UGC-NET December 2020 and June 2021 computer Science and application solutions
| Q1➡ | Data Structure Two balanced binary trees are given with m and n elements, respectively. They can be merged into a balanced binary search tree in time. |
| i ➥ O(m*log n) |
| ii ➥ O(m*log(m+n)) |
| iii ➥ O(m*n) |
| iv ➥ O(m+n) |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | binary trees | Help-Line |
| Q2➡ | Computer Graphics What is the transformation matrix M that transforms a square in the xy-plane defined by (1, 1)T, (-1,1)T,(-1,-1)T and (1,-1)T to a parallelogram whose corresponding vertices are (2, 1)T, (0,-1)T,(-2,-1)T and (0,-1)T? |
i ➥ 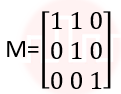 |
ii ➥ 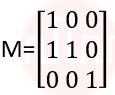 |
iii ➥ 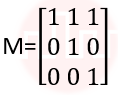 |
iv ➥ 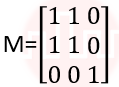 |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q3➡ | Algorithms In the following table, the left column contains the names of standard graph algorithms and the right column contains the time complexities of the algorithms. Here, n and m are number of vertices and edges, respectively. Match each algorithm with its time complexity. 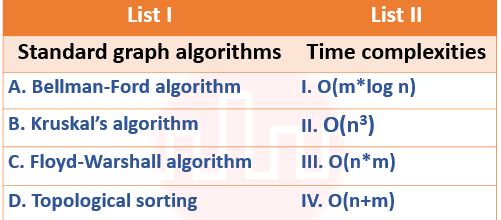 Choose the correct answer from the options given below: Options:- |
| i ➥ A – II, B – I, C – III, D – IV |
| ii ➥ A – II, B – IV, C – III, D – I |
| iii ➥ A – III, B – I, C – II, D – IV |
| iv ➥ A – III, B – IV, C – I, D – II |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q4➡ | Database Management System A transaction may be in one of the following states during its execution life cycle in concurrent execution environment. A. FAILED B. TERMINATED C. PARTIALLY COMMITTED D. COMMITTED E. ACTIVE Given a transaction in active state during its execution, find its next transitioned state from the options given below: |
| i ➥ A only |
| ii ➥ C only |
| iii ➥ D only |
| iv ➥ Either A or C only |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q5➡ | Theory of Computation Which of the following languages are not regular? A. L={ (01)n0k | n > k, k>=0 } B. L={ cnbkan+k | n >= 0, k>=0 } C. L={ 0n1k | n≠k } Choose the correct answer from the options given below: |
| i ➥ A and C only |
| ii ➥ A and B only |
| iii ➥ A, B and C |
| iv ➥ B and C only |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q6➡ | Database Management System Which of the DBMS component ensures that concurrent execution of multiple operations on the database results into a consistent database state? |
| i ➥ Buffer manager |
| ii ➥ File manager |
| iii ➥ Logs |
| iv ➥ Transaction processing system |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q7➡ | Database Management System Given the following STUDENT-COURSE scheme: STUDENT (Rollno, Name, courseno) where Rollno is the primary key of relation STUDENT and courseno is the primary key of relation COURSE. Attribute coursename of COURSE takes unique values only. Which of the following query(ies) will find total number of students enrolled in each course, along with its coursename. A. SELECT coursename, count(*) 'total' from STUDENT natural join COURSE group by coursename; |
| i ➥ A and B only |
| ii ➥ A only |
| iii ➥ B only |
| iv ➥ C only |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q8➡ | Operating System Given memory access time as p nanoseconds and additional q nanoseconds for handling the page fault. What is the effective memory access time if a page fault occurs once for every 100 instructions? |
i ➥ 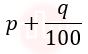 |
ii ➥ 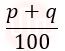 |
| iii ➥ |
iv ➥ 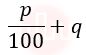 |
| Answer: I ➥ Click below to see detailed Solution |
| [Easy Solution] | Explanation On YouTube | Page Fault | Help-Line |
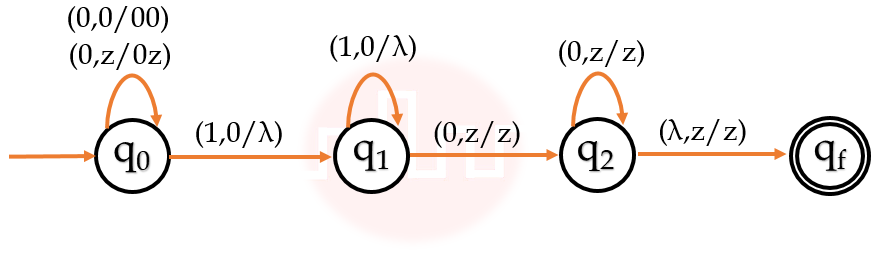
| Q9➡ | Theory of Computation What language is accepted by the pushdown automaton M=({q0, q1, q2}, {a, b}, {a, b, z}, δ, q0, z, {q2}) with δ(q0, a, a) ={ (q0, aa) }; δ(q0, b, a) ={(q0, ba)} δ(q0, a, b) ={ (q0, ab) }; δ(q0, b, b) ={ (q0, bb) } δ(q0, a, z) ={ (q0, az) }; δ(q0, b, z) ={ (q0, bz) } δ(q0, λ, b) ={ (q1, b) }; δ(q0, λ, a) ={ (q1, a) } δ(q1, a, a) ={ (q1, λ) }; δ(q1, b, b) ={ (q1, λ) } δ(q1, λ, z) ={ (q2, z) }? |
| i ➥ L = { w | na(w) <= nb(w), w Є {a, b}+}} |
| ii ➥ L = { w | na(w) = nb(w), w Є {a, b}+}} |
| iii ➥ L = { w | nb(w) <= na(w), w Є {a, b}+}} |
| iv ➥ L= {wwR | w Є {a, b}+} |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q10➡ | Operating System In a file allocation system, the following allocation schemes are used: A. Contiguous B. Indexed C. Linked allocation Which of the allocation scheme(s) given above will not suffer from external fragmentation? Choose the correct answer from the options given below: |
| i ➥ A and B only |
| ii ➥ A only |
| iii ➥ B and C only |
| iv ➥ C only |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q11➡ | Compiler Design Given below are two statements Statement I: LL(1) and LR are examples of Bottom-up parsers. Statement II: Recursive descent parser and SLR are examples of Top-down parsers In light of the above statements, choose the correct answer from the options given below Options:- |
| i ➥ Both Statement I and Statement II are false |
| ii ➥ Both Statement I and Statement II are true |
| iii ➥ Statement I is false but Statement II is true |
| iv ➥ Statement I is true but Statement II is false |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q12➡ | Software Engineering Given below are two statements, one is labelled as Assertion A and the other is labelled as Reason R Assertion A : Software developers do not do exhaustive software testing in practice. Reason R : Even for small inputs, exhaustive testing is too computationally intensive (e.g., takes too long) to run all the tests. In light of the above statements, choose the correct answer from the options given below |
| i ➥ A is false but R is true |
| ii ➥ A is true but R is false |
| iii ➥ Both A and R are true and R is the correct explanation of A |
| iv ➥ Both A and R are true but R is NOT the correct explanation of A |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q13➡ | Discrete Mathematics Let (X,* ) be a semi-group. Furthermore, for every a and b in X, if a ≠ b, then a*b ≠ b*a. Based on the defined semi-group, choose the correct equalities from the options given below: A. For every a in X, a*a = a B. For every a, b in X, a*b *a= a C. For every a, b, c in X, a*b *c= a*c |
| i ➥ A and B only |
| ii ➥ A and C only |
| iii ➥ A, B and C |
| iv ➥ B and C only |
| Answer: III Explanation: Given, (X,* ) be a semi-group. for every a and b in X, if a ≠ b, then a*b ≠ b*a. Concept, Semi Group(X,* ) have 2 properties, which are: 1) Closure Property if a and b in X, then a*b∈X 2) Associative Property if a,b and c in X, then (a*b)*c = a*(b*c) Let’s solve, A) For every a in X, a*a = a Lets assume a*a ≠ a Lets suppose a*a = b, where a ≠ b ⟹ a*(a*a) = a*b ⟹ (a*a)*a = a*b {∵ by associative property, a*(b*c) = (a*b)*c} ⟹ b*a = a*b {∵ we suppose a*a = b} Since it is given, for every a and b in X, if a ≠ b, then a*b ≠ b*a, but here a*b = b*a, which proves that our initial assumption is wrong. Hence, For every a in X, a*a = a (Correct) B) For every a, b in X, a*b *a= a Lets assume a*b*a ≠ a Lets suppose a*b*a = b, where a ≠ b it is given, a*b ≠ b*a, and we already suppose a*b*a = b. Now put b = a*b*a in a*b ≠ b*a ⟹ a*(a*b*a) ≠ (a*b*a)*a ⟹ (a*a)*b*a ≠ a*b*(a*a) {∵ by associative property, a*(b*c) = (a*b)*c} ⟹ a*b*a ≠ a*b*a {∵ it is given in A, a*a = a and we already proved that this is correct} Here, a*b*a ≠ a*b*a but it is actually equal, which proves that our initial assumption is wrong. Hence, For every a, b in X, a*b *a= a (Correct) C) For every a, b, c in X, a*b *c= a*c Lets assume a*b*c ≠ a*c Lets suppose a*b*c = a, and a*c=b where a ≠ b it is given, a*b ≠ b*a, and we already suppose a*b*c = a and a*c=b . Now put a= a*b*c and b = a*c in a*b ≠ b*a ⟹ (a*b*c)*(a*c) ≠ (a*c)*(a*b*c) ⟹ a*b*(c*a*c) ≠ (a*c*a)*b*c {∵ by associative property, a*(b*c) = (a*b)*c} ⟹ a*b*c ≠ a*b*c {∵ it is given in B, a*b *a= a and we already proved that this is correct. Like statement B, we can write c*a*c=c and a*c*a=a } Here, a*b*c ≠ a*b*c but it is actually equal, which proves that our initial assumption is wrong. Hence, For every a, b in X, a*b *a= a (Correct) Therefore, Option(III) is correct. |
| [Easy Solution] | Explanation On YouTube | Discrete Math | Help-Line |
| Q14➡ | Database Management System A company is consuming parts in the manufacturing of other products. Each of the part is either manufactured within the company or purchased from the external suppliers or both. For each part, part_number, part_name is maintained. Attribute batch_number is maintained if the consumed part is manufactured in the company. If part is purchased from external supplier, then supplier name is maintained. Which of the following constraints need to be considered when modelling class/subclass concepts in ERD for the given problem. |
| i ➥ Disjoint constraint only |
| ii ➥ Partial participation and disjoint constraints |
| iii ➥ Partial participation |
| iv ➥ Total specialization and overlapping constraints |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q15➡ | Software Engineering Given below are two statements Statement I: Cleanroom software process model incorporates the statistical quality certification of code increments as they accumulate into a system. Statement II: Cleanroom software engineering follows the classic analysis, design, code, test, and debug cycle to software development and focussing on defect removal rather than defect prevention. In light of the above statements, choose the correct answer from the options given below Options:- |
| i ➥ Both Statement I and Statement II are false |
| ii ➥ Both Statement I and Statement II are true |
| iii ➥ Statement I is false but Statement II is true |
| iv ➥ Statement I is true but Statement II is false |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Cleanroom | Help-Line |
| Q16➡ | Artificial Intelligence Which agent deals with the happy and unhappy state? |
| i ➥ Goal-based Agent |
| ii ➥ Learning Agent |
| iii ➥ Model-based agent |
| iv ➥ Utility-based agent |
| Answer: IV Explanation: An agent is anything that can be viewed as perceiving its environment through sensors and sensor acting upon that environment from actuators. All intelligent systems have four basic kinds of agent programs that represent the principles: • Simple reflex agents; • Model-based reflex agents; • Goal-based agents; and • Utility-based agents.   |
| More Discussion | Explanation On YouTube | Utility-based agent | Help-Line |
| Q17➡ | Discrete Mathematics How many ways are there to assign 5 different jobs to 4 different employees if every employee is assigned at least 1 job? |
| i ➥ 1024 |
| ii ➥ 20 |
| iii ➥ 240 |
| iv ➥ 625 |
| Answer: III Explanation: Given, 5 different jobs and 4 different employees every employee is assigned at least 1 job Let’s solve, Lets take 4 employees as A,B,C,D 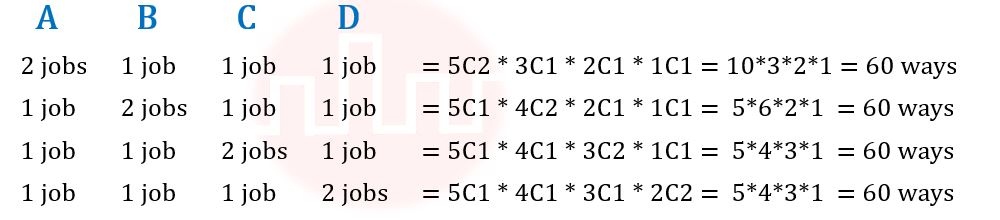 Total ways = 60 + 60 + 60 + 60 = 240 ways Therefore, Option(III) is correct. |
| [Easy Solution] | Explanation On YouTube | Discrete Math | Help-Line |
| Q18➡ | Software Engineering The V components in MVC are responsible for: |
| i ➥ Business logic and domain objects. |
| ii ➥ Security of the system. |
| iii ➥ Translating between user interface actions/events and operations on the domain objects. |
| iv ➥ User interface. |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q19➡ | Computer Graphics Given below are two statements Statement I: The maximum number of sides that a triangle might have when clipped to a rectangular viewport is 6. Statement II: In 3D graphics, the perspective transformation is nonlinear in z. In light of the above statements, choose the correct answer from the options given below Options:- |
| i ➥ Both Statement I and Statement II are false |
| ii ➥ Both Statement I and Statement II are true. |
| iii ➥ Statement I is false but Statement II is true. |
| iv ➥ Statement I is true but Statement II is false. |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q20➡ | Artificial Intelligence Consider the sentence below. There is a country that borders both India and Pakistan. Which of the following logical expressions express the above sentence correctly when the predicate Country(x) represents that x is a country and Borders(x, y) represents that the countries x and y share the border? |
| i ➥ [∃c Country(c)] ⇒ [Border (c, India) ∧ Border (c,Pakistan)] |
| ii ➥ ∃c Border (Country(c), India ∧ Pakistan) |
| iii ➥ ∃c Country(c) ∧ Border (c, India) ∧ Border (c,Pakistan) |
| iv ➥ ∃c Country(c) ⇒ [Border (c, India) ∧ Border (c,Pakistan)] |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Propositional logic | Help-Line |
| Q21➡ | Programming in JAVA Consider the following recursive function F() in Java that takes an integer value and returns a string value: 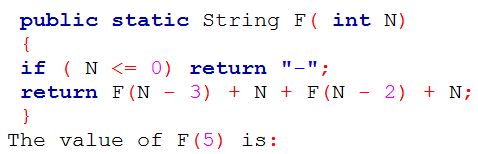 |
| i ➥ -1-145-2-245 |
| ii ➥ -2-25-1-3-135 |
| iii ➥ -2-25-3-1-135 |
| iv ➥ -2-25-3-135 |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q22➡ | Software Engineering If every requirement stated in the Software Requirement Specification (SRS) has only one interpretation, then SRS is said to be |
| i ➥ consistent |
| ii ➥ correct |
| iii ➥ unambiguous |
| iv ➥ verifiable |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | SRS | Help-Line |
| Q23➡ | Computer Graphics Suppose you have eight ‘black and white’ images taken with a 1-megapixel camera and one ‘8-color’ image taken by an 8-megapixel camera. How much hard disk space in total do you need to store these images on your computer? |
| i ➥ 1 GB |
| ii ➥ 3 GB |
| iii ➥ 3 MB |
| iv ➥ 4 MB |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q24➡ | Database Management System Given a fixed-length record file that is ordered on the key field. The file needs B disk blocks to store R number of records. Find the average access time needed to access any record of the given file using binary search. |
| i ➥ B/2 |
| ii ➥ log2 B |
| iii ➥ B+R |
| iv ➥ B |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q25➡ | Software Engineering In the context of Software Configuration Management (SCM), what kind of files should be committed to your source control repository? A. Code files B. Documentation files C. Output files D. Automatically generated files that are required for your system to be used. Choose the correct answer from the options given below: |
| i ➥ A and B only |
| ii ➥ B and C only |
| iii ➥ C and D only |
| iv ➥ D and A only |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q26➡ | Digital Logic Design The Octal equivalent of hexadecimal (D.C)16 is: |
| i ➥ (15.3)8 |
| ii ➥ (15.6)8 |
| iii ➥ (61.3)8 |
| iv ➥ (61.6)8 |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q27➡ | Artificial Intelligence Which among the following statement(s) is(are) FALSE? A. Greedy best-first search is not optimal but is often efficient. B. A* is complete and optimal provided h(n) is admissible or consistent. C. Recursive best-first search is efficient in terms of time complexity but poor in terms of space complexity. D. h(n) = 0 is an admissible heuristic for the 8-puzzle. |
| i ➥ A and D only |
| ii ➥ A only |
| iii ➥ C and D only |
| iv ➥ C only |
| Answer – IV Explanation:  So correct option is (IV). |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q28➡ | Database Management System The order of a leaf node in a B+ tree is the maximum number of (value, data record pointer) pairs it can hold. Given that the block size is 1K bytes, data record pointer is 7 bytes long, the value field is 9 bytes long and a block pointer is 6 bytes long, what is the order of the leaf node? |
| i ➥ 63 |
| ii ➥ 64 |
| iii ➥ 67 |
| iv ➥ 68 |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q29➡ | Computer Graphics Suppose a Bezier curve P(t) is defined by the Following four control points in the xy-plane: P0=(-2, 0); P1=(-2,4);P2=(2,4); and P3=(2,0). Then which of the following statement are correct ? A. Bezier curve P(t) has degree 3. B. B. bezier curve P(t) may extend outside the convex full of its control points. Choose the correct answer from the options below: |
| i ➥ A and B only |
| ii ➥ A and C only |
| iii ➥ A, B, and C |
| iv ➥ B and C only |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q30➡ | Programming in C What does the following function f() in ‘C’ return? int f(unsigned int N) { unsigned int counter = 0; while(N > 0) { counter += N & 1; N = N >> 1; } return counter == 1;} |
| i ➥ 1 if N is a power of 2, otherwise 0 |
| ii ➥ 1 if N is odd, otherwise 0 |
| iii ➥ 1 if the binary representation of N has any 1’s, otherwise 0 |
| iv ➥ 1 if the binary representation of N is all 1’s, otherwise 0 |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q31➡ | Computer Architecture Given below are three statements related to interrupt handling mechanism A. Interrupt handler routine is not stored at a fixed address in the memory. B. CPU hardware has a dedicated wire called the interrupt request line used for handling interrupts C. Interrupt vector contains the memory addresses for speciaized interrupt handlers. In the context of above statements, choose the correct answer from the options given below: Options:- |
| i ➥ A is TRUE only |
| ii ➥ Both A and B are TRUE only |
| iii ➥ Both A, C are TRUE only |
| iv ➥ Both B and C are TRUE only |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q32➡ | Theory of Computation L1 = { 0n1n0m | n>=1, m>=1 } L2 = { 0n1m0m | n>=1, m>=1 } L3 = { 0n1n0n | n>=1} Which of the following are correct statements? A. L3 =L1 ∩ L2 B. L1 and L2 are context free languages but L3 is not a context free language C. L1 and L2 are not context free languages but L3 is a context free language D. L1 is a subset of L3 Choose the correct answer from the options given below: |
| i ➥ A and C only |
| ii ➥ A and D only |
| iii ➥ A only |
| iv ➥ A and B only |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q33➡ | Linear Programming Problem Consider the following linear optimization problem: Maximize Z = 6x+5y Subject to 2x – 3y <= 5 x+3y <= 11 4x + y <=15 and x>=0, y >= 0. The optimal solution of the problem is: |
| i ➥ 15 |
| ii ➥ 25 |
| iii ➥ 31.72 |
| iv ➥ 41.44 |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q34➡ | Discrete Mathematics Which of the following Graphs is (are) planar? 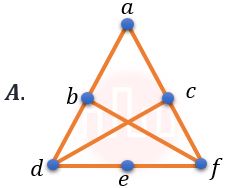 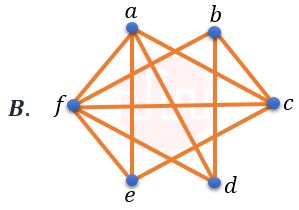 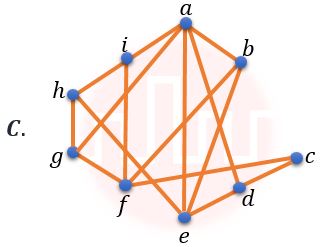 choose the correct answer from the options given below: |
| i ➥ A and B only |
| ii ➥ A only |
| iii ➥ B and C only |
| iv ➥ B only |
| More Discussion | Explanation On YouTube | Page Fault | Help-Line |
| Q35➡ | Programming Match List I with List II 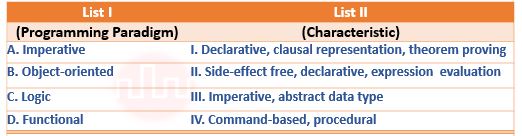 Choose the correct answer from the options given below: |
| i ➥ A – II, B – III, C – I, D – IV |
| ii ➥ A – III, B – IV, C – I, D – II |
| iii ➥ A – IV, B – III, C – I, D – II |
| iv ➥ A – IV, B – III, C – II, D – I |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q36➡ | Software Engineering In software testing, beta testing is the testing performed by ______. |
| i ➥ potential customers at the developer’s location |
| ii ➥ potential customers at their own locations |
| iii ➥ product developers at the customer’s location |
| iv ➥ product developers at their own locations |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q37➡ | Software Engineering A system has 99.99% uptime and has a mean-time-between-failure of 1 day. How fast does the system repair itself in order to reach this availability goal? |
| i ➥ 10 seconds |
| ii ➥ 11 seconds |
| iii ➥ 12 seconds |
| iv ➥ 9 seconds |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q38➡ | Artificial Intelligence Given below are two statements Statement I: Breadth-First Search is optimal when all the step costs are equal whereas uniform-cost se optimal with any step-cost. Statement II: When all the step costs are same uniform-cost search expends more nodes at depth d the Breadth-First Search. In light of the above statements, choose the correct answer from the options given below |
| i ➥ Both Statement I and Statement II are false |
| ii ➥ Both Statement I and Statement II are true |
| iii ➥ Statement I is false but Statement II is true |
| iv ➥ Statement I is true but Statement II is false |
| Answer: II Explanation : 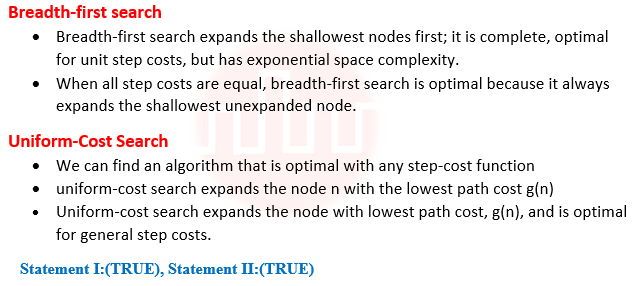 So correct option (II). |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q39➡ | Which of the statements given below is/are correct? It is always important and useful to include an ‘alt’ attribute on ‘img’ tag in HTML because A. users who cannot see the image due to vision impairment can have a textual description of the image (which can be spoken aloud by a screen reader). B. If the image fails to load (slow connection, broken path, etc.) then alt text is displayed instead. C. SEO (Search Engine Optimization) benefits. Choose the correct answer from the options given below: |
| i ➥ A only |
| ii ➥ A, B, and C |
| iii ➥ B and C only |
| iv ➥ C only |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q40➡ | Java Match List I with List II  Choose the correct answer from the options given below: |
| i ➥ A – I, B – III, C – IV, D – II |
| ii ➥ A – II , B – III, C – IV, D – I |
| iii ➥ A – II, B – IV, C – III, D – I |
| iv ➥ A – III, B – II, C – IV, D – I |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q41➡ | Computer Architecture Which of the following statement is true? A. Control memory is part of the hardwired control unit. B. Program control instructions are used to alter the sequential flow of the program. C. The register indirect addressing mode for accessing memory operand is similar to displacement addressing mode. D. CPU utilization is not affected by the introduction of Interrupts. |
| i ➥ A |
| ii ➥ B |
| iii ➥ C |
| iv ➥ D |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q42➡ | Linear Programming Problem A company stores products in a warehouse. Storage bins in this warehouse are specified by their aisle, location in the aisle, and self. There are 50 aisles, 85 horizontal locations in each aisle, and 5 shelves throughout the warehouse. What is the least number of products the company can have so that at least two products must be stored in the same bin? |
| i ➥ 21251 |
| ii ➥ 251 |
| iii ➥ 4251 |
| iv ➥ 426 |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q43➡ | Data Structure A hash function h defined as h(key)=key mod 7, with linear probing, is used to insert the keys 44, 45, 79, 55, 91, 18, 63 into a table indexed from 0 to 6. What will be the location of key 18? |
| i ➥ 3 |
| ii ➥ 4 |
| iii ➥ 5 |
| iv ➥ 6 |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q44➡ | Theory of Computation Any string of terminals that can generated by the following context free grammar (where S is start non-terminal symbol) S→XY X→0X|1X|0 Y→Y0|Y1|0 |
| i ➥ has at least one 1 |
| ii ➥ has no consecutive 0’s or 1’s |
| iii ➥ should end with 0 |
| iv ➥ has at least two 0’s |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q45➡ | Discrete Mathematics which of the following are logically equivalent ? A. ¬p→(q→r)and q→(p∨r) B. (p→q)→r and p→(q→r) C. (p→q)→(r→s) and (p→r)→(q→s) Choose the correct answer from the options below: |
| i ➥ A and B only |
| ii ➥ A and C only |
| iii ➥ A only |
| iv ➥ B and C only |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q46➡ | Theory of Computation Match List I with List II 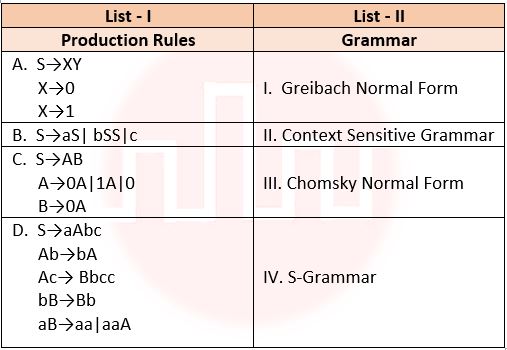 Choose the correct answer from the options below: |
| i ➥ A – III, B -I , C – IV, D – II |
| ii ➥ A – III, B -II , C – I, D – IV |
| iii ➥ A – III, B -IV, C – I, D – II |
| iv ➥ A – IV, B -III , C – I, D – II |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
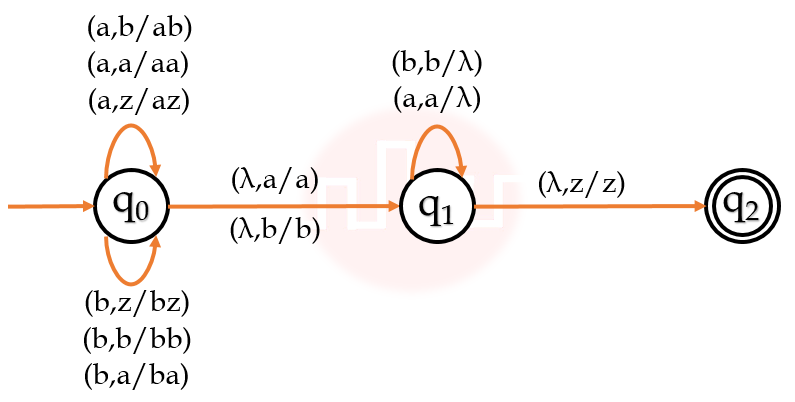
| Q47➡ | Theory of Computation What is the minimum number of states required to the finite automaton equivalent to the transition diagram given below?  |
| i ➥ 3 |
| ii ➥ 4 |
| iii ➥ 5 |
| iv ➥ 6 |
| Answer: III ➥ Click below to see detailed Solution |
| [Easy Solution] | Explanation On YouTube | Page Fault | Help-Line |
| Q48➡ | Discrete Mathematics For which value of n is Wheel graph Wn regular? |
| i ➥ 2 |
| ii ➥ 3 |
| iii ➥ 4 |
| iv ➥ 5 |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q49➡ | Database Management System Given the following STUDENT-COURSE scheme: STUDENT (Rollno, Name, Courseno) COURSE (Courseno, Coursename, Capacity), where Rollno is the primary key of relation STUDENT and Courseno is the primary key of relation COURSE. Attribute Coursename of COURSE takes unique values only. The number of records in COURSE and STUDENT tables are 3 and 5 respectively. Following relational algebra query is executed: R=STUDENT X COURSE Match List I with List II in context to the above problem statement.  Choose the correct answer from the options given below: |
| i ➥ A -I , B -III , C -IV , D – II |
| ii ➥ A -I , B -III , C -IV , D – II |
| iii ➥ A -I , B -III, C -II , D – IV |
| iv ➥ A -III , B -I , C -IV , D – II |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q50➡ | Artificial Intelligence Consider the given tree below. Calculate the value at the root of the tree using alpha-beta pruning algorithm. 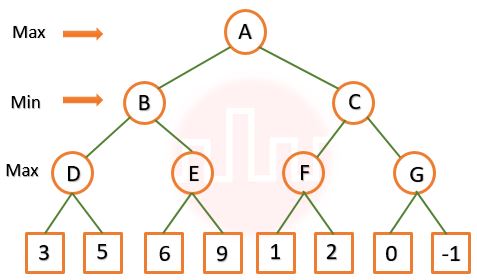 |
| i ➥ 3 |
| ii ➥ 5 |
| iii ➥ 6 |
| iv ➥ 9 |
Show Answer With Best Explanation
| Answer : II Explanation: Alpha Beta Pruning ➨Alpha Beta Pruning is a method which is used to optimizes the Minimax algorithm. ➨Alpha-beta pruning works with depth-first search up to a stated depth limit. Search tree is searched through from left to right. Like in minimax search, ➨in the minimum nodes the minimum is generated from the minimum value of the successor nodes and in the maximum nodes similarly the maximum. ➨At every leaf node the evaluation is calculated. ➨For every maximum node the current largest child value is saved in α. ➨For every minimum node the current smallest child value is saved in β. 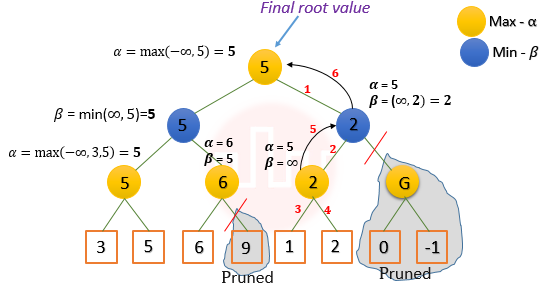 So the correct option is (II). |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q51➡ | Theory of Computation Given below are two statements Statement I: The family of context free languages is closed under homomorphism Statement II: The family of context free languages is closed under reversal. In light of the above statements, choose the correct answer from the options given below |
| i ➥ Both Statement I and Statement II are false |
| ii ➥ Both Statement I and Statement II are true |
| iii ➥ Statement I is false but Statement II is true |
| iv ➥ Statement I is true but Statement II is false |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q52➡ | Data Structure A double-ended queue (dequeue) supports adding and removing items from both the ends of the queue. The operations supported by dequeue are AddFront(adding item to front of the queue), AddRear(adding item to the rear of the queue), RemoveFront(removing item from the front of the queue), and RemoveRear(removing item from the rear of the queue). You are given only stacks to implement this data structure. You can implement only push and pop operations. What’s the time complexity of performing AddFront() and AddRear() assuming m is the size of the stack and n is the number of elements? |
| i ➥ O(1) and O(n) |
| ii ➥ O(m) and O(n) |
| iii ➥ O(n) and O(1) |
| iv ➥ O(n) and O(m) |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q53➡ | Database Management System Given a relation scheme R(x,y,z,w) with functional dependencies set F={x→y, z→w}. All attributes take single and atomic values only. A. Relation R is in First Normal FORM B. Relation R is in Second Normal FORM C. Primary key of R is xz Choose the correct answer from the options given below: |
| i ➥ A and C only |
| ii ➥ B and C only |
| iii ➥ B only |
| iv ➥ C only |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q54➡ | Computer Network In Ethernet when Manchester coding is used, the bit rate is ______. |
| i ➥ Half the baud rate |
| ii ➥ Same as the baud rate |
| iii ➥ Thrice the baud rate |
| iv ➥ twice the baud rate |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q55➡ | Database Management System Which of the following is used to create a database schema? |
| i ➥ DDL |
| ii ➥ DML |
| iii ➥ HTML |
| iv ➥ XML |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q56➡ | Computer Graphics Which of the statements given below are correct? The midpoint (or Bresenham) algorithm for rasterizing lines is optimized relative to DDA algorithm in that A. it avoids round-off operations. B. it is incremental. C. it uses only integer arithmetic. D. all straight lines can be displayed as straight (exact). Choose the correct answer from the options given below: |
| i ➥ A and B only |
| ii ➥ A and C only |
| iii ➥ A, B, and C only |
| iv ➥ A, B, C, and D |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q57➡ | Data Structure A data structure is required for storing a set of integers such that each of the following operations can be done in O(log n) time, where n is the number of elements in the set. ∎ Deletion of the smallest element ∎ Insertion of an element if it is not already present in the set Which of the following data structures can be used for this purpose? |
| i ➥ A balanced binary search tree can be used but not a heap. |
| ii ➥ A heap can be used but not a balanced binary search tree. |
| iii ➥ Both balanced binary search tree and heap can be used. |
| iv ➥ Neither balanced binary search tree nor heap can be used. |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q58➡ | Operating System Match List I with List II 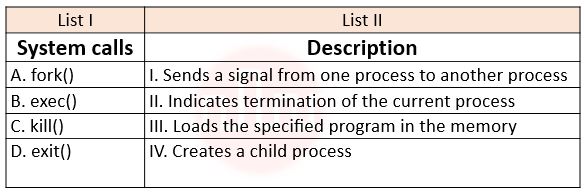 Choose the correct answer from the options given below: |
| i ➥ A – II , B – III , C – IV , D – I |
| ii ➥ A – IV , B – I , C – II , D – III |
| iii ➥ A – IV , B – III , C – I , D – II |
| iv ➥ A – IV , B – III , C – II, D – I |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q59➡ | Theory of Computation Find the regular expression for the language accepted by the automata given below. 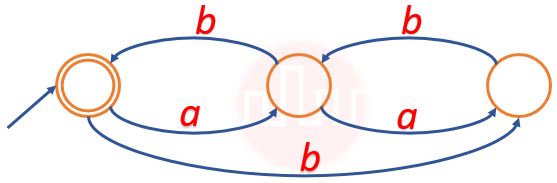 |
| i ➥ (a+b)ab(ab+bb+ aa*(a+b)ab)* |
| ii ➥ (aa*(a+b)ab)* |
| iii ➥ a*(a+b)ab(ab+bb+ aa*(a+b)ab)* |
| iv ➥ a*ab(ab+bb+ aa*(a+b)ab)* |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q60➡ | Discrete Mathematics Let us assume a person climbing the stairs can take one stair or two stairs at a time. How many ways can this person climb a flight of eight stairs? |
| i ➥ 21 |
| ii ➥ 24 |
| iii ➥ 31 |
| iv ➥ 34 |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q61➡ | Data Structure Consider the following graph.  Among the following sequences I. a b e g h f II. a b f e h g III. a b f h g e IV. a f g h b e Which are depth first traversals of the above graph? |
| i ➥ I and IV only |
| ii ➥ I, II, and IV only |
| iii ➥ I, III, and IV only |
| iv ➥ II, III, and IV only |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q62➡ | Software Engineering Match List I with List II 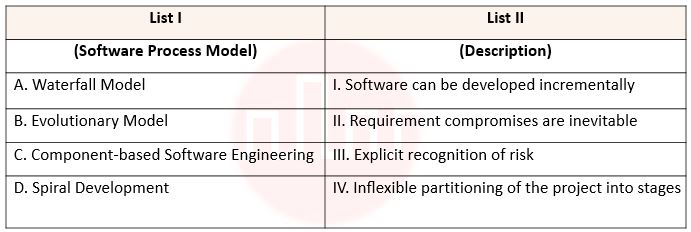 Choose the correct answer from the options given below: |
| i ➥ A – I, B – IV, C – II, D – III |
| ii ➥ A – II, B – III, C – I, D – IV |
| iii ➥ A – IV, B – I, C – II, D – III |
| iv ➥ A – IV, B – I, C – III, D – II |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q63➡ | Software Engineering In software engineering, what kind of notation do formal methods predominantly use? |
| i ➥ computer code |
| ii ➥ diagrammatic |
| iii ➥ mathematical |
| iv ➥ textual |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q64➡ | Data Structure Which of these statements about the floor and ceiling functions are correct Statement I: ⌊2x⌋= ⌊x⌋+ ⌊x+(1/2)⌋ for all real number x Statement I: ⌈x+y⌉= ⌈x⌉+ ⌈y⌉ for all real number x and y |
| i ➥ Both Statement I and Statement II are false |
| ii ➥ Both Statement I and Statement II are true |
| iii ➥ Statement I is false but Statement II is true |
| iv ➥ Statement I is true but Statement II is false |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q65➡ | Database Management System Consider following two statements: Statement I: Relational database schema represents the logical design of the database. Statement II: Current snapshot of a relation only provides the degree of the relation. In the context to the above statements, choose the correct option from the options given below: |
| i ➥ Both Statement I and Statement II are FALSE |
| ii ➥ Both Statement I and Statement II are TRUE |
| iii ➥ Statement I is FALSE but Statement II is TRUE |
| iv ➥ Statement I is TRUE but Statement II is FALSE |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q66➡ | Algorithms Which of the given options provides the increasing order of asymptotic complexity of functions f1, f2, f3 and f4? A. f1(n) = 2n B. f2(n) = n3/2 C. f3(n) = n log n D. f4(n) = nlog n Choose the correct answer from the options given below Options:- |
| i ➥ B, C, A, D |
| ii ➥ B, C, D, A |
| iii ➥ C, B, A, D |
| iv ➥ C, B, D, A |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
UGC-NET December 2020 and June 2021 computer Science and application solutions
| Q67➡ | Database Management System Suppose a B+ tree is used for indexing a database file. Consider the following information: size of the search key field= 10 bytes, block size = 1024 bytes, size of the record pointer= 9 bytes, size of the block pointer= 8 bytes. Let K be the order of internal node and L be the order of leaf node of B+ tree, then (K, L)=_____, |
| i ➥ (34, 31) |
| ii ➥ (50, 52) |
| iii ➥ (57, 53) |
| iv ➥ (60, 64) |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q68➡ | Computer Network Given below are two statements Statement I: Telnet, Ftp, Http are application layer protocol Statement II: The Iridium project was planned to launch 66 low orbit satellites. In light of the above statements, choose the correct answer from the options given below. |
| i ➥ Both Statement I and Statement II are false |
| ii ➥ Both Statement I and Statement II are true |
| iii ➥ Statement I is false but Statement II is true |
| iv ➥ Statement I is true but Statement II is false |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q69➡ | Operating System Consider the following 3 processes with the length of the CPU burst time given in milliseconds: 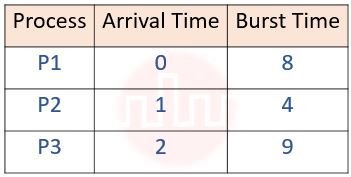 What is the average waiting time for these processes if they are scheduled using preemptive shortest job first scheduling algorithm? |
| i ➥ 2.66 |
| ii ➥ 4.66 |
| iii ➥ 5.5 |
| iv ➥ 6 |
| Answer: II ➥ Click below to see detailed Solution |
| [Easy Solution] | Explanation On YouTube | CPU Scheduling | Help-Line |
| Q70➡ | Data Structure The postfix form of the expression (A + B) * (C * D – E) * F / G is _____ . |
| i ➥ A B + C D * E – * F * G / |
| ii ➥ A B + C D * E – F * * G / |
| iii ➥ A B + C D * E – F G / * * |
| iv ➥ A B + C D E * – * F * G / |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q71➡ | Software Engineering Identify the correct order of the following five levels of Capability Maturity Model (from lower to higher) to measure the maturity of an organization’s software process. A. Defined B. Optimizing C. Initial D. Managed E. Repeatable Choose the correct answer from the options given below |
| i ➥ C, A, E, D, B |
| ii ➥ C, B, D, E, A |
| iii ➥ C, E, A, B, D |
| iv ➥ C, E, A, D, B |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q72➡ | Data Structure Which of the following concepts can be used to identify loops? A. Depth first ordering B. Dominators C. Reducible graphs Choose the correct answer from the options given below: |
| i ➥ A and B only |
| ii ➥ A and C only |
| iii ➥ A, B and C |
| iv ➥ B and C only |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q73➡ | Data Structure Given below are two statements Statement I: In an undirected graph, number of odd degree vertices is even. Statement II: In an undirected graph, sum of degrees of all vertices is even. In light of the above statements, choose the correct answer from the options given below. |
| i ➥ Both Statement I and Statement II are false. |
| ii ➥ Both Statement I and Statement II are true. |
| iii ➥ Statement I is false but Statement II is true. |
| iv ➥ Statement I is true but Statement II is false. |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q74➡ | Digital Logic Design Match List I with List II 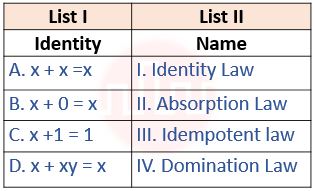 Choose the correct answer from the options given below: |
| i ➥ A – I, B -III , C – IV, D – II |
| ii ➥ A – III, B -I , C – II, D – IV |
| iii ➥ A – III, B -I , C – IV, D – II |
| iv ➥ A – III, B -IV , C – I, D – II |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q75➡ | Computer Network Match List I with List II 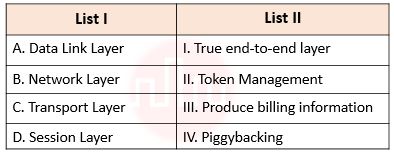 Choose the correct answer from the options given below: |
| i ➥ A – II, B – III, C – I, D – IV |
| ii ➥ A – IV, B – I, C – III, D – II |
| iii ➥ A – IV, B – II, C – I, D – III |
| iv ➥ A – IV, B – III, C – I, D – II |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q76➡ | Operating System Comprehension: Q76 to Q80 Read the following and answer the questions: Consider a machine with 16 GB main memory and 32-bits virtual address space, with page size as 4KB. Frame size and page size is same for the given machine. If a process of size 34KB is to be executed on this machine, then what will be the size of internal fragmentation for this process? |
| i ➥ 1KB |
| ii ➥ 2KB |
| iii ➥ 4KB |
| iv ➥ Zero |
| Answer: II ➥ Click below to see detailed Solution |
| [Easy Solution] | Explanation On YouTube | Memory Management | Help-Line |
| Q77➡ | Operating System Comprehension: Q76 to Q80 Read the following and answer the questions: Consider a machine with 16 GB main memory and 32-bits virtual address space, with page size as 4KB. Frame size and page size is same for the given machine. What is the size of page table for handling the given virtual address space, given that each page table entry is of size 2 bytes? |
| i ➥ 12KB |
| ii ➥ 2KB |
| iii ➥ 2MB |
| iv ➥ 32MB |
| Answer: III ➥ Click below to see detailed Solution |
| [Easy Solution] | Explanation On YouTube | Memory Management | Help-Line |
| Q78➡ | Operating System Comprehension: Q76 to Q80 Read the following and answer the questions: Consider a machine with 16 GB main memory and 32-bits virtual address space, with page size as 4KB. Frame size and page size is same for the given machine. What is the minimum number of bits needed for the physical address? |
| i ➥ 12 |
| ii ➥ 24 |
| iii ➥ 28 |
| iv ➥ 34 |
| Answer: IV ➥ Click below to see detailed Solution |
| [Easy Solution] | Explanation On YouTube | CPU Scheduling | Help-Line |
| Q79➡ | Operating System Comprehension: Q76 to Q80 Read the following and answer the questions: Consider a machine with 16 GB main memory and 32-bits virtual address space, with page size as 4KB. Frame size and page size is same for the given machine. The number of bits reserved for the frame offset is __________ |
| i ➥ 12 |
| ii ➥ 14 |
| iii ➥ 32 |
| iv ➥ 8 |
| Answer: I ➥ Click below to see detailed Easy Solution |
| [Easy Solution] | Explanation On YouTube | CPU Scheduling | Help-Line |
| Q80➡ | Operating System Comprehension: Q76 to Q80 Read the following and answer the questions: Consider a machine with 16 GB main memory and 32-bits virtual address space, with page size as 4KB. Frame size and page size is same for the given machine. Find number of pages required for the given virtual address space. |
| i ➥ 210 |
| ii ➥ 212 |
| iii ➥ 220 |
| iv ➥ 230 |
| Answer: III ➥ Click below to see detailed Easy Solution |
| [Easy Solution] | Explanation On YouTube | CPU Scheduling | Help-Line |
| Q81➡ | Computer Architecture Which of the following is not an example of pseudo-instruction? |
| i ➥ DEC |
| ii ➥ END |
| iii ➥ HLT |
| iv ➥ ORG |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q82➡ | Computer Network Which of the following statement is False? |
| i ➥ Packet switching can lead to reordering unlike circuit switching. |
| ii ➥ Packet switching leads to better utilization of bandwidth resources than circuit switching. |
| iii ➥ Packet switching results in less variation in the delay than circuit switching. |
| iv ➥ Packet switching sender and receiver can use any bit rate, format or framing method unlike circuit switching. |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q83➡ | Digital Logic Design Match List I with List II 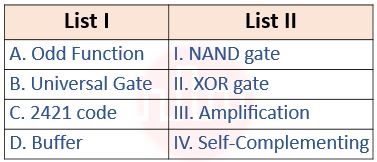 Choose the correct answer from the options given below: |
| i ➥ A – I, B – II, C – III, D – IV |
| ii ➥ A – I, B – III, C – II, D – IV |
| iii ➥ A – II, B – I, C – IV, D – III |
| iv ➥ A – IV, B – II, C – III, D – I |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q84➡ | Digital Logic Design The characteristics of the combinational circuits are: A. Output at any time is function of inputs at that time B. Contains memory elements C. Do not have feedback paths D. Clock is used to trigger the circuits to obtain outputs Choose the correct answer from the options given below: |
| i ➥ A and B only |
| ii ➥ A and C only |
| iii ➥ B and C only |
| iv ➥ B and D only |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q85➡ | Computer Network A message is encrypted using public key cryptography to send a message from sender to receiver. Which one of the following statements is True? |
| i ➥ Receiver decrypts using his own public key |
| ii ➥ Receiver decrypts using sender’s public key |
| iii ➥ Sender encrypts using his own public key |
| iv ➥ Sender encrypts using receiver’s public key |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q86➡ | Data Structure The reverse Polish notation of the following infix expression [A*{B+C*(D+E)}] / {F*(G+H)} is ________. |
| i ➥ ABCDE*++*FGH+*/ |
| ii ➥ ABCDE+**+FGH+*/ |
| iii ➥ ABCDE+*+*FGH*+/ |
| iv ➥ ABCDE+*+*FGH+*/ |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q87➡ | Computer Architecture Given below are two statements Statement I: CISC computers have a large of number of addressing modes. Statement II: In RISC machines memory access is limited to load and store instructions. In light of the above statements, choose the correct answer from the options given below |
| i ➥ Both Statement I and Statement II are false |
| ii ➥ Both Statement I and Statement II are true |
| iii ➥ Statement I is false but Statement II is true |
| iv ➥ Statement I is true but Statement II is false |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q88➡ | Computer Architecture The cache coherence problem can be solved A. by having multiport memory B. allow only nonshared data to be stored in cache C. using a snoopy cache controller D. using memory interleaving Choose the correct answer from the options given below: |
| i ➥ A and C only |
| ii ➥ B and C only |
| iii ➥ B and D only |
| iv ➥ D and C only |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q89➡ | Computer Network In electronic mail, which of the following protocols allows the transfer of multimedia? |
| i ➥ IMAP |
| ii ➥ MIME |
| iii ➥ POP3 |
| iv ➥ SMTP |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q90➡ | Computer Network Which of the following statements are true? A. X.25 is connection-oriented network B. X.25 doesn’t support switched virtual circuits. C. Frame relay service provides acknowledgements. D. Frame relay service provides detection of transmission errors. Choose the correct answer from the options given below: |
| i ➥ A and D only |
| ii ➥ B and C only |
| iii ➥ B and D only |
| iv ➥ C and D only |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q91➡ | Computer Network The address of class B host is to be split into subnets with 6-bit subnet number. What is the maximum number of subnets and the maximum number of hosts in each subnet? |
| i ➥ 62 subnets and 1022 hosts |
| ii ➥ 62 subnets and 262142 hosts |
| iii ➥ 64 subnets and 1024 hosts |
| iv ➥ 64 subnets and hosts 262142 |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | IP Address | Help-Line |
| Q92➡ | Computer Architecture Arrange the following in the increasing order of complexity. A. I/O Module B. I/O processor C. I/O Channel D. DMA Choose the correct answer from the options given below Options:- |
| i ➥ A, B, C, D |
| ii ➥ A, D, C, B |
| iii ➥ C, D, A, B |
| iv ➥ D, C, B, A |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q93➡ | Computer Network Which of the following statements are true? A.Frequency division multiplexing technique can be handled by digital circuits. B.Time division multiplexing technique can be handled by analog circuits C. Wavelength division multiplexing technique is used with optical fiber for combining two signals. D. Frequency division multiplexing technique can be applied when the bandwidth of a link is greater than the bandwidth of the signals to be transmitted. Choose the correct answer from the options given below: |
| i ➥ A and D only |
| ii ➥ B and D only |
| iii ➥ B and D only |
| iv ➥ C and D only |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q94➡ | Digital Logic Design A digital computer has a common bus system for 8 registers 16 bits each. How many multiplexers are required to implement common bus? What size of multiplexers is required? |
| i ➥ 16, 16×1 |
| ii ➥ 16, 8×1 |
| iii ➥ 8, 16×1 |
| iv ➥ 8, 8×1 |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q95➡ | Algorithms Let G(x) be the generator polynomial used for CRC checking. The condition that should be satisfied by the G(x) to catch all errors consisting of an odd number of inverted bits is: |
| i ➥ (1-x2) is factor of G(x) |
| ii ➥ (x+1) is factor of G(x) |
| iii ➥ (x2+1) is factor of G(x) |
| iv ➥ (x-1) is factor of G(x) |
Show Answer With Best Explanation
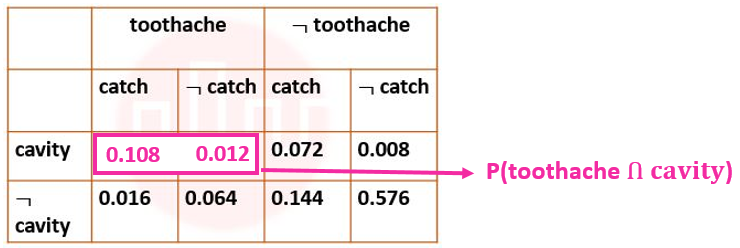
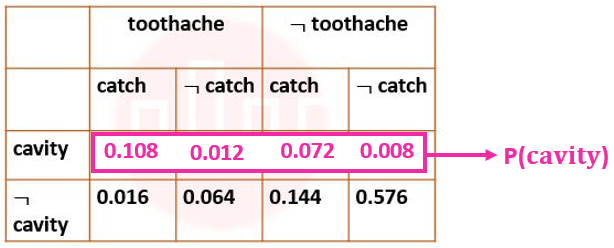
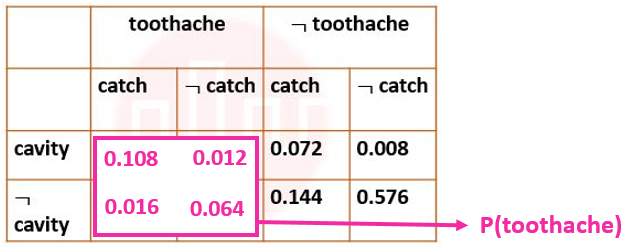
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
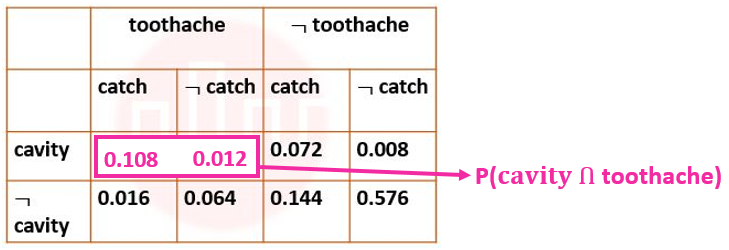
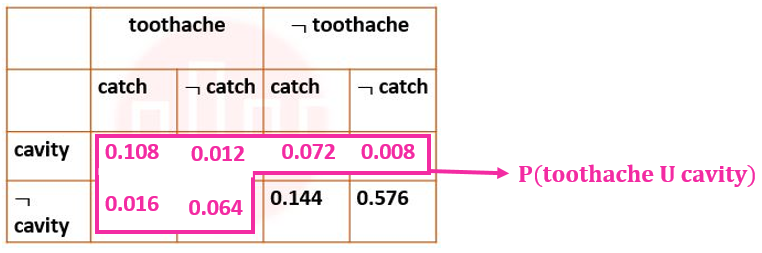
| Q96➡ | Artificial Intelligence Next five questions are based on the following passage. Consider a domain consisting of three Boolean variables Toothache, Cavity, and Catch. The full joint distribution is a 2×2×2 table as shown in the figure below. 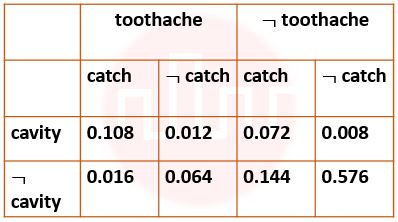 The probability of a toothache, given evidence of a cavity, P(toothache | cavity) is ____. |
| i ➥ 0.216 |
| ii ➥ 0.280 |
| iii ➥ 0.400 |
| iv ➥ 0.600 |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Probability | Help-Line |
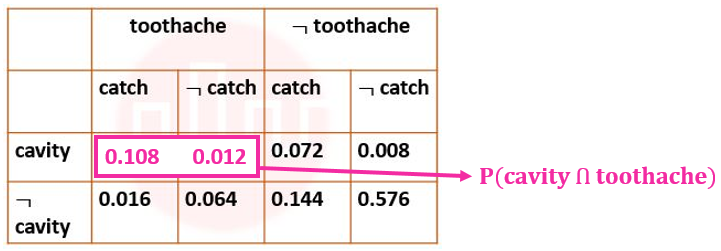
| Q97➡ | Artificial Intelligence Next five questions are based on the following passage. Consider a domain consisting of three Boolean variables Toothache, Cavity, and Catch. The full joint distribution is a 2×2×2 table as shown in the figure below.  P(cavity U toothache) is________________. |
| i ➥ 0.120 |
| ii ➥ 0.200 |
| iii ➥ 0.280 |
| iv ➥ 0.600 |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Probability | Help-Line |
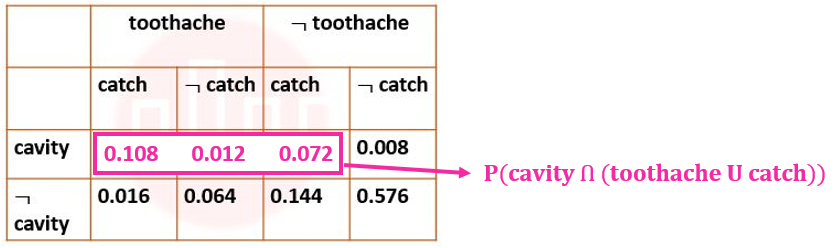
| Q98➡ | Artificial Intelligence Next five questions are based on the following passage. Consider a domain consisting of three Boolean variables Toothache, Cavity, and Catch. The full joint distribution is a 2×2×2 table as shown in the figure below.  The probability for Cavity, given that either Toothache or Catch is true, P(Cavity | toothache U catch) is _______. |
| i ➥ 0.4615 |
| ii ➥ 0.5384 |
| iii ➥ 0.6000 |
| iv ➥ 0.8000 |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Probability | Help-Line |
| ` Q99➡ | Artificial Intelligence Next five questions are based on the following passage. Consider a domain consisting of three Boolean variables Toothache, Cavity, and Catch. The full joint distribution is a 2×2×2 table as shown in the figure below.  The marginal probability of cavity P(cavity) is _____. |
| i ➥ 0.080 |
| ii ➥ 0.120 |
| iii ➥ 0.200 |
| iv ➥ 0.216 |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Probability | Help-Line |
| Q100➡ | Artificial Intelligence Next five questions are based on the following passage. Consider a domain consisting of three Boolean variables Toothache, Cavity, and Catch. The full joint distribution is a 2×2×2 table as shown in the figure below.  The probability of a cavity, given evidence of a toothache, P(cavity | toothache) is ____. |
| i ➥ 0.216 |
| ii ➥ 0.280 |
| iii ➥ 0.400 |
| iv ➥ 0.600 |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Probability | Help-Line |
UGC-NET December 2020 and June 2021 computer Science and application solutions

 =1, m>=1 }”>
=1, m>=1 }”>
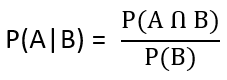
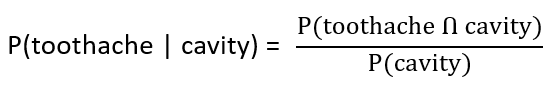

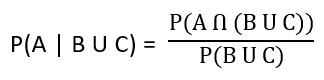
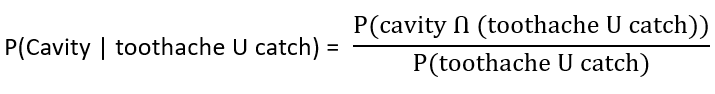
 = 0.4615
= 0.4615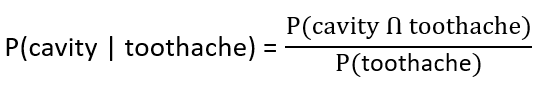
 = 0.6
= 0.6