (a)-(ii), (b)-(iv), (c)-(i), (d)-(iii) |
| B – (a)-(i), (b)-(iii), (c)-(ii), (d)-(iv) |
| C – (a)-(i), (b)-(iv), (c)-(ii), (d)-(iii) |
| D – (a)-(i), (b)-(iv), (c)-(ii), (d)-(iii) |
Show Answer With Best Explanation
| Question 40 A counting semaphore is initialized to 8. 3 wait() operations and 4 signal() operations are applied. Find the current value of semaphore variable |
Show Answer With Best Explanation
| Q41➡ | Computer Graphics Consider the following statement with respect to approaches to fill area on raster systems: (P) To determine the overlap intervals for scan lines that cross the area. (Q) To start from a given interior position and paint outward from this point until we encounter the specified boundary conditions. Select the correct answer from the options given below: |
| i ➥ P only |
| ii ➥ Q only |
| iii ➥ Both P and Q |
| iv ➥ Neither P nor Q |
Show Answer With Best Explanation
| Question 42➡ | Computer Network Piconet is a basic unit of a Bluetooth system consisting of _______ master node and up to ________ active salve nodes. |
| i ➥ one, five |
| ii ➥ one, seven |
| iii ➥ two, eight |
| iv ➥ one, eight |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Bluetooth | Help-Line |
| Question 43 Consider the following: (a) Trapping at local maxima (b) Reaching a plateau (c) Traversal along the ridge. Which of the following option represents shortcomings of the hill climbing algorithm? |
| A – (a) and (b) only |
| B – (a) and (c) only |
| C – (b) and (c) only |
| D – (a), (b) and (c) |
Show Answer With Best Explanation
| Question 44 According to Dempster-Shafer theory for uncertainty management, Where Bel(A) denotes Belief of event A. |
| A – 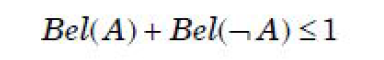 |
B – 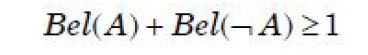 |
C – 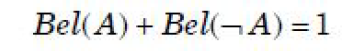 |
D – 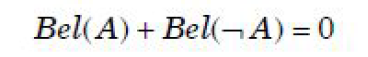 |
Show Answer With Best Explanation
Question 45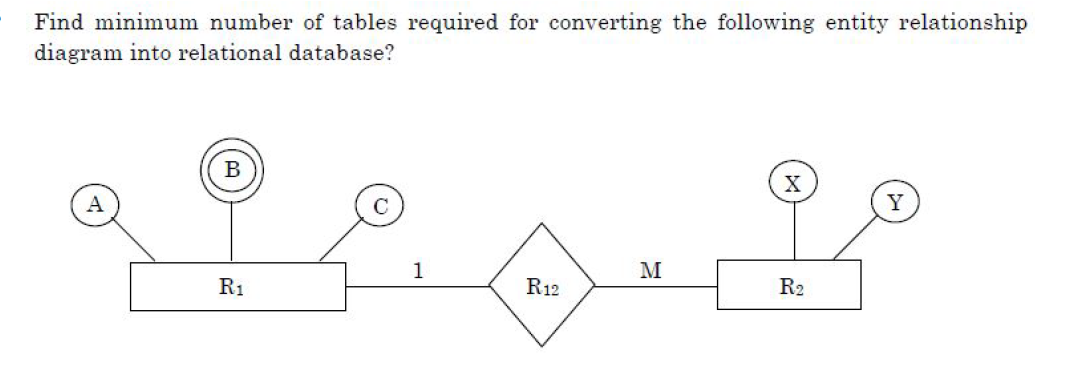 |
| A – 2 |
| B – 4 |
| C – 3 |
| D – 5 |
Show Answer With Best Explanation
| Question 46 Consider the following statements with respect to duality in LPP: (a) The final simplex table giving optimal solution of the primal also contains optimal solution of its dual in itself. (b) If either the primal or the dual problem has a finite optimal solution, then the other problem also has a finite optimal solution. (c) If either problem has an unbounded optimal solution, then the other problem has no feasible solution at all. Which of the statements is (are) correct? |
| A – only (a) and (b) |
| B – only (a) and (c) |
| C – only (b) and (c) |
| D – (a), (b) and (c) |
Show Answer With Best Explanation
| Question 47 The Data Encryption Standard (DES) has a function consists of four steps. Which of the following is correct order of these four steps? |
| A – an expansion permutation, S-boxes, an XOR operation, a straight permutation |
| B – an expansion permutation, an XOR operation, S-boxes, a straight permutation |
| C – an straight permutation, S-boxes, an XOR operation, an expansion permutation |
| D – a straight permutation, an XOR operation, S-boxes, an expansion permutation |
Show Answer With Best Explanation
| Question 48 Give asymptotic upper and lower bound for T(n) given below. Assume T(n) is constant for n≤2. T(n)= 4T(√n)+lg^2 n |
| A – T(n)= θ(lg*(lg^2 n)lg n) |
| B – T(n)= θ(lg^2n lg n) |
| C – T(n)= θ(lg^2 n (lg lg n)) |
| D – T(n)= θ(lg (lg n)lg n) |
Show Answer With Best Explanation
| Question 49➡ | Computer Network The full form of ICANN is |
| i ➥ Internet Corporation for Assigned Names and Numbers |
| ii ➥ Internet Corporation for Assigned Names and Names |
| iii ➥ Institute of Corporation for Assigned Names and Numbers |
| iv ➥ Internet connection for Assigned Names and Numbers |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | ICANN | Help-Line |
| Question 50➡ | Computer Network Consider a subnet with 720 routers. If a three-level hierarchy is chosen, with eight clusters, each containing 9 regions of 10 routers, then the total number of entries in hierarchical table of each router is |
| i ➥ 25 |
| ii ➥ 27 |
| iii ➥ 53 |
| iv ➥ 72 |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Routing | Help-Line |
| Question 51 In a system for a restaurant, the main scenario for placing order is given below: (a) Customer reads menu (b) Customer places an order (c) Order is sent to kitchen for preparation (d) Ordered items are served (e) Customer requests for a bill for the order (f) Bill is prepared for this order (g) Customer is given the bill (h) Customer pays the bill A sequence diagram for the scenario will have at least how many objects among whom the messages will be exchanged. |
| A – 3 |
| B – 4 |
| C – 5 |
| D – 6 |
Show Answer With Best Explanation
| Question 52 Given two tables R1(x, y) and R2(y, z) with 50 and 30 number of tuples respectively. Find maximum number of tuples in the output of natural join between tables R1 and R2 i.e. R1 * R2? (*. Natural Join) |
| A – 30 |
| B – 20 |
| C – 50 |
| D – 1500 |
Show Answer With Best Explanation
| Question 53 Consider the following statements : (a) Windows Azure is a cloud-based operating system. (b) Google App Engine is an integrated set of online services for consumers to communicate and share with others. (c) Amazon Cloud Front is a web service for content delivery. Which of the statements is (are) correct? |
| A – Only (a) and (b) |
| B – Only (a) and (c) |
| C – Only (b) and (c) |
| D – (a), (b) and (c) |
Show Answer With Best Explanation
| Question 54 Let A = (001, 0011, 11, 101} and B = (01, 111, 111, 010}. Similarly, let C = {00, 001, 1000} and D = {0, 11,011}. Which of the following pairs have a post-correspondence solution? |
| A – Only pair (A, B) |
| B – Only pair (C, D) |
| C – Both (A, B) and (C, D) |
| D – Neither (A, B) nor (C, D) |
Show Answer With Best Explanation
| Question 55 An ______chart is a project schedule representation that presents project plan as a directed graph. The critical path is the______sequence of _______tasks and it defines project ______ |
| A – Activity, Shortest, Independent, Cost |
| B – Activity, Longest, Dependent, Duration |
| C – Activity, Longest, Independent, Duration |
| D – Activity, Shortest, Dependent, Duration |
Show Answer With Best Explanation
| Question 56 Consider a weighted directed graph. The current shortest distance from source S to node x is represented by d[x]. Let d[u] = 15, w[u, v] = 12. What is the updated value of d[u] based on current information |
| A – 29 |
| B – 27 |
| C – 25 |
| D – 17 |
Show Answer With Best Explanation
| Question 57 Let a2e mod n = (ae)2 mod n and a2e+1 mod n = a (ac)2 mod n. For a = 7, b = 17 and n = 561, what is the value of ab(mod n)? |
| A – 160 |
| B – 166 |
| C – 157 |
| D – 67 |
Show Answer With Best Explanation
| Question 58➡ | Computer Network Consider the following statements : (a) Fiber optic cable is much lighter than copper cable. (b) Fiber optic cable is not affected by power surges or electromagnetic interference. (c) Optical transmission is inherently bidirectional. Which of the statements is (are) correct? |
| i ➥ Only (a) and (b) |
| ii ➥ Only (a) and (c) |
| iii ➥ Only (b) and (c) |
| iv ➥ (a), (b) and (c) |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Transmission Media | Help-Line |
| Question 59 Which of the following class of IP address has the last address as 223.255.255.255? |
| A – Class A |
| B – Class B |
| C – Class C |
| D – Class D |
Show Answer With Best Explanation
| Question 60 A computer uses a memory unit of 512 K words of 32 bits each. A binary instruction code is stored in one word of the memory. The instruction has four parts: an addressing mode field to specify one of the two-addressing mode (direct and indirect), an operation code, a register code part to specify one of the 256 registers and an address part. How many bits are there in addressing mode part, opcode part, register code part and the address part? |
| A – 1, 3, 9, 19 |
| B – 1, 4, 9, 18 |
| C – 1, 4, 8, 19 |
| D – 1, 8, 8, 20 |
Show Answer With Best Explanation
Question 61 |
| A – G1 and G3 are equivalent |
| B – G2 and G3 are equivalent |
| C – G2 and G4 are equivalent |
| D – G3 and G4 are equivalent |
Show Answer With Best Explanation
Question 62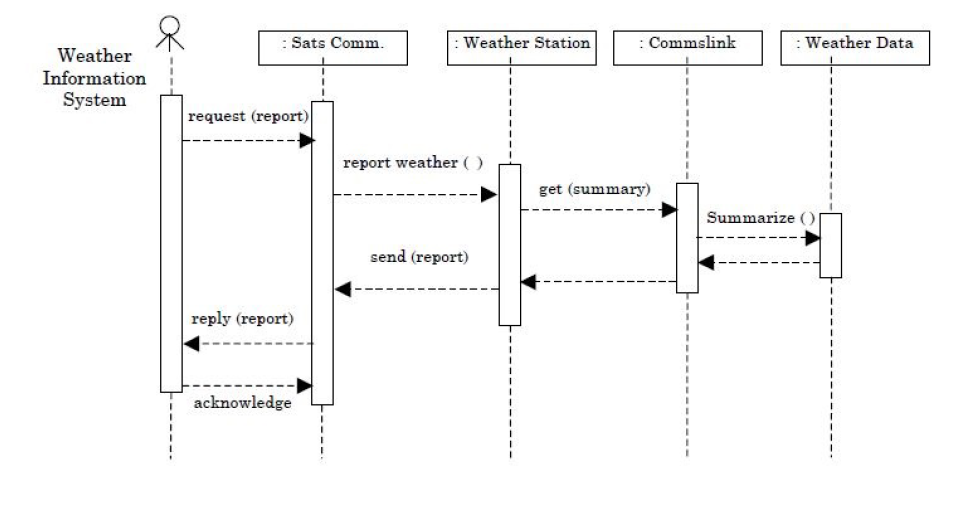 The sequence diagram given in Figure 1 for the Weather Information System takes place when an external system requests the summarized data from the weather station. The increasing order of lifeline for the objects in the system are: |
| A – Sat comms → Weather station → Commslink → Weather data |
| B – Sat comms → Comms link → Weather station → Weather data |
| C – Weather data → Comms link → Weather station → Sat Comms |
| D – Weather data → Weather station → Comms link → Sat Comms |
Show Answer With Best Explanation
| Question 63 Consider the following language families : L1 = The context – free language L2 = The context – sensitive language L3 = The recursively enumerable language L4 = The recursive language Which one of the following options is correct? |
| A – L1 ⊆ L2 ⊆ L3 ⊆ L4 |
| B – L2 ⊆ L1 ⊆ L3 ⊆ L4 |
| C – L1 ⊆ L2 ⊆ L4 ⊆ L3 |
| D – L2 ⊆ L1 ⊆ L4 ⊆ L3 |
Show Answer With Best Explanation
| Question 64 When using Dijkstra’s algorithm to find shortest path in a graph, which of the following statement is not true? |
| A – It can find shortest path within the same graph data structure |
| B – Every time a new node is visited, we choose the node with smallest known distance/cost (weight) to visit first |
| C – Shortest path always passes through least number of vertices |
| D – The graph needs to have a non-negative weight on every edge |
Show Answer With Best Explanation
Question 65 |
| A – 24 |
| B – 576 |
| C – 14.4 |
| D – 49.2 |
Show Answer With Best Explanation
Question 66 |
| A – (a)-(ii), (b)-(iii), (c)-(iv), (d)-(i) |
| B – (a)-(i), (b)-(ii), (c)-(iii), (d)-(iv) |
| C – (a)-(ii), (b)-(i), (c)-(iv), (d)-(iii) |
| D – (a)-(i), (b)-(ii), (c)-(iv), (d)-(iii) |
Show Answer With Best Explanation
| Question 67 Let P be the set of all people. Let R be a binary relation on P such that (a, b) is in R if a is a brother of b. Is R symmetric, transitive, an equivalence relation, a partial order relation? |
| A – NO.NO.NO.NO |
| B – NO.NO.YES.NO |
| C – NO.YES.NO.NO |
| D – NO.YES.YES.NO |
Show Answer With Best Explanation
| Question 68 Consider the language L={n>2} on Σ={a,b}. Which ch one of the following generates the language L? |
| A – S →aA |a,A → aAb |b |
| B – S → aaA |λ, A → aAb|λ |
| C – S → aaaA |a, A → aAb|λ |
| D – S → aaaA , A → aAb|λ |
Show Answer With Best Explanation
| Question 69 The order of schema ?10?101? and ???0??1 are and ________ respectively. |
| A – 5.3 |
| B – 5.2 |
| C – 7.5 |
| D – 8.7 |
Show Answer With Best Explanation
| Question 70➡ | Computer Network Match List I with List II 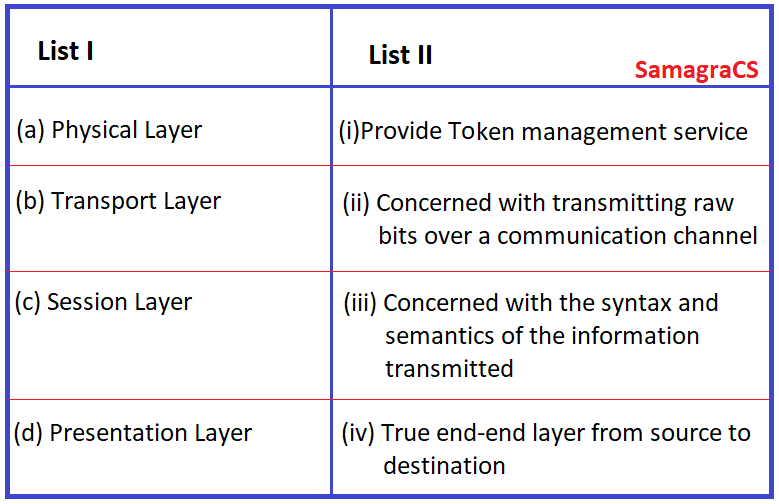 |
| i ➥ (a).(ii), (b).(iv), (c).(iii). (d).(i) |
| ii ➥ (a).(iv). (b).(iii). (c).(ii). (d).(i) |
| iii ➥ (a).(ii), (b).(iv), (c).(i), (d).(iii) |
| iv ➥ (a).(iv), (b).(ii), (c).(i), (d).(iii) |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | TCP/IP Model | Help-Line |
Question 71 |
| A – (a)-(iii), (b)-(i), (c)-(iv), (d)-(ii) |
| B – (a)-(i), (b)-(ii), (c)-(iii), (d)-(iv) |
| C – (a)-(iv), (b)-(ii), (c)-(iii), (d)-(i) |
| D – (a)-(iv), (b)-(iii), (c)-(ii), (d)-(i) |
Show Answer With Best Explanation
| Q72➡ | Computer Graphics A rectangle is bounded by the lines x = 0; y=0, x = 5 and y = 3. The line segment joining (–1, 0) and (4, 5), if clipped against this window will connect the points _____. |
| i ➥ (0, 1) and (3, 3) |
| ii ➥ (0, 1) and (2, 3) |
| iii ➥ (0, 1) and (4, 5) |
| iv ➥ (0, 1) and (3, 5) |
Show Answer With Best Explanation
Question 73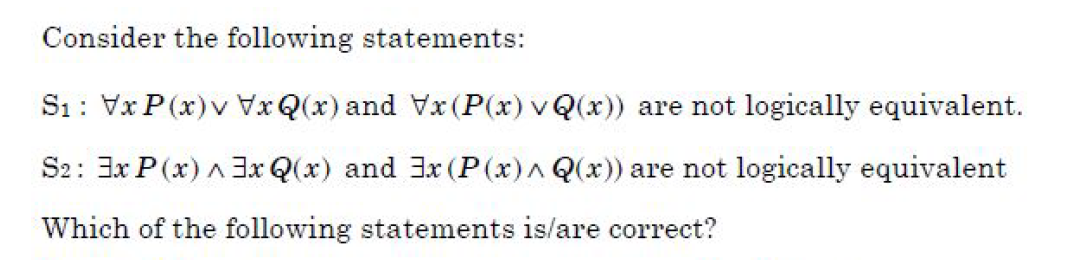 |
| A – only S1 and S2 |
| B – only S1 and S3 |
| C – only S2 and S3 |
| D – S1, S2 and S3 |
Show Answer With Best Explanation
| Question 74 What are the greatest lower bound (GLB) and the least upper bound (LUB) of the sets A = {3, 9, 12} and B = {1, 2, 4, 5, 10} if they exist in poset (z*,/)? |
| A – A (GLB – 3, LUB – 36); B (GLB – 1, LUB – 20) |
| B – A(GLB – 3, LUB – 12); B (GLB -1, LUB – 10) |
| C – A (GLB -1, LUB – 36); B (GLB – 2, LUB – 20) |
| D – A (GLB – 1, LUB – 12); B (GLB – 2, LUB – 10) |
Show Answer With Best Explanation
Question 75 |
| A – (a)-(iv), (b)-(iii), (c)-(ii), (d)-(i) |
| B – (a)-(iv), (b).(iii), (c)-(i), (d)-(ii) |
| C – (a)-(iii), (b)-(iv), (c)-(i), (d)-(i) |
| D – (a)-(iii), (b)-(iv), (c)-(ii), (d)-(i) |
Show Answer With Best Explanation
| Question 76 A clique in an undirected graph G = (V, E) is a subset V’ ⊆ V of vertices, such that |
| A – If (u, v) ∈ E then u ∈ V’ and v ∈ V’ |
| B – If (u, v) ∈ E then u ∈ V’ or v ∈ V’ |
| C – Each pair of vertices in V’ is connected by an edge |
| D – All pairs of vertices in V’ are not connected by an edge |
Show Answer With Best Explanation
Question 77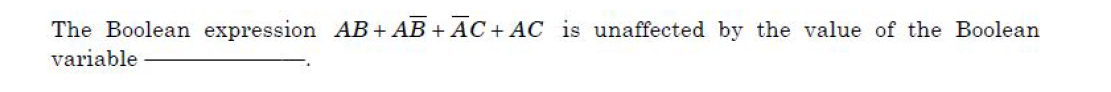 |
| A – A |
| B – B |
| C – C |
| D – A, B and C |
Show Answer With Best Explanation
Question 78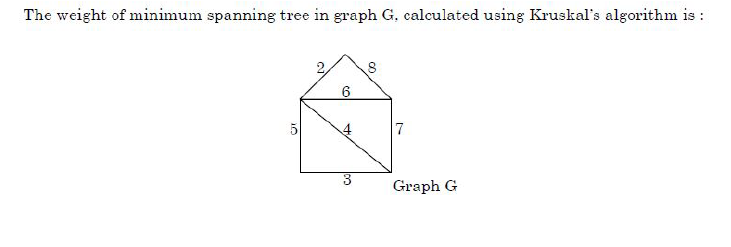 |
| A – 14 |
| B – 15 |
| C – 17 |
| D – 18 |
Show Answer With Best Explanation
| Question 79 Which of the following CPU scheduling algorithms is/are supported by LINUX operating system? |
| A – Non-preemptive priority scheduling |
| B – Preemptive priority scheduling and time sharing CPU scheduling |
| C – Time sharing scheduling only |
| D – Priority scheduling only |
Show Answer With Best Explanation
| Question 80 What is the output of following C program? #include main( ) { int i, j, x = 0; for (i = 0; i <5; ++i) for (j=0;j <i ;++j) { x + = (i + j – 1); break; } printf (“%d”,x) ; } |
| A – 6 |
| B – 5 |
| C – 4 |
| D – 3 |
Show Answer With Best Explanation
| Question 81 Which of the following methods are used to pass any number of parameters to the operating system through system calls? |
| A – Registers |
| B – Block or table in main memory |
| C – Stack |
| D – Block in main memory and stack |
Show Answer With Best Explanation
| Question 82 The following program is stored in the memory unit of the basic computer. Give the content of accumulator register in hexadecimal after the execution of the program. 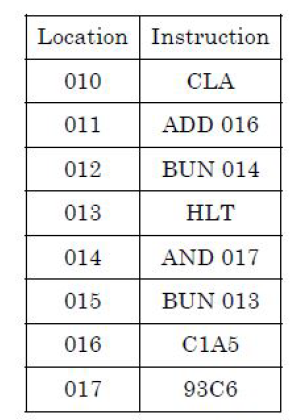 |
| A – A1B4 |
| B – 81B4 |
| C – A184 |
| D – 8184 |
Show Answer With Best Explanation
| Question 83 Java Virtual Machine (JVM) is used to execute architectural neutral byte code. Which of the following is needed by the JVM for execution of Java Code? |
| A – Class loader only |
| B – Class loader and Java Interpreter |
| C – Class loader, Java Interpreter and API |
| D – Java Interpreter only |
Show Answer With Best Explanation
Question 84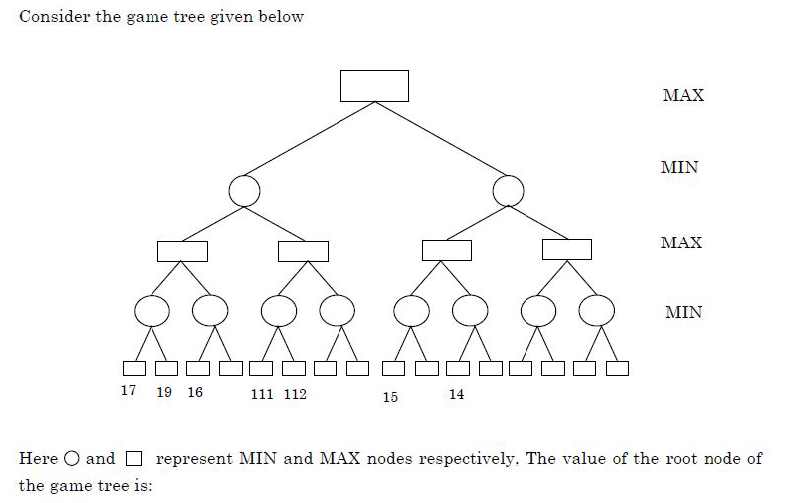 |
| A – 14 |
| B – 17 |
| C – 111 |
| D – 112 |
Show Answer With Best Explanation
| Question 85 A basic feasible solution of an mXn Transportation-Problem is said to be non-degenerate, if basic feasible solution contains exactly____number of individual allocation in ___positions |
| A – m+n+1, independent |
| B – m+n-1, independent |
| C – m+n-1, appropriate |
| D – m-n+1, independent |
Show Answer With Best Explanation
| Question 86 Given following equation: (142)b + (112)b-2 = (75)8. Find base b. |
| A – 3 |
| B – 6 |
| C – 7 |
| D – 5 |
Show Ans5wer With Best Explanation
| Question 87 Consider the following models: M1: Mamdani model M2: Takagi-Sugeno-Kang model M3: Kosko’s additive model(SAM) Which of the following option contains example of additive rule model? |
| A – Only M1 and M2 |
| B – Only M2 and M3 |
| C – Only M1 and M3 |
| D – M1, M2 and M3 |
Show Answer With Best Explanation
| Question 88 A fuzzy conjunction operators, t(x,y), and a fuzzy disjunction operator, s(x,y) from a pair if they satisfy: t(x,y)=1-s(1-x, 1-y). If t(x,y)= xy/ (x+y-xy) then s(x,y) is given by |
| A – (x+y)/1-xy |
| B – (x+y-2xy)/1-xy |
| C – (x+y-xy)/1-xy |
| D – (x+y-xy)/1+xy |
Show Answer With Best Explanation
| Question 89 How many reflexive relations are there on a set with 4 elements? |
| A – 24 |
| B – 212 |
| C – 42 |
| D – 2 |
Show Answer With Best Explanation
| Q90➡ | Computer Graphics Which of the following algorithms is not used for line clipping? |
| i ➥ Cohen-Sutherland algorithm |
| ii ➥ Southerland-Hodgeman algorithm |
| iii ➥ Liang-barsky algorithm |
| iv ➥ Nicholl-Lee-Nicholl algorithm |
Show Answer With Best Explanation
| Question 91 A flow graph F with entry node (1) and exit node (11) is shown below: 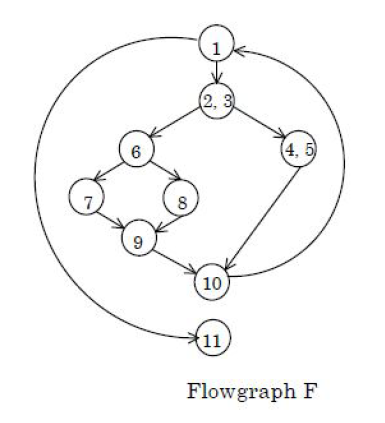 How many predicate nodes are there and what are their names |
| A – Three: (1, (2,3), 6) |
| B – Three: (1, 4, 6) |
| C – Four: ((2,3), 6, 10, 11) |
| D – Four: ((2,3), 6, 9, 10) |
Show Answer With Best Explanation
| Question 92 A flow graph F with entry node (1) and exit node (11) is shown below:  How many regions are there in flow graph F |
| A – 2 |
| B – 3 |
| C – 4 |
| D – 5 |
Show Answer With Best Explanation
| Question 93 A flow graph F with entry node (1) and exit node (11) is shown below:  What is the cyclomatic complexity of flowgraph F |
| A – 2 |
| B – 3 |
| C – 4 |
| D – 5 |
Show Answer With Best Explanation
| Question 94 A flow graph F with entry node (1) and exit node (11) is shown below:  How many nodes are there in the longest independent path? |
| A – 6 |
| B – 7 |
| C – 8 |
| D – 9 |
Show Answer With Best Explanation
| Question 95 A flow graph F with entry node (1) and exit node (11) is shown below:  How many nodes are there in flow graph F? |
| A – 9 |
| B – 10 |
| C – 11 |
| D – 12 |
Show Answer With Best Explanation
| Question 96 Comprehension: Answer question (96-100) based on the problem statement given below: An organization needs to maintain database having five attributes A, B, C, D, E. These attributes are functionally dependent on each other for which functionally dependency set F is given as : F: {A→ BC, D → E, BC → D, A →D}. Consider a universal relation R(A, B, C, D, E) with functional dependency set F. Also all attributes are simple and take atomic values only. Ques -> Minimal cover F’ of functional dependency set F is |
| A – F’ = {A → B, A → C, BC → D, D →E} |
| B – F’ = {A → BC, B → D, D → E} |
| C – F’ = {A → B, A → C, A → D, D → E} |
| D – F’ = {A → B, A → C, B → D, C → D.D → E} |
Show Answer With Best Explanation
| Question 97 Comprehension: Answer question (96-100) based on the problem statement given below: An organization needs to maintain database having five attributes A, B, C, D, E. These attributes are functionally dependent on each other for which functionally dependency set F is given as : F: {A→ BC, D → E, BC → D, A →D}. Consider a universal relation R(A, B, C, D, E) with functional dependency set F. Also all attributes are simple and take atomic values only. Assume that given table R is decomposed in two tables 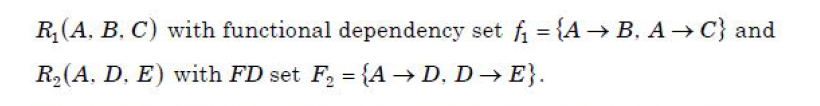 Which of the following option is true w.r.t. given decomposition? |
| A – Dependency preservation property is followed |
| B – R1 and R2 are both in 2 NF |
| C – R2 is in 2 NF and R3 is in 3 NF |
| D – R1 is in 3 NF and R2 is in 2 NF |
Show Answer With Best Explanation
| Question 98 Comprehension: Answer question (96-100) based on the problem statement given below: An organization needs to maintain database having five attributes A, B, C, D, E. These attributes are functionally dependent on each other for which functionally dependency set F is given as : F: {A→ BC, D → E, BC → D, A →D}. Consider a universal relation R(A, B, C, D, E) with functional dependency set F. Also all attributes are simple and take atomic values only. ✔Identify the redundant functional dependency in F |
| A – BC→D |
| B – D→E |
| C – A→D |
| D – A→BC |
Show Answer With Best Explanation
| Question 99 Comprehension: Answer question (96-100) based on the problem statement given below: An organization needs to maintain database having five attributes A, B, C, D, E. These attributes are functionally dependent on each other for which functionally dependency set F is given as : F: {A→ BC, D → E, BC → D, A →D}. Consider a universal relation R(A, B, C, D, E) with functional dependency set F. Also all attributes are simple and take atomic values only. ✔Identify primary key of table R with functional dependency set F |
| A – AC |
| B – AD |
| C – A |
| D – AB |
Show Answer With Best Explanation
| Question 100 Comprehension: Answer question (96-100) based on the problem statement given below: An organization needs to maintain database having five attributes A, B, C, D, E. These attributes are functionally dependent on each other for which functionally dependency set F is given as : F: {A→ BC, D → E, BC → D, A →D}. Consider a universal relation R(A, B, C, D, E) with functional dependency set F. Also all attributes are simple and take atomic values only. ✔Identify the normal form in which relation R belong to |
| A – 1NF |
| B – 2NF |
| C – 3NF |
| D – BCNF |