UGC NET Previous Years Question Solution Paper- Dec-2018
| Q1➡ Consider the language L given by L = { 2nk | k > 0 , and n is non − negative integer number } The minimum number of states of finite automaton which accept the language L is |
| A ➥ n |
| B ➥ n+1 |
| C ➥ 2n |
| D ➥ n (n + 1 )/2 |
Show Answer With Best Explanation
| Q2➡ | Computer Graphics In 3D Graphics, which of the following statements about perspective and parallel projection is/are true? P: In a perspective projection, the farthest an object is from the center of projection, the smaller it appears. Q: Parallel projection is equivalent to a perspective projection where the viewer is standing infinitely far away R: Perspective projections do not preserve straight lines. |
| i ➥ P and R only |
| ii ➥ P,Q and R |
| iii ➥ Q and R only |
| iv ➥ P and Q only |
Show Answer With Best Explanation
| Q3➡ Which of the following is true for semi-dynamic environment? |
| A ➥ The environment itself does not change with the passage of time but the agent’s performance score does. |
| B ➥ The environment change while the agent is deliberating. |
| C ➥ Even if the environment changes with the passage of time while deliberating, the performance score does not change. |
| D ➥ Environment and performance score, both change simultaneously. |
Show Answer With Best Explanation
| Q4➡ Consider the following method : int f(int m, int n, boolean x, boolean y) { int res=0; if(m<0) { res=n-m; } else if(x || y) { res= -1; if( n==m) { res =1; } } Else { res=n; } return res; } /*end of f */ |
| A ➥ (3,2) |
| B ➥ (3,4) |
| C ➥ (4,3) |
| D ➥ (2,3) |
Show Answer With Best Explanation
Q5➡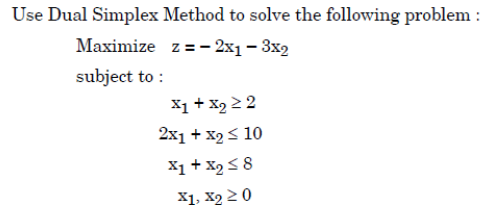 |
| A ➥ x1 =2, x2 =0 and z = -4 |
| B ➥ x1 =2, x2 =6 and z = -22 |
| C ➥ x1 =0, x2 =2 and z = -6 |
| D ➥ x1 =6, x2 =2 and z = -18 |
Show Answer With Best Explanation
| Q6➡ If the frame buffer has 10-bits per pixel and 8-bits are allocated for each of the R,G and B components then what would be the size of the color lookup table(LUT) |
| A ➥ (210 +211 ) bytes |
| B ➥ (210 + 224 ) bytes |
| C ➥ (210 +28 ) bytes |
| D ➥ (28 + 29 ) bytes |
Show Answer With Best Explanation
| Q7➡ Consider the following problems: (i) Whether a finite automaton halts on all inputs? (ii) Whether a given Context Free Language is Regular? (iii) Whether a Turing Machine computes the product of two numbers? Which one of the following is correct? |
| A ➥ Only (i) and (iii) are undecidable problems |
| B ➥ (i), (ii) and (iii) are undecidable problems |
| C ➥ Only (i) and (ii) are undecidable problems |
| D ➥ Only (ii) and (iii) are undecidable problems |
Show Answer With Best Explanation
| Q8➡ Consider the following language: L1 = { an+m bn am | n, m ≥ 0 } L2 = { an+m bn+m an+m |n, m ≥ 0 } Which one of the following is correct? |
| A ➥ Only L1 is Context Free Language |
| B ➥ Both L1 and L2 are Context Free Language |
| C ➥ Both L 1 and L 2 are not Context Free Language |
| D ➥ Only L2 is Context Free Language |
Show Answer With Best Explanation
Q19➡ | Computer Graphics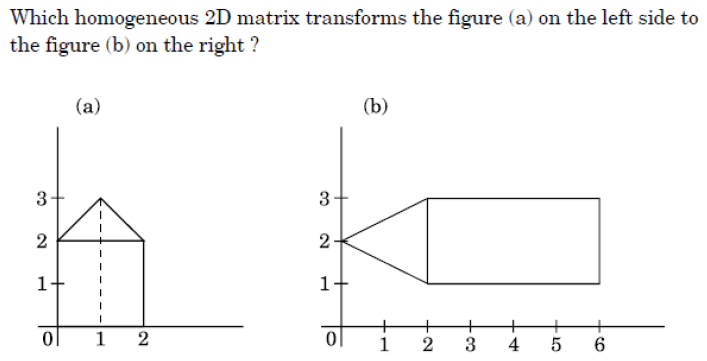 |
i ➥ 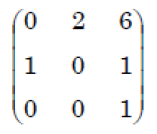 |
ii ➥ 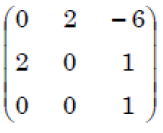 |
iii ➥ 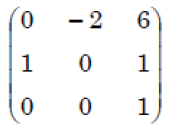 |
iv ➥ 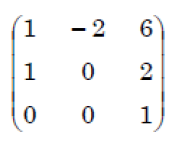 |
Show Answer With Best Explanation
Q20➡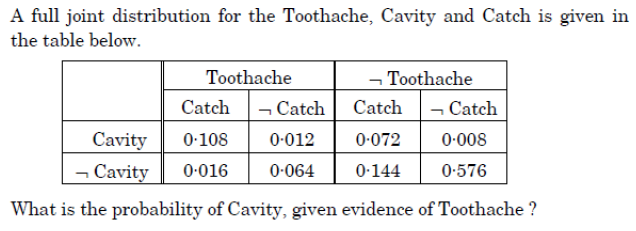 |
| A ➥ < 0.6, 0.8 > |
| B ➥ < 0.4, 0.8 > |
| C ➥ < 0.2, 0.8 > |
| D ➥ < 0.6, 0.4 > |
Show Answer With Best Explanation
Q11➡ |
| A ➥ (a)-(iv), (b)-(iii), (c)-(ii), (d)-(i) |
| B ➥ (a)-(iii), (b)-(iv), (c)-(ii), (d)-(i) |
| C ➥ (a)-(ii), (b)-(i),(c)-(iii), (d)-(iv) |
| D ➥ (a)-(i), (b)-(ii), (c)-(iii), (d)-(iv) |
Show Answer With Best Explanation
| Q12➡ The number of substrings that can be formed from string given by a d e f b g h n m p is |
| A ➥ 56 |
| B ➥ 10 |
| C ➥ 55 |
| D ➥ 45 |
Show Answer With Best Explanation
| Q13➡ A survey has been conducted on methods of commuter travel. Each respondent was asked to check Bus, Train or Automobile as a major methods of travelling to work. More than one answer was permitted. The results reported were as follows : Bus 30 people; Train 35 people; Automobile 100 people; Bus and Train 15 people; Bus and Automobile 15 people; Train and Automobile 20 people; and all the three methods 5 people. How many people complete the survey form? |
| A ➥ 120 |
| B ➥ 160 |
| C ➥ 165 |
| D ➥ 115 |
Show Answer With Best Explanation
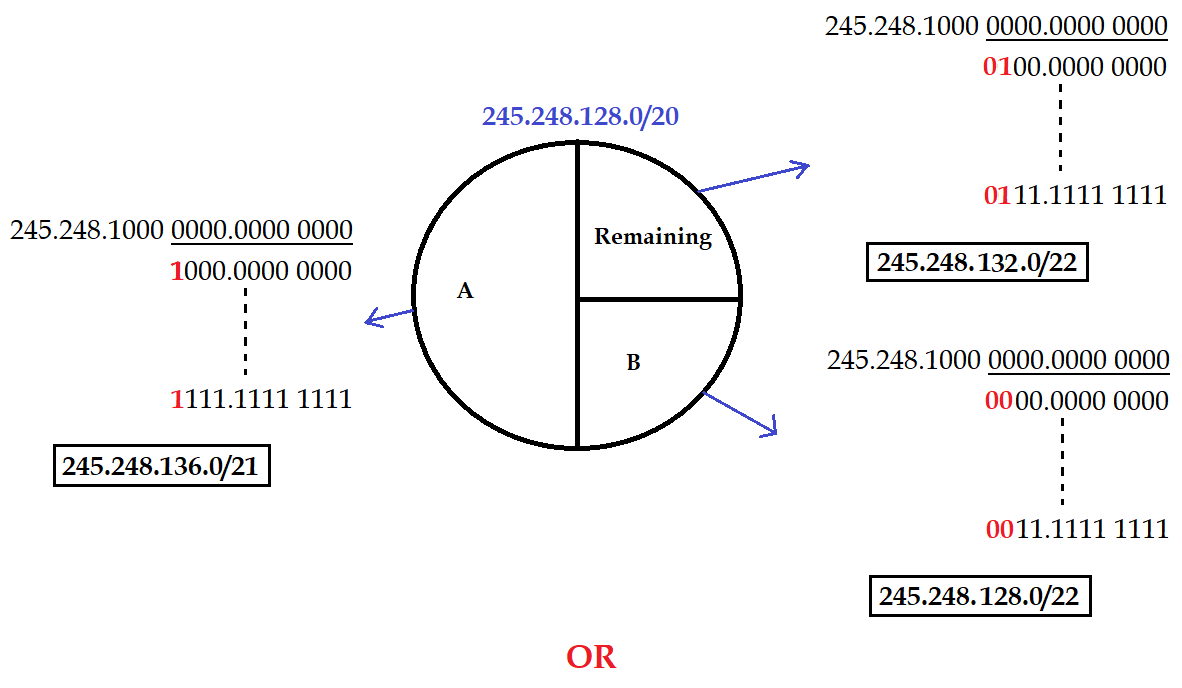
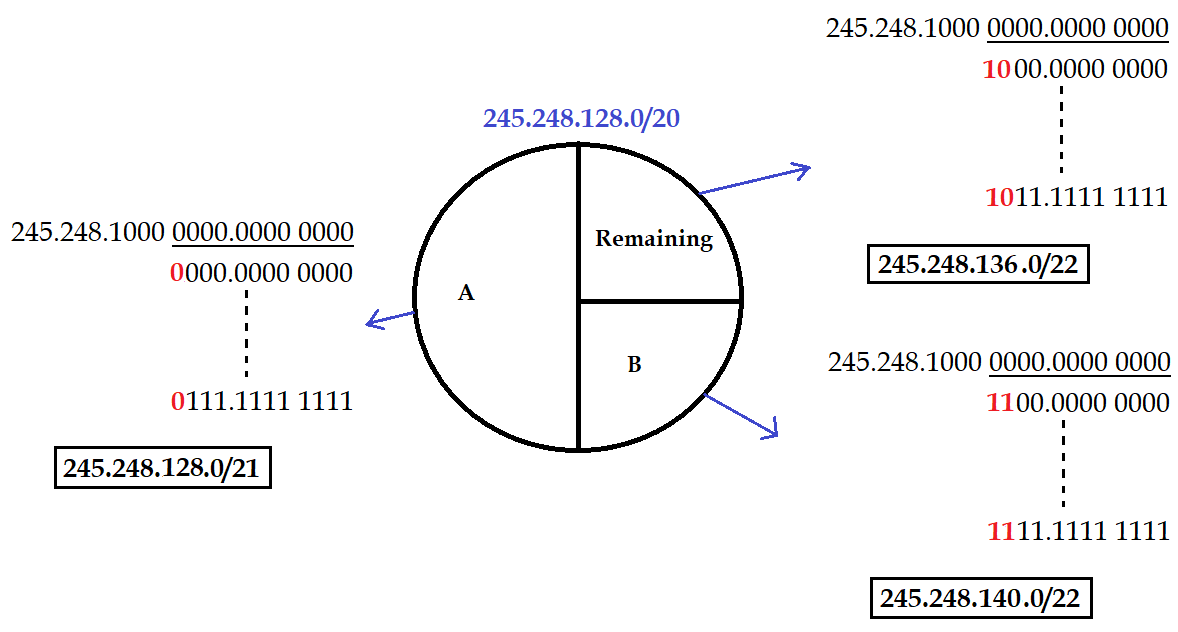
| Question 14➡ | Computer Network An internet service provider (ISP) has following chunk of CIDR-based IP addresses available with it: 245.248.128.0/20 . The ISP want to give half of this chunk of addresses to organization A and a quarter to Organization B while retaining the remaining with itself. Which of the following is a valid allocation of addresses to A and B? |
| i ➥ 245.248.132.0/22 and 245.248.132.0/21 |
| ii ➥ 245.248.136.0/21 and 245.248.128.0/22 |
| iii ➥ 245.248.136.0/24 and 245.248.132.0/21 |
| iv ➥ 245.248.128.0/21 and 245.248.128.0/22 |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | IP Address | Help-Line |
| Q15➡ Suppose P,Q and R are co-operating processes satisfying Mutual Exclusion condition. Then if the process Q is executing in its critical section then |
| A ➥ Both ‘P’ and ‘R’ executes in critical section |
| B ➥ ‘P’ executes in critical section |
| C ➥ ‘R’ executes in critical section |
| D ➥ Neither ‘P’ nor ‘Q’ executes in their critical section |
Show Answer With Best Explanation
| Q16➡ Suppose for a process P, reference to pages in order are 1, 2, 4, 5,2,1,2,4. Assume that main memory can accommodate 3 pages and the main memory has already pages 1 and 2 in the order 1 – first, 2- second. At this moment, assume FIFO Page Replacement Algorithm is used then the number of page faults that occur to complete the execution of process P is |
| A ➥ 5 |
| B ➥ 6 |
| C ➥ 3 |
| D ➥ 4 |
Show Answer With Best Explanation
| Q17➡ A process residing in main memory and ready and waiting for execution, is kept on |
| A ➥ Wait Queue |
| B ➥ Job Queue |
| C ➥ Execution Queue |
| D ➥ Ready Queue |
Show Answer With Best Explanation
| Q18➡ Which of the following statements is/are false? P: The clean-room strategy to software engineering is based on the incremental software process model. Q: The clean-room strategy to software engineering is one of the ways to overcome “unconscious” copying of copyrighted code. Choose the correct answer from the code given below: |
| A ➥ Neither P and Q |
| B ➥ Both P and Q |
| C ➥ Q only |
| D ➥ P only |
Show Answer With Best Explanation
| Q19➡ Which of the following statements is/are true? P: Software Re-engineering is preferable for software products having high failure rates, having poor design and/or having poor code structure Q: Software Reverse Engineering is the process of analyzing software with the objective of recovering its design and requirement specification. |
| A ➥ Both P and Q |
| B ➥ Q only |
| C ➥ P only |
| D ➥ Neither P nor Q |
Show Answer With Best Explanation
Q20➡ |
| A ➥ (a)-(iv),(b)-(iii), (c)- (ii), (d)-(i) |
| B ➥ (a)-(iii),(b)-(iv), (c)- (i), (d)-(ii) |
| C ➥ (a)-(ii),(b)-(iii), (c)- (iv), (d)-(i) |
| D ➥ (a)-(iii),(b)-(iv), (c)- (ii), (d)-(i) |
Show Answer With Best Explanation
| Question 21➡ | Computer Network Consider the following two statements: S1: TCP handles both congestion and flow control S2: UDP handles congestion but not flow control Which of the following option is correct with respect to the above statements (S1) and (S2)? |
| i ➥ Both S1 and S2 are correct |
| ii ➥ Neither S1 nor S2 is correct |
| iii ➥ S1 is not correct but S2 is correct |
| iv ➥ S1 is correct but S2 is not correct |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | TCP UDP Protocol | Help-Line |
| Q22➡ Consider the statements below : “ There is a country that borders both India and Nepal. “ Which of the following represents the above sentence correctly ? |
| A ➥ ∃c Country(c) ∧ Border(c, India) ∧ Border(c, Nepal) |
| B ➥ ∃c Country(c) ⇒ [ Border(c, India) ∧ Border(c, Nepal)] |
| C ➥ ∃c Border(Country(c), India ∧ Nepal) |
| D ➥ [∃c Country(c)] ⇒ [Border(c,India) ∧ Border(c, Nepal)] |
Show Answer With Best Explanation
| Q23➡ Consider R to be any regular language and L1 .L2 be any two context-free languages Which one of the following is correct ? |
| A ➥ L1 ⋂ L2 is context free |
| B ➥ L1 is context free |
| C ➥ L1 − R is context free |
| D ➥ (L1 ⋃ L2 )‘ − R is context free |
Show Answer With Best Explanation
Q24➡ |
| A ➥ (a)-(i), (b)-(ii), (c) -(iii), (d)-(iv) |
| B ➥ (a)-(iv), (b)-(iii), (c) -(ii), (d)-(i) |
| C ➥ (a)-(i), (b)-(iv), (c) -(iii), (d)-(ii) |
| D ➥ (a)-(iv), (b)-(i), (c) -(ii), (d)-(iii) |
Show Answer With Best Explanation
| Q25➡ Which of the following is not one of the principles of agile software development method ? |
| A ➥ Incremental delivery |
| B ➥ Customer involvement |
| C ➥ Embrace change |
| D ➥ Following the plan |
Show Answer With Best Explanation
| Q26➡ Consider a system with 2 level cache. Access times of Level 1, Level 2 cache and main memory are 0.5 ns, 5 ns and 100 ns respectively. The hit rates of Level1 and Level2 caches are 0.7 and 0.8 respectively. What is the average access time of the system ignoring the search time within cache? |
| A ➥ 24.35 ns |
| B ➥ 35.20 ns |
| C ➥ 7.55 ns |
| D ➥ 20.75 ns |
Show Answer With Best Explanation
| Q27➡ A Computer uses a memory unit with 256K word of 32 bits each. A binary instruction code is stored in one word of memory. The instruction has four parts: an indirect bit, an operation code and a register code part to specify one of 64 registers and an address part. How many bits are there in operation code, the register code part and the address part? |
| A ➥ 6,7,18 |
| B ➥ 7,6,18 |
| C ➥ 7,7,18 |
| D ➥ 18,7,7 |
Show Answer With Best Explanation
| Q28➡ An agent can improve its performance by |
| A ➥ Responding |
| B ➥ Observing |
| C ➥ Perceiving |
| D ➥ Learning |
Show Answer With Best Explanation
| Q29➡ In PERT/CPM , the merge event represents___________ of two or more events. |
| A ➥ Completion |
| B ➥ Splitting |
| C ➥ Joining |
| D ➥ Beginning |
Show Answer With Best Explanation
| Q30➡ Suppose a cloud contains software stack such as Operating system, Application software, etc. This model is referred as ______ model. |
| A ➥ IaaS |
| B ➥ PaaS |
| C ➥ SaaS |
| D ➥ MaaS |
Show Answer With Best Explanation
| Q31➡ In computers, Subtraction is generally carried out by. |
| A ➥ 9’s complement |
| B ➥ 10’s complement |
| C ➥ 1’s complement |
| D ➥ 2’s complement |
Show Answer With Best Explanation
| Q32➡ In Linux operating system environment _________ command is used to print a file. |
| A ➥ ptr |
| B ➥ print |
| C ➥ pr |
| D ➥ lpr |
Show Answer With Best Explanation
| Q33➡ Which of the following HTML5 codes will affect the horizontal as well as vertical alignment of the table content? |
| A ➥ < td style = “horizontal − align : center; vertical − align:middle;”> BASH </ td > |
| B ➥ < td align = “middle” valign = ” center” > BASH < /td > |
| C ➥ < td style = ” text − align : center; vertical − align : middle; ” > BASH < / td > |
| D ➥ < td halign = ” middle” valign = ” center” > BASH < / td > |
Show Answer With Best Explanation
| Q34➡ Dirty bit is used to show the |
| A ➥ Page with corrupted data |
| B ➥ Page that is modified after being loaded into cache memory |
| C ➥ Page with low frequency occurrence |
| D ➥ Wrong page |
Show Answer With Best Explanation
| Question 35➡ | Computer Network Identify the correct sequence in which the following packets are transmitted on the network by a host when a browser requests a web page from a remote server, assuming that the host has been restarted. |
| i ➥ HTTP GET request, DNS query, TCP SYN |
| ii ➥ DNS query, TCP SYN, HTTP GET request |
| iii ➥ TCP SYN, DNS query, HTTP GET request |
| iv ➥ DNS query, HTTP Get request, TCP SYN |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | TCP | Help-Line |
| Q36➡ Consider the following postfix expression with single digit operands : 6 2 3 * / 4 2 * + 6 8 * – The top two elements of the stack after second * is evaluated, are : |
| A ➥ 6, 2 |
| B ➥ 8, 2 |
| C ➥ 8, 1 |
| D ➥ 6, 3 |
Show Answer With Best Explanation
| Q37➡ _______ command is used to remove a relation from an SQL database |
| A ➥ Remove table |
| B ➥ Update table |
| C ➥ Drop table |
| D ➥ Delete table |
Show Answer With Best Explanation
| Q38➡ If a graph (G) has no loops or parallel edges and if the number of vertices(n) in the graph is n≥3, then the graph G is Hamiltonian if. (i) deg(v) ≥n/3 for each vertex v (ii) deg(v) + deg(w) ≥ n whenever v and w are not connected by an edge. (iii) E (G) ≥ 1/3 (n − 1 )(n − 2 ) + 2 |
| A ➥ ii) and (iii) only |
| B ➥ (ii) only |
| C ➥ (iii) only |
| D ➥ (i) and (iii) only |
Show Answer With Best Explanation
| Q39➡ Consider the following boolean equations : (i). wx + w(x + y) + x(x + y)=x+wy (ii). (wx’(y+xz’)+w’x’)y=x’y What can you say about the above equations ? |
| A ➥ (i) is false and (ii) is true |
| B ➥ (i) is true and (ii) is false |
| C ➥ Both (i) and (ii) are false |
| D ➥ Both (i) and (ii) are true |
Show Answer With Best Explanation
| Q40➡ Data Scrubbing is ? |
| A ➥ A process to upgrade the quality of data before it is moved into a data warehouse |
| B ➥ A process to reject data from the data warehouse and to create necessary indexes. |
| C ➥ A process to lead the data in the warehouse and to create the necessary indexes. |
| D ➥ A process to upgrade the quality of data after it is moved into a data warehouse |
Show Answer With Best Explanation
| Q41➡ Consider a disk pack with 32 surfaces, 64 tracks and 512 sectors per pack. 256 bytes of data are stored in a bit serial manner in a sector. The number of bits required to specify a particular sector in the disk is |
| A ➥ 18 |
| B ➥ 22 |
| C ➥ 19 |
| D ➥ 20 |
Show Answer With Best Explanation
| Q42➡ Consider the following statements S1: A heuristic is admissible if it never overestimates the cost to reach the goal S2: A heuristic is monotonous if it follows triangle inequality property. Which one of the following is true referencing the above statements? |
| A ➥ Both the statements S1 and S2 are true. |
| B ➥ Neither of the statements S1 and S2 are true |
| C ➥ Statement S1 is false but statement S2 is true. |
| D ➥ Statement S1 is true but statement S2 is false. |
Show Answer With Best Explanation
| Q43➡ The grammar S ⟶ (S) | SS | ∈ is not suitable for predictive parsing because the grammar is |
| A ➥ Ambiguous |
| B ➥ Left Recursive |
| C ➥ Right Recursive |
| D ➥ An Operator Grammar |
Show Answer With Best Explanation
| Q44➡ Consider the following two languages: L 1 = {x | for some y with | y| = 2 |x| ,xy∈ L and L is regular language} L 2 = { x | for some y such that |x| = |y|, xy∈ L and L is regular language} Which one of the following is correct? |
| A ➥ Both L 1 and L 2 are regular languages |
| B ➥ Both L 1 and L 2 are not regular languages |
| C ➥ Only L 2 is regular language |
| D ➥ Only L 1 is regular language |
Show Answer With Best Explanation
| Q45➡ Consider the following statements : (i) Auto increment addressing mode is useful in creating self-relocating code. (ii) If auto addressing mode is included in an instruction set architecture, then an additional ALU is required for effective address calculation. (iii) In auto increment addressing mode, the amount of increment depends on the size of the data item accessed. Which of the above statements is/are true ? Choose the Correct answer from the code given below: Code: |
| A ➥ (ii) and (iii) only |
| B ➥ (i) and (ii) only |
| C ➥ iii) only |
| D ➥ (ii) only |
Show Answer With Best Explanation
| Q46➡ Consider the vocabulary with only four propositions A,B,C and D. How many models are there for the following sentence? ( ⌐ A ∨ ⌐ B ∨ ⌐ C ∨ ⌐ D) |
| A ➥ 7 |
| B ➥ 8 |
| C ➥ 16 |
| D ➥ 15 |
Show Answer With Best Explanation
| Q47➡ Consider the following statements related to AND-OR Search algorithm. S 1 : A solution is a sub tree that has a goal node at every leaf. S 2 : OR nodes are analogous to the branching in a deterministic environment S 3 : AND nodes are analogous to the branching in a non-deterministic environment. Which one of the following is true referencing the above statements? Choose the correct answer from the code given below: |
| A ➥ S1- True, S2- True, S3- True |
| B ➥ S1- False, S2- True, S3- True |
| C ➥ S1- True, S2- True, S3- False |
| D ➥ S1- False, S2- True, S3- False |
Show Answer With Best Explanation
| Question 48➡ | Computer Network Consider ISO-OSI network architecture reference model. Session layer of this model offer Dialog control, token management and __ as services. |
| i ➥ Synchronization |
| ii ➥ Asynchronization |
| iii ➥ Errors |
| iv ➥ Flow control |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | ISO OSI Model | Help-Line |
Q49➡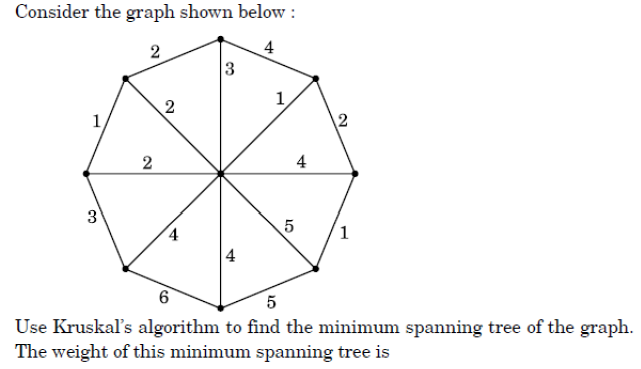 |
| A ➥ 17 |
| B ➥ 13 |
| C ➥ 16 |
| D ➥ 14 |
Show Answer With Best Explanation
| Q50➡ | Computer Graphics In 3D Graphics, which of the following statement/s is/are true ? P: Back-face culling is an example of an image-precision visible-surface determination. Q: Z-Buffer is a 16-bit, 32-bit, or 64-bit field associated with each pixel in a frame buffer that can be used to determine the visible surface at each pixel. |
| i ➥ P only |
| ii ➥ Neither P nor Q |
| iii ➥ P and Q |
| iv ➥ Q only |
Show Answer With Best Explanation
| Q51➡ Consider the following recursive Java function f that takes two long arguments and returns a float value : public static float f(long m, long n) { float result = (float) m / (float) n; if (m < 0 || n < 0) return 0⋅0f; else result += f(m2, n3); result result; } Which of the following integers best approximates the value of f(2,3) ? |
| A ➥ 0 |
| B ➥ 2 |
| C ➥ 1 |
| D ➥ 3 |
Show Answer With Best Explanation
| Q52➡ The solution of recurrence relation : T(n)=2T(sqrt(n))+lg(n) is . |
| A ➥ O(lg (n) lg(lg(n))) |
| B ➥ O(lg (n)) |
| C ➥ O(lg (n) lg(n)) |
| D ➥ O(n lg (n)) |
Show Answer With Best Explanation
| Q53➡ The Boolean expression A’⋅B+A.B’+A.B is equivalent to |
| A ➥ (A+B)’ |
| B ➥ A.B |
| C ➥ A+B |
| D ➥ A’.B |
Show Answer With Best Explanation
| Q54➡ The clustering index is defined on the fields which are of type |
| A ➥ non-key and ordering |
| B ➥ key and non-ordering |
| C ➥ key and ordering |
| D ➥ non-key and non-ordering |
Show Answer With Best Explanation
| Q55➡ ___________System call creates new process in Unix. |
| A ➥ Create new |
| B ➥ Fork |
| C ➥ Fork new |
| D ➥ Create |
Show Answer With Best Explanation
| Q56➡ Software coupling involves dependencies among pieces of software called modules. Which of the following are correct statements with respect to module coupling? P: Common Coupling occurs when two modules share the same global data Q: control Coupling occur when modules share a composite data structure and use only part of it. R: Content coupling occurs when one module modifies or relies on the internal working of another module. Choose the correct answer from the code given below: |
| A ➥ P and R only |
| B ➥ Q and R only |
| C ➥ P and Q only |
| D ➥ All of P,Q and R |
Show Answer With Best Explanation
| Q57➡ Suppose a system has 12 instances of some resources with n processes competing for that resource. Each process may require 4 instances of the resource. The maximum value of n for which the system never enters into deadlock is |
| A ➥ 6 |
| B ➥ 5 |
| C ➥ 4 |
| D ➥ 3 |
Show Answer With Best Explanation
| Q58➡ Consider the following Grammar G : S ➝ A | B A➝ a | c B➝ b | c Where {S,A,B} is the set of non-terminals, {a,b,c} is the set of terminals. Which of the following statement(s) is/are correct ? S 1 : LR(1) can parse all strings that are generated using grammar G. S 2 : LL(1) can parse all strings that are generated using grammar G. |
| A ➥ Only S 1 |
| B ➥ Only S 2 |
| C ➥ Both S 1 and S 2 |
| D ➥ Neither S 1 nor S 2 |
Show Answer With Best Explanation
| Q59➡ The Software Requirement Specification(SRS) is said to be _ if and only if no subset of individual requirements described in it conflict with each other. |
| A ➥ Consistent |
| B ➥ Verifiable |
| C ➥ Correct |
| D ➥ Unambiguous |
Show Answer With Best Explanation
| Q60➡ Software products need perfective maintenance for which of the following reasons? |
| A ➥ To support the new features that users want it to support |
| B ➥ To overcome wear and tear caused by the repeated use of the software. |
| C ➥ When the customers need the product to run on new platforms |
| D ➥ To rectify bugs observed while the system is in use. |
Show Answer With Best Explanation
| Q61➡ In mathematical logic, which of the following are statements ? (i) There will be snow in January. (ii) What is the time now ? (iii) Today is Sunday. (iv) You must study Discrete Mathematics. Choose the correct answer from the code given below: Code: |
| A ➥ (ii) and (iv) |
| B ➥ (i) and (ii) |
| C ➥ (iii) and (iv) |
| D ➥ (i) and (iii) |
Show Answer With Best Explanation
| Question 62➡ | Computer Network Which of the following statement/s is/are true? (i) Firewall can screen traffic going into or out of an organization. (ii) Virtual private networks cam simulate an old leased network to provide certain desirable properties. Choose the correct answer from the code given below: |
| i ➥ A) (i) only |
| ii ➥ B) Neither (i) nor(ii) |
| iii ➥ C) Both (i) and (ii) |
| iv ➥ D) (ii) only |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Firewall | Help-Line |
| Q63➡ The third generation mobile phone are digital and based on. |
| A ➥ Broadband CDMA |
| B ➥ CDMA |
| C ➥ D-AMPS |
| D ➥ AMPS |
Show Answer With Best Explanation
| Q64➡ Consider the following set of processes and the length of CPU burst time given in milliseconds: 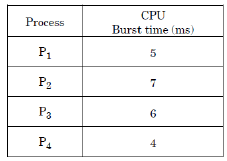 Assume that processes being scheduled with Round-Robin Scheduling Algorithm with Time Quantum 4ms. Then The waiting time for P4 is _ ms. |
| A ➥ 6 |
| B ➥ 12 |
| C ➥ 4 |
| D ➥ 0 |
Show Answer With Best Explanation
| Q65➡ Consider the following sequence of two transactions on a bank account(A) with initial balance 20,000 that transfers 5,000 to another account (B) and then apply 10% interest. (i) T1 start (ii) T1 A old=20000 new 15,000 (iii) T1 B old=12000 new=17000 (iv) T1 commit (v) T2 start (vi) T2 A old=15000 new=16500 (vii) T2 commit Suppose the database system crashes out just before log record (vii) is written. When the system is restricted, which one statement is true of the recovery process ? |
| A ➥ We must undo log record (vi) to set A to 16,500 and then redo log record (ii) and (iii). |
| B ➥ We need not redo records (ii) and (iii) because transaction T1 has committed. |
| C ➥ We must redo log record (vi) to set A to 16,500. |
| D ➥ We can apply redo and undo operation in arbitrary order because they are idempotent. |
Show Answer With Best Explanation
| Q66➡ Which of the following statements are true ? (i) Every logic network is equivalent to one using just NAND gates or just NOR gates. (ii) Boolean expressions and logic networks correspond to labelled acyclic digraphs. (iii) No two Boolean algebras with n atoms are isomorphic. (iv) Non-zero elements of finite Boolean algebras are not uniquely expressible as joins of atoms. Choose the correct answer from the code given below: CODE: |
| A ➥ (ii), (iii) and (iv) only |
| B ➥ (i), (ii) and (iii) only |
| C ➥ (i) and (iv) only |
| D ➥ (i) and (ii) only |
Show Answer With Best Explanation
| Q67➡ Which of the following statement/s is/are true ? (i) Facebook has the world’s largest Hadoop cluster. (ii) Hadoop 2.0 allows live stream processing of real time data |
| A ➥ Both (i) and (ii) |
| B ➥ (i) only |
| C ➥ (ii) only |
| D ➥ Neither (i) nor (ii) |
Show Answer With Best Explanation
| Q68➡ Consider the following pseudo-code fragment, where m is a non-negative integer that has been initialized: p=0; k=0; while(k < m) p = p + 2k; k=k+1; end while Which of the following is a loop invariant for the while statement? (Note: a loop variant for a while statement is an assertion that is true each time guard is evaluated during the execution of the while statement). |
| A ➥ p = 2k − 1 and 0≤k≤m |
| B ➥ p = 2k+1 − 1 and 0≤k≤m |
| C ➥ p = 2k+1 − 1 and 0≤k < m |
| D ➥ p = 2k − 1 and 0≤k < m |
Show Answer With Best Explanation
| Q35➡ | Computer Network The host is connected to a department network which is a part of a university network. The university network, in turn, is part of the internet. The largest network, in which the Ethernet address of the host is unique, is |
| i ➥ The university network |
| ii ➥ The internet |
| iii ➥ The subnet to which the host belongs |
| iv ➥ The department network |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Networking Basic Concept | Help-Line |
Q70➡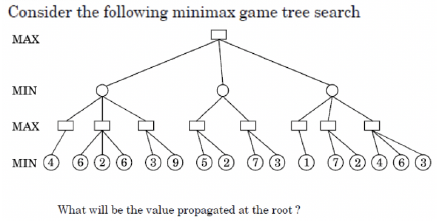 |
| A ➥ 6 |
| B ➥ 5 |
| C ➥ 4 |
| D ➥ 3 |
Show Answer With Best Explanation
| Q71➡ The elements 42, 25, 30, 40, 22, 35, 26 are inserted one by one in the given order into a max-heap. The resultant max-heap is stored in an array implementation as |
| A ➥ <42, 40, 35, 25, 22, 30, 26> |
| B ➥ <42, 35, 40, 22, 25, 30, 26> |
| C ➥ <42, 35, 40, 22, 25, 26, 30> |
| D ➥ <42, 40, 35, 25, 22, 26, 30> |
Show Answer With Best Explanation
Q72➡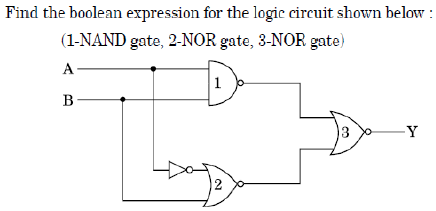 |
| A ➥ AB’ |
| B ➥ A’B’ |
| C ➥ AB |
| D ➥ A’B’ |
Show Answer With Best Explanation
Q73➡ Which statements are true ? P: For a line with slope m>1, we should change the outer loop in line (4) to be over y. Q: Lines (10) and (12) update the decision variable d through an incremental evaluation of the line equation f. R: The algorithm fails if d is ever 0. Choose the correct answer from the code given below: Code: |
| A ➥ P and Q only |
| B ➥ P,Q and R |
| C ➥ Q and R only |
| D ➥ P only |
Show Answer With Best Explanation
| Q74➡ | Computer Network Suppose that everyone in a group of N people wants to communicate secretly with (N-1) other people using symmetric key cryptographic system. The communication between any two persons should not be decodable by the others in the group. The number of keys required in the system as a whole to satisfy the confidentiality requirement is |
| i ➥ 2N |
| ii ➥ N(N-1) |
| iii ➥ N(N-1)/2 |
| iv ➥ (N-1) 2 |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Miscellaneous Topic | Help-Line |
| Q75➡ An attribute A of data type varchar(20) has the value ‘xyz’ and attribute B of data type char(20) has the value “Imnop” , then the attribute A has spaces and attribute B has spaces. |
| A ➥ 3, 5 |
| B ➥ 20, 5 |
| C ➥ 20 , 20 |
| D ➥ 3 ,20 |
Show Answer With Best Explanation
| Q76➡ Consider the C/C++ function f() given below: void f(char w [ ] ) { int x = strlen(w); //length of a string char c; For (int i = 0; i < x; i++) { c = w[i]; w[i] = w[x – i – 1]; w[x – i – 1] = c; } } Which of the following is the purpose of f() ? |
| A ➥ It outputs the contents of the array in the original order. |
| B ➥ It output the contents of the array with the characters shifted over by one position. |
| C ➥ It outputs the contents of the array in the reverse order. |
| D ➥ It output the content of the array with the characters rearranged so they are no longer recognized a the words in the original phrase. |
Show Answer With Best Explanation
| Q77➡ The relation ≤ and < on a boolean algebra are defined as : x ≤ y and only if x ∨ y = y x < y means x ≤ y but x ≠ y x ≥ y means y ≤ x and x > y means y <x Consider the above definitions, which of the following is not true in the boolean algebra ? (i)If x ≤ y and y ≤ z, then x ≤ z (ii)If x ≤ y and y ≤ x, then x=y (iii)If x < y and y < z, then x ≤ y (iv)If x < y and y < z, then x < y Choose the correct answer from the code given below: Code: |
| A ➥ (ii) and (iii) only |
| B ➥ (i) and (ii) only |
| C ➥ (iv) only |
| D ➥ (iii) only |
Show Answer With Best Explanation
| Q78➡ The K-coloring of an undirected graph G=(V,E) is a function C: V➝{0,1,……,K-1} such that c(u)≠c(v) for every edge (u,v) ∈ E Which of the following is not correct? |
| A ➥ G is 2-colorable |
| B ➥ G has no cycles of odd length |
| C ➥ G is bipartite |
| D ➥ G has cycle of odd length |
Show Answer With Best Explanation
| Q79➡ Data warehouse contains___________ data that is never found in operational environment. |
| A ➥ Summary |
| B ➥ Encrypted |
| C ➥ Encoded |
| D ➥ Scripted |
Show Answer With Best Explanation
Q80➡ |
| A ➥ (a)-(i), (b)-(ii), (c)-(iv), (d)-(iii) |
| B ➥ (a)-(i), (b)-(iii), (c)-(iv), (d)-(ii) |
| C ➥ (a)-(ii), (b)-(iii), (c)-(iv), (d)-(i) |
| D ➥ (a)-(iii), (b)-(ii), (c)-(iv), (d)-(i) |
Show Answer With Best Explanation
| Q81➡ A legacy software system has 940 modules. The latest release require that 90 of these modules be changed. In addition, 40 new modules were added and 12 old modules were removed. Compute the software maturity index for the system. |
| A ➥ 0.524 |
| B ➥ 0.923 |
| C ➥ 0.725 |
| D ➥ 0.849 |
Show Answer With Best Explanation
Q82➡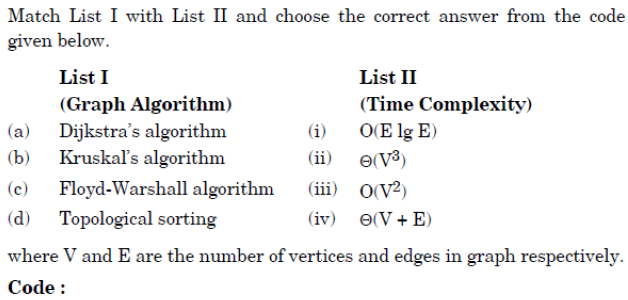 |
| A ➥ (a)-(iii), (b)-(i), (c)-(iv), (d)-(ii) |
| B ➥ (a)-(iii), (b)-(i), (c)-(ii), (d)-(iv) |
| C ➥ (a)-(i), (b)-(iii), (c)-(iv), (d)-(ii) |
| D ➥ (a)-(i), (b)-(iii), (c)-(ii), (d)-(iv) |
Show Answer With Best Explanation
| Q83➡ What does the following java function perform ? (Assume int occupies four bytes of storage) public static int f(int a) { //Pre-conditions : a>0 and no overflow/underflow occurs int b=0; for(int i=0; i<32; i++) { b=b <<1; b= b | (a & 1); a = a >>> 1; // This is a logical shift } Return b; } |
| A ➥ Return the int that represents the number of 1’s in the binary representation of integer a. |
| B ➥ Return the int that represents the number of 0’s in the binary representation of integer a. |
| C ➥ Return the int that has the binary representation of integer a. |
| D ➥ Return the int that has the reversed binary representation of integer a. |
Show Answer With Best Explanation
| Q84➡ Consider two sequences X and Y : X = <0,1,2,1,3,0,1 > Y = <1,3,2,0,1,0 > The length of longest common subsequence between X and Y is |
| A ➥ 5 |
| B ➥ 4 |
| C ➥ 3 |
| D ➥ 2 |
Show Answer With Best Explanation
| Q85➡ The second smallest of n elements can be found with ______ comparisons in worst case. |
| A ➥ 3n/2 |
| B ➥ n-1 |
| C ➥ lg n |
| D ➥ n + ceil(lg n) -2 |
Show Answer With Best Explanation
| Q86➡ Consider the following x86 – assembly language instructions : MOV AL, 153 NEG AL The contents of the destination register AL (in 8-bit binary notation), the status of Carry Flag(CF) and Sign Flag(SF) after the execution of above instructions, are |
| A ➥ AL = 0110 0111; CF = 0; SF =1 |
| B ➥ AL = 0110 0110; CF = 0; SF =0 |
| C ➥ AL = 0110 0111; CF = 1; SF =0 |
| D ➥ AL = 0110 0110; CF = 1; SF =1 |
Show Answer With Best Explanation
| Q87➡ A box contains six red balls and four green balls. Four balls are selected at random from the box. What is the probability that two of the selected balls will be red and two will be green ? |
| A ➥ 3/7 |
| B ➥ 1/9 |
| C ➥ 1/35 |
| D ➥ 1/14 |
Show Answer With Best Explanation
| Q88➡ let r= a(a + b)*, s=aa*b and t=a*b be three regular expressions. Consider the following: (i) L(s) ⊆ L(r) and L(s) ⊆ L(t) (ii). L(r) ⊆ L(s) and L(s) ⊆ L(t) Choose the correct answer from the code given below: Code: |
| A ➥ Neither (i) nor (ii) is correct |
| B ➥ Only (i) is correct |
| C ➥ Only (ii) is correct |
| D ➥ Both (i) and (ii) are correct |
Show Answer With Best Explanation
| Q89➡ A binary search tree is constructed by inserting the following numbers in order: 60, 25, 72, 15, 30, 68, 101, 13, 18, 47, 70, 34 The number of nodes is the left subtree is. |
| A ➥ 3 |
| B ➥ 5 |
| C ➥ 7 |
| D ➥ 6 |
Show Answer With Best Explanation
| Q90➡ To overcome difficulties in Readers-Writers problem, which of the following statement/s is/are true? i) Writers are given exclusive access to shared objects ii) Readers are given exclusive access to shared objects iii) Both readers and writers are given exclusive access to shared objects. Choose the correct answer from the code given below: |
| A ➥ (ii) only |
| B ➥ (i) only |
| C ➥ (i) only |
| D ➥ Both (ii)&(iii) |
Show Answer With Best Explanation
Q91➡ |
| A ➥ (a)-(iv), (b)-(i), (c) -(ii), (d)-(iii) |
| B ➥ (a)-(i), (b)-(iv), (c) -(ii), (d)-(iii) |
| C ➥ (a)-(iv), (b)-(ii), (c) -(i), (d)-(iii) |
| D ➥ (a)-(i), (b)-(iv), (c) -(iii), (d)-(ii) |
Show Answer With Best Explanation
| Q92➡ The decimal floating point number -40.1 represented using IEEE-754 32-bit representation and written in hexadecimal form is |
| A ➥ 0xC2206666 |
| B ➥ 0xC2006000 |
| C ➥ 0xC2006666 |
| D ➥ 0xC2206000 |
Show Answer With Best Explanation
| Q93➡ In a ternary tree, the number of internal nodes of degree 1,2 and 3 is 4,3 and 3 respectively. The number of leaf nodes in the ternary tree is |
| A ➥ 9 |
| B ➥ 10 |
| C ➥ 11 |
| D ➥ 12 |
Show Answer With Best Explanation
Q94➡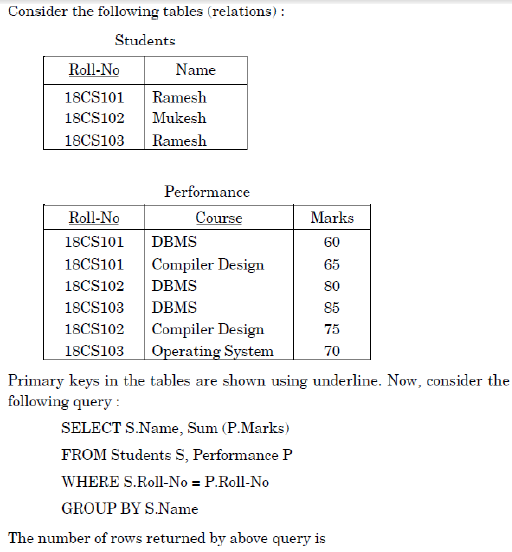 |
| A ➥ 2 |
| B ➥ 3 |
| C ➥ 1 |
| D ➥ 0 |
Show Answer With Best Explanation
| Q95➡ Which of the following problem is decidable for recursive language (L) ? |
| A ➥ Is w∈L, where w is a string ? |
| B ➥ Is L=R, where R is given regular set ? |
| C ➥ Is L = Σ* ? |
| D ➥ Is L = ф ? |
Show Answer With Best Explanation
| Q96➡ Consider the singly linked list. What is the worst case time complexity of the best-known algorithm to delete the node a, pointer to this node is q, from the list ? |
| A ➥ O(n) |
| B ➥ O(n lg n) |
| C ➥ O(lg n) |
| D ➥ O(1) |
Show Answer With Best Explanation
| Q97➡ | Computer Network Which of the following statement/s is/are true ? (i) windows XP supports both peer-peer and client-server networks. (ii) Windows XP implements Transport protocols as drivers that can be loaded and uploaded from the system dynamically. |
| i ➥ Both (i) and (ii) |
| ii ➥ Neither (i) nor (ii) |
| iii ➥ (ii) only |
| iv ➥ (i) only |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Miscellaneous Topic | Help-Line |
| Q98➡ Consider the schema R=(A, B, C, D, E, F) on which the following functional dependencies hold : A➝B B,C➝D E➝C D➝A What are the candidate keys of R ? |
| A ➥ AE and BE |
| B ➥ AE, BE and DE |
| C ➥ AEF, BEF and BCF |
| D ➥ AEF, BEF and DEF |
Show Answer With Best Explanation
| Q99➡ The four byte IP Address consists of |
| A ➥ Host Address |
| B ➥ Both Network and Host Address |
| C ➥ AEF, BEF and BCF |
| D ➥ Neither network nor Host Address |
Show Answer With Best Explanation
Q100➡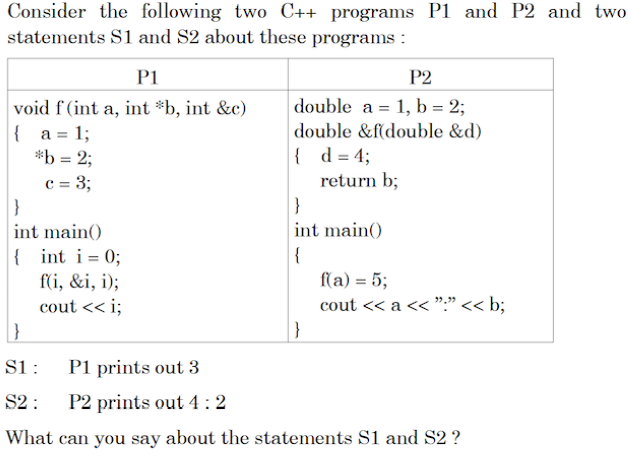 |
| A ➥ Both S1 and S2 are true |
| B ➥ Only S2 is true |
| C ➥ Only S1 is true |
| D ➥ Neither S1 nor S2 is true |