| Q1➡ | Artificial Intelligence The negation of “Some students like hockey” is |
| i ➥ Some students dislike hockey |
| ii ➥ Every student dislike hockey |
| iii ➥ Every student like hockey |
| iv ➥ All students like hockey |
| Best Explanation: Answer: (ii) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q2➡ | Discrete Math A relation ‘R’ is defined on ordered pairs of integers as : (x, y) R (u, v) if x<u and y>v. Then R is |
| i ➥ Neither a partial order nor an equivalence relation |
| ii ➥ A partial order but not a total order |
| iii ➥ A total order |
| iv ➥ An equivalence relation |
| Best Explanation: Answer: (i) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q3➡ | Discrete Math Suppose you are married and you and your partner attend a party with three other married couples. Several handshakes took place. No one shook hands with himself ( or herself ) or with their partner, and no one shook hands with the same person more than once. After all hand shaking was completed , suppose you asked each person, including your partner, how many hands they had shaken. Each person gave a different answer. How many hands did your spouse shake? |
| i ➥ 1 |
| ii ➥ 2 |
| iii ➥ 3 |
| iv ➥ 4 |
| Best Explanation: Answer: (iii) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q4➡ | Programming Consider the following conditional code , which returns a Boolean values If((x>25) && (y>100)) return ‘false’; else if((x <= 25) && (y<=100)) return ‘true’; else if((x>25) && (y<=100)) return ‘false’; else return ‘true’; Simplify it by filling in the following blank with a single Boolean expression without changing the behavior of the conditional code. If (………………..) return ‘true’; else return ‘false’; |
| i ➥ X>25 |
| ii ➥ X≤25 |
| iii ➥ Y>100 |
| iv ➥ Y≤100 |
| Best Explanation: Answer: (ii) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q5➡ | Computer Architecture Which one of the following type of memory is fastest |
| i ➥ Cache memory |
| ii ➥ Register memory |
| iii ➥ Main memory |
| iv ➥ Secondary memory |
| Best Explanation: Answer: (ii) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q6➡ | Digital Logic Design The memory size for n address lines and m data lines is given by |
| i ➥ 2m×n |
| ii ➥ m×n2 |
| iii ➥ 2n×m |
| iv ➥ n×m2 |
| Best Explanation: Answer: (iii) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q7➡ | Digital Logic Design Simplify the following using K-map F(A, B, C, D) = Σ(0, 2, 5, 7, 8, 10, 13, 15) |
| i ➥ BD + B’D’ |
| ii ➥ AC + A’C’ |
| iii ➥ BC + B’C’ |
| iv ➥ AD + A’D’ |
| Best Explanation: Answer: (i) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q8➡ | Computer Architecture Consider an unpipelined machine with 10nsec clock cycles which uses four cycles for ALU operations and branches where as five cycles for memory operation. Assume that the relative frequencies of these operations are : 40%, 20% and 40 %, respectively. Due to clock skew and setup pipeline let us consider that the machine adds one nsec overhead to the clock. How much speedup is observed in the instruction execution rate when a pipelined machine is considered? |
| i ➥ 2 times |
| ii ➥ 4 times |
| iii ➥ 6 times |
| iv ➥ 8 times |
| Best Explanation: Answer: (ii) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q9➡ | Programming Machine Level Language is a/an |
| i ➥ Assembly Language |
| ii ➥ Low Level Language |
| iii ➥ High Level Language |
| iv ➥ Translating Language |
| Best Explanation: Answer: (ii) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q10➡ | Programming Which of the following is wrong about the data types? |
| i ➥ The number is always positive when qualifier ‘unsigned’ is used. |
| ii ➥ The number can be positive or negative when the qualifier ‘signed’ is used |
| iii ➥ The range of value for signed data types is more than that of unsigned data types |
| iv ➥ The left most bit in unsigned data type is used to represent the value |
| Best Explanation: Answer: (iii) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q11➡ | Programming If a constructor ‘Date’ is declared explicitly and has to be defined outside the class. Which of the following is correct? |
| i ➥ Date :: Date (int dd) {/*……*/} |
| ii ➥ Explicit Date :: Date (int dd) {/*…..*/} |
| iii ➥ Such a constructor cannot be defined |
| iv ➥ Constructor always has be defined inside the class |
| Best Explanation: Answer: (i) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q12➡ | Computer Network Which one of the following allows the session to continue? |
| i ➥ When a user quits a browser |
| ii ➥ When the user logs out and is invalidated by the servlet |
| iii ➥ When the session is timed out due to inactivity |
| iv ➥ When the user refreshes the browser and there is a persistent cookie |
| Best Explanation: Answer: (iv) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q13➡ | Artificial Intelligence Overfitting is expected when we observe that? |
| i ➥ With training iterations error on training set as well as test set decreases |
| ii ➥ With training iterations error on training set decrease but test set increases |
| iii ➥ With training iterations error on training set as well as test set increases |
| iv ➥ With training iterations training set as well as test error remains constant |
| Best Explanation: Answer: (ii) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q14➡ | Database Management System identify the incorrect statements: |
| i ➥ A candidate key is minimal set of one or more attributes that, taken collectively, allow us to uniquely identify any entity in the entity set. |
| ii ➥ A candidate key for which no proper subset is also a candidate key is called a super key. |
| iii ➥ A super key is a set of one or more attributes that, taken collectively, allows us to uniquely identify any entity in the entity set. |
| iv ➥ A super key for which no proper subset is also a super key is called a candidate key. |
| Best Explanation: Answer: (ii) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q15➡ | Database Management System Consider the two relations below. The primary keys are underlined. Identify all possible foreign key(s) from the options based only on the two relations. EMP (eid, ename, did) DEPT ( did, dname) |
| i ➥ eid |
| ii ➥ did |
| iii ➥ eid, did |
| iv ➥ eid, did, enameeid, did, ename |
| Best Explanation: Answer: (ii) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q16➡ | Data Management System Which of the following statement is correct , according to the following instance of the relational schema R (X, Y, Z) ? 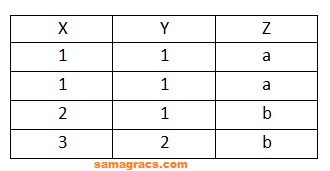 |
| i ➥ X→Y, Z→X |
| ii ➥ Y→Z, Z→X |
| iii ➥ X→Y, X→Z |
| iv ➥ Y→X, X→Z |
| Best Explanation: Answer: (iii) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q17➡ | Operating System In Linux Operating system, when ___________ is invoked , it is passed a set of flags that determine how much sharing is to take place between the parent and child tasks. |
| i ➥ Fork() |
| ii ➥ Clone() |
| iii ➥ Pthread() |
| iv ➥ Thread() |
| Best Explanation: Answer: (ii) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q18➡ | Operating System The main function of the microkernel is to provide a communication facility between the _______ program and the various _______ that are also running in user space . |
| i ➥ Virtual, processes |
| ii ➥ System, processes |
| iii ➥ Client, services |
| iv ➥ Virtual, services |
| Best Explanation: Answer: (iii) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q19➡ | Operating System Consider an operating system capable of loading and executing a single sequential user process at a time. The disk head scheduling algorithm used is first come first served (FCFS) . if FCFS is replaced by shorted seek time first (SSTF) and the vendor claims 50% better benchmark results. What is the expected improvement in the I/O performance of user programs? |
| i ➥ 50% |
| ii ➥ 100% |
| iii ➥ 25% |
| iv ➥ 0% |
| Best Explanation: Answer: (iv) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q20➡ | Operating System For the following set of processes scheduled using FCFS policy, determine the average waiting time. Assume that the processes arrived in the order P1, P2, P3, P4. 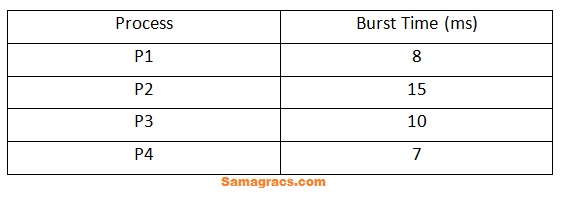 |
| i ➥ 8 |
| ii ➥ 16 |
| iii ➥ 32 |
| iv ➥ 48 |
| Best Explanation: Answer: (ii) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q21➡ | Software Engineering Which of the following is not a Non-functional requirement? |
| i ➥ Portability |
| ii ➥ Security |
| iii ➥ Scalability |
| iv ➥ User interaction |
| Best Explanation: Answer: (iv) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q22➡ | Software Engineering COCOMO stands for ………………… |
| i ➥ Consumed cost model |
| ii ➥ Constructive cost model |
| iii ➥ Common control model |
| iv ➥ Composition cost model |
| Best Explanation: Answer: (ii) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q23➡ | Software Engineering Modifying the software to match change in the ever changing environment is called as |
| i ➥ Adaptive maintenance |
| ii ➥ Corrective maintenance |
| iii ➥ Perfective maintenance |
| iv ➥ Preventive maintenance |
| Best Explanation: Answer: (i) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q24➡ | Software Engineering For a function of two variable, boundary value analysis yields. |
| i ➥ 4n+3 test cases |
| ii ➥ 4n+1 test cases |
| iii ➥ n+4 test cases |
| iv ➥ 2n+4 test cases |
| Best Explanation: Answer: (ii) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q25➡ | Data Structure How many different tree are possible with ‘n’ nodes? |
| i ➥ n-1 |
| ii ➥ 2n-1 |
| iii ➥ 2n |
| iv ➥ 2n-n |
| Best Explanation: Answer: Mark to All Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
Q26➡ | Programming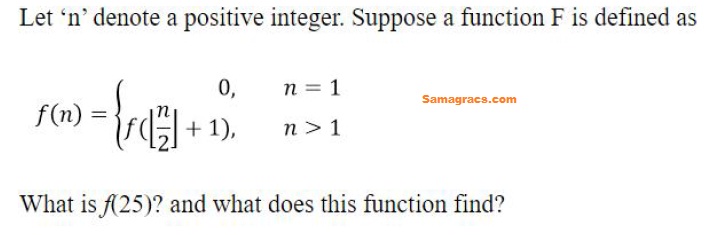 |
| i ➥ 4, ⌊log2n⌋ |
| ii ➥ 14, ⌊log2n⌋ |
| iii ➥ 4, ⌊n/2⌋ |
| iv ➥ 14, ⌊n/2⌋ |
| Best Explanation: Answer: (i) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q27➡ | Algorithm Given the FFT we can have ……………….. time procedure for multiplying two polynomials A(X) and B (X) of degree bound n where input and output representations are in coefficient form, assuming n is a power of 2. |
| i ➥ O(n2) |
| ii ➥ O(n.nlog2n) |
| iii ➥ O(2n) |
| iv ➥ O(log2n) |
| Best Explanation: Answer: (ii) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q28➡ | Algorithm Consider the graph below : 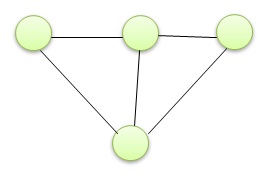 How many spanning trees can be found? |
| i ➥ 10 |
| ii ➥ 5 |
| iii ➥ 9 |
| iv ➥ 8 |
| Best Explanation: Answer: (iv) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q29➡ | Theory of Computation The Transition function ‘δ’ in multi-tape Turing machine is defined as : |
| i ➥ δ : 2Q × Γk → 2Q × Γk × {L, R, S}k |
| ii ➥ δ : Q × Q × Γk → Q × Q × Γk × {L, R, S} k |
| iii ➥ δ : Q × Γk → Q × Γk × {L, R, S} k |
| iv ➥ δ : Q × Γk × 2Q → Q × Γk × 2Q × {L, R, S} k |
| Best Explanation: Answer: (iii) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q30➡ | Theory of Computation In pumping lemma for regular languages, to say a language is satisfying pumping lemma, what is the minimum length of ‘y’ if you consider the string as ‘xyz’. |
| i ➥ n |
| ii ➥ 2 |
| iii ➥ 1 |
| iv ➥ 0 |
| Best Explanation: Answer: (iii) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q31➡ | Compiler Design The item generated by the production A → ɛ is : |
| i ➥ A →. |
| ii ➥ A → ɛ. |
| iii ➥ A → .ɛ |
| iv ➥ A → ɛ |
| Best Explanation: Answer: (i) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q32➡ | Theory of Computation In the ɛ-NFA , M = ({q0, q1, q2, q3}, {a}, δ , q0, {q3} ) where ‘δ ’ is given in the transition table below, what is the minimum length of string to reach to the final state? 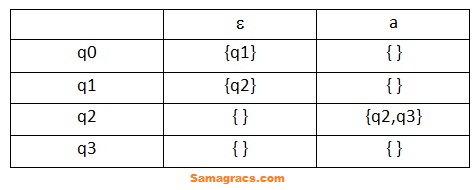 |
| i ➥ 0 |
| ii ➥ 1 |
| iii ➥ 2 |
| iv ➥ 3 |
| Best Explanation: Answer: (ii) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q33➡ | Computer Network Given Ethernet address 01011010 00010001 01010101 00011000 10101010 00001111 in binary, what is the address in hexadecimal notation ? |
| i ➥ 5A : 88 : AA : 18 : 55 : F0 |
| ii ➥ 5A : 81 : BA : 81 : AA : 08 |
| iii ➥ 5A : 18 : 5A : 18 : 55 : 0F |
| iv ➥ 5A : 11 : 55 : 18 : 55 : 0F |
| Best Explanation: Answer: (iv) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q34➡ | Computer Network A computer on a 10 Mbps network is regulated by a token bucket. The token bucket is filled at a rate of 2 Mbps. It is initially filled to capacity with 16 megabits. What is the maximum duration for which the computer can transmit at the full 10 Mbps? |
| i ➥ 1.6 seconds |
| ii ➥ 2 seconds |
| iii ➥ 5 seconds |
| iv ➥ 8 seconds |
| Best Explanation: Answer: (ii) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q35➡ | Computer Network In the standard Ethernet with transmission rate of 10 Mbps , assume that the length of the medium is 2500 m and size of a frame is 512 byes. The propagation speed of a signal in a cable is normally 2×108 m/s. calculate transmission delay and propagation delay. |
| i ➥ 25.25 µs and 51.2 µs |
| ii ➥ 51.2 µs and 12.5 µs |
| iii ➥ 10.2 µs and 50.12 µs |
| iv ➥ 12.5 µs and 51.2 µs |
| Best Explanation: Answer: (ii) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q36➡ | Computer Network In CRC coding if the data word is 111111 , divisor is 1010 and the remainder is 110. Which of the following code is true? |
| i ➥ 011111101 |
| ii ➥ 001010110 |
| iii ➥ 111111110 |
| iv ➥ 110111111 |
| Best Explanation: Answer: (iii) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q37➡ | Artificial Intelligence The A* algorithm is optimal when, |
| i ➥ It always find the solution with the lowest total cost if the heuristic ‘h’ is admissible |
| ii ➥ Always finds the solution with the highest total cost if the heuristic ‘h’ is admissible. |
| iii ➥ Finds the solution with the lowest total cost if the heuristic ‘h’ is not admissible. |
| iv ➥ It always finds the solution with the highest total cost if the heuristic ‘h’ is not admissible. |
| Best Explanation: Answer: (i) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q38➡ | Artificial Intelligence Which Artificial intelligence technique enables the computers to understand the associations and relationships between objects & events? |
| i ➥ Heuristic processing |
| ii ➥ Cognitive science |
| iii ➥ Relative symbolism |
| iv ➥ Pattern matching |
| Best Explanation: Answer: (iv) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q39➡ | Artificial Intelligence Where does the value of alpha- beta search get updated ? |
| i ➥ Along the path of search |
| ii ➥ Initial state itself |
| iii ➥ At the end |
| iv ➥ None of these. |
| Best Explanation: Answer: (i) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q40➡ | Artificial Intelligence 4-input neuron has weight 1, 2, 3, 4 . The transfer function is linear with the constant of proportionality being equal to 3. The inputs are 5, 7, 10, and 30 respectively. the output will be : |
| i ➥ 120 |
| ii ➥ 213 |
| iii ➥ 410 |
| iv ➥ 507 |
| Best Explanation: Answer: (iv) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q41➡ | Discrete Mathematics Consider the following statements: P : There exists no simple, undirected and connected graph with 80 vertices and 77 edges Q : All vertices of Euler graph are of even degree R : Every simple, undirected, connected and acyclic graph with 50 vertices has at least two vertices of degree one S : There exists a bipartite graph with more than ten vertices which is 2 – colorable. What is the number of correct statements among the above statements. |
| i ➥ 1 |
| ii ➥ 2 |
| iii ➥ 3 |
| iv ➥ 4 |
| Best Explanation: Answer: (iv) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q42➡ | Discrete Mathematics consider the following statements. A : There exists a Boolean algebra with 5 elements B : Every element of Boolean algebra has unique complement C : It a Lattice ‘L’ is a Boolean algebra then ‘L’ is not relatively complemented D : The direct product of two Boolean algebra is also a Boolean algebra Choose the correct answer about the four statements given above. |
| i ➥ Only A and D are correct |
| ii ➥ Only B and D are correct |
| iii ➥ All statement are NOT Correct |
| iv ➥ All statement are correct |
| Best Explanation: Answer: (ii) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q43➡ | Operating System Which of the statement is not true in regards to virtual memory? |
| i ➥ The main objective for using virtual memory is to increase the effective capacity of the memory system |
| ii ➥ Size of the program can be as large as the size of the secondary memory |
| iii ➥ Program and data are stored in the secondary memory |
| iv ➥ None of these |
| Best Explanation: Answer: (iv) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q44➡ | Computer Architecture Which of the following is/are true for Dynamic RAM (DRAM) ? (A) It is slower than static RAM (SRAM) (B) Packing Density is Higher than Static RAM (SRAM) (C) It’s faster than Static RAM (SRAM) (D) It is requires data refreshing which of the correct answer from the options given below : |
| i ➥ A, B and D only |
| ii ➥ A, B and C only |
| iii ➥ C and D only |
| iv ➥ B and D only |
| Best Explanation: Answer: (i) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q45➡ | Computer Architecture Which of the following statement is/are false? A : The processor has direct access to both primary and secondary memory B : Primary memory stores the active instructions and data for the program being executed on the process C : Secondary memory is used as a backup memory D : memory system is implemented on a single level memory Choose the correct answer from the options given below : |
| i ➥ A and B only |
| ii ➥ B and C only |
| iii ➥ A, B and C only |
| iv ➥ A and D only |
| Best Explanation: Answer: (iv) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q46➡ | Discrete Mathematics Given a vector with Cartesian components (x,y) , if scaling is done with Matrix Row1[ 0.5 0 ], Row2[0 1.5] which of the following are true: (A) Decrease the vertical by three halves (B) Increase the vertical by three halves (C) Double the horizontal (D) Halves the horizontal Choose the correct from the options given below: |
| i ➥ A and C only |
| ii ➥ A and D only |
| iii ➥ B and C only |
| iv ➥ B and D only |
| Best Explanation: Answer: (iv) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q47➡ | Programming Language Which of the following lists define in HTML Share similar elements? (A) Unordered lists (B) Ordered List (C) Definition List (D) Correlated List (E) Enumerated lists Choose the appropriate answer from the options given below: |
| i ➥ A, B, D only |
| ii ➥ A, C, E only |
| iii ➥ A, B, C only |
| iv ➥ A, C, D only |
| Best Explanation: Answer: Mark to All Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q48➡ | Database What are the drawback of using file system to store data ? (A) Data inconsistency (B) Difficulty in accessing data (C) Data isolation (D) Atomicity of updates Choose the correct answer from the options given below: |
| i ➥ A, B only |
| ii ➥ B, C, D only |
| iii ➥ A, B, C only |
| iv ➥ A, B, C, D |
| Best Explanation: Answer: (iv) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q49➡ | Database which of the following database model, we have a parent -child relationship? (A) Hierarchical database (B) Network database (C) Relational database Choose the correct from the options given below: |
| i ➥ A, B |
| ii ➥ A, C |
| iii ➥ B, C |
| iv ➥ A, B, C |
| Best Explanation: Answer: (i) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q50➡ | Database Identify the correct operation which produces the below output based on two relations R1 and R2 . 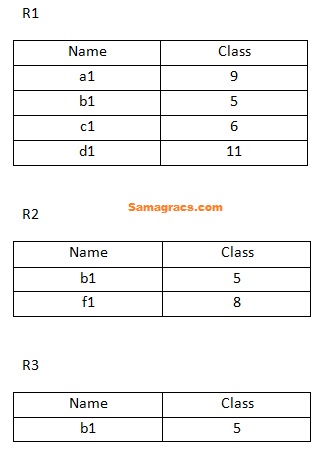 Choose the correct answer from the options below: |
| i ➥ R1∩ R2 |
| ii ➥ R1- R2 |
| iii ➥ R1- (R1-R2) |
| iv ➥ R1∪R2 |
| Best Explanation: Answer: (i), (iii) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q51➡ | Operating System Which of the following statements are true? (A) Shortest remaining time first scheduling may cause starvation (B) Preemptive scheduling may cause starvation (C) Round robin is better than FCFS in term of response time Choose the correct answer from the options given below: |
| i ➥ A only |
| ii ➥ B, C only |
| iii ➥ A, B only |
| iv ➥ A, B, C |
| Best Explanation: Answer: (iv) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q52➡ | Operating System In design protocol of critical section problem, each process must ask permission to enter critical section in ……… code, it then executes in the critical section; once it, finishes executes in the critical section it enters the …….. code. The process then enters the……..code. |
| i ➥ entry section, remainder section, exit section |
| ii ➥ entry section, exit section, remainder section |
| iii ➥ remainder section, entry section, exit section |
| iv ➥ remainder section, exit section, entry section |
| Best Explanation: Answer: (ii) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q53➡ | Software Engineering How do you create agile processes to manage unpredictability? (A) Requirements gathering must be conducted very carefully (B) Risk analysis must be conducted before planning takes place (C) Software increments must be delivered in short time periods (D) Software processes must not adapt to changes incrementally Choose the correct answer from the options given below: |
| i ➥ A only |
| ii ➥ B only |
| iii ➥ C only |
| iv ➥ D only |
| Best Explanation: Answer: (iii) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q54➡ | Software Engineering Software project manager is responsible for the following task: (A) Project planning (B) Project status tracking (C) Resources management (D) Risk management (E) Project delivery within time & budget Choose the correct answer from the options given below: |
| i ➥ All the statements are correct |
| ii ➥ Only B & C are correct |
| iii ➥ Only A & D are correct |
| iv ➥ All the statements are not correct |
| Best Explanation: Answer: (i) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q55➡ | Software Engineering Mr X designed open source software which must comply with some criteria. Choose the false statement in respect of above. (A) No restriction on redistribution of the software as part or whole (B) The integrity of the author’s source code must be maintained. (C) The software can be sold after distribution. Choose the correct answer from the options given below: |
| i ➥ A only |
| ii ➥ B only |
| iii ➥ C only |
| iv ➥ All statements are false |
| Best Explanation: Answer: (iii) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q56➡ | Algorithm Circuit satisfiability problem: Given a Boolean combinatorial circuit composed of AND, OR and NOT gates, is it satisfiable ? One output Boolean combinatorial circuit is satisfiable means for the given inputs the output will be 1. (A) The circuit satisfiability problem belongs to class NP (B) The circuit satisfiability problem is at least as hard as any language in NP (C) The circuit satisfiability is NP- Complete (D) The size of the circuit is Θ( K2+1) (E) If P≠NP this situation would contradict the NP – completeness of the problem. Choose the correct answer from the options given below: |
| i ➥ A, C , D only |
| ii ➥ B, D, E only |
| iii ➥ A, B, C only |
| iv ➥ B, C, D only |
| Best Explanation: Answer: (iii) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q57➡ | Data Structure Given an expression (A + B*D) / (E-F) + G (A) The prefix notation is +/+A*DB-EFG (B) The prefix expression is the reverse of the postfix expression (C) The order of operands in infix expression and postfix expression are the same. (D) The order of operands in infix expression, prefix expression and postfix expression are the same Choose the most appropriate answer from the options given below: |
| i ➥ A, C and D only |
| ii ➥ C and D only |
| iii ➥ A and B only |
| iv ➥ A and D only |
| Best Explanation: Answer: (ii) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q58➡ | Theory of Computation The Transition function ‘δ’ in mu Which of the following is /are correct about the regular expression? aa*bb*cc*dd* (A) The language for the given expression L = { anbncmdm | n≥1, m≥1 } ∪ { anbmcmdn | n≥1, m≥1 } (B) The context free language for the given expression is S→AB | C A→ aAb | ab B→ cBd | cd C→aCd | aDd D→bDc | BC (C) The language generated by this expression is equal number of a’s, followed by equal number of b’s , followed by equal number of c’s and followed by equal number of d’s. Choose the correct answer from the options given below: |
| i ➥ Only A is correct |
| ii ➥ Only B is Correct |
| iii ➥ Both A and B are correct |
| iv ➥ All the three A, B and C are correct |
| Best Explanation: Answer: (iii) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q59➡ | Compiler Design Which of the following statements are correct? (A) The first three address instruction in the intermediate code is a leader. (B) The instruction which is exactly at the middle of the given three address code is a leader. (C) Any instruction that is the target of a conditional or unconditional jump is a leader. (D) Any instruction that immediately follows a conditional or unconditional jump is a leader. Choose the correct answer from the options given below: |
| i ➥ A, B and C |
| ii ➥ B, C and D |
| iii ➥ A, C and D |
| iv ➥ A, B, C and D |
| Best Explanation: Answer: (iii) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q60➡ | Theory of Computation which of the following are correct on regular expression? (A) φ + L = L + φ = L (B) ɛ L = L ɛ = L (C) φ L = L φ = φ (D) φ L = L φ = L Choose the correct answer from the options given below: |
| i ➥ A, B and D only |
| ii ➥ A, B and C only |
| iii ➥ B and D only |
| iv ➥ A and D only |
| Best Explanation: Answer: (ii) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q61➡ | Computer Network Consider two hosts P and Q are connected through a router R. The maximum transfer unit (MTU) value of the link between P and R is 1500 bytes and between R and Q is 820 bytes. A TCP segment of size of 1400 bytes is transferred from P to Q through R with IP identification value of 0x1234, Assume that IP header size is 20 bytes Further the packet is allowed to be fragmented that is Don’t Fragment (DF) flag in the IP Header is not set by P which of the following statement is are true (A) Two fragments are created at R and IP datagram size carrying the second fragment is 620 bytes (B) If the second fragment is lost then R resend the fragment with IP Identification value of 0x1334 (C) If the second fragment lost then P required to resend the entire TCP segment (D) TCP destination port can be determined by analyzing the second fragment only Choose the correct answer from the options given below: |
| i ➥ A, B and C only |
| ii ➥ A and C only |
| iii ➥ C and D only |
| iv ➥ B and D only |
| Best Explanation: Answer: (ii) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q62➡ | Computer Network The solution to silly window syndrome problem is/are (A) Nagle’s algorithm (B) Clark’s algorithm (C) Jacobson’s algorithm (D) Piggy backing algorithm Choose the correct answer from the options given below: |
| i ➥ A and B only |
| ii ➥ A and C only |
| iii ➥ C and D only |
| iv ➥ B and D only |
| Best Explanation: Answer: (i) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q63➡ | Artificial Intelligence Which AI system mimics the evolutionary process to generate increasingly better solution to a process to a problem? (A) Self-organizing neural network (B) Back propagation neural network (C) Generic algorithm (D) Forward propagation neural network Choose the correct answer from the options given below: |
| i ➥ A only |
| ii ➥ B only |
| iii ➥ C only |
| iv ➥ D only |
| Best Explanation: Answer: (iii) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q64➡ | Artificial Intelligence Consider the following Learning algorithms. (A) Logistic regression (B) Back propagation (C) Linear regression (D) Forward propagation Which of the following options represents classification algorithm? Choose the correct answer from the options given below: |
| i ➥ A and C only |
| ii ➥ B and D only |
| iii ➥ A and B only |
| iv ➥ C and D only |
| Best Explanation: Answer: (iii) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q65➡ | Artificial Intelligence Which Boolean operation on two variables can be represented by a single perception layer? (A) X1 AND X2 (B) X1 OR X2 (C) X1 NOR X2 (D) X1 XOR X2 Choose the most appropriate answer from the options given below: |
| i ➥ A and B only |
| ii ➥ B and C only. |
| iii ➥ A, B and C only |
| iv ➥ A, B, C and D only |
| Best Explanation: Answer: (iii) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q66➡ | Discrete Mathematics Match List (I) with List (II) 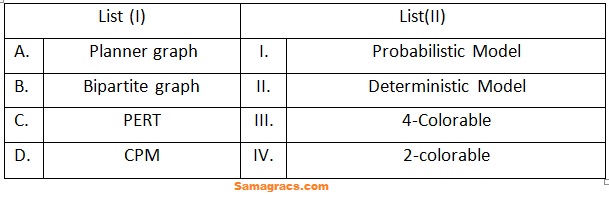 Choose the correct answer from the options given below: |
| i ➥ A-(IV), B-(III), C-(I), D-(II) |
| ii ➥ A-(III), B-(IV), C-(II), D-(I) |
| iii ➥ A-(II), B-(IV), C-(I), D-(III) |
| iv ➥ A-(III), B-(IV), C-(I), D-(II) |
| Best Explanation: Answer: (iv) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q67➡ | Computer Architecture Match List (I) with List (II) 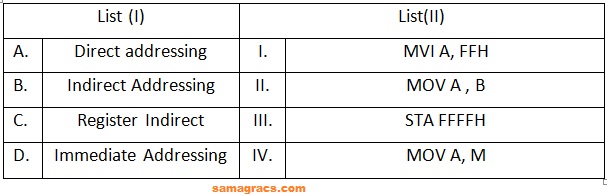 Choose the correct answer from the options given below: |
| i ➥ A-(I), B-(II), C-(III), D-(IV) |
| ii ➥ A-(II), B-(III), C-(IV), D-(I) |
| iii ➥ A-(III), B-(IV), C-(II), D-(I) |
| iv ➥ A-(IV), B-(III), C-(I), D-(II) |
| Best Explanation: Answer: (iii) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q68➡ | Programming Match List (I) with List (II) 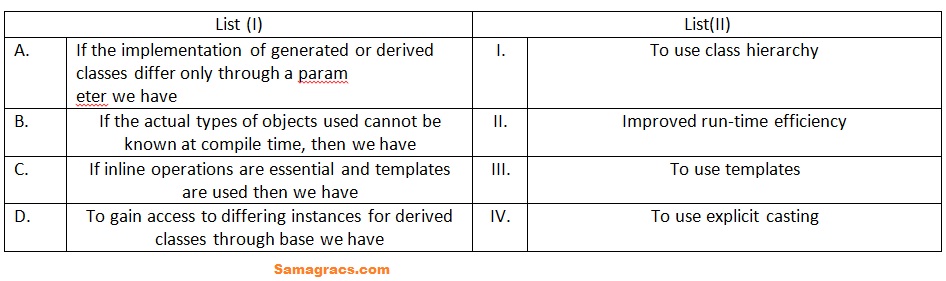 Choose the correct answer from the options given below: |
| i ➥ A-(I), B-(II), C-(IV), D-(III) |
| ii ➥ A-(III), B-(I), C-(II), D-(IV) |
| iii ➥ A-(I), B-(III), C-(II), D-(IV) |
| iv ➥ A-(II), B-(I), C-(III), D-(IV) |
| Best Explanation: Answer: (ii) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q69➡ | Programming Match List (I) with List (II) 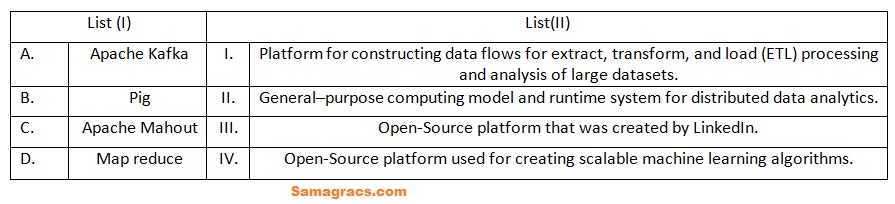 Choose the correct answer from the options given below: |
| i ➥ A-(II), B-(IV), C-(I), D-(III) |
| ii ➥ A-(II), B-(I), C-(IV), D-(III) |
| iii ➥ A-(III), B-(I), C-(IV), D-(II) |
| iv ➥ A-(I), B-(II), C-(IV), D-(III) |
| Best Explanation: Answer: (iii) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q70➡ | Operating System Match List (I) with List (II) 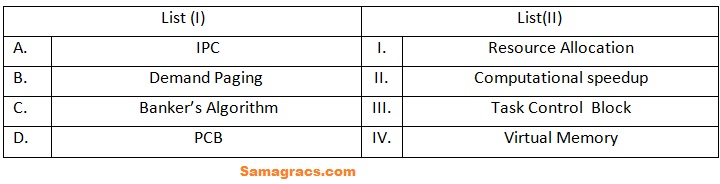 Choose the correct answer from the options given below: |
| i ➥ A-(II), B-(I), C-(IV), D-(III) |
| ii ➥ A-(II), B-(IV), C-(I), D-(III) |
| iii ➥ A-(I), B-(II), C-(III), D-(IV) |
| iv ➥ A-(II), B-(III), C-(I), D-(IV) |
| Best Explanation: Answer: (ii) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q71➡ | Software Engineering Match List (I) with List (II) 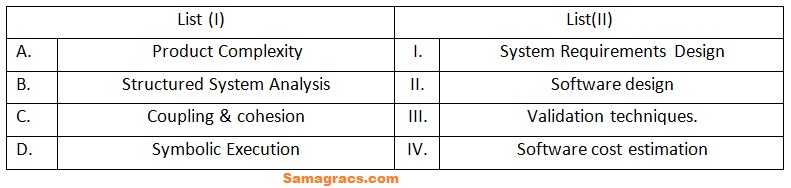 Choose the correct answer from the options given below: |
| i ➥ A-(II), B-(III), C-(IV), D-(I) |
| ii ➥ A-(III), B-(I), C-(IV), D-(II) |
| iii ➥ A-(IV), B-(I), C-(II), D-(III) |
| iv ➥ A-(III), B-(IV), C-(I), D-(II) |
| Best Explanation: Answer: (iii) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q72➡ | Algorithm Match List (I) with List (II) 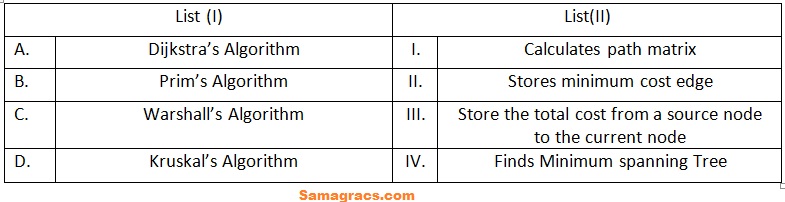 Choose the correct answer from the options given below: |
| i ➥ A-(I), B-(II), C-(III), D-(IV) |
| ii ➥ A-(III), B-(II), C-(I), D-(IV) |
| iii ➥ A-(II), B-(I), C-(IV), D-(III) |
| iv ➥ A-(III), B-(IV), C-(II), D-(I) |
| Best Explanation: Answer: (ii) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q73➡ | Theory of Computation Match the following based on the language accepted by using brute force method of parsing. 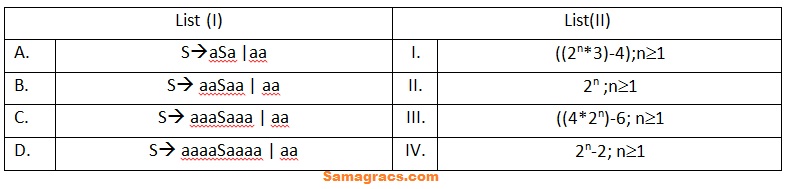 Choose the correct answer from the options given below: |
| i ➥ A-(IV), B-(III), C-(I), D-(II) |
| ii ➥ A-(II), B-(IV), C-(I), D-(III) |
| iii ➥ A-(I), B-(IV), C-(III), D-(II) |
| iv ➥ A-(II), B-(III), C-(I), D-(IV) |
| Best Explanation: Answer: (ii) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q74➡ | Computer Network Match List (I) with List (II) 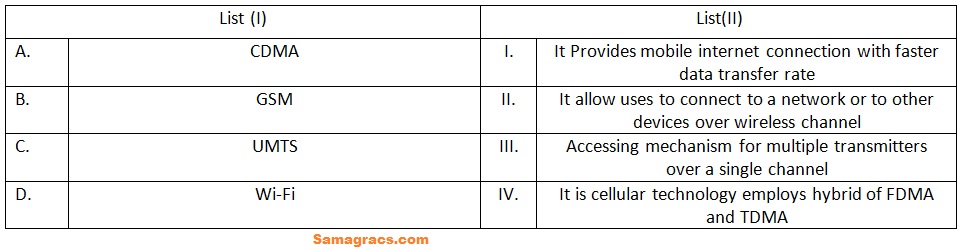 Choose the correct answer from the options given below: |
| i ➥ A-(III), B-(IV), C-(II), D-(I) |
| ii ➥ A-(III), B-(IV), C-(I), D-(II) |
| iii ➥ A-(II), B-(III), C-(IV), D-(I) |
| iv ➥ A-(II), B-(I), C-(IV), D-(III) |
| Best Explanation: Answer: (ii) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q75➡ | Artificial Intelligence March List(I) with List (II) 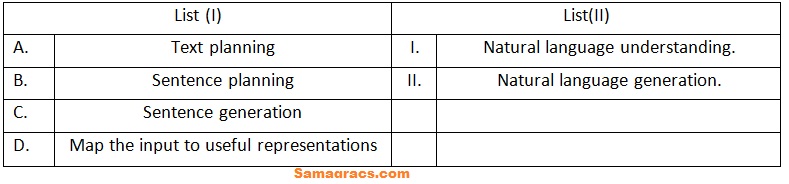 Choose the correct answer from the options given below: |
| i ➥ A-(I), B-(II), C-(I), D-(II) |
| ii ➥ A-(II), B-(II), C-(I), D-(II) |
| iii ➥ A-(I), B-(II), C-(II), D-(I) |
| iv ➥ A-(II), B-(II), C-(II), D-(I) |
| Best Explanation: Answer: (iv) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q76➡ | Artificial Intelligence consider the statements: A : There does not exist a polynomial time algorithm to solve integer Linear programming problem. B : Main focus of PERT is ‘minimizing time’ . Choose the correct option about the statements A and B. |
| i ➥ A is True; B is True |
| ii ➥ A is True; B is False |
| iii ➥ A is False; B is True |
| iv ➥ A is False; B is False |
| Best Explanation: Answer: (i) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q77➡ | Computer Architecture The Correct sequence in fetch- executes cycle is …………. (A) Decode (B) Fetch (C) Execute Choose the correct answer from the following |
| i ➥ A-B-C |
| ii ➥ B-C-A |
| iii ➥ C-B-A |
| iv ➥ B-A-C |
| Best Explanation: Answer: (iv) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q78➡ | Programming Language In what sequence the initialization, testing and execution of body is done while using do while loop? (A) Commenting (B) Execution of the body (C) Initialization (D) Testing the condition Choose the correct answer from the following: |
| i ➥ D,B,C |
| ii ➥ D,C,B |
| iii ➥ C,A,B |
| iv ➥ C,B,D |
| Best Explanation: Answer: (iv) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q79➡ | Artificial Intelligence Select the correct order of DBSCAN Algorithm. (A) Find recursively all its density connected points and assign them to the same cluster as the core point. (B) Find all the neighbor point with eps and identify the core points with more than MinPts neighbor’s. (C) Iterate through the remaining unvisited pointed in the dataset. (D) For each core point if it is not already assigned to a cluster, create a new cluster. Choose the correct answer from the following: |
| i ➥ B, D, C, A |
| ii ➥ D, B, C, A |
| iii ➥ B, D, A, C |
| iv ➥ D, B, A, C |
| Best Explanation: Answer: (iii) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q80➡ | Operating System Select the correct order of events after power is initialized on a system: (A) Bootstrap loader is loaded from the disk (B) Kernel is loaded onto the memory (C) Firmware ROM loads boot block Choose the correct answer from the options given below: |
| i ➥ B, C, A |
| ii ➥ C, A, B |
| iii ➥ A, B, C |
| iv ➥ A, C, B |
| Best Explanation: Answer: (ii) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q81➡ | Software Engineering Given below are two statements: one is labeled as Assertion A and the other is labeled as Reason R. Assertion A: Cohesion is a qualitative indication of the degree to which a module can be written more compactly and is able to complete its function in a timely manner. Reason R. Cohesion is a qualitative indication of the degree to which a module is connected to other modules and the outside world. In the belt of the above statements choose the most appropriate answer from the options given below. |
| i ➥ Both A and Rare correct and R is the correct explanation of A |
| ii ➥ Both A and Rare correct but R is NOT the correct explanation of A |
| iii ➥ A is correct but R is not correct |
| iv ➥ A is not correct but R is correct. |
| Best Explanation: Answer: (iii) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q82➡ | Algorithm Given the graph below which one of the following edges cannot be added in that order to find a minimum spanning tree using algorithm. 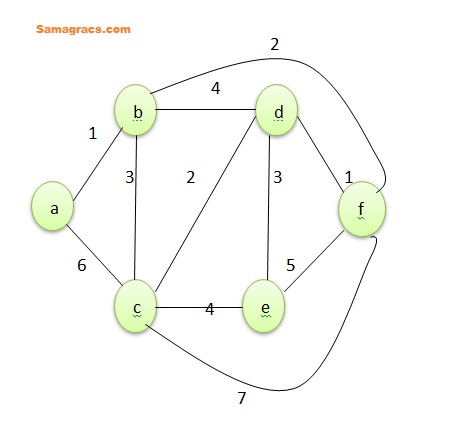 (A) a-b (B) d-f (C) b-f (D) d-c (E) d-e Choose the correct answer from the options given below: |
| i ➥ A, B, C, D, E |
| ii ➥ A, B, D, C, E |
| iii ➥ B, A, C, E, D |
| iv ➥ B, A, D, C, E |
| Best Explanation: Answer: (iii) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q83➡ | Theory of Computation What is the safest order while simplifying context Free Grammar? |
| i ➥ Elimination of ɛ-productions , Unit productions and then useless symbols & Productions. |
| ii ➥ Elimination of useless symbols & productions, ɛ- productions and then Unit Productions. |
| iii ➥ Elimination of Unit productions, ɛ- productions and then useless symbols and productions. |
| iv ➥ Elimination of ɛ- productions. Useless symbols and productions and then Unit Productions. |
| Best Explanation: Answer: (i) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q84➡ | Computer Network Rearrange the following sequence in the context of OSI layers: (A) Transforming the raw bits in the form of frame for transmission (B) Transmission of raw bits over communication channel (C) Handling user interfaces (D) Control and monitoring of subnet (E) Transmission data through connection orientated or connection less using datagram. Choose the correct answer from the options given below: |
| i ➥ A-B-C-D-E |
| ii ➥ B-C-D-E-A |
| iii ➥ B-A-D-E-C |
| iv ➥ A-B-D-E-C |
| Best Explanation: Answer: (iii) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q85➡ | Artificial Intelligence Choose the correct option describing the features of artificial neural network (A) It is essentially machine learning algorithm. (B) It is useful when solving the problems for which the data set is very large. (C) They are able to extract features without input from the programmer. (D) These are system modeled on the human brain and nervous system Choose the correct answer from the options given below: |
| i ➥ All the statements are correct |
| ii ➥ Only B and C are correct |
| iii ➥ Only A and D are correct |
| iv ➥ All the statements are not correct. |
| Best Explanation: Answer: (i) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q86➡ | Artificial Intelligence Four person: P, Q, R and S are in police custody and one of them has committed a crime. They confess as follows: (A) Person P: Q did it (B) Person Q: S did it (C) Person R: I did not do it (D) Person S: Q lied If exactly one of the statements is false. Which of the following is the guilty person? |
| i ➥ P |
| ii ➥ Q |
| iii ➥ R |
| iv ➥ S |
| Best Explanation: Answer: (ii) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q87➡ | Computer Graphics Assertion A: A Raster scan device is a CRT graphic device and can use a television monitor for display. Reason R: In Raster scan display the picture is composed of a series of dots. These dots are traced out as a series of horizontal lines. Television works in a similar fashion. In the light of the above statements: choose the correct answer from the options given below |
| i ➥ Both A and R are true and R is the correct explanation of A |
| ii ➥ Both A and R are true but R is not the correct explanation of A |
| iii ➥ A is true but R is false |
| iv ➥ A is false but R is true |
| Best Explanation: Answer: (i) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q88➡ | Operating System An OS follows round robin scheduling with time quantum of 4 ms. Assuming that the CPU is free now and there are 20 processes waiting in the ready queue, the maximum amount of time that a process waits before getting into the CPU is…………. |
| i ➥ 80 ms |
| ii ➥ 76 ms |
| iii ➥ 84 ms |
| iv ➥ None of the above |
| Best Explanation: Answer: (ii) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
Q89➡ | Discrete Mathematics  |
| i ➥ Both statement (I) and Statement (II) are correct |
| ii ➥ Both statement (I) and Statement (II) are incorrect |
| iii ➥ Statement (I) is correct but Statement (II) is incorrect |
| iv ➥ Statement (I) is incorrect and Statement (II) is correct |
| Best Explanation: Answer: (iii) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q90➡ | Computer Network A TCP Server application is programmed to listen on port P on Host S. A TCP Client is connected to the TCP Server over the network. Considered that while TCP Connection is active the server is crashed and rebooted Assume that the client does not use TCP keep alive timer. Which of the following behaviors is/are possible? Statement I: If client is waiting to receive a packet, it may wait indefinitely Statement II: If the client sends a packet after the server reboot, it will receive the FIN segment In the light of the above statements. Choose the correct answer from the options given below: |
| i ➥ Both Statement I and Statement II are true |
| ii ➥ Both Statement I and Statement II are false |
| iii ➥ Statement I is true but Statement II is false |
| iv ➥ Statement I is false but Statement II is true |
| Best Explanation: Answer: (iii) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q91➡ | Computer Network An organization is granted the block 130.56.0.0/16. The administration wants to create 1024 subnets. Find the number of addresses is each subnet. |
| i ➥ 32 |
| ii ➥ 64 |
| iii ➥ 128 |
| iv ➥ 16 |
| Best Explanation: Answer: (ii) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q92➡ | Computer Network An organization is granted the block 130.56.0.0/16 . The administration wants to create 1024 subnets. Find the subnet prefix |
| i ➥ 130.56 |
| ii ➥ 136.0 |
| iii ➥ 136.255 |
| iv ➥ 136.56.255 |
| Best Explanation: Answer: (i) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q93➡ | Computer Network An organization is granted the block 130.56.0.0/16. The administration wants to create 1024 subnets. Find first and last addresses of First subnet. |
| i ➥ 130.56.0.0 130.56.254.254 |
| ii ➥ 130.56.0.0 130.56.0.63 |
| iii ➥ 130.0.0.0 130.255.255.255 |
| iv ➥ 130.56.0.0 130.56.255.63 |
| Best Explanation: Answer: (ii) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q94➡ | Computer Network An organization is granted the block 130.56.0.0/16 . The administration wants to create 1024 subnets. Find first and last address of the last subnet. |
| i ➥ 130.56.0.0 130.56.254.255 |
| ii ➥ 130.56.255.0 130.56.255.255 |
| iii ➥ 130.56.0.192 130.255.255.255 |
| iv ➥ 130.56.255.192 130.56.255.255 |
| Best Explanation: Answer: (iv) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q95➡ | Computer Network An organization is granted the block 130.56.0.0/16 . The administration wants to create 1024 subnets. Find the subnet mask. |
| i ➥ 130.255.255.255 |
| ii ➥ 130.56.255.255 |
| iii ➥ 130.56.0.255 |
| iv ➥ 130.56.155.192 |
| Best Explanation: Answer: Mark to All Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
Q96➡ | Theory of Computation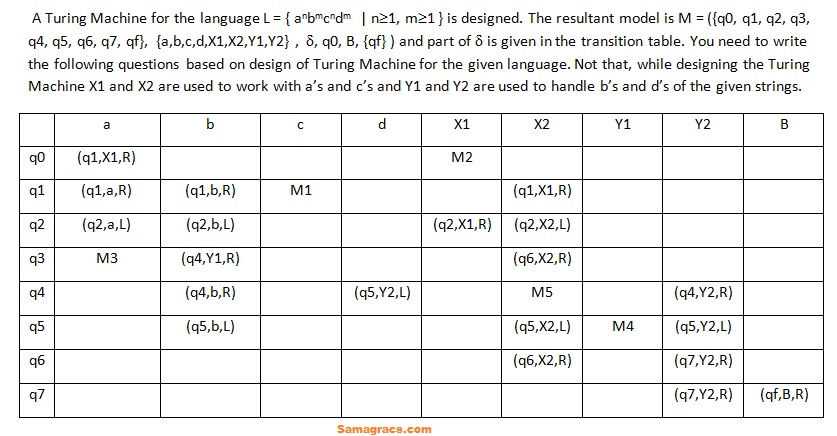 What is the Move in the cell with number ‘M1’ of the resultant Table? |
| i ➥ (q2,X2,R) |
| ii ➥ (q2,X2,L) |
| iii ➥ (q3,X2,L) |
| iv ➥ Error Entry |
| Best Explanation: Answer: (ii) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
Q97➡ | Theory of Computation What is the Move in the cell with number ‘M2’ of the resultant Table? |
| i ➥ (q1,X1,R) |
| ii ➥ (q1,a,R) |
| iii ➥ (q2,X1,R) |
| iv ➥ Error Entry |
| Best Explanation: Answer: (iv) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
Q98➡ | Theory of Computation What is the Move in the cell with number ‘M3’ of the resultant Table? |
| i ➥ (q1,X1,L) |
| ii ➥ (q4,X1,R) |
| iii ➥ (q1,X1,R) |
| iv ➥ Error Entry |
| Best Explanation: Answer: (iii) Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
Q99➡ | Theory of Computation  What is the Move in the cell with number ‘M4’ of the resultant Table? |
| i ➥ (q5,Y1,L) |
| ii ➥ (q3,Y1,R) |
| iii ➥ (q4,Y1,L) |
| iv ➥ (q3,Y1,L) |
| Best Explanation: Answer: Mark to All Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
Q100➡ | Theory of Computation What is the Move in the cell with number ‘M5’ of the resultant Table? |
| i ➥ (q4,X2,R) |
| ii ➥ (q5,X2,R) |
| iii ➥ (q5,X2,L) |
| iv ➥ Error Entry |
| Best Explanation: Answer: Mark to All Explanation: Upload Soon |
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
