GATE CSE 2008 PYQ
| Q1➡ | Engineering Mathematics |
| i ➥ 1 |
| ii ➥ -1 |
| iii ➥ ∞ |
| iv ➥ -∞ |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Calculus | Help-Line |
| Q2➡ | Engineering Mathematics If P, Q, R are subsets of the universal set U, then (P∩Q∩R) ∪ (Pc∩Q∩R) ∪ Qc ∪ Rc is |
| i ➥ Qc ∪Rc |
| ii ➥ P ∪ Qc ∪Rc |
| iii ➥ Pc ∪ Qc ∪Rc |
| iv ➥ U |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Sets and relation | Help-Line |
| Q3➡ | Engineering Mathematics The following system of equations x1 + x2 + 2x3 = 1 x1 + 2x2 + 3x3 = 2 x1 + 4x2 + ax3 = 4 has a unique solution. The only possible value(s) for a is/are |
| i ➥ 0 |
| ii ➥ either 0 or 1 |
| iii ➥ one of 0,1 or -1 |
| iv ➥ any real number |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Linear Algebra | Help-Line |
| Q4➡ | Digital logic design In the IEEE floating point representation, the hexadecimal value 0×00000000 corresponds to |
| i ➥ the normalized value 2-127 |
| ii ➥ the normalized value 2-128 |
| iii ➥ the normalized value +0 |
| iv ➥ the special value +0 |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Number systems | Help-Line |
| Q5➡ | Digital logic design In the Karnaugh map shown below, X denotes a don’t care term. What is the minimal form of the function represented by the Karnaugh map? 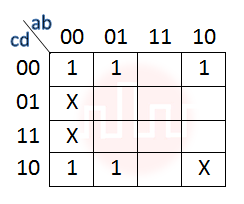 |
| i ➥ b’.d’+a’.d’ |
| ii ➥ a’.b’+b’.d’+a’.b.d’ |
| iii ➥ b’.d’+a’.b.d’ |
| iv ➥ a’.b’+b’.d’+a’.d’ |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | K Map | Help-Line |
| Q6➡ | Digital logic design Let r denote number system radix. The only value(s) of r that satisfy the equation |
| i ➥ decimal 10 |
| ii ➥ decimal 11 |
| iii ➥ decimal 10 and 11 |
| iv ➥ any value >2 |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Number systems | Help-Line |
| Q7➡ | Data structure The most efficient algorithm for finding the number of connected components in an undirected graph on n vertices and m edges has time complexity |
| i ➥ θ(n) |
| ii ➥ θ(m) |
| iii ➥ θ(m+n) |
| iv ➥ θ(mn) |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Graphs | Help-Line |
| Q8➡ | Digital logic design Given f1, f3 and f in canonical sum of products form (in decimal) for the circuit 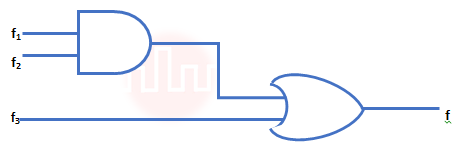 f1 = Σm(4,5,5,7,8) f3 = Σm(1,6,15) f = Σm(1,6,8,15) then f2 is |
| i ➥ Σm(4,6) |
| ii ➥ Σm(4,8) |
| iii ➥ Σm(6,8) |
| iv ➥ Σm(4,6,8) |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Canonical normal form | Help-Line |
| Q9➡ | Theory of computation Which of the following is true for the language {ap|p is a prime} ? |
| i ➥ It is not accepted by a Turing Machine |
| ii ➥ It is regular but not context-free |
| iii ➥ It is context-free but not regular |
| iv ➥ It is neither regular nor context-free, but accepted by a Turing machine |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Identify Class Language | Help-Line |
| Q10➡ | Theory of computation Which of the following are decidable? I.Whether the intersection of two regular languages is infinite II.Whether a given context-free language is regular III.Whether two push-down automata accept the same language IV.Whether a given grammar is context-free |
| i ➥ I and II |
| ii ➥ I and IV |
| iii ➥ II and III |
| iv ➥ II and IV |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q11➡ | Compiler design Which of the following describes a handle (as applicable to LR-parsing) appropriately? |
| i ➥ It is the position in a sentential form where the next shift or reduce operation will occur. |
| ii ➥ It is non-terminal whose production will be used for reduction in the next step. |
| iii ➥ It is a production that may be used for reduction in a future step along with a position in the sentential form where the next shift or reduce operation will occur. |
| iv ➥ It is the production p that will be used for reduction in the next step along with a position in the sentential form where the right hand side of the production may be found. |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Compilers | Help-Line |
| Q12➡ | Compiler design Some code optimizations are carried out on the intermediate code because |
| i ➥ They enhance the portability of the compiler to other target processors |
| ii ➥ Program analysis is more accurate on intermediate code than on machine code |
| iii ➥ The information from dataflow analysis cannot otherwise be used for optimization |
| iv ➥ The information from the front end cannot otherwise be used for optimization |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Compilers | Help-Line |
| Q13 | Theory of computation If L and L’ are recursively enumerable, then L is |
| i ➥ Regular |
| ii ➥ Context-free |
| iii ➥ Context-sensitive |
| iv ➥ Recursive |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Recursive enumerable Language | Help-Line |
| Q14➡ | Computer network What is the maximum size of data that the application layer can pass on to the TCP layer below? |
| i ➥ Any size |
| ii ➥ 216 bytes-size of TCP header |
| iii ➥ 216 bytes |
| iv ➥ 1500 bytes |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Application layer protocol | Help-Line |
| Q15➡ | Database Management system Which of the following tuple relational calculus expression(s) is/are equivalent to |
| i ➥ I only |
| ii ➥ II only |
| iii ➥ III only |
| iv ➥ III and IV only |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Relational calculus | Help-Line |
| Q16➡ | Database Management system A clustering index is defined on the fields which are of type |
| i ➥ non-key and ordering |
| ii ➥ non-key and non-ordering |
| iii ➥ Key and ordering |
| iv ➥ Key and non-ordering |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Indexing | Help-Line |
| Q17➡ | Computer networks Which of the following system calls results in the sending of SYN packets? |
| i ➥ Socket |
| ii ➥ Bind |
| iii ➥ Listen |
| iv ➥ Connect |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Socket | Help-Line |
| Q18➡ | Programming Which combination of the integer variables x, y and z makes the variable a get the value 4 in the following expression? a = (x > y) ? ((x > z) ? x : z) : ((y > z) ? y : z) |
| i ➥ x = 3, y = 4, z = 2 |
| ii ➥ x = 6, y = 5, z = 3 |
| iii ➥ x = 6, y = 3, z = 5 |
| iv ➥ x = 5, y = 4, z = 5 |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | C-Programming | Help-Line |
| Q19➡ | Data structures The Breadth First Search algorithm has been implemented using the queue data structure. One possible order of visiting the nodes of the following graph is 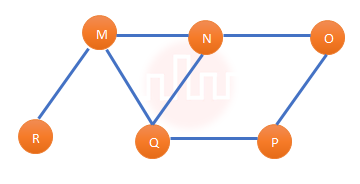 |
| i ➥ MNOPQR |
| ii ➥ NQMPOR |
| iii ➥ QMNPRO |
| iv ➥ QMNPOR |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Graphs | Help-Line |
| Q20➡ | Operating system The data blocks of a very large file in the Unix file system are allocated using |
| i ➥ Contiguous allocation |
| ii ➥ Linked allocation |
| iii ➥ Indexed allocation |
| iv ➥ An extension of indexed allocation |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | File system | Help-Line |
| Q21➡ | Engineering mathematics The minimum number of equal length subintervals needed to approximate to an accuracy of at least using the trapezoidal rule is |
| i ➥ 1000e |
| ii ➥ 1000 |
| iii ➥ 100e |
| iv ➥ 100 |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Trapezidal rule | Help-Line |
| Q22➡ | Engineering mathematics The Newton-Raphson iteration can be used to compute the |
| i ➥ Square of R |
| ii ➥ Reciprocal of R |
| iii ➥ Square root of R |
| iv ➥ logarithm of R |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Newton raphson method | Help-Line |
| Q23➡ | Engeering mathematics Which of the following statements is true for every planar graph on n vertices? |
| i ➥ The graph is connected |
| ii ➥ The graph is eulerian |
| iii ➥ The graph has a vertex-cover of size at most 3n/4 |
| iv ➥ The graph has an independent set of size at least n/3 |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Graph theory | Help-Line |
| Q24➡ | Engineering Mathematics |
| i ➥ P = Q – k |
| ii ➥ P = Q +k |
| iii ➥ P = Q |
| iv ➥ P = Q – 2k |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Permutation and combination | Help-Line |
| Q25➡ | Engineering Mathematics A point on a curve is said to be an extremum if it is a local minimum or a local maximum. The number of distinct extrema for the curve 3x4 – 16x3 + 24x2 + 37 is |
| i ➥ 0 |
| ii ➥ 1 |
| iii ➥ 2 |
| iv ➥ 3 |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Calculus | Help-Line |
| Q26➡ | Digital logic design If P, Q, R are Boolean variables, (P+Q’) (P . Q’+P . R)(P’ . R’+ Q) then Simplifies to |
| i ➥ P . Q’ |
| ii ➥ P . R’ |
| iii ➥ P . Q’+R |
| iv ➥ P . R’+Q |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Boolean algebra | Help-Line |
| Q27➡ | Engineering Mathematics Aishwarya studies either computer science or mathematics everyday. If she studies computer science on a day, then the probability that she studies mathematics the next day is 0.6. If she studies mathematics on a day, then the probability that she studies computer science the next day is 0.4. Given that Aishwarya studies computer science on Monday, what is the probability that she studies computer science on Wednesday? |
| i ➥ 0.24 |
| ii ➥ 0.36 |
| iii ➥ 0.4 |
| iv ➥ 0.6 |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Probability | Help-Line |
| Q28➡ | Engineering Mathematics How many of the following matrices have an eigenvalue 1? |
| i ➥ One |
| ii ➥ Two |
| iii ➥ Three |
| iv ➥ Four |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Linear algebra | Help-Line |
| Q29➡ | Engineering Mathematics Let X be a random variable following normal distribution with mean +1 and variance 4. Let Y be another normal variable with mean -1 and variance unknown. If P(X ≤ -1) = P(Y ≥ 2), the standard deviation of Y is |
| i ➥ 3 |
| ii ➥ 2 |
| iii ➥ √2 |
| iv ➥ 1 |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Probability | Help-Line |
| Q30➡ | Engineering Mathematics Let fsa and pda be two predicates such that fsa(x) means x is a finite state automaton, and pda(y) means that y is a pushdown automaton. Let equivalent be another predicate such that equivalent (a, b) means a and b are equivalent. Which of the following first order logic statements represents the following: Each finite state automaton has an equivalent pushdown automaton |
| i ➥ (∀x fsa(x)) ⇒ (∃y pda(y) ∧ equivalent(x,y)) |
| ii ➥ ∼∀y(∃x fsa(x) ⇒pda(y) ∧ equivalent(x,y)) |
| iii ➥ ∀x ∃y(fsa(x) ∧pda(y) ∧ equivalent(x,y)) |
| iv ➥ ∀x ∃y(fsa(y)∧pda(x) ∧ equivalent(x,y)) |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Propositional logic | Help-Line |
| Q31➡ | Engineering Mathematics P and Q are two propositions. Which of the following logical expressions are equivalent? I. P v ~Q II. ~(~P^Q) III. (P^Q) v (P^~Q) v (~P^~Q) IV. (P^Q) v (P^~Q) v (~P^Q) |
| i ➥ Only I and II |
| ii ➥ Only I, II and III |
| iii ➥ Only I, II and IV |
| iv ➥ All of I, II, III and IV |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Propositional logic | Help-Line |
| Q32➡ | Computer organization For a magnetic disk with concentric circular tracks, the seek latency is not linearly proportional to the seek distance due to |
| i ➥ non-uniform distribution of requests |
| ii ➥ arm starting and stopping inertia |
| iii ➥ higher capacity of tracks on the periphery of the platter |
| iv ➥ use of unfair arm scheduling policies |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Secondary storage | Help-Line |
| Q33➡ | Computer organization Which of the following is/are true of the auto-increment addressing mode? I.It is useful in creating self-relocating code II.If it is included in an Instruction Set Architecture, then an additional ALU is required for effective address calculation III.The amount of increment depends on the size of the data item accessed |
| i ➥ I only |
| ii ➥ II only |
| iii ➥ III only |
| iv ➥ II and III only |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Addressing modes | Help-Line |
| Q34➡ | Computer organization Which of the following must be true for the RFE (Return From Exception) instruction on a general purpose processor? I.It must be a trap instruction II.It must be a privileged instruction III.An exception cannot be allowed to occur during execution of an RFE instruction |
| i ➥ I only |
| ii ➥ II only |
| iii ➥ I and II only |
| iv ➥ I, II and III only |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Machine instructions | Help-Line |
| Q35➡ | Computer organization For inclusion to hold between two cache levels L1 and L2 in a multi-level cache hierarchy, which of the following are necessary? I.L1 must be a write-through cache II.L2 must be a write-through cache III.The associativity of L2 must be greater than that of L1 IV.The L2 cache must be at least as large as the L1 cache |
| i ➥ IV only |
| ii ➥ I and IV only |
| iii ➥ I, III and IV only |
| iv ➥ I, II, III and IV only |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Cache | Help-Line |
| Q36➡ | Computer organization Which of the following are NOT true in a pipelined processor? I.Bypassing can handle all RAW hazards II.Register renaming can eliminate all register carried WAR hazards III.Control hazard penalties can be eliminated by dynamic branch prediction |
| i ➥ I and II only |
| ii ➥ I and III only |
| iii ➥ II and III only |
| iv ➥ I, II and III |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Pipelining | Help-Line |
| Q37➡ | Computer organization The use of multiple register windows with overlap causes a reduction in the number of memory accesses for I.Function locals and parameters II.Register saves and restores III.Instruction fetches |
| i ➥ I only |
| ii ➥ II only |
| iii ➥ III only |
| iv ➥ I, II and III |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Run time environments | Help-Line |
| Q38➡ | Computer organization In an instruction execution pipeline, the earliest that the data TLB (Translation Lookaside Buffer) can be accessed is |
| i ➥ Before effective address calculation has started |
| ii ➥ During effective address calculation |
| iii ➥ After effective address calculation has completed |
| iv ➥ After data cache lookup has completed |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Virtual memory | Help-Line |
| Q39➡ | Algorithms Consider the following functions: f (n) = 2n g(n) = n! h (n) = nlogn Which of the following statements about the asymptotic behaviour of f(n), g(n), and h(n) is true? |
| i ➥ f(n) = O(g(n)); g(n) = O(h(n)) |
| ii ➥ f(n) = Ω(g(n)); g(n) = O(h(n)) |
| iii ➥ g(n) = O(f(n)); h(n) = O(f(n)) |
| iv ➥ h(n) = O(f(n)); g(n) = Ω(f(n)) |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Time complexity | Help-Line |
| Q40➡ | Algorithms The minimum number of comparisons required to determine if an integer appears more than n/2 times in a sorted array of n integers is |
| i ➥ θ(n) |
| ii ➥ θ(logn) |
| iii ➥ θ(log*n) |
| iv ➥ θ(1) |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Time complexity | Help-Line |
| Q41➡ | Database management system A B-tree of order 4 is built from scratch by 10 successive insertions. What is the maximum number of node splitting operations that may take place? |
| i ➥ 3 |
| ii ➥ 4 |
| iii ➥ 5 |
| iv ➥ 6 |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | B trees | Help-Line |
| Q42➡ | Data structures G is a graph on n vertices and 2n – 2 edges. The edges of G can be partitioned into two edge-disjoint spanning trees. Which of the following is NOT true for G? |
| i ➥ For every subset of k vertices, the induced subgraph has at most 2k–2 edges |
| ii ➥ The minimum cut in G has at least two edges |
| iii ➥ There are two edge-disjoint paths between every pair to vertices |
| iv ➥ There are two vertex-disjoint paths between every pair of vertices |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Graphs | Help-Line |
| Q43➡ | Algorithms Consider the Quicksort algorithm. Suppose there is a procedure for finding a pivot element which splits the list into two sub-lists each of which contains at least one-fifth of the elements. Let T(n) be the number of comparisons required to sort n elements. Then |
| i ➥T(n) ≤ 2T(n/5) + n |
| ii ➥ T(n) ≤ T(n/5) + T(4n/5) + n |
| iii ➥ T(n) ≤ 2T(4n/5) + n |
| iv ➥ T(n) ≤ 2T(n/2) + n |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Sorting | Help-Line |
| Q44➡ | Algorithms The subset-sum problem is defined as follows: Given a set S of n positive integers and a positive integer W, determine whether there is a subset of S Whose elements sum to W. An algorithm Q solves this problem in O(nW) time. Which of the following statements is false? |
| i ➥ Q solves the subset-sum problem in polynomial time when the input is encoded in unary |
| ii ➥ Q solves the subset-sum problem in polynomial time when the input is encoded in binary |
| iii ➥ The subset sum problem belongs to the class NP |
| iv ➥ The subset sum problem is NP-hard |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | P- NP | Help-Line |
Q45➡ | Algorithms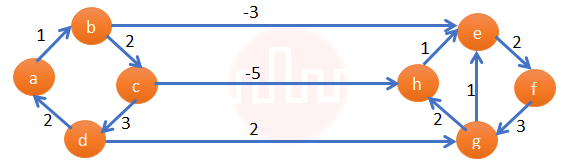 Dijkstra’s single source shortest path algorithm when run from vertex a in the above graph, computes the correct shortest path distance to |
| i ➥ only vertex a |
| ii ➥ only vertices a, e, f, g, h |
| iii ➥ only vertices a, b, c, d |
| iv ➥ all the vertices |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Shortest path | Help-Line |
| Q46➡ | Data structures You are given the postorder traversal, P, of a binary search tree on the n elements 1, 2, …, n. You have to determine the unique binary search tree that has P as its postorder traversal. What is the time complexity of the most efficient algorithm for doing this? |
| i ➥ θ(log n) |
| ii ➥ θ(n) |
| iii ➥ θ(nlog n) |
| iv ➥ None of the above, as the tree cannot be uniquely determined |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Binary search tree | Help-Line |
| Q47➡ | Data structures We have a binary heap on n elements and wish to insert n more elements (not necessarily one after another) into this heap. The total time required for this is |
| i ➥ θ(log n) |
| ii ➥ θ(n) |
| iii ➥ θ(nlog n) |
| iv ➥ θ(n2) |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Heap tree | Help-Line |
| Q48➡ | Theory of computation Which of the following statements is false? |
| i ➥ Every NFA can be converted to an equivalent DFA |
| ii ➥ Every non-deterministic Turing machine can be converted to an equivalent deterministic Turing machine |
| iii ➥ Every regular language is also a context-free language |
| iv ➥ Every subset of a recursively enumerable set is recursive |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Recursive enumerable language | Help-Line |
| Q49➡ | Theory of computation Given below are two finite state automata (–> indicates the start state and F indicates a final state) 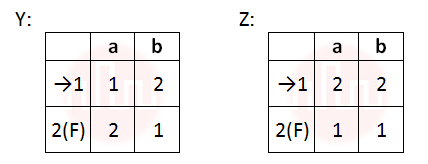 Which of the following represents the product automaton Z×Y? |
i ➥ 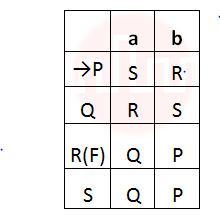 |
ii ➥ 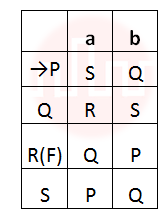 |
iii ➥ 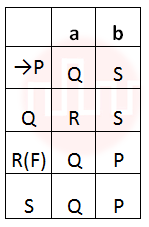 |
iv ➥ 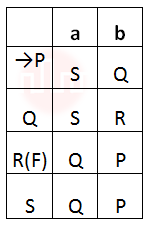 |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Finite automata | Help-Line |
| Q50➡ | Theory of computation Which of the following statements are true? I.Every left-recursive grammar can be converted to a right-recursive grammar and vice-versa II.All e-productions can be removed from any context-free grammar by suitable transformations III.The language generated by a context-free grammar all of whose productions are of the form X –> w or X –> wY (where, w is a string of terminals and Y is a non-terminal), is always regular. IV.The derivation trees of strings generated by a context-free grammar in Chomsky Normal Form are always binary trees |
| i ➥ I, II, III and IV |
| ii ➥ II, III and IV only |
| iii ➥ I, III and IV only |
| iv ➥ I, II and IV only |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Context free grammar | Help-Line |
| Q51➡ | Theory of computation Match the following: 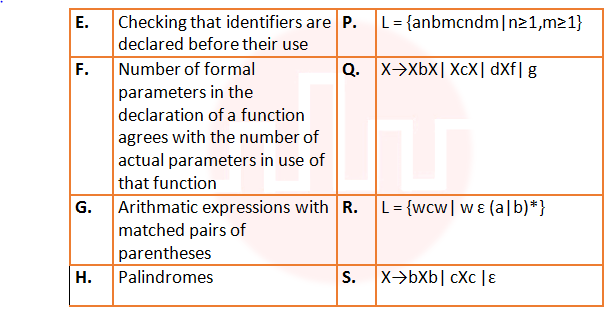 |
| i ➥ E – P, F – R, G – Q, H – S |
| ii ➥ E – R, F – P, G – S, H – Q |
| iii ➥ E – R, F – P, G – Q, H – S |
| iv ➥ E – P, F – R, G – S, H – Q |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Match the following | Help-Line |
| Q52➡ | Theory of computation following NFAs with the regular expressions they correspond to 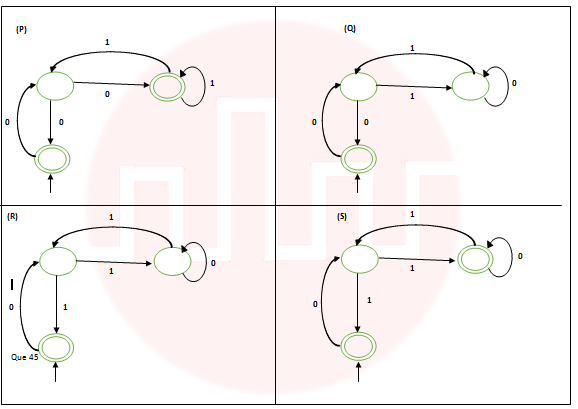 |
| i ➥ P-1, Q-3, R-2, S-4 |
| ii ➥ P-1, Q-3, R-2, S-4 |
| iii ➥ P-1, Q-2, R-3, S-4 |
| iv ➥ P-3, Q-2, R-1, S-4 |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Finite automata | Help-Line |
| Q53➡ | Theory of computation Which of the following are regular sets? I. {anb2m | n >= 0, m >= 0} II. {anbm | n = 2m} III. {anbm | n != 2m} IV. {xcy | x,y ɛ {a,b}*} |
| i ➥ I and IV only |
| ii ➥ I and III only |
| iii ➥ I only |
| iv ➥ IV only |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Regular language | Help-Line |
| Q54➡ | Compiler design Which of the following are true? I.A programming language which does not permit global variables of any kind and has no nesting of procedures/functions, but permits recursion can be implemented with static storage allocation II.Multi-level access link (or display) arrangement is needed to arrange activation records only if the programming language being implemented has nesting of procedures/functions III.Recursion in programming languages cannot be implemented with dynamic storage allocation IV.Nesting procedures/functions and recursion require a dynamic heap allocation scheme and cannot be implemented with a stack-based allocation scheme for activation records V.Programming languages which permit a function to return a function as its result cannot be implemented with a stack-based storage allocation scheme for activation records |
| i ➥ II and IV only |
| ii ➥ I, III and IV only |
| iii ➥ I, II and V only |
| iv ➥ II, III and V only |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Run time enviornments | Help-Line |
| Q55➡ | Compiler design An LALR(1) parser for a grammar G can have shift-reduce (S-R) conflicts if and only if |
| i ➥ the SLR(1) parser for G has S-R conflicts |
| ii ➥ the LR(1) parser for G has S-R conflicts |
| iii ➥ the LR(0) parser for G has S-R conflicts |
| iv ➥ the LALR(1) parser for G has reduce-reduce conflicts |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Parsers | Help-Line |
| Q56➡ | Computer networks In the slow start phase of the TCP congestion control algorithm, the size of the congestion window |
| i ➥ does not increase |
| ii ➥ increases linearly |
| iii ➥ increases quadratically |
| iv ➥ increases exponentially |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | TCP | Help-Line |
| Q57➡ | Computer networks If a class B network on the Internet has a subnet mask of 255.255.248.0, what is the maximum number of hosts per subnet? |
| i ➥ 1022 |
| ii ➥ 1023 |
| iii ➥ 2046 |
| iv ➥ 2047 |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | IP address | Help-Line |
| Q58➡ | Computer networks A computer on a 10Mbps network is regulated by a token bucket. The token bucket is filled at a rate of 2Mbps. It is initially filled to capacity with 16Megabits. What is the maximum duration for which the computer can transmit at the full 10Mbps? |
| i ➥ 1.6 seconds |
| ii ➥ 2 seconds |
| iii ➥ 5 seconds |
| iv ➥ 8 seconds |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Token bucket | Help-Line |
| Q59➡ | Computer networks A client process P needs to make a TCP connection to a server process S. Consider the following situation: the server process S executes a socket (), a bind () and a listen () system call in that order, following which it is preempted. Subsequently, the client process P executes a socket () system call followed by connect () system call to connect to the server process S. The server process has not executed any accept() system call. Which one of the following events could take place? |
| i ➥ connect ( ) system call returns successfully |
| ii ➥ connect ( ) system call blocks |
| iii ➥ connect ( ) system call returns an error |
| iv ➥ connect ( ) system call results in a core dump |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Sockets | Help-Line |
| Q60➡ | Programming What is printed by the following C program? int f (int x, int * py, int * *ppz) void main ( ) { { int y, z; int c, * b, * *a; * *ppz + = 1; z = *ppz; c = 4; b = &c; a = &b; * py + = 2; y = *py; pr int f (” %d”, f (c, b, a)); x + = 3; } return x + y + z; } |
| i ➥ 18 |
| ii ➥ 19 |
| iii ➥ 21 |
| iv ➥ 22 |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | C Programming | Help-Line |
| Q61➡ | Programming Choose the correct option to fill ? 1 and ? 2 so that the program below prints an input string in reverse order. Assume that the input string is terminated by a newline character. void reverse (void){ int c; if (?1)reverse ( ); ? 2 } main ( ) { pr int f (“Enter Text “); pr int f (“\ n “); reverse ( );pr int f (“\ n “); } |
| i ➥ ?1 is (getchar( ) != ’\n’) ?2 is getchar(c); |
| ii ➥ ?1 is (c = getchar( ) ) != ’\n’) ?2 is getchar(c); |
| iii ➥ ?1 is (c != ’\n’) ?2 is putchar(c); |
| iv ➥ ?1 is ((c = getchar()) != ’\n’) ?2 is putchar(c); |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | C Programming | Help-Line |
| Q62➡ | Data structures The following C function takes a single-linked list of integers as a parameter and rearranges the elements of the list. The function is called with the list containing the integers 1,2,3,4,5,6,7 in the given order. What will be the contents of the list after the function completes execution? struct node { int value; struct node * next; }; Void rearrange (struct node * list){ struct node * p, * q; int temp; if (!list !list – > next)return; p = list; q = list – > next; while (q) { temp = p- >value;p- > value = q- > value; q- > value = temp;p = q- > next; q = p ? p- > next : 0; } } |
| i ➥ 1,2,3,4,5,6,7 |
| ii ➥ 2,1,4,3,6,5,7 |
| iii ➥ 1,3,2,5,4,7,6 |
| iv ➥ 2,3,4,5,6,7,1 |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Linked list | Help-Line |
| Q63➡ | Operating system |
| i ➥ 0 and 0 |
| ii ➥ 0 and 1 |
| iii ➥ 1 and 0 |
| iv ➥ 1 and 1 |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Process synchronization | Help-Line |
| Q64➡ | Operating system Which of the following statements about synchronous and asynchronous I/O is NOT true? |
| i ➥ An ISR is invoked on completion of I/O in synchronous I/O but not in asynchronous I/O |
| ii ➥ In both synchronous and asynchronous I/O, an ISR (Interrupt Service Routine) is invoked after completion of the I/O |
| iii ➥ A process making a synchronous I/O call waits until I/O is complete, but a process making an asynchronous I/O call does not wait for completion of the I/O |
| iv ➥ In the case of synchronous I/O, the process waiting for the completion of I/O is woken up by the ISR that is invoked after the completion of I/O |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | I/O handling | Help-Line |
| Q65➡ | Operating system Which of the following is NOT true of deadlock prevention and deadlock avoidance schemes? |
| i ➥ In deadlock prevention, the request for resources is always granted if the resulting state is safe |
| ii ➥ In deadlock avoidance, the request for resources is always granted if the result state is safe |
| iii ➥ Deadlock avoidance is less restrictive than deadlock prevention |
| iv ➥ Deadlock avoidance requires knowledge of resource requirements a priori |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Deadlock | Help-Line |
| Q66➡ | Operating system A process executes the following code for (i =0; i < n; i + +) for ( ); The total number of child processes created is |
| i ➥ n |
| ii ➥ (2n) – 1 |
| iii ➥ 2n |
| iv ➥ (2n+1) – 1 |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | System calls | Help-Line |
| Q67➡ | Operating system A processor uses 36 bit physical addresses and 32 bit virtual addresses, with a page frame size of 4 Kbytes. Each page table entry is of size 4 bytes. A three level page table is used for virtual to physical address translation, where the virtual address is used as follows • Bits 30-31 are used to index into the first level page table • Bits 21-29 are used to index into the second level page table • Bits 12-20 are used to index into the third level page table, and • Bits 0-11 are used as offset within the page The number of bits required for addressing the next level page table (or page frame) in the page table entry of the first, second and third level page tables are respectively |
| i ➥ 20, 20 and 20 |
| ii ➥ 24, 24 and 24 |
| iii ➥ 24, 24 and 20 |
| iv ➥ 25, 25 and 24 |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Virtual memory | Help-Line |
| Q68➡ | Database Management system Let R and S be two relations with the following schema |
| i ➥ Only I and II |
| ii ➥ Only I, II and III |
| iii ➥ Only I and III |
| iv ➥ Only I, III and IV |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Relational algebra | Help-Line |
| Q69➡ | Database Management system Consider the following relational schemes for a library database: Book(Title, Author, Catalog_ no, Publisher, Year, Pr ice) Collection (Title, Author, Catalog_ no) with in the following functional dependencies: I.Title Author ® Catalog_no II.Catalog_no ® Title Author Publisher Year III.Publisher Title Year ® Pr ice Assume {Author, Title} is the key for both schemes. Which of the following statements is true? |
| i ➥ Both Book and Collection are in BCNF |
| ii ➥ Both Book and Collection are in 3NF only |
| iii ➥ Book is in 2NF and Collection is in 3NF |
| iv ➥ Both Book and Collection are in 2NF only |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Normalization | Help-Line |
| Q70➡ | Database Management system Consider a file of 16384 records. Each record is 32 bytes long and its key field is of size 6 bytes. The file is ordered on a non-key field, and the file organization is unspanned. The file is stored in a file system with block size 1024 bytes, and the size of a block pointer is 10 bytes. If the secondary index is built on the key field of the file, and a multi-level index scheme is used to store the secondary index, the number of first-level and second-level blocks in the multi-level index are respectively |
| i ➥ 8 and 0 |
| ii ➥ 128 and 6 |
| iii ➥ 256 and 4 |
| iv ➥ 512 and 5 |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Indexing | Help-Line |
| Q71➡ | Computer organization Consider a machine with a 2-way set associative data cache of size 64Kbytes and block size 16bytes. The cache is managed using 32 bit virtual addresses and the page size is 4Kbyts. A program to be run on this machine begins as follows: double ARR [1024][1024]; int i, j ; /* Initialize array ARR to 0.0 * / for (i = 0;i < 1024; i + +) for (j = 0; j < 1024; j + +) ARR [i] [j] = 0.0; The size of double is 8Bytes. Array ARR is located in memory starting at the beginning of virtual page 0xFF000 and stored in row major order. The cache is initially empty and no pre-fetching is done. The only data memory references made by the program are those to array ARR The total size of the tags in the cache directory is |
| i ➥ 32Kbits |
| ii ➥ 34Kbits |
| iii ➥ 64Kbits |
| iv ➥ 68Kbits |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Cache | Help-Line |
| Q72➡ | Computer organization Consider a machine with a 2-way set associative data cache of size 64Kbytes and block size 16bytes. The cache is managed using 32 bit virtual addresses and the page size is 4Kbyts. A program to be run on this machine begins as follows: double ARR [1024][1024]; int i, j ; /* Initialize array ARR to 0.0 * / for (i = 0;i < 1024; i + +) for (j = 0; j < 1024; j + +) ARR [i] [j] = 0.0; The size of double is 8Bytes. Array ARR is located in memory starting at the beginning of virtual page 0xFF000 and stored in row major order. The cache is initially empty and no pre-fetching is done. The only data memory references made by the program are those to array ARR. Which of the following array elements has the same cache index as ARR [0] [0]? |
| i ➥ ARR [0] [4] |
| ii ➥ ARR [4] [0] |
| iii ➥ ARR [0] [5] |
| iv ➥ ARR [5] [0] |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Cache | Help-Line |
| Q73➡ | Computer organization Consider a machine with a 2-way set associative data cache of size 64Kbytes and block size 16bytes. The cache is managed using 32 bit virtual addresses and the page size is 4Kbyts. A program to be run on this machine begins as follows: double ARR [1024][1024]; int i, j ; /* Initialize array ARR to 0.0 * / for (i = 0;i < 1024; i + +) for (j = 0; j < 1024; j + +) ARR [i] [j] = 0.0; The size of double is 8Bytes. Array ARR is located in memory starting at the beginning of virtual page 0xFF000 and stored in row major order. The cache is initially empty and no pre-fetching is done. The only data memory references made by the program are those to array ARR The cache hit ratio for this initialization loop is |
| i ➥ 0% |
| ii ➥ 25% |
| iii ➥ 50% |
| iv ➥ 75% |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Cache | Help-Line |
| Q74➡ | Algorithms |
| i ➥ θ(n) and θ(n) |
| ii ➥ θ(2n) and θ(n) |
| iii ➥ θ(n) and θ(2n) |
| iv ➥ θ(2n) and θ(2n) |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Time complexity | Help-Line |
| Q75➡ | Programming |
| i ➥ 1661 and 1640 |
| ii ➥ 59 and 59 |
| iii ➥ 1640 and 1640 |
| iv ➥ 1640 and 1661 |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | C programming | Help-Line |
| Q76➡ | Computer organization Delayed branching can help in the handling of control hazards For all delayed conditional branch instructions, irrespective of whether the condition evaluates to true or false |
| i ➥ The instruction following the conditional branch instruction in memory is executed. |
| ii ➥ The first instruction in the fall through path is executed. |
| iii ➥ The first instruction in the taken path is executed. |
| iv ➥ The branch takes longer to execute than any other instruction. |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q77➡ | Computer organization Delayed branching can help in the handling of control hazards The following code is to run on a pipelined processor with one branch delay slot: I1 : ADD R2 ¬ R7 + R8 I2 : SUB R4 ¬ R5 – R6 I3 : ADD R1 ¬ R2 + R3 I4 : STORE Memory [R4] ¬ R1 BRANCH to Label if R1 = = 0 Which of the instructions I1, I2, I3 or I4 can legitimately occupy the delay slot without any other program modification? |
| i ➥ I1 |
| ii ➥ I2 |
| iii ➥ I3 |
| iv ➥ I4 |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Pipelining | Help-Line |
| Q78➡ | Algorithms Let xn denote the number of binary strings of length n that contain no consecutive 0s. Which of the following recurrences does xn satisfy? |
| i ➥ xn = 2xn-1 |
| ii ➥ xn = x⌊n/2⌋+1 |
| iii ➥ xn = x⌊n/2⌋+n |
| iv ➥ xn = xn-1+xn-2 |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Recurrence | Help-Line |
| Q79➡ | Algorithms Let xn denote the number of binary strings of length n that contain no consecutive 0s. The value of x5 is |
| i ➥ 5 |
| ii ➥ 7 |
| iii ➥ 8 |
| iv ➥ 16 |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Recurrence | Help-Line |
| Q80➡ | Algorithms The subset-sum problem is defined as follows. Given a set of n positive integers, S={a1,a2,a3,…,an}, and positive integer W, is there a subset of S whose elements sum to W? A dynamic program for solving this problem uses a 2-dimensional Boolean array, X, with n rows and W+1 columns. X[i,j],1≤i≤n,0≤j≤W, is TRUE, if and only if there is a subset of {a1,a2,…,ai} whose elements sum to j. Which of the following is valid for 2≤i≤n, and ai≤j≤W? |
| i ➥ X[i, j] = X[i – 1, j] ∨ X[i, j – ai] |
| ii ➥ X[i, j] = X[i – 1, j] ∨ X[i – 1, j – ai] |
| iii ➥ X[i, j] = X[i – 1, j] ∧ X[i, j – ai] |
| iv ➥ X[i, j] = X[i – 1, j] ∧ X[i -1, j – ai] |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Dynamic programming | Help-Line |
| Q81➡ | Algorithms The subset-sum problem is defined as follows. Given a set of n positive integers, S={a1,a2,a3,…,an}, and positive integer W, is there a subset of S whose elements sum to W? A dynamic program for solving this problem uses a 2-dimensional Boolean array, X, with n rows and W+1 columns. X[i,j],1≤i≤n,0≤j≤W, is TRUE, if and only if there is a subset of {a1,a2,…,ai} whose elements sum to j. Which entry of the array X, if TRUE, implies that there is a subset whose elements sum to W? |
| i ➥ X[1, W] |
| ii ➥ X[n, 0] |
| iii ➥ X[n, W] |
| iv ➥ X[n-1, n] |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Dynamic programming | Help-Line |
| Q82➡ | Database Management system Consider the following ER diagram 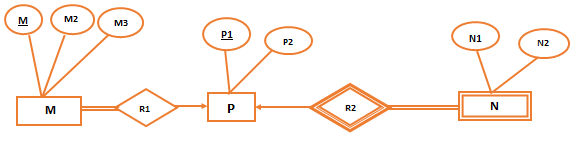 The minimum number of tables needed to represent M, N, P, R1, R2 is |
| i ➥ 2 |
| ii ➥ 3 |
| iii ➥ 4 |
| iv ➥ 5 |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | ER-model | Help-Line |
| Q83➡ | Database Management system Consider the following ER diagram 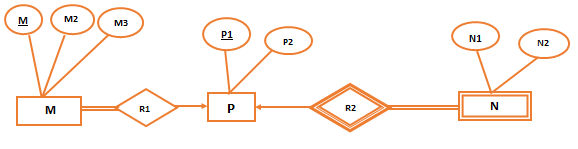 Which of the following is a correct attribute set for one of the tables for the correct answer to the above question? |
| i ➥ {M1, M2, M3, P1} |
| ii ➥ {M1, P1, N1, N2} |
| iii ➥ {M1, P1, N1} |
| iv ➥ {M1, P1} |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | ER-model | Help-Line |
| Q84➡ | Algorithms Consider the following C program that attempts to locate an element x in an array Y[ ] using binary search. The program is erroneous. On which of the following contents of Y and x does the program fail? |
| i ➥ Y is [1 2 3 4 5 6 7 8 9 10] and x < 10 |
| ii ➥ Y is [1 3 5 7 9 11 13 15 17 19] and x < 1 |
| iii ➥ Y is [2 2 2 2 2 2 2 2 2 2] and x > 2 |
| iv ➥ Y is [2 4 6 8 10 12 14 16 18 20] and 2 < x < 20 and x is even |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Binary search | Help-Line |
| Q85➡ | Algorithms Consider the following C program that attempts to locate an element x in an array Y[ ] using binary search. The program is erroneous. The correction needed in the program to make it work properly is |
| i ➥ Change line 6 to: if (Y[k] < x) i = k + 1; else j = k-1; |
| ii ➥ Change line 6 to: if (Y[k] < x) i = k – 1; else j = k+1; |
| iii ➥ Change line 6 to: if (Y[k] <= x) i = k; else j = k; |
| iv ➥ Change line 7 to: } while ((Y[k] == x) && (i < j)); |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Binary search | Help-Line |
| Q27➡ | |
| i ➥ |
| ii ➥ |
| iii ➥ |
| iv ➥ |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q27➡ | |
| i ➥ |
| ii ➥ |
| iii ➥ |
| iv ➥ |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q27➡ | |
| i ➥ |
| ii ➥ |
| iii ➥ |
| iv ➥ |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q27➡ | |
| i ➥ |
| ii ➥ |
| iii ➥ |
| iv ➥ |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q27➡ | |
| i ➥ |
| ii ➥ |
| iii ➥ |
| iv ➥ |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q27➡ | |
| i ➥ |
| ii ➥ |
| iii ➥ |
| iv ➥ |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q27➡ | |
| i ➥ |
| ii ➥ |
| iii ➥ |
| iv ➥ |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q27➡ | |
| i ➥ |
| ii ➥ |
| iii ➥ |
| iv ➥ |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q27➡ | |
| i ➥ |
| ii ➥ |
| iii ➥ |
| iv ➥ |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q27➡ | |
| i ➥ |
| ii ➥ |
| iii ➥ |
| iv ➥ |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q27➡ | |
| i ➥ |
| ii ➥ |
| iii ➥ |
| iv ➥ |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
