Computer Network Subject wise UGC NET Question Analysis
Networking PYQ Part-2
| Q.1➡ | UGC NET DEC 2023 The work done by UDP is/are: (A) Congestion control (B) Flow control (C) Retransmission (D) Segments transmission Choose the correct answer from the options given below : |
| i ➥ (A) and (D) Only |
| ii ➥ (C) Only |
| iii ➥ (D) Only |
| iv ➥ (B) and (C) Only |
| Best Explanation: Answer: (III) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q.2➡ | UGC NET DEC 2023 Has functions are used to produce the message digests which are then encrypted with a private key to get : |
| i ➥ Public key |
| ii ➥ Digital signature |
| iii ➥ Cipher text |
| iv ➥ Data Encryption Standard |
| Best Explanation: Answer: (II) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q.3➡ | UGC NET DEC 2023 Which of the following are example of CSMA channel sensing methods ? (A) 1-persistent (B) 2-persistent (C) p-persistent (D) o-persistent Choose the correct answer from the options given below : |
| i ➥ (A), (B) and (D) Only |
| ii ➥ (A), (C) and (D) Only |
| iii ➥ (B), (C) and (D) Only |
| iv ➥ (A), (B) and (C) Only |
| Best Explanation: Answer: (II) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q.4➡ | UGC NET DEC 2023 Match List – I with List – II. List – I (A) Monoalphabetic Cipher (B) DES (C) Stream Cipher (D) Polyalphabetic Cipher List – II (I) Round key (II) One-to-many relationship (III) One-to-one relationship (IV) Feedback mechanism Choose the correct answer from the options given below : |
| i ➥ (A)-(III), (B)-(I), (C)-(IV), (D)-(II) |
| ii ➥ (A)-(III), (B)-(IV), (C)-(II), (D)-(I) |
| iii ➥ (A)-(I), (B)-(III), (C)-(IV), (D)-(II) |
| iv ➥ (A)-(II), (B)-(I), (C)-(IV), (D)-(III) |
| Best Explanation: Answer: (I) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q.5➡ | UGC NET DEC 2023 Which of the following is not a field in TCP header ? |
| i ➥ Sequence Number |
| ii ➥ Checksum |
| iii ➥ Fregmentation offset |
| iv ➥ Window size |
| Best Explanation: Answer: (III) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q.6➡ | UGC NET DEC 2023 Arrange the following in ascending order : (A) Remainder of 4916 when divided by 17 (B) Remainder of 2446 when divided by 9 (C) Remainder of 15517 when divided by 17 (D) Last digits of the number 745 Choose the correct answer from the options given below : |
| i ➥ (A), (B), (C), (D) |
| ii ➥ (A), (B), (D), (C) |
| iii ➥ (A), (C), (B), (D) |
| iv ➥ (D), (C), (B), (A) |
| Best Explanation: Answer: (III) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q.7➡ | UGC NET DEC 2023 Which of the following statement/s are CORRECT ? (A) NRZ is a bipolar scheme in which the positive voltage define bit is 0 (zero). (B) NRZ-L and NRZ-I both have an average signal rate of N/2. (C) The idea of RZ and NRZ-L are combined into Manchester scheme. (D) NRZ-L and NRZ-I both have DC component problems. (E) The minimum bandwidth of Manchester and differential Manchester is 3 times that of NRZ. Choose the correct answer from the options given below : |
| i ➥ (A), (B) and (C) Only |
| ii ➥ (A), (C), (D) and (E) Only |
| iii ➥ (B), (C) and (D) Only |
| iv ➥ (A), (B), (C) and (E) Only |
| Best Explanation: Answer: (III) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q.8➡ UGC NET DEC 2023 In “bit stuffing”, each frame begins and ends with a bit pattern in hexadecimal? |
| i ➥ Ox8C |
| ii ➥ Ox6F |
| iii ➥ OxFF |
| iv ➥ Ox7E |
| Best Explanation: Answer: (IV) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q.9➡ | UGC NET DEC 2023 A multiplexes combines for 100 Kbps channels using a time slot of 2 bits. What is the bit rate? |
| i ➥ 100 Kbps |
| ii ➥ 200 Kbps |
| iii ➥ 40 Kbps |
| iv ➥ 1000 Kbps |
| Best Explanation: Answer: (III) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q10➡ | UGC NET DEC 2023 Which of the following statement/s is/are NOT CORRECT ? (A) OSPF is based on distance-vector routing protocol. (B) Both link-state and distance-vector routing are based on the least cost goal. (C) BGP4 is based on the path-vector algorithm. (D) The three-node instability can be avoided using split horizon combined with poison reverse. (E) RIP is based on link state algorithm. Choose the correct answer from the options given below : |
| i ➥ (A), (D) and (E) Only |
| ii ➥ (A) and (B) Only |
| iii ➥ (B) and (C) Only |
| iv ➥ (B), (C) and (E) Only |
| Best Explanation: Answer: (I) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q.11➡ | UGC NET DEC 2023 Given below are two statements: Statement (I): In datagram networks – routers hold state information about connections Statement (II): In virtual circuit network- each virtual circuit requires router table space per connection In the light of the above statements, choose the most appropriate answer from the options given below: |
| i ➥ Both Statement I and Statement II are correct |
| ii ➥ Both Statement I and Statement II are incorrect |
| iii ➥ Statement I is correct but Statement II is incorrect |
| iv ➥ Statement I is incorrect but Statement II is correct |
| Best Explanation: Answer: (IV) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q.12➡ | UGC NET DEC 2023 Arrange the following steps in the correct order for a DHCP Client to renew its IP lease with a DHCP server: (A) DHCP client sends a DHCPREQUEST message (B) DHCP server acknowledges the renewal with a DHCPACK message (C) DHCP client checks the local lease timer and initiates renewal (D) DHCP server updates its lease database Choose the correct answer from the options given below: |
| i ➥ (A), (B), (C), (D) |
| ii ➥ (C), (D), (Β), (A) |
| iii ➥ (C), (B), (A), (D) |
| iv ➥ (C), (A), (B), (D) |
| Best Explanation: Answer: (IV) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q.13➡ | UGC NET JUNE 2023 IP datagram has arrived with following partial information in the header (in hexadecimal) 45000054000300002006….. What is the header size? |
| i ➥ 10 bytes |
| ii ➥ 20 bytes |
| iii ➥ 30 bytes |
| iv ➥ 40 bytes |
| Best Explanation: Answer: II Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q.14➡ | UGC NET JUNE 2023 IP datagram has arrived with following partial information in the header (in hexadecimal) 45000054000300002006…. How many more routers can the packet travel to? |
| i ➥ 22 |
| ii ➥ 26 |
| iii ➥ 30 |
| iv ➥ 32 |
| Best Explanation: Answer: IV Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q.15➡ | UGC NET JUNE 2023 IP datagram has arrived with following partial information in the header (in hexadecimal) 45000054000300002006…. What is the protocol of the payload being carried by the packet? |
| i ➥ ICMP |
| ii ➥ SCTP |
| iii ➥ TCP protocol |
| iv ➥ IGMP |
| Best Explanation: Answer: III Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q.16➡ | UGC NET JUNE 2023 IP datagram has arrived with following partial information in the header (in hexadecimal) 45000054000300002006… What is the efficiency of this datagram? |
| i ➥ 76.19% |
| ii ➥ 80.50% |
| iii ➥ 82.24% |
| iv ➥ 85.45% |
| Best Explanation: Answer: I Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q.17➡ | UGC NET JUNE 2023 IP datagram has arrived with following partial information in the header (in hexadecimal) 45000054000300002006…. What is the size of datagram? |
| i ➥ 64 bytes |
| ii ➥ 74 bytes |
| iii ➥ 84 bytes |
| iv ➥ 104 bytes |
| Best Explanation: Answer: III Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q.18➡ | UGC NET JUNE 2023 Match List I with List II 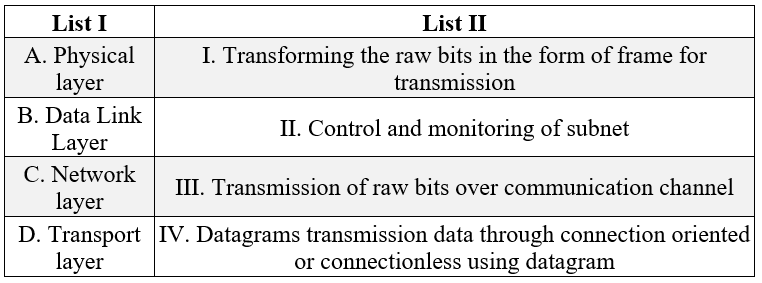 Choose the correct answer from the options given below: |
| i ➥ A-III B-II C-I D-IV |
| ii ➥ A-II B-III C-I D-IV |
| iii ➥ A-III B-I C-II D-IV |
| iv ➥ A-II B-IV C-I D-III |
| Best Explanation: Answer: III Explanation: A. Physical layer → III Transmission of raw bits over communication channel B. Data Link Layer → I. Transforming the raw bits in the form of frame for transmission C. Network layer → II. Control and monitoring of subnet D. Transport layer → IV. Datagrams transmission data through connection oriented or connectionless using datagram |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q.19➡ | UGC NET JUNE 2023 Match List I with List II 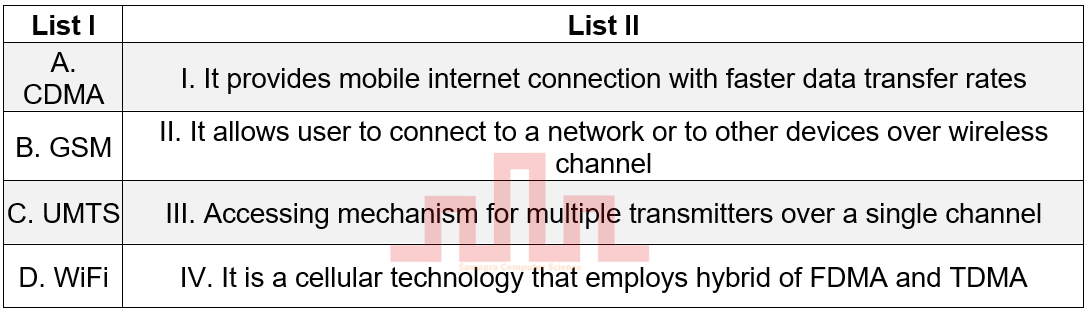 |
| i ➥ A-III B-IV C-II D-I |
| ii ➥ A-III B-IV C-I D-II |
| iii ➥ A-II B-III C-IV D-I |
| iv ➥ A-II B-I C-IV D-III |
| Best Explanation: Answer: II Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q.20➡ | UGC NET JUNE 2023 A TCP server application is programmed to listen on port P on host S. A TCP client is connected to the TCP server over the network, Consider that while TCP connection is active the server is crashed and rebooted. Assume that the client does not use TCP keep alive timer. Which of the following behavior /s is/are possible? Statement I: The TCP application server on S can listen on P after reboot. Statement II: If client sends a packet after the server reboot, it will receive the RST segment. In the light of the above statements, choose the correct answer from the options given below. |
| i ➥ Both Statement I and Statement II are true |
| ii ➥ Both Statement I and Statement II are false |
| iii ➥ Statement I is true but Statement II is false |
| iv ➥ Statement I is false but Statement II is true |
| Best Explanation: Answer: I Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q.21➡ | UGC NET JUNE 2023 In the standard Ethernet with transmission rate of 10Mbps, asssume that the length of the medium is 2500 m and size of a frame is 512 bytes. The propagation speed of a signal in a cable is normally 2 * 10 ^ 8 * m / s The transmission delay and propogation delay are. |
| i ➥ 25.25μs and 51.2μs |
| ii ➥ 51.2μs and 12.5μs |
| iii ➥ 10.24μs and 50.12μs |
| iv ➥ 12.5μs and 51.2μs |
| Best Explanation: Answer: II Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q.22➡ | UGC NET JUNE 2023 Consider two hosts P and Q that are connected through a router R. The maximum transfer unit (MTU) value of the link between P and R is 1500 bytes and between R and Q is 820 bytes. A TCP segment of size 1400 bytes is transferred from P to Q through R with IP identification value of 0 x 1234. Assume that IP header size is 20 bytes. Further the pcaket is allowed to be fragmented that is Don’t fragment (DF) flag in the IP Header is not set by P. Which of the following statement/s is/are true? A. Two fragments are created at R and IP datagram size carrying the second fragment is 620 bytes B. If the second fragment is lost, then R resends the fragment with IP identification value of 0 × 1234 C. If the second fragment lost, then P requires to resend the entire TCP segment. D. TCP destination port can be determined by analyzing the second fragment only. Choose the correct answer from the options given below: |
| i ➥ A, B and C only |
| ii ➥ A and C only |
| iii ➥ C and D only |
| iv ➥ B and D only |
| Best Explanation: Answer: B Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q.23➡ | NET June 2023 Match List I with List II 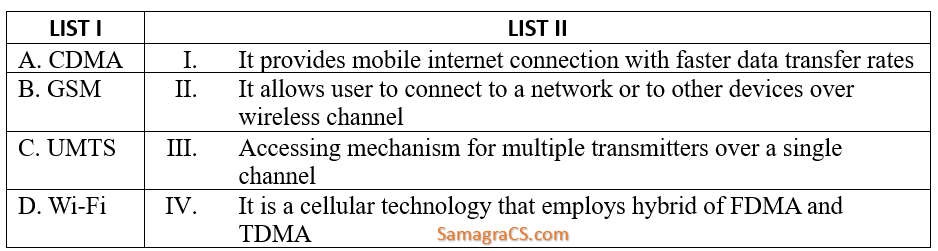 Choose the correct answer from the options given below: |
| i ➥ A-III, B-IV, C-II, D-I |
| ii ➥ A-III, B-IV, C-I, D-II |
| iii ➥ A-II, B-III, C-IV, D-I |
| iv ➥ A-II, B-I, C-IV, D-III |
| Best Explanation: Answer: (ii) Explanation: Here is a brief explanation of each technology: CDMA (Code Division Multiple Access): A cellular technology that uses a spread spectrum technique to allow multiple users to share a single frequency channel. GSM (Global System for Mobile Communications): A cellular technology that uses digital signals to provide mobile voice and data services. UMTS (Universal Mobile Telecommunications System): A 3G cellular technology that provides faster data transfer rates than GSM. Wi-Fi (Wireless Fidelity): A wireless networking technology that allows devices to connect to the internet or to each other over a short distance. Now, let’s match each technology with its corresponding description in the image: A-III: CDMA is an accessing mechanism for multiple transmitters over a single channel. B-IV: GSM is a cellular technology that employs a hybrid of FDMA (Frequency Division Multiple Access) and TDMA (Time Division Multiple Access). C-I: UMTS provides mobile internet connection with faster data transfer rates. D-II: Wi-Fi allows user to connect to a network or to other devices over wireless channel. Therefore, the correct answer is 2. A-III, B-IV, C-I, D-II. |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q.24➡ | NET June 2023 A TCP server application is programmed to listen on port P on host S. A TCP client is connected to the TCP server over the network, consider that while TCP connection is active the server is crashed and rebooted. Assume that the client does not use TCP keepalive timer. Which of the following behaviour/s is/are possible? Statement I: The TCP application server on S can listen on P after reboot. Statement II: If client sends a packet after the server reboot, it will receive the RST segment. In the light of the above statements, choose the correct answer from the options given below. |
| i ➥ Both Statement I and Statement II are true |
| ii ➥ Both Statement I and Statement II are false |
| iii ➥ Statement I is true but Statement II is false |
| iv ➥ Statement I is false but Statement II is true |
| Best Explanation: Answer: (i) Explanation: Statement I: The TCP application server on S can listen on P after reboot. This statement is true. When the server reboots, it can reestablish the listening socket on port P, assuming there are no conflicts or issues preventing it from doing so. Statement II: If the client sends a packet after the server reboot, it will receive the RST segment. This statement is also true. When the server reboots, any existing TCP connections are terminated, and the client will receive a RST (reset) segment as a response to any further data it sends on the previous connection. So, the correct answer is: Both Statement I and Statement II are true. |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q.25➡ | NET June 2023 In the standard Ethernet with transmission rate of 10 Mbps, assume that the length of the medium is 2500m and size of a frame is 512 bytes. The propagation speed of a signal in a cable is normally 2 x 108 m/s. The transmission delay and propagation delay are |
| i ➥ 25.25μs and 51.2μs |
| ii ➥ 51.2 μs and 12.5 μs |
| iii ➥ 10.24 μs and 50.12 μs |
| iv ➥ 12.5 μs and 51.2 μs |
| Best Explanation: Answer: (ii) Explanation: Transmission delay in Ethernet is the time it takes to transmit a single frame over the physical medium. It is calculated by dividing the frame size by the transmission rate. In this case, the transmission delay is: Transmission delay = Frame size / Transmission rate→ 512 bytes / 10 Mbps = 51.2 microsecondsPropagation delay in Ethernet is the time it takes for a single bit to travel from the source to the destination over the physical medium. It is calculated by dividing the length of the medium by the propagation speed of the signal. In this case, the propagation delay is: Propagation delay = Length of medium / Propagation speed→ 2500 m / 2 x 10^8 m/s = 12.5 microsecondsTherefore, the transmission delay and propagation delay in the standard Ethernet with a transmission rate of 10 Mbps, a medium length of 2500 m, and a frame size of 512 bytes are 51.2 microseconds and 12.5 microseconds, respectively. |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q.26➡ | NET June 2023 Match List I with List II 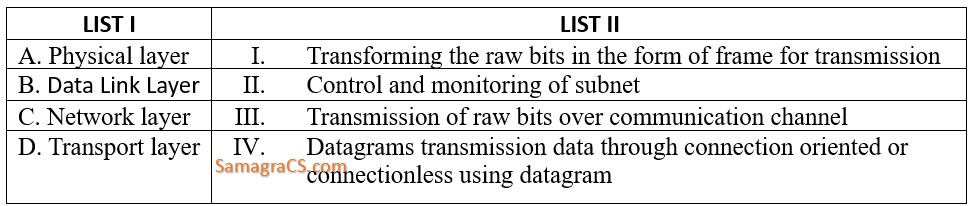 Choose the correct answer from the options given below: |
| i ➥ A-III, B-II, C-I, D-IV |
| ii ➥ A-II, B-III, C-I, D-IV |
| iii ➥ A-III, B-I, C-II, D-IV |
| iv ➥ A-II, B-IV, C-I, D-III |
| Best Explanation: Answer: (i) Explanation: Here’s the correct match for List I with List II: A. Physical layer – III. Transmission of raw bits over a communication channel B. Data Link Layer – I. Transforming the raw bits into the form of frames for transmission C. Network layer – II. Control and monitoring of the subnet D. Transport layer – IV. Datagram transmission of data through connection-oriented or connectionless using datagrams So, the correct match is: A-III, B-I, C-II, D-IV |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q.27➡ | NET June 2023 Consider two hosts P and Q that are connected through a router R. The maximum transfer unit (MTU) value of the link between P and 1500 bytes and between R and Q is 820 bytes. A TCP segment of size 1400 bytes is transferred from P to Q through R with IP identification value of 0x1234. Assume that IP header size is 20 bytes. Further the packet is allowed to be fragmented that is Don’t fragment (DF) flag in the IP Header is not set by P. Which of the following statement/s is/are true? A. Two fragments are created at R and IP datagram size carrying the second fragment is 620 bytes B. If the second fragment is lost, then R resends the fragment with IP identification value of 0x1234 C. If the second fragment lost, then P requires to resend the entire TCP segment. D. TCP destination port can be determined by analysing the second fragment only. Choose the correct answer from the options given below: |
| i ➥ A. B and C only |
| ii ➥ A and C only |
| iii ➥ C and D only |
| iv ➥ B and D only |
| Best Explanation: Answer: (iii) Explanation: Let’s analyze each statement: A. Two fragments are created at R, and the IP datagram size carrying the second fragment is 620 bytes. This statement is true. Since the MTU between P and R is 1500 bytes and the MTU between R and Q is 820 bytes, when the 1400-byte TCP segment from P is forwarded through R, it will be fragmented into two parts. The first fragment will be 820 bytes, and the second fragment will be 580 bytes (1400 – 820). B. If the second fragment is lost, then R resends the fragment with an IP identification value of 0x1234. This statement is false. R is a router and does not maintain the state of TCP segments. It is the responsibility of the end-hosts (P and Q) to handle retransmissions and not the router (R). C. If the second fragment is lost, then P requires to resend the entire TCP segment. This statement is true. If the second fragment is lost, P would have to resend the entire TCP segment to ensure that all data is delivered to the destination, as the TCP protocol ensures reliable data transfer. D. TCP destination port can be determined by analyzing the second fragment only. This statement is false. The destination port of a TCP segment is typically found in the TCP header of the original unfragmented segment. It is not determined by analyzing any single fragment. So, the correct answer is: A and C only |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q.28➡ | NET June 2023 IP datagram has arrived with following partial information in the header (in hexadecimal) 45000054000300002006….. What is the header size? |
| i ➥ 10 bytes |
| ii ➥ 20 bytes |
| iii ➥ 30 bytes |
| iv ➥ 40 bytes |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Best Explanation: Answer: (ii) Explanation: The IP datagram header size is 20 bytes. The first byte of the header contains the version and header length fields. The version field is always 4 for IPv4, and the header length field is a 4-bit field that specifies the number of 32-bit words in the header. The minimum value for the header length field is 5, which indicates a length of 5 × 32 bits = 160 bits = 20 bytes. The maximum value for the header length field is 15, which indicates a length of 15 × 32 bits = 480 bits = 60 bytes. In the given partial header, the first byte is 45. The first four bits of this byte are 45, which is the hexadecimal representation of the decimal number 17. Since the header length field is a 4-bit field, the value 17 is invalid. Therefore, the only possible value for the header length field is 5, which indicates a header size of 20 bytes.Here is a breakdown of the first 10 bytes of the header: 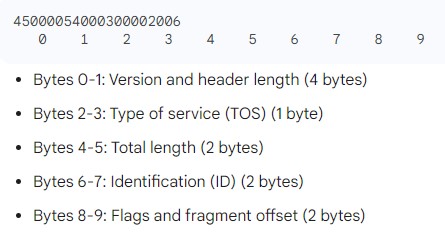 Bytes 0-1: Version and header length (4 bytes) Bytes 2-3: Type of service (TOS) (1 byte) Bytes 4-5: Total length (2 bytes) Bytes 6-7: Identification (ID) (2 bytes) Bytes 8-9: Flags and fragment offset (2 bytes) The remaining bytes of the header contain additional information, such as the source and destination IP addresses, time to live (TTL), and protocol number. |
| Q.29➡ | NET June 2023 IP datagram has arrived with following partial information in the header (in hexadecimal) 45000054000300002006….. How many more routers can the packet travel to? |
| i ➥ 22 |
| ii ➥ 26 |
| iii ➥ 30 |
| iv ➥ 32 |
| Best Explanation: Answer: (iv) Explanation: In an IPv4 header, the “Time to Live” (TTL) field determines the maximum number of routers (hops) that a packet can travel through before it is discarded. The TTL field is 8 bits in length, so it can have values from 0 to 255. In the provided hexadecimal information, the TTL field appears to be “20” in hexadecimal, which is equivalent to 32 in decimal. This means that the packet can travel through 32 more routers (hops) before it is discarded. So, the answer is: 32 Answer will be : (iv) 32 |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q.30➡ | NET June 2023 IP datagram has arrived with following partial information in the header (in hexadecimal) 45000054000300002006….. What is the protocol of the payload being carried by the packet? |
| i ➥ ICMP |
| ii ➥ SCTP |
| iii ➥ TCP protocol |
| iv ➥ IGMP |
| Best Explanation: Answer: (iii) Explanation: In an IPv4 header, the protocol field is a 1-byte (8-bit) field that specifies the protocol of the payload being carried by the packet. The protocol field indicates the type of data encapsulated in the IP packet. In the provided hexadecimal information, the protocol field is “06” in hexadecimal, which is equivalent to 6 in decimal. The protocol value of 6 corresponds to the “TCP protocol.” So, the protocol of the payload being carried by the packet is “TCP protocol.” The correct answer is: TCP protocol |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q.31➡ | NET June 2023 IP datagram has arrived with following partial information in the header (in hexadecimal) 45000054000300002006….. What is the size of datagram? |
| i ➥ 64 bytes |
| ii ➥ 74 bytes |
| iii ➥ 84 bytes |
| iv ➥ 104 bytes |
| Best Explanation: Answer: (iii) Explanation: 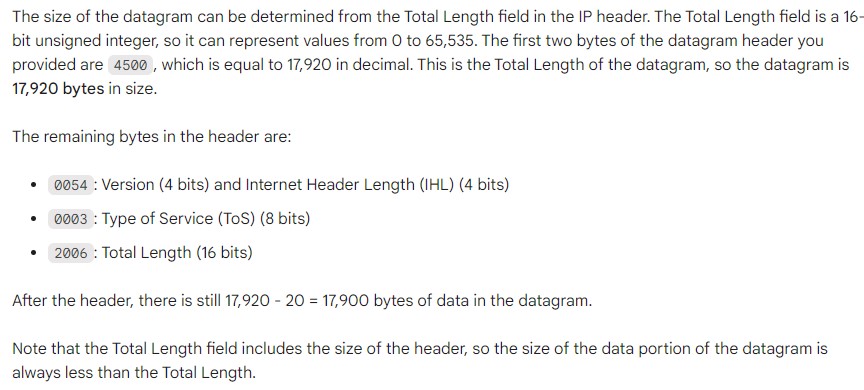 Answer : 84 bytes. The Total Length field in the IP header is 4500, which is equal to 17,920 in decimal. This is the total size of the datagram, including the header. The header is 20 bytes long, so the size of the data portion of the datagram is 17,920 – 20 = 17,900 bytes.Therefore, the size of the datagram is 84 bytes. |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q.32➡ | NET June 2023 IP datagram has arrived with following partial information in the header (in hexadecimal) 45000054000300002006….. What is the efficiency of this datagram? |
| i ➥ 76.19% |
| ii ➥ 80.50% |
| iii ➥ 82.24% |
| iv ➥ 185.45% |
| Best Explanation: Answer: (i) Explanation: 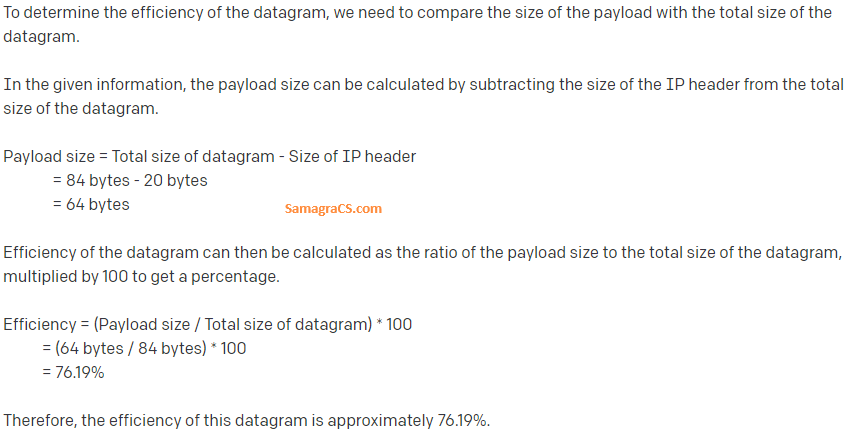 |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q.33➡ | NET December 2022 Which one of the following allows the session to continue? |
| i ➥ When a user quits a browser |
| ii ➥ When the user logs out and is invalidated by the servlet |
| iii ➥ When the session is timed out due to inactivity |
| iv ➥ When the user refreshes the browser and there is a persistent cookie |
| Best Explanation: Answer: (iv) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q.34➡ | NET December 2022 Given Ethernet address 01011010 00010001 01010101 00011000 10101010 00001111 in binary, what is the address in hexadecimal notation ? |
| i ➥ 5A : 88 : AA : 18 : 55 : F0 |
| ii ➥ 5A : 81 : BA : 81 : AA : 08 |
| iii ➥ 5A : 18 : 5A : 18 : 55 : 0F |
| iv ➥ 5A : 11 : 55 : 18 : 55 : 0F |
| Best Explanation: Answer: (iv) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q.35➡ | NET December 2022 A computer on a 10 Mbps network is regulated by a token bucket. The token bucket is filled at a rate of 2 Mbps. It is initially filled to capacity with 16 megabits. What is the maximum duration for which the computer can transmit at the full 10 Mbps? |
| i ➥ 1.6 seconds |
| ii ➥ 2 seconds |
| iii ➥ 5 seconds |
| iv ➥ 8 seconds |
| Best Explanation: Answer: (ii) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q.36➡ | NET December 2022 In the standard Ethernet with transmission rate of 10 Mbps , assume that the length of the medium is 2500 m and size of a frame is 512 byes. The propagation speed of a signal in a cable is normally 2×108 m/s. calculate transmission delay and propagation delay. |
| i ➥ 25.25 µs and 51.2 µs |
| ii ➥ 51.2 µs and 12.5 µs |
| iii ➥ 10.2 µs and 50.12 µs |
| iv ➥ 12.5 µs and 51.2 µs |
| Best Explanation: Answer: (ii) Explanation: Transmission delay in Ethernet is the time it takes to transmit a single frame over the physical medium. It is calculated by dividing the frame size by the transmission rate. In this case, the transmission delay is: Transmission delay = Frame size / Transmission rate → 512 bytes / 10 Mbps = 51.2 microsecondsPropagation delay in Ethernet is the time it takes for a single bit to travel from the source to the destination over the physical medium. It is calculated by dividing the length of the medium by the propagation speed of the signal. In this case, the propagation delay is: Propagation delay = Length of medium / Propagation speed → 2500 m / 2 x 10^8 m/s = 12.5 microsecondsTherefore, the transmission delay and propagation delay in the standard Ethernet with a transmission rate of 10 Mbps, a medium length of 2500 m, and a frame size of 512 bytes are 51.2 microseconds and 12.5 microseconds, respectively. |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q.37➡ | NET December 2022 In CRC coding if the data word is 111111 , divisor is 1010 and the remainder is 110. Which of the following code is true? |
| i ➥ 011111101 |
| ii ➥ 001010110 |
| iii ➥ 111111110 |
| iv ➥ 110111111 |
| Best Explanation: Answer: (iii) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q.38➡ | NET December 2022 Consider two hosts P and Q are connected through a router R. The maximum transfer unit (MTU) value of the link between P and R is 1500 bytes and between R and Q is 820 bytes. A TCP segment of size of 1400 bytes is transferred from P to Q through R with IP identification value of 0x1234, Assume that IP header size is 20 bytes Further the packet is allowed to be fragmented that is Don’t Fragment (DF) flag in the IP Header is not set by P which of the following statement is are true (A) Two fragments are created at R and IP datagram size carrying the second fragment is 620 bytes (B) If the second fragment is lost then R resend the fragment with IP Identification value of 0x1334 (C) If the second fragment lost then P required to resend the entire TCP segment (D) TCP destination port can be determined by analyzing the second fragment only Choose the correct answer from the options given below: |
| i ➥ A, B and C only |
| ii ➥ A and C only |
| iii ➥ C and D only |
| iv ➥ B and D only |
| Best Explanation: Answer: (ii) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q.39➡ | NET December 2022 The solution to silly window syndrome problem is/are (A) Nagle’s algorithm (B) Clark’s algorithm (C) Jacobson’s algorithm (D) Piggy backing algorithm Choose the correct answer from the options given below: |
| i ➥ A and B only |
| ii ➥ A and C only |
| iii ➥ C and D only |
| iv ➥ B and D only |
| Best Explanation: Answer: (i) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
Q.40➡ | NET December 2022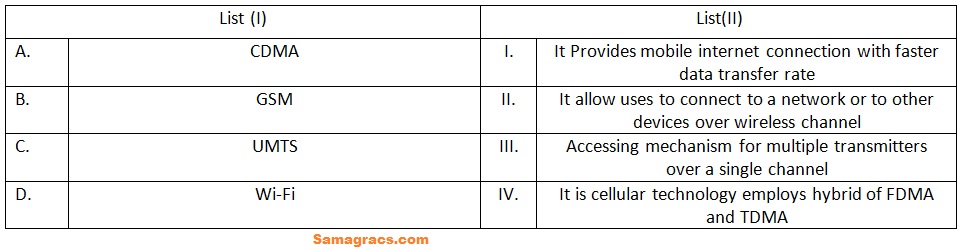 Choose the correct answer from the options given below: |
| i ➥ A-(III), B-(IV), C-(II), D-(I) |
| ii ➥ A-(III), B-(IV), C-(I), D-(II) |
| iii ➥ A-(III), B-(IV), C-(I), D-(II) |
| iv ➥ A-(II), B-(I), C-(IV), D-(III) |
| Best Explanation: Answer: (ii) Explanation: Here is a brief explanation of each technology: CDMA (Code Division Multiple Access): A cellular technology that uses a spread spectrum technique to allow multiple users to share a single frequency channel. GSM (Global System for Mobile Communications): A cellular technology that uses digital signals to provide mobile voice and data services. UMTS (Universal Mobile Telecommunications System): A 3G cellular technology that provides faster data transfer rates than GSM. Wi-Fi (Wireless Fidelity): A wireless networking technology that allows devices to connect to the internet or to each other over a short distance. Now, let’s match each technology with its corresponding description in the image: A-III: CDMA is an accessing mechanism for multiple transmitters over a single channel. B-IV: GSM is a cellular technology that employs a hybrid of FDMA (Frequency Division Multiple Access) and TDMA (Time Division Multiple Access). C-I: UMTS provides mobile internet connection with faster data transfer rates. D-II: Wi-Fi allows user to connect to a network or to other devices over wireless channel. Therefore, the correct answer is 2. A-III, B-IV, C-I, D-II. |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q.41➡ | NET December 2022 Rearrange the following sequence in the context of OSI layers: (A) Transforming the raw bits in the form of frame for transmission (B) Transmission of raw bits over communication channel (C) Handling user interfaces (D) Control and monitoring of subnet (E) Transmission data through connection orientated or connection less using datagram. Choose the correct answer from the options given below: |
| i ➥ A-B-C-D-E |
| ii ➥ B-C-D-E-A |
| iii ➥ B-A-D-E-C |
| iv ➥ A-B-D-E-C |
| Best Explanation: Answer: (iii) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q.42➡ | NET December 2022 A TCP Server application is programmed to listen on port P on Host S. A TCP Client is connected to the TCP Server over the network. Considered that while TCP Connection is active the server is crashed and rebooted Assume that the client does not use TCP keep alive timer. Which of the following behaviors is/are possible? Statement I: If client is waiting to receive a packet, it may wait indefinitely Statement II: If the client sends a packet after the server reboot, it will receive the FIN segment In the light of the above statements. Choose the correct answer from the options given below: |
| i ➥ Both Statement I and Statement II are true |
| ii ➥ Both Statement I and Statement II are false |
| iii ➥ Statement I is true but Statement II is false |
| iv ➥ Statement I is false but Statement II is true |
| Best Explanation: Answer: (iii) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q.43➡ | NET December 2022 An organization is granted the block 130.56.0.0/16. The administration wants to create 1024 subnets. Find the number of addresses is each subnet. |
| i ➥ 32 |
| ii ➥ 64 |
| iii ➥ 128 |
| iv ➥ 16 |
| Best Explanation: Answer: (ii) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q.44➡ | NET December 2022 An organization is granted the block 130.56.0.0/16 . The administration wants to create 1024 subnets. Find the subnet prefix |
| i ➥ 130.56 |
| ii ➥ 136.0 |
| iii ➥ 136.255 |
| iv ➥ 136.56.255 |
| Best Explanation: Answer: (i) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q.45➡ | NET December 2022 An organization is granted the block 130.56.0.0/16. The administration wants to create 1024 subnets. Find first and last addresses of First subnet. |
| i ➥ 130.56.0.0 130.56.254.254 |
| ii ➥ 130.56.0.0 130.56.0.63 |
| iii ➥ 130.0.0.0 130.255.255.255 |
| iv ➥ 130.56.0.0 130.56.255.63 |
| Best Explanation: Answer: (ii) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q.46➡ | NET December 2022 An organization is granted the block 130.56.0.0/16 . The administration wants to create 1024 subnets. Find first and last address of the last subnet. |
| i ➥ 130.56.0.0 130.56.254.255 |
| ii ➥ 130.56.255.0 130.56.255.255 |
| iii ➥ 130.56.255.0 130.56.255.255 |
| iv ➥ 130.56.255.192 130.56.255.255 |
| Best Explanation: Answer: (iv) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q.47➡ | NET December 2022 An organization is granted the block 130.56.0.0/16 . The administration wants to create 1024 subnets. Find the subnet mask. |
| i ➥ 130.255.255.255 |
| ii ➥ 130.56.255.255 |
| iii ➥ 130.56.0.255 |
| iv ➥ 130.56.155.192 |
| Best Explanation: Answer: Mark to All Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q.48➡ | NET June 2022 match List I with List II: 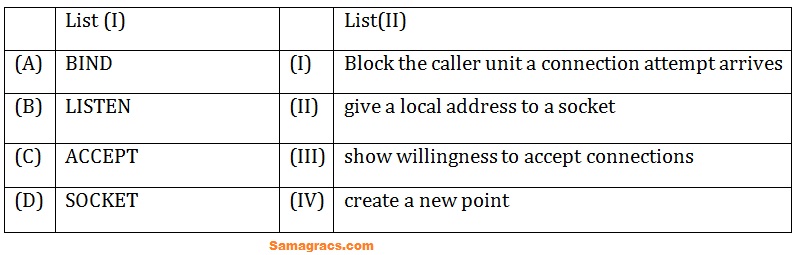 Choose the correct answer from the options given below: |
| i ➥ (A)-(I),(B)-(III),(C)-(II),(D)-(IV) |
| ii ➥ (A)-(II),(B)-(III),(C)-(I),(D)-(IV) |
| iii ➥ (A)-(III),(B)-(II),(C)-(I),(D)-(IV) |
| iv ➥ (A)-(I),(B)-(II),(C)-(III),(D)-(IV) |
| Best Explanation: Answer: (ii) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q.49➡ | NET June 2022 which one is a connectionless transport layer protocol that belongs to the internet protocol family? |
| i ➥ Transmission control protocol (TCP) |
| ii ➥ User Datagram Protocol (UDP) |
| iii ➥ Routing Protocol (RP) |
| iv ➥ Datagram Control Protocol (DCP) |
| Best Explanation: Answer: (ii) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q.50➡ | NET June 2022 which of the following is correct for the destination address 4A : 30 : 10 : 21 : 10 : 1A? |
| i ➥ Unicast address |
| ii ➥ Multicast address |
| iii ➥ Broadcast address |
| iv ➥ Unicast and broadcast address |
| Best Explanation: Answer: (i) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q.51➡ | NET June 2022 which mode is a block cipher implementation as a self synchronizing stream cipher? |
| i ➥ Cipher Block chaining mode |
| ii ➥ Cipher feedback mode |
| iii ➥ Electronic codebook mode |
| iv ➥ Output feedback mode |
| Best Explanation: Answer: (ii) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q.52➡ | NET June 2022 The representation of 4 bits code 1101 into 7 bit, even parity Hamming code is |
| i ➥ (1010101) |
| ii ➥ (1111001) |
| iii ➥ (1011101) |
| iv ➥ (1110000) |
| Best Explanation: Answer: (i) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q.53➡ | NET June 2022 which layer divides each message into packets at the source and re-assembles them at the destination? |
| i ➥ Network layer |
| ii ➥ Transport layer |
| iii ➥ Data link layer |
| iv ➥ Physical layer |
| Best Explanation: Answer: (ii) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q.54➡ | NET June 2022 Consider an error free 64 kbps satellite channel used to sent 512 byte data frames I one direction with very short acknowledgements coming back the other way. What is the maximum throughput for window size of 15? |
| i ➥ 32 kbps |
| ii ➥ 48 kbps |
| iii ➥ 64 kbps |
| iv ➥ 70 kbps |
| Best Explanation: Answer: (iii) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q.55➡ | NET June 2022 For multiprocessor system , interconnection network – cross bar switch is an example of |
| i ➥ Non blocking network |
| ii ➥ Blocking network |
| iii ➥ That varies from connection to connection |
| iv ➥ Recurrent network |
| Best Explanation: Answer: (i) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q.56➡ | NET June 2022 Using ‘RSA’ algorithm, if p = 13, q = 5 and e = 7 . the value of d and cipher value of ‘6’ with (e,n) key are |
| i ➥ 7, 4 |
| ii ➥ 7, 1 |
| iii ➥ 7, 46 |
| iv ➥ 55, 1 |
| Best Explanation: Answer: (iii) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
Q.57➡ | NET June 2022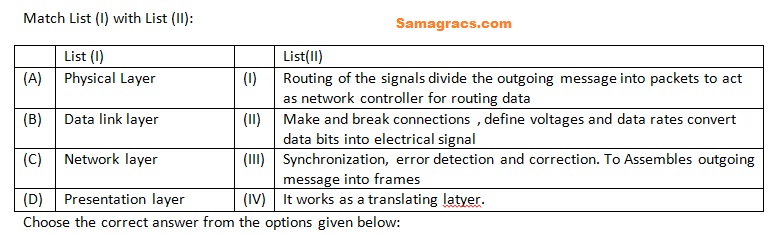 |
| i ➥ (A)-(IV),(B)-(III),(C)-(II),(D)-(I) |
| ii ➥ (A)-(II),(B)-(III),(C)-(IV),(D)-(I) |
| iii ➥ (A)-(IV),(B)-(III),(C)-(I),(D)-(II) |
| iv ➥ (A)-(II),(B)-(III),(C)-(I),(D)-(IV) |
| Best Explanation: Answer: (iv) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
Q.58➡ | NET June 2022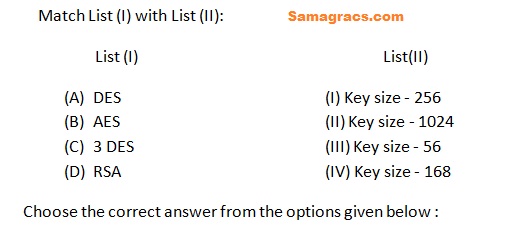 |
| i ➥ (A)-(I),(B)-(II),(C)-(IV),(D)-(III) |
| ii ➥ (A)-(III),(B)-(I),(C)-(IV),(D)-(II) |
| iii ➥ (A)-(III),(B)-(IV),(C)-(II),(D)-(I) |
| iv ➥ (A)-(IV),(B)-(II),(C)-(III),(D)-(I) |
| Best Explanation: Answer: (ii) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q.59➡ | NET June 2022 A classless address is given as 167.199.170.82/27. The number of addresses in the network is |
| i ➥ 64 addresses |
| ii ➥ 32 addresses |
| iii ➥ 28 addresses |
| iv ➥ 30 addresses |
| Best Explanation: Answer: (ii) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q.60➡ | NET June 2022 Based on following passage, answer the questions : A 300 km long truck operates at 1.536 mbps and is used to transmit 64 bytes frames and uses sliding window protocol. the propagation speed is 6 µ sec/km. If only 6 bits are reserved for sequence number field , then the efficiency of the system is |
| i ➥ 0.587 |
| ii ➥ 0.875 |
| iii ➥ 0.578 |
| iv ➥ 0.50 |
| Best Explanation: Answer: (i) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q.61➡ | NET June 2022 Based on following passage , answer the questions : A 300 km long truck operates at 1.536 mbps and is used to transmit 64 bytes frames and uses sliding window protocol. the propagation speed is 6 μ sec/km. The minimum number of bits required in sequence number fields of the packet is |
| i ➥ 6 bits |
| ii ➥ 7 bits |
| iii ➥ 5 bits |
| iv ➥ 4 bits |
| Best Explanation: Answer: (ii) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q.62➡ | NET June 2022 Based on following passage , answer the questions : A 300 km long truck operates at 1.536 mbps and is used to transmit 64 bytes frames and uses sliding window protocol. the propagation speed is 6 µ sec/km. The maximum achievable throughput is |
| i ➥ 0.768 |
| ii ➥ 0.678 |
| iii ➥ 0.901 |
| iv ➥ 0.887 |
| Best Explanation: Answer: (ii) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q.63➡ | NET June 2022 Based on following passage , answer the questions : A 300 km long truck operates at 1.536 mbps and is used to transmit 64 bytes frames and uses sliding window protocol. the propagation speed is 6 µ sec/km. The transmission and propagation delays are respectively |
| i ➥ Tt = 333.33 µ sec, Tp = 18000 µ sec |
| ii ➥ Tt = 300 µ sec, Tp = 15360 µ sec |
| iii ➥ Tt = 33.33 µ sec, Tp = 1800 µ sec |
| iv ➥ Tt = 1800 µ sec, Tp = 33.33 µ sec |
| Best Explanation: Answer: (i) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q.64➡ | NET June 2022 Based on following passage , answer the questions : A 300 km long truck operates at 1.536 mbps and is used to transmit 64 bytes frames and uses sliding window protocol. the propagation speed is 6 µ sec/km. The Sender window size to get the maximum efficiency is |
| i ➥ 108 |
| ii ➥ 109 |
| iii ➥ 55 |
| iv ➥ 56 |
| Best Explanation: Answer: (ii) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q.65➡ | NET November 2021 In Ethernet when Manchester coding is used, the bit rate is ______. |
| i ➥ Half the baud rate |
| ii ➥ Same as the baud rate |
| iii ➥ Thrice the baud rate |
| iv ➥ twice the baud rate |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q.66➡ | NET November 2021 Given below are two statements Statement I: Telnet, Ftp, Http are application layer protocol Statement II: The Iridium project was planned to launch 66 low orbit satellites. In light of the above statements, choose the correct answer from the options given below. |
| i ➥ Both Statement I and Statement II are false |
| ii ➥ Both Statement I and Statement II are true |
| iii ➥ Statement I is false but Statement II is true |
| iv ➥ Statement I is true but Statement II is false |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q.67➡ | NET November 2021 Match List I with List II 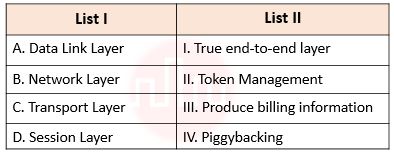 Choose the correct answer from the options given below: |
| i ➥ A – II, B – III, C – I, D – IV |
| ii ➥ A – IV, B – I, C – III, D – II |
| iii ➥ A – IV, B – II, C – I, D – III |
| iv ➥ A – IV, B – III, C – I, D – II |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q.68➡ | NET November 2021 Which of the following statement is False? |
| i ➥ Packet switching can lead to reordering unlike circuit switching. |
| ii ➥ Packet switching leads to better utilization of bandwidth resources than circuit switching. |
| iii ➥ Packet switching results in less variation in the delay than circuit switching. |
| iv ➥ Packet switching sender and receiver can use any bit rate, format or framing method unlike circuit switching. |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q.69➡ | NET November 2021 A message is encrypted using public key cryptography to send a message from sender to receiver. Which one of the following statements is True? |
| i ➥ Receiver decrypts using his own public key |
| ii ➥ Receiver decrypts using sender’s public key |
| iii ➥ Sender encrypts using his own public key |
| iv ➥ Sender encrypts using receiver’s public key |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q.70➡ | NET November 2021 In electronic mail, which of the following protocols allows the transfer of multimedia? |
| i ➥ IMAP |
| ii ➥ MIME |
| iii ➥ POP3 |
| iv ➥ SMTP |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q71➡ | NET November 2021 Which of the following statements are true? A. X.25 is connection-oriented network B. X.25 doesn’t support switched virtual circuits. C. Frame relay service provides acknowledgements. D. Frame relay service provides detection of transmission errors. Choose the correct answer from the options given below: |
| i ➥ A and D only |
| ii ➥ B and C only |
| iii ➥ B and D only |
| iv ➥ C and D only |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q.72➡ | NET November 2021 The address of class B host is to be split into subnets with 6-bit subnet number. What is the maximum number of subnets and the maximum number of hosts in each subnet? |
| i ➥ 62 subnets and 1022 hosts |
| ii ➥ 62 subnets and 262142 hosts |
| iii ➥ 64 subnets and 1024 hosts |
| iv ➥ 64 subnets and hosts 262142 |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | IP Address | Help-Line |
| Q.73➡ | NET November 2021 Which of the following statements are true? A.Frequency division multiplexing technique can be handled by digital circuits. B.Time division multiplexing technique can be handled by analog circuits C. Wavelength division multiplexing technique is used with optical fiber for combining two signals. D. Frequency division multiplexing technique can be applied when the bandwidth of a link is greater than the bandwidth of the signals to be transmitted. Choose the correct answer from the options given below: |
| i ➥ A and D only |
| ii ➥ B and D only |
| iii ➥ B and D only |
| iv ➥ C and D only |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q.74➡ | NET November 2020 Using ‘RSA’ public key cryptosystem, if p=3, q=11 and d=7, find the value of e and encrypt the number ’19’? |
| i ➥ 20,19 |
| ii ➥ 33,11 |
| iii ➥ 3,28 |
| iv ➥ 77,28 |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Network Security | Help-Line |
| Q.75➡ | NET November 2020 Given below are two statements: Statement I: In Caesar Cipher each letter of Plain text is replaced by another letter for encryption. Statement II: Diffie-Hellman algorithm is used for exchange of secret key. In the light of the above statements, choose the correct answer from the options given below: |
| i ➥ Both Statement I and Statement II are true |
| ii ➥ Both Statement I and Statement II are false |
| iii ➥ Statement I is correct but Statement II is false |
| iv ➥ Statement I is incorrect but Statement II is true |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Network Security | Help-Line |
| Q.76➡ | NET November 2020 Firewall is a device that filters access to the protected network from the outside network. Firewall can filter the packets on the basis of (A) Source IP address (B) Destination IP Address (C) TCP Source Port (D) UDP Source Port (E) TCP Destination Port Choose the correct answer from the options given below: |
| i ➥ (A), (B) and (C) only |
| ii ➥ (B) and (E) only |
| iii ➥(C) and (D) only |
| iv ➥(A), (B), (C), (D) and (E) only |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Firewall | Help-Line |
| Q.77➡ | NET November 2020 Match List I with List II 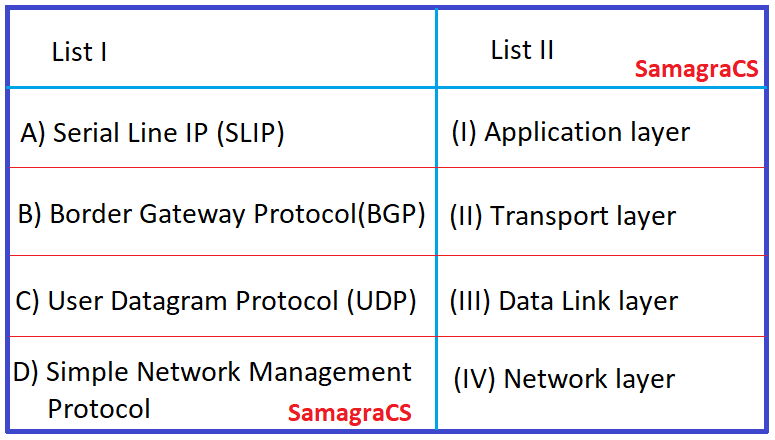 Choose the correct answer from the options given below: |
| i ➥ A-I, B-II, C-III, D-IV |
| ii ➥ A-III, B-IV, C-II, D-I |
| iii ➥ A-II, B-III, C-IV, D-I |
| iv ➥ A-III, B-I, C-IV, D-II |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Protocols | Help-Line |
| Q.78➡ | NET November 2020 Protocols in which the sender sends one frame and then waits for an acknowledgement before proceeding for the next frame are called as___. |
| i ➥ Simplex protocols |
| ii ➥ Unreserved simplex protocols |
| iii ➥ Simplex stop and wait protocols |
| iv ➥ Restricted simplex protocols |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Flow Control | Help-Line |
| Q.79➡ | NET November 2020 Post office protocol (POP) is a message access protocol which is used to extract messages for clients. In this regard, which of the following are true? A) POP has two modes, Delete mode and keep B) In Delete mode, mail is deleted from mailbox after each retrieval C) In Delete mode, mail is deleted from the mailbox before each retrieval. D) In keep mode, mail is deleted before retrieval. E) In keep mode, mail remains in the mailbox after retrieval. Choose the correct answer from the options given below: |
| i ➥ (A) and (B) only |
| ii ➥ (A), (D) and (E) only |
| iii ➥(A), (B), (C) and (D) only |
| iv ➥ (A), (B) and (E) only |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Protocols | Help-Line |
Q.80➡ | NET November 2020  |
| i ➥ Both Statement I and Statement II are true |
| ii ➥ Both Statement I and Statement II are false |
| iii ➥ Statement I is correct but Statement II is false |
| iv ➥ Statement I is incorrect but Statement II is true |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Protocols | Help-Line |
| Q81➡ | NET December 2019 Which of the following is not needed by an encryption algorithm used in Cryptography? A) KEY B) Message C) Ciphertext D) User details |
| i ➥ (C) only |
| ii ➥ (D) only |
| iii ➥ (B) , (C) and (D) only |
| iv ➥ (C) and (D) only |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Network Security | Help-Line |
| Q.82➡ | NET December 2019 A network with a bandwidth of 10 Mbps can pass only an average of 12,000 frames per minute with each frame carrying an average of 10,000 bits. What is the throughput of this network? |
| i ➥ 1,000,000 bps |
| ii ➥ 2,000,000 bps |
| iii ➥ 12,000,000 bps |
| iv ➥ 1,200,00,000 bps |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Flow Control | Help-Line |
| Q.83➡ | NET December 2019 Consider the following statements with respect to network security: (a) Message confidentiality means that the sender and the receiver expect privacy. (b) Message integrity means that the data must arrive at the receiver exactly as they were sent. (c) Message authentication means the receiver is ensured that the message is coming from the intended sender. Which of the statements is (are) correct? |
| i ➥ Only (a) and (b) |
| ii ➥ Only (a) and (c) |
| iii ➥ Only (b) and (c) |
| iv ➥ (a), (b) and (c) |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Network Security | Help-Line |
| Q.84➡ | NET December 2019 Piconet is a basic unit of a Bluetooth system consisting of _______ master node and up to ________ active salve nodes. |
| i ➥ one, five |
| ii ➥ one, seven |
| iii ➥ two, eight |
| iv ➥ one, eight |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Bluetooth | Help-Line |
| Q.85➡ | NET December 2019 The full form of ICANN is |
| i ➥ Internet Corporation for Assigned Names and Numbers |
| ii ➥ Internet Corporation for Assigned Names and Names |
| iii ➥ Institute of Corporation for Assigned Names and Numbers |
| iv ➥ Internet connection for Assigned Names and Numbers |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | ICANN | Help-Line |
| Q.86➡ | NET December 2019 Consider a subnet with 720 routers. If a three-level hierarchy is chosen, with eight clusters, each containing 9 regions of 10 routers, then the total number of entries in hierarchical table of each router is |
| i ➥ 25 |
| ii ➥ 27 |
| iii ➥ 53 |
| iv ➥ 72 |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Routing | Help-Line |
| Q.87➡ | NET December 2019 Consider the following statements : (a) Fiber optic cable is much lighter than copper cable. (b) Fiber optic cable is not affected by power surges or electromagnetic interference. (c) Optical transmission is inherently bidirectional. Which of the statements is (are) correct? |
| i ➥ Only (a) and (b) |
| ii ➥ Only (a) and (c) |
| iii ➥ Only (b) and (c) |
| iv ➥ (a), (b) and (c) |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Transmission Media | Help-Line |
| Q.88➡ | NET December 2019 Match List I with List II 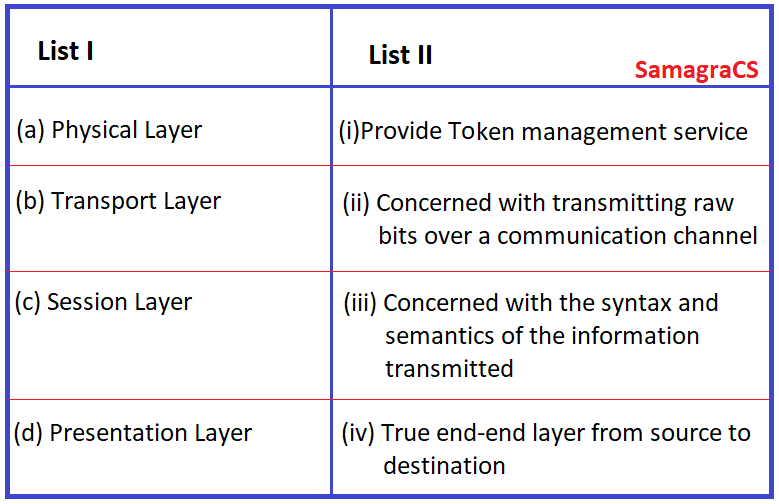 |
| i ➥ (a).(ii), (b).(iv), (c).(iii). (d).(i) |
| ii ➥ (a).(iv). (b).(iii). (c).(ii). (d).(i) |
| iii ➥ (a).(ii), (b).(iv), (c).(i), (d).(iii) |
| iv ➥ (a).(iv), (b).(ii), (c).(i), (d).(iii) |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | TCP/IP Model | Help-Line |
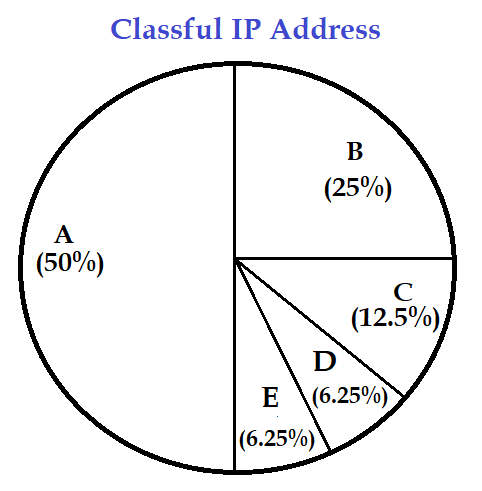
| Q.89➡ | NET June 2019 What percentage(%) of the IPv4, IP address space do all class C addresses consume? |
| i ➥ 12.5% |
| ii ➥ 25% |
| iii ➥ 37.5% |
| iv ➥ 50% |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | IP Address | Help-Line |
| Q.90➡ | NET June 2019 In the TCP/IP model, encryption and decryption are functions of __ layer |
| i ➥ Data link |
| ii ➥ Network |
| iii ➥ Transport |
| iv ➥ Application |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | TCP/IP Model | Help-Line |
| Q.91➡ | NET June 2019 What is the name of the protocol that allows a client to send a broadcast message with its MAC address and receive an IP address in reply? |
| i ➥ ARP |
| ii ➥ DNS |
| iii ➥ RARP |
| iv ➥ ICMP |
Show Answer With Best Explanation
| Q.92➡ | NET June 2019 The RSA encryption algorithm also works in reverse, that is, you can encrypt a message with the private key and decrypt it using the public key. This property is used in |
| i ➥ Intrusion detection systems |
| ii ➥ Digital signatures |
| iii ➥ Data Compression |
| iv ➥ Certification |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Network Security | Help-Line |
| Q.93➡ | NET June 2019 You are designed a link layer protocol for a link with bandwidth of 1 Gbps (109 bits/second) over a fiber link with length of 800 km. Assume the speed of light in this medium is 200000 km/second. What is the propagation delay in this link? |
| i ➥ 1 millisecond |
| ii ➥ 2 millisecond |
| iii ➥ 3 millisecond |
| iv ➥ 4 millisecond |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Delay | Help-Line |
| Q.94➡ | NET June 2019 Consider the following two statements with respect to IPv4 in computer networking: P: The loopback(IP) address is a member of class B network Q: The loopback(IP) address is used to send a packet from host to itself What can you say about the statements P and Q? |
| i ➥ P-True; Q-False |
| ii ➥ P-False; Q-True |
| iii ➥ P-True; Q-True |
| iv ➥ P-False; Q-false |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | IP Address | Help-Line |
Q.95➡ | NET June 2019 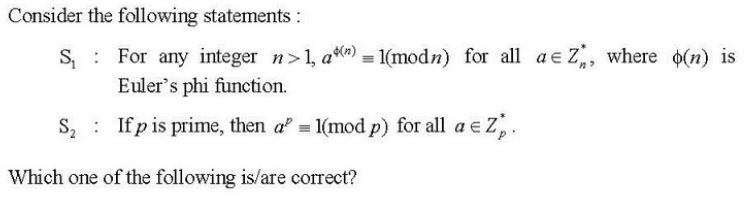 |
| i ➥ Only S1 |
| ii ➥ Only S2 |
| iii ➥ Both S1 and S2 |
| iv ➥ Neither S1 nor S2 |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Network Security | Help-Line |
| Q.96➡ | NET June 2019 You need 500 subnets, each with about 100 usable host addresses per subnet. What network mask will you assign using a class B network address? |
| i ➥ 255.255.255.252 |
| ii ➥ 255.255.255.128 |
| iii ➥ 255.255.255.0 |
| iv ➥ 255.255.254.0 |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | IP Address | Help-Line |
| Q.97➡ | NET June 2019 The ability to inject packets into the internet with false source address is known as : |
| i ➥ Man-in-the-Middle attack |
| ii ➥ IP phishing |
| iii ➥ IP sniffing |
| iv ➥ IP Spoofing |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Network Security | Help-Line |
Q.98➡ | NET June 2019 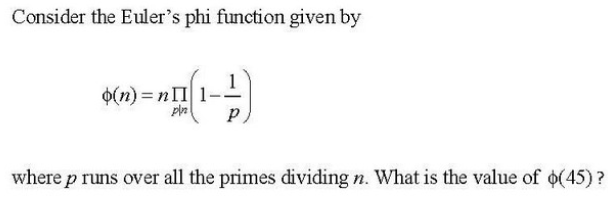 |
| i ➥ 3 |
| ii ➥ 12 |
| iii ➥ 6 |
| iv ➥ 24 |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Network Security | Help-Line |
| Q.99➡ | NET June 2019 A fully connected network topology is a topology in which there is a direct link between all pairs of nodes. Given a fully connected network with n nodes, the number of direct links as a function of n can be expressed as |
| i ➥ n(n+1)/2 |
| ii ➥ (n+1)/2 |
| iii ➥ n/2 |
| iv ➥ n(n-1)/2 |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Network Topology | Help-Line |
| Q.100➡ | NET June 2019 Which of the following statements is/are true with regard to various layers in the Internet stack? P: At the link layer, a packet of transmitted information is called a frame Q: At the network layer, a packet of transmitted information is called a segment |
| i ➥ P only |
| ii ➥ Q only |
| iii ➥ P and Q |
| iv ➥ Neither P nor Q |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | ISO OSI Model | Help-Line |
| Q.101➡ | NET December 2018 Consider ISO-OSI network architecture reference model. Session layer of this model offer Dialog control, token management and __ as services. |
| i ➥ Synchronization |
| ii ➥ Asynchronization |
| iii ➥ Errors |
| iv ➥ Flow control |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | ISO OSI Model | Help-Line |
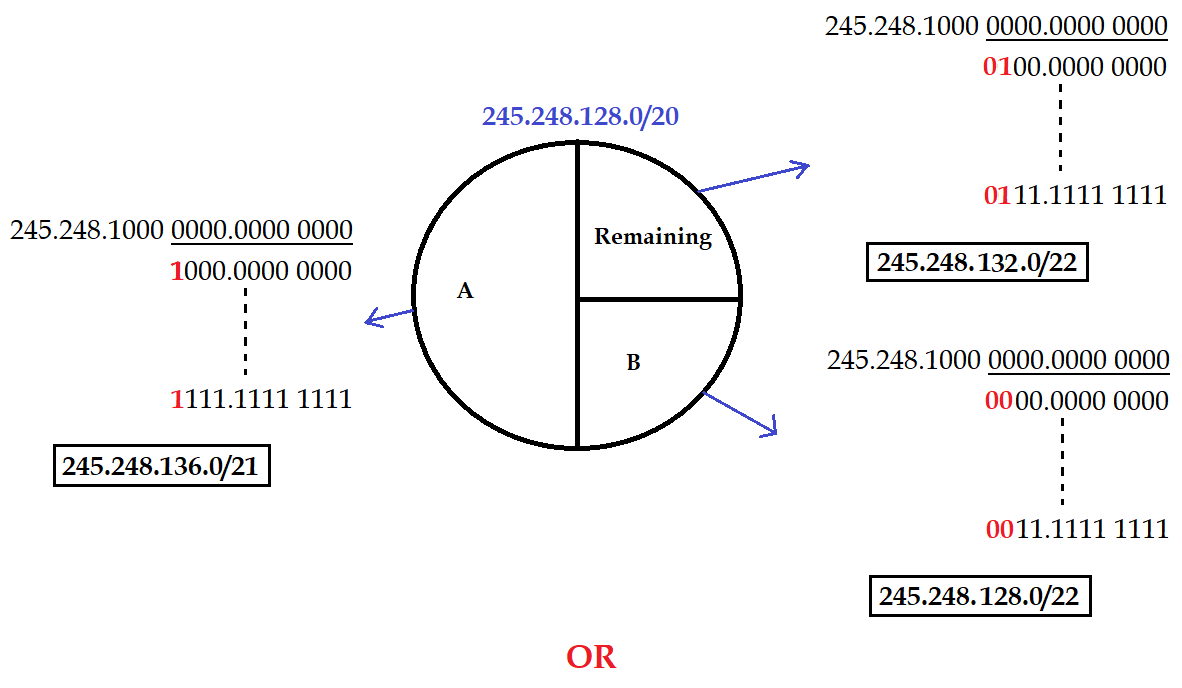
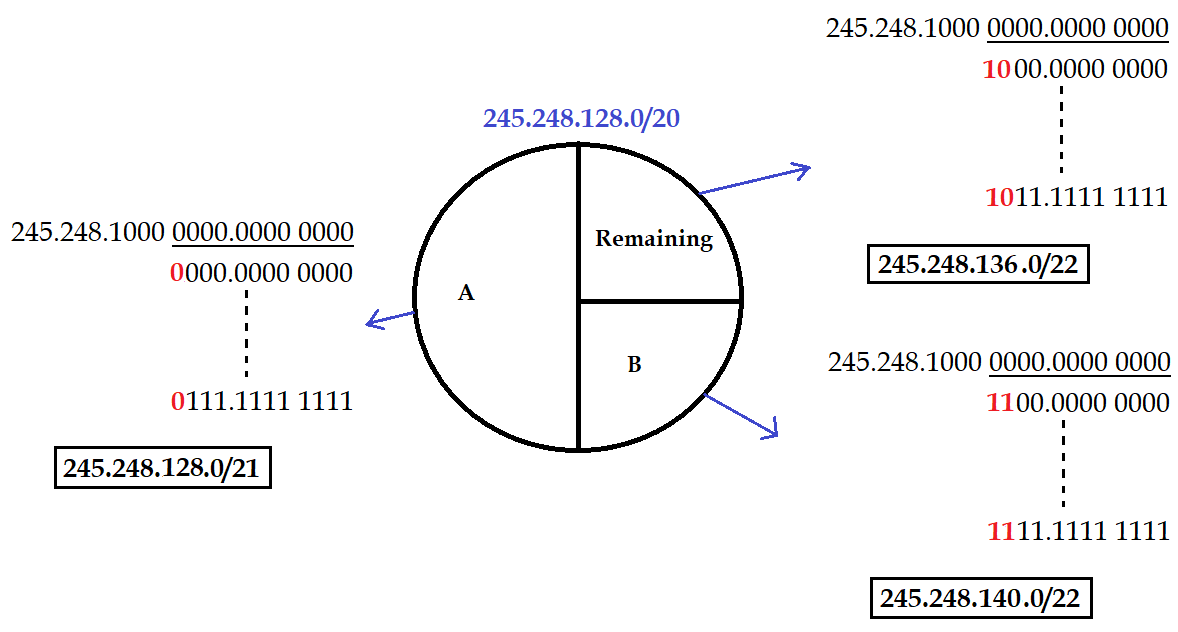
| Q.102➡ | NET December 2018 An internet service provider (ISP) has following chunk of CIDR-based IP addresses available with it: 245.248.128.0/20 . The ISP want to give half of this chunk of addresses to organization A and a quarter to Organization B while retaining the remaining with itself. Which of the following is a valid allocation of addresses to A and B? |
| i ➥ 245.248.132.0/22 and 245.248.132.0/21 |
| ii ➥ 245.248.136.0/21 and 245.248.128.0/22 |
| iii ➥ 245.248.136.0/24 and 245.248.132.0/21 |
| iv ➥ 245.248.128.0/21 and 245.248.128.0/22 |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | IP Address | Help-Line |
| Q.103➡ | NET December 2018 Which of the following statement/s is/are true? (i) Firewall can screen traffic going into or out of an organization. (ii) Virtual private networks cam simulate an old leased network to provide certain desirable properties. Choose the correct answer from the code given below: |
| i ➥ A) (i) only |
| ii ➥ B) Neither (i) nor(ii) |
| iii ➥ C) Both (i) and (ii) |
| iv ➥ D) (ii) only |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Firewall | Help-Line |
| Q.104➡ | NET December 2018 Identify the correct sequence in which the following packets are transmitted on the network by a host when a browser requests a web page from a remote server, assuming that the host has been restarted. |
| i ➥ HTTP GET request, DNS query, TCP SYN |
| ii ➥ DNS query, TCP SYN, HTTP GET request |
| iii ➥ TCP SYN, DNS query, HTTP GET request |
| iv ➥ DNS query, HTTP Get request, TCP SYN |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | TCP | Help-Line |
| Q.105➡ | NET December 2018 Consider the following two statements: S1: TCP handles both congestion and flow control S2: UDP handles congestion but not flow control Which of the following option is correct with respect to the above statements (S1) and (S2)? |
| i ➥ Both S1 and S2 are correct |
| ii ➥ Neither S1 nor S2 is correct |
| iii ➥ S1 is not correct but S2 is correct |
| iv ➥ S1 is correct but S2 is not correct |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | TCP UDP Protocol | Help-Line |
| Q.106➡ | NET December 2018 Match the following secret key algorithm (List 1) with the corresponding key lengths (List 2) and choose the correct answer from the code given below: 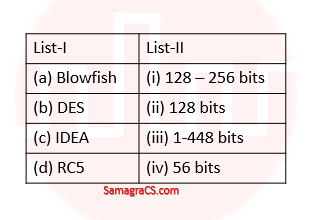 |
| i ➥ (a)-(ii),(b)-(iii), (c)- (iv), (d)-(i) |
| ii ➥ (a)-(iv),(b)-(iii), (c)- (ii), (d)-(i) |
| iii ➥ (a)-(iii),(b)-(iv), (c)- (ii), (d)-(i) |
| iv ➥ (a)-(iii),(b)-(iv), (c)- (i), (d)-(ii) |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Network Security | Help-Line |
| Q.107➡ | NET December 2018 The four byte IP Address consists of |
| i ➥ Neither network nor Host Address |
| ii ➥ Network Address |
| iii ➥ Both Network and Host Address |
| iv ➥ Host Address |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | IP Address | Help-Line |
| Q.108➡ | NET December 2018 Which of the following statement/s is/are true ? (i) windows XP supports both peer-peer and client-server networks. (ii) Windows XP implements Transport protocols as drivers that can be loaded and uploaded from the system dynamically. |
| i ➥ Both (i) and (ii) |
| ii ➥ Neither (i) nor (ii) |
| iii ➥ (ii) only |
| iv ➥ (i) only |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Miscellaneous Topic | Help-Line |
| Q.109➡ | NET December 2018 The host is connected to a department network which is a part of a university network. The university network, in turn, is part of the internet. The largest network, in which the Ethernet address of the host is unique, is |
| i ➥ The university network |
| ii ➥ The internet |
| iii ➥ The subnet to which the host belongs |
| iv ➥ The department network |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Networking Basic Concept | Help-Line |
| Q.110➡ | NET December 2018 Suppose that everyone in a group of N people wants to communicate secretly with (N-1) other people using symmetric key cryptographic system. The communication between any two persons should not be decodable by the others in the group. The number of keys required in the system as a whole to satisfy the confidentiality requirement is |
| i ➥ 2N |
| ii ➥ N(N-1) |
| iii ➥ N(N-1)/2 |
| iv ➥ (N-1) 2 |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Miscellaneous Topic | Help-Line |
| Q.111➡ | NET June 2018 A slotted ALOHA network transmits 200-bit frames using a shared channel with a 200 Kbps bandwidth. Find the throughput of the system, if the system (all stations put together) produces 250 frames per second: |
| i ➥ 49 |
| ii ➥ 368 |
| iii ➥ 149 |
| iv ➥ 151 |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Access Control | Help-Line |
| Q.112➡ | NET June 2018 The period of a signal is 100 ms. Its frequency is: |
| i ➥ 1003 Hertz |
| ii ➥ 10−2 KHz |
| iii ➥ 10−3 KHz |
| iv ➥ 105 Hertz |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Numerical | Help-Line |
| Q.113➡ | NET June 2018 The dotted-decimal notation of the following IPV4 address in binary notation is . 10000001 00001011 00001011 11101111 |
| i ➥ 111.56.45.239 |
| ii ➥ 129.11.10.238 |
| iii ➥ 129.11.11.239 |
| iv ➥ 111.56.11.239 |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | IP Address | Help-Line |
| Q.114➡ | NET June 2018 Which of the following statements are true ? (I) Advanced Mobile Phone System (AMPS) is a second generation cellular phone system. (II) IS – 95 is a second generation cellular phone system based on CDMA and DSSS. (III) The Third generation cellular phone system will provide universal personnel communication. |
| i ➥ (a) and (b) only |
| ii ➥ (b) and (c) only |
| iii ➥ (a), (b) and (c) |
| iv ➥ (a) and (c) only |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Cellular System | Help-Line |
| Q.115➡ | NET June 2018 Match the following symmetric block ciphers with corresponding block and key sizes : 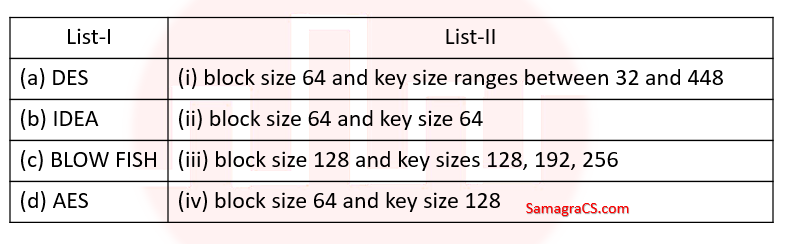 |
| i ➥ (a)-(iv), (b)-(ii), (c)-(i), (d)-(iii) |
| ii ➥ (a)-(ii), (b)-(iv), (c)-(i), (d)-(iii) |
| iii ➥ (a)-(ii), (b)-(iv), (c)-(iii), (d)-(i) |
| iv ➥ (a)-(iv), (b)-(ii), (c)-(iii), (d)-(i) |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Network Security | Help-Line |
| Q.116➡ | NET June 2018 Which of the following statements are true ? (a) Three broad categories of Networks are (i) Circuit Switched Networks (ii) Packet Switched Networks (iii) Message Switched Networks (b) Circuit Switched Network resources need not be reserved during the set up phase. (c) In packet switching there is no resource allocation for packets. Code: |
| i ➥ (a) and (b) only |
| ii ➥ (b) and (c) only |
| iii ➥ (a) and (c) only |
| iv ➥ (a), (b) and (C) |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Switching | Help-Line |
| Q.117➡ | NET June 2018 In Challenge-Response authentication the claimant__________ |
| i ➥ Proves that she knows the secret without revealing it |
| ii ➥ Proves that she doesn’t know the secret |
| iii ➥ Reveals the secret |
| iv ➥ Gives a challenge |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Network Security | Help-Line |
| Q.118➡ | NET June 2018 Decrypt the message “WTAAD” using the Caesar Cipher with key=15. |
| i ➥ LIPPS |
| ii ➥ HELLO |
| iii ➥ OLLEH |
| iv ➥ DAATW |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Network Security | Help-Line |
| Q.119➡ | NET June 2018 To guarantee correction of upto t errors, the minimum Hamming distance dmin in a block code must be__________. |
| i ➥ t+1 |
| ii ➥ t−2 |
| iii ➥ 2t−1 |
| iv ➥ 2t+1 |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Hamming Distance | Help-Line |
| Q.120➡ | NET June 2018 Encrypt the Message “HELLO MY DEARZ” using Transposition Cipher with  |
| i ➥ HLLEO YM AEDRZ |
| ii ➥ EHOLL ZYM RAED |
| iii ➥ ELHL MDOY AZER |
| iv ➥ ELHL DOMY ZAER |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Network Security | Help-Line |
| Q.121➡ | NET November 2017 Paper-2 Which of the following devices takes data sent from one network device and forwards it to the destination node based on MAC address ? |
| i ➥ Hub |
| ii ➥ Modem |
| iii ➥ Switch |
| iv ➥ Gateway |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Hardware Devices | Help-Line |
| Q.122➡ | NET November 2017 Paper-2 ___________do not take their decisions on measurements or estimates of the current traffic and topology. |
| i ➥ Static algorithms |
| ii ➥ Adaptive algorithms |
| iii ➥ Non – adaptive algorithms |
| iv ➥ Recursive algorithms |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Routing Algorithms | Help-Line |
| Q.123➡ | NET November 2017 Paper-2 The number of bits used for addressing in Gigabit Ethernet is___________. |
| i ➥ 32 bit |
| ii ➥ 48 bit |
| iii ➥ 64 bit |
| iv ➥ 128 bit |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Ethernet | Help-Line |
| Q.124➡ | NET November 2017 Paper-2 Which of the following layer of OSI Reference model is also called end-to-end layer? |
| i ➥ Network layer |
| ii ➥ Data layer |
| iii ➥ Session layer |
| iv ➥ Transport layer |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | ISO OSI Model | Help-Line |

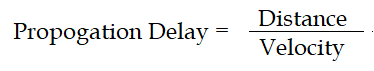

 = 10-3 second = 1 millisecond
= 10-3 second = 1 millisecond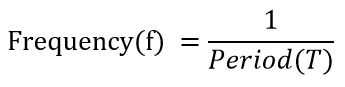
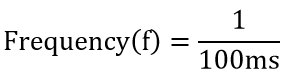
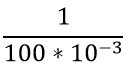 second
second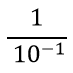 second
second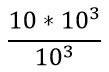 Hz
Hz