GATE CSE 2009 PYQ
| Q1➡ | Engineering Mathematics Which one of the following in NOT necessarily a property of a Group? |
| i ➥ Commutativity |
| ii ➥ Associativity |
| iii ➥ Existence of inverse for every element |
| iv ➥ Existence of identity |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Group | Help-Line |
| Q2➡ | Engineering Mathematics What is the chromatic number of an n-vertex simple connected graph which does not contain any odd length cycle? Assume n ≥ 2. |
| i ➥ 2 |
| ii ➥ 3 |
| iii ➥ n-1 |
| iv ➥ n |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Graph theory | Help-Line |
| Q3➡ | Engineering Mathematics Which one of the following is TRUE for any simple connected undirected graph with more than 2 vertices? |
| i ➥ No two vertices have the same degree. |
| ii ➥ At least two vertices have the same degree. |
| iii ➥ At least three vertices have the same degree. |
| iv ➥ All vertices have the same degree. |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Graph theory | Help-Line |
| Q4➡ | Engineering Mathematics Consider the binary relation R = {(x, y), (x, z), (z, x), (z, y)} on the set {x, y, z}. Which one of the following is TRUE? |
| i ➥ R is symmetric but NOT antisymmetric |
| ii ➥ but R is NOT symmetric antisymmetric |
| iii ➥ R is both symmetric and antisymmetric |
| iv ➥ R is neither symmetric nor antisymmetric |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Set and relation | Help-Line |
| Q5➡ | Digital Logic design (1217)8 is equivalent to |
| i ➥ (1217)16 |
| ii ➥ (028F)16 |
| iii ➥ (2297)16 |
| iv ➥ (0B17)16 |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Number systems | Help-Line |
| Q6➡ | Digital Logic design What is the minimum number of gates required to implement the Boolean function (AB+C) if we have to use only 2-input NOR gates? |
| i ➥ 2 |
| ii ➥ 3 |
| iii ➥ 4 |
| iv ➥ 5 |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Logic gates | Help-Line |
| Q7➡ | Digital Logic design How many 32K × 1 RAM chips are needed to provide a memory capacity of 256K-bytes? |
| i ➥ 8 |
| ii ➥ 32 |
| iii ➥ 64 |
| iv ➥ 128 |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Memory Interfacing | Help-Line |
| Q8➡ | Computer Organization A CPU generally handles an interrupt by executing an interrupt service routine |
| i ➥ As soon as an interrupt is raised. |
| ii ➥ By checking the interrupt register at the end of fetch cycle. |
| iii ➥ By checking the interrupt register after finishing the execution of the current instruction. |
| iv ➥ By checking the interrupt register at fixed time intervals. |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Interrupt | Help-Line |
| Q9➡ | Operating system In which one of the following page replacement policies, Belady’s anomaly may occur? |
| i ➥ FIFO |
| ii ➥ Optimal |
| iii ➥ LRU |
| iv ➥ MRU |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Page replacement | Help-Line |
| Q10➡ | Operating system The essential content(s) in each entry of a page table is / are |
| i ➥ Virtual page number |
| ii ➥ Page frame number |
| iii ➥ Both virtual page number and page frame number |
| iv ➥ Access right information |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Page replacement | Help-Line |
| Q11➡ | Algorithms What is the number of swaps required to sort n elements using selection sort, in the worst case? |
| i ➥ θ(n) |
| ii ➥ θ(n log n) |
| iii ➥ θ(n2) |
| iv ➥ θ(n2 logn) |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Sorting | Help-Line |
| Q12➡ | Theory of computation S → aSa|bSb|a|b; The language generated by the above grammar over the alphabet {a,b} is the set of |
| i ➥ All palindromes. |
| ii ➥ All odd length palindromes. |
| iii ➥ Strings that begin and end with the same symbol. |
| iv ➥ All even length palindromes. |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Context free language | Help-Line |
| Q13➡ | Algorithms Which of the following statement(s) is / are correct regarding Bellman-Ford shortest path algorithm? P. Always finds a negative weighted cycle, if one Q. Finds whether any negative weighted cycle is reachable from the source. |
| i ➥ P Only |
| ii ➥ Q Only |
| iii ➥ Both P and Q |
| iv ➥ Neither P nor Q |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Shortest path | Help-Line |
| Q14➡ | Algorithms Let πA be a problem that belongs to the class NP. Then which one of the following is TRUE? |
| i ➥ There is no polynomial time algorithm for πA. |
| ii ➥ If πA can be solved deterministically in polynomial time,then P = NP. |
| iii ➥ If πA is NP-hard, then it is NP-complete. |
| iv ➥ πA may be undecidable. |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | P-NP | Help-Line |
| Q15➡ | Theory of computation Which one of the following languages over the alphabet {0,1} is described by the regular expression: (0+1)*0(0+1)*0(0+1)*? |
| i ➥ The set of all strings containing the substring 00. |
| ii ➥ The set of all strings containing at most two 0’s. |
| iii ➥ The set of all strings containing at least two 0’s. |
| iv ➥ The set of all strings that begin and end with either 0 or 1. |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Regular Expressions | Help-Line |
| Q16➡ | Theory of computation Which one of the following is FALSE? |
| i ➥ There is unique minimal DFA for every regular language. |
| ii ➥ Every NFA can be converted to an equivalent PDA. |
| iii ➥ Complement of every context-free language is recursive. |
| iv ➥ Every non-deterministic PDA can be converted to an equivalent deterministic PDA. |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | NFA | Help-Line |
| Q17➡ | Compiler design Match all items in Group 1 with correct options from those given in Group 2 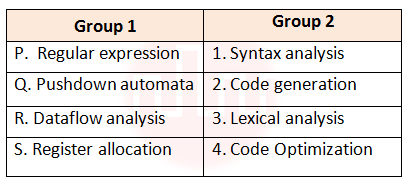 |
| i ➥ P-4, Q-1, R-2, S-3 |
| ii ➥ P-3, Q-1, R-4, S-2 |
| iii ➥ P-3, Q-4, R-1, S-2 |
| iv ➥ P-2, Q-1, R-4, S-3 |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Compilers | Help-Line |
| Q18➡ | Programming Consider the program below: # include int fun(int n, int * f_p) { int t, f; if (n <= 1) { * f_p = 1; return 1; } t = fun (n- 1, f_p); f = t+ * f_p; * f_p = t; return f; } int main() { int x = 15; printf (” % d\ n”, fun(5, & x)); return 0; } The value printed is: |
| i ➥ 6 |
| ii ➥ 8 |
| iii ➥ 14 |
| iv ➥ 15 |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | C Programming | Help-Line |
| Q19➡ | Software Engineering The coupling between different modules of a software is categorized as follows: I. Content coupling II. Common coupling III. Control coupling IV .Stamp coupling V. Data coupling Coupling between modules can be ranked in the order of strongest (least desirable) to weakest (most desirable) as follows: |
| i ➥ I-II-III-IV-V |
| ii ➥ V-IV-III-II-I |
| iii ➥ I-III-V-II-IV |
| iv ➥ IV-II-V-III-I |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q20➡ | Programming Consider the HTML Table definition given below: The number of rows in each column and the number of columns in each row are: |
| i ➥ (2, 2, 3) and (2, 3, 2) |
| ii ➥ (2, 2, 3) and (2, 2, 3) |
| iii ➥ (2, 3, 2) and (2, 3, 2) |
| iv ➥ (2, 3, 2) and (2, 2, 3) |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Learn Topic Wise | Help-Line |
| Q21➡ | Engineering Mathematics An unbalanced dice (with 6 faces, numbered from 1 to 6) is thrown. The probability that the face value is odd is 90% of the probability that the face value is even. The probability of getting any even numbered face is the same If the probability that the face is even given that it is greater than 3 is 0.75, which one of the following options is closest to the probability that the face value exceeds 3? |
| i ➥ 0.453 |
| ii ➥ 0.468 |
| iii ➥ 0.485 |
| iv ➥ 0.492 |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Probability | Help-Line |
| Q22➡ | Engineering Mathematics For the composition table of a cyclic group shown belown 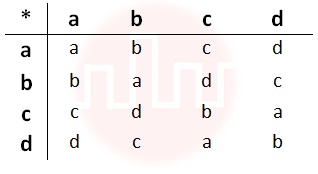 Which one of the following choices is correct? |
| i ➥ a, b are generators |
| ii ➥ b, c are generators |
| iii ➥ c, d are generators |
| iv ➥ d, a are generators |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Set and relation | Help-Line |
| Q23➡ | Engineering Mathematics Which one of the following is the most appropriate logical formula to represent the statement? “Gold and silver ornaments are precious”. The following notations are used: G(x): x is a gold ornament S(x): x is a silver ornament P(x): x is precious |
| i ➥ ∀x(P(x) → (G(x) ∧ S(x))) |
| ii ➥ ∀x((G(x) ∧ S(x)) → P(x)) |
| iii ➥ ∃x((G(x) ∧ S(x)) → P(x) |
| iv ➥ ∀x((G(x) ∨ S(x)) → P(x)) |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Propositional logic | Help-Line |
| Q24➡ | Engineering Mathematics The binary operation □ is defined as follows : 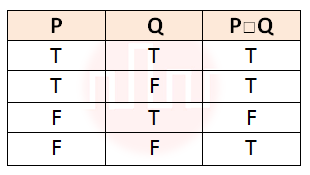 Which one of the following is equivalent to P V Q ? |
| i ➥ ¬Q □ ¬P |
| ii ➥ P □ ¬Q |
| iii ➥ ¬P □ Q |
| iv ➥ ¬P □ ¬Q |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Propositional logic | Help-Line |
| Q25➡ | Engineering Mathematics is equivalent to |
| i ➥ 0 |
| ii ➥ 1 |
| iii ➥ ln 2 |
| iv ➥ 1/2 ln 2 |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Calculus | Help-Line |
| Q26➡ | Engineering Mathematics Consider the following well-formed formulae: I. ¬∀x(P(x)) II. ¬∃(P(x)) III. ¬∃(¬P(x)) IV. ∃x(¬(P(x)) Which of the above are equivalent? |
| i ➥ I and III |
| ii ➥ I and IV |
| iii ➥ II and III |
| iv ➥ II and IV |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Propositional logic | Help-Line |
| Q27➡ | Theory of computation Given the following state table of an FSM with two states A and B, one input and one output: 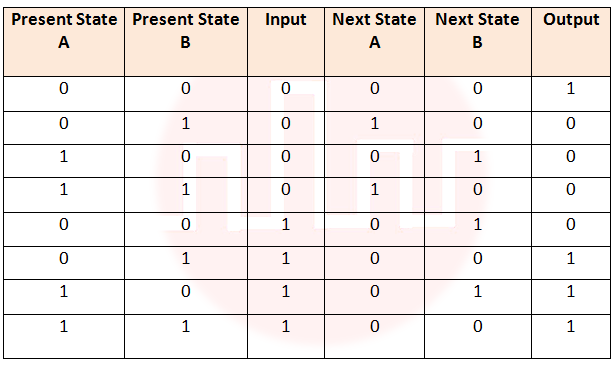 If the initial state is A = 0, B=0, what is the minimum length of an input string which will take the machine to the state A=0, B=1 with Output=1? |
| i ➥ 3 |
| ii ➥ 4 |
| iii ➥ 5 |
| iv ➥ 6 |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Finite automata | Help-Line |
| Q28➡ | Computer organization Consider a 4 stage pipeline processor. The number of cycles needed by the four instructions I1, I2, I3, I4 in stages S1, S2, S3, S4 is shown below: 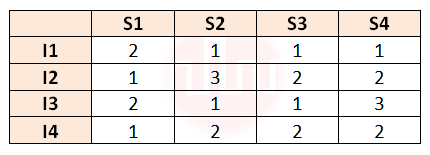 What is the number of cycles needed to execute the following loop? For (i=1 to 2) {I1; I2; I3; I4;} |
| i ➥ 16 |
| ii ➥ 23 |
| iii ➥ 28 |
| iv ➥ 30 |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Pipelining | Help-Line |
| Q29➡ | Computer organization Consider a 4-way set associative cache (initially empty) with total 16 cache blocks. The main memory consists of 256 blocks and the request for memory blocks is in the following order: 0, 255, 1, 4, 3, 8, 133, 159, 216, 129, 63, 8, 48, 32, 73, 92, 155. Which one of the following memory block will NOT be in cache if LRU replacement policy is used? |
| i ➥ 3 |
| ii ➥ 8 |
| iii ➥ 129 |
| iv ➥ 216 |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Cache | Help-Line |
| Q30➡ | Operating system Consider a system with 4 types of resources R1 (3 units), R2 (2 units), R3 (3 units), R4 (2 units). A non-preemptive resource allocation policy is used. At any given instance, a request is not entertained if it cannot be completely satisfied. Three processes P1, P2, P3 request the sources as follows if executed independently. 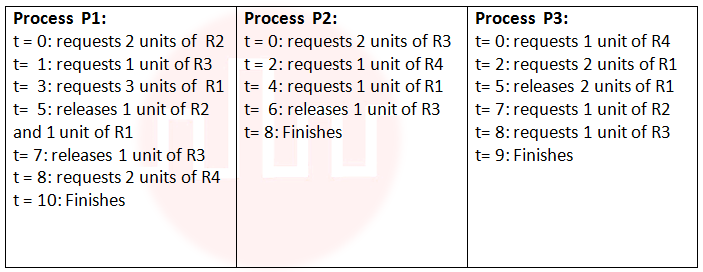 Which one of the following statements is TRUE if all three processes run concurrently starting at time t=0? |
| i ➥ All processes will finish without any deadlock. |
| ii ➥ Only P1 and P2 will be in deadlock. |
| iii ➥ Only P1 and P3 will be in deadlock. |
| iv ➥ All three processes will be in deadlock. |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Deadlock | Help-Line |
| Q31➡ | Operating system Consider a disk system with 100 cylinders. The requests to access the cylinders occur in following sequence: 4, 34, 10, 7, 19, 73, 2, 15, 6, 20 Assuming that the head is currently at cylinder 50, what is the time taken to satisfy all requests if it takes 1ms to move from one cylinder to adjacent one and shortest seek time first policy is used? |
| i ➥ 95 ms |
| ii ➥ 119 ms |
| iii ➥ 233 ms |
| iv ➥ 276 ms |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | CPU Scheduling | Help-Line |
| Q32➡ | Operating system In the following process state transition diagram for a uniprocessor system, assume that there are always some processes in the ready state: 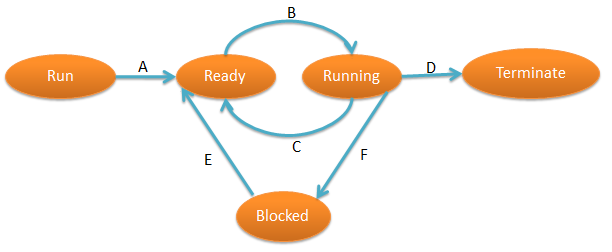 Now consider the following statements: I. If a process makes a transition D, it would result in another process making transition A immediately. II. A process P2 in blocked state can make transition E while another process P1 is in running state. III. The OS uses preemptive scheduling. IV. The OS uses non-preemptive scheduling. Which of the above statements are TRUE? |
| i ➥ I and II |
| ii ➥ I and III |
| iii ➥ II and III |
| iv ➥ II and IV |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Process Scheduling | Help-Line |
| Q33➡ | Operating system The enter_CS() and leave_CS() functions to implement critical section of a process are realized using test-and-set instruction as follows: void enter_CS(X) { while (test-and-set(X)); } void leave_CS(X) { X=0; } In the above solution, X is a memory location associated with the CS and is initialized to 0. Now consider the following statements: I.The above solution to CS problem is deadlock-free II.The solution is starvation III.The processes enter CS in FIFO IV.More than one process can enter CS at the same time. Which of the above statements is TRUE? |
| i ➥ I only |
| ii ➥ I and II |
| iii ➥ II and III |
| iv ➥ IV only |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Process synchronization | Help-Line |
| Q34➡ | Operating Systems A multilevel page table is preferred in comparison to a single level page table for translating virtual address to physical address because |
| i ➥ It reduces the memory access time to read or write a memory location. |
| ii ➥ It helps to reduce the size of page table needed to implement the virtual address space of a process. |
| iii ➥ It is required by the translation lookaside buffer. |
| iv ➥ It helps to reduce the number of page faults in page replacement algorithms. |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Virtual Memory | Help-Line |
| Q35➡ | Algorithms The running time of an algorithm is represented by the following recurrence relation: Which one of the following represents the time complexity of the algorithm? |
| i ➥ θ(n) |
| ii ➥ θ(n log n) |
| iii ➥ θ(n2) |
| iv ➥ θ(n2log n ) |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Time Complexity | Help-Line |
| Q36➡ | Data Structures The keys 12, 18, 13, 2, 3, 23, 5 and 15 are inserted into an initially empty hash table of length 10 using open addressing with hash function h(k) = k mod 10 and linear probing. What is the resultant hash table? |
i ➥  |
ii ➥ 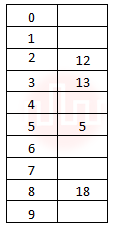 |
iii ➥ 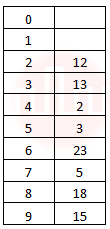 |
iv ➥ 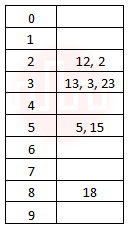 |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Hashing | Help-Line |
| Q37➡ | Data Structures What is the maximum height of any AVL-tree with 7 nodes? Assume that the height of a tree with a single node is 0. |
| i ➥ 2 |
| ii ➥ 3 |
| iii ➥ 4 |
| iv ➥ 5 |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | AVL Trees | Help-Line |
| Q38➡ | Algorithms Consider the following graph 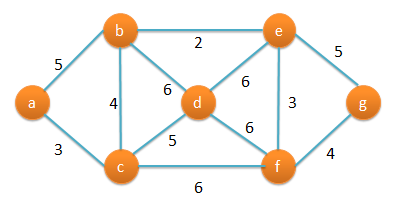 Which one of the following is NOT the sequence of edges added to the minimum spanning tree using Kruskal’s algorithm? |
| i ➥ (b,e)(e,f)(a,c)(b,c)(f,g)(c,d) |
| ii ➥ (b,e)(e,f)(a,c)(f,g)(b,c)(c,d) |
| iii ➥ (b,e)(a,c)(e,f)(b,c)(f,g)(c,d) |
| iv ➥ (b,e)(e,f)(b,c)(a,c)(f,g)(c,d) |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Minimum Spanning Tree | Help-Line |
| Q39➡ | Algorithms In quick sort, for sorting n elements, the (n/4)th smallest element is selected as pivot using an O(n) time algorithm. What is the worst case time complexity of the quick sort? |
| i ➥ θ(n) |
| ii ➥ θ(n log n) |
| iii ➥ θ(n2) |
| iv ➥ θ(n2 log n ) |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Sorting | Help-Line |
| Q40➡ | Theory of Computation Let L = L1 ∩ L2, where L1 and L2 are languages as defined below: L1 = {ambmcanbn | m,n ≥ 0 } L2 = {aibjck | i,j,k ≥ 0 } Then L is |
| i ➥ Not recursive |
| ii ➥ Regular |
| iii ➥ Context free but not regular |
| iv ➥ Recursively enumerable but not context free |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Identify class language | Help-Line |
| Q41➡ | Theory of Computation The above DFA accepts the set of all strings over {0,1} 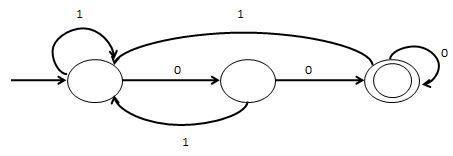 that |
| i ➥ begin either with 0 or 1 |
| ii ➥ end with 0 |
| iii ➥ end with 00 |
| iv ➥ contain the substring 00 |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Finite automata | Help-Line |
| Q42➡ | Compiler design Which of the following statements are TRUE? I.There exist parsing algorithms for some programming languages whose complexities are less than q (n3 ). II.A programming language which allows recursion can be implemented with static storage III.No L-attributed definition can be evaluated in the framework of bottom-up parsing. IV.Code improving transformations can be performed at both source language and intermediate code level |
| i ➥ I and II |
| ii ➥ I and IV |
| iii ➥ III and IV |
| iv ➥ I,III and IV |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Parsers | Help-Line |
| Q43➡ | Database Management System Consider two transactions T1 and T2, and four schedules S1, S2, S3, S4 of T1 and T2 as given below: T1 = R1[X] W1[X] W1[Y] T2 = R2[X] R2[Y] W2[Y] S1 = R1[X] R2[X] R2[Y] W1[X] W1[Y] W2[Y] S2 = R1[X] R2[X] R2[Y] W1[X] W2[Y] W1[Y] S3 = R1[X] W1[X] R2[X] W1[Y] R2[Y] W2[Y] S1 = R1[X] R2[Y]R2[X]W1[X] W1[Y] W2[Y] Which of the above schedules are conflict-serializable? |
| i ➥ S1 and S2 |
| ii ➥ S2 and S3 |
| iii ➥ S3 ONLY |
| iv ➥ S4 ONLY |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Transactions | Help-Line |
| Q44➡ | Database Management System The following key values are inserted into a B+ tree in which order of the internal nodes is 3, and that of the leaf nodes is 2, in the sequence given below. The order of internal nodes is the maximum number of tree pointers in each node, and the order of leaf nodes is the maximum number of data items that can be stored in it. The B+ tree is initially 10, 3, 6, 8, 4, 2, 1 The maximum number of times leaf nodes would get split up as a result of these insertions is |
| i ➥ 2 |
| ii ➥ 3 |
| iii ➥ 4 |
| iv ➥ 5 |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | B+ Trees | Help-Line |
| Q45➡ | Database Management System Let R and S be relational schemes such that R={a,b,c} and S={c}. Now consider the following queries on the database: I. πR-S(r)-πR-S(πR-S(r)×s-πR-S,S(r)) II. {t|t∈ πR-S(r) ∧ ∀u ∈ s(∃v ∈ r(u = v[s] ∧ t = v[R – S]))} III. {t|t∈ πR-S(r) ∧ ∀v ∈ r(∃u ∈ s(u = v[s] ∧ t = v[R – S]))} IV. Select R.a, R.b from R, S where R.c = S.c Which of the above queries are equivalent? |
| i ➥ I and II |
| ii ➥ I and III |
| iii ➥ II and IV |
| iv ➥ III and IV |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Relational Calculus | Help-Line |
| Q46➡ | Computer network In the RSA public key cryptosystem, the private and public keys are (e,n) and (d,n) respectively, where n=p*q and p and q are large primes. Besides, n is public and p and q are private. Let M be an integer such that 0 < M < n and f(n) = (p- 1)(q-1). Now consider the following equations. I. M’= Me mod n M = (M’)d mod n II. ed ≡ 1 mod n III. ed ≡ 1 mod f(n) IV. M’= Me mod f(n) M = (M’)d mod f(n) Which of the above equations correctly represent RSA cryptosystem? |
| i ➥ I and II |
| ii ➥ I and III |
| iii ➥ II and IV |
| iv ➥ III and IV |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Network security | Help-Line |
| Q47➡ | Computer network While opening a TCP connection, the initial sequence number is to be derived using a time-of-day (ToD) clock that keeps running even when the host is down. The low order 32 bits of the counter of the ToD clock is to be used for the initial sequence numbers. The clock counter increments once per millisecond. The maximum packet lifetime is given to be Which one of the choices given below is closest to the minimum permissible rate at which sequence numbers used for packets of a connection can increase? |
| i ➥ 0.015/s |
| ii ➥ 0.064/s |
| iii ➥ 0.135/s |
| iv ➥ 0.327/s |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | TCP | Help-Line |
| Q48➡ | Computer network Let G(x) be the generator polynomial used for CRC checking. What is the condition that should be satisfied by G(x) to detect odd number of bits in error? |
| i ➥ G(x) contains more than two terms. |
| ii ➥ G(x) does not divide 1+xk, for any k not exceeding the frame length. |
| iii ➥ 1+x is a factor of G(x). |
| iv ➥ G(x) has an odd number of terms. |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Error detection | Help-Line |
| Q49➡ Software Engineering Which of the following statements are TRUE? I.The context diagram should depict the system as a single bubble. II.External entities should be identified clearly at all levels of DFDs. III. Control information should not be represented in a DFD. IV. A data store can be connected either to another data store or to an external entity. |
| i ➥ II and III |
| ii ➥ I, II and IV |
| iii ➥ I and III |
| iv ➥ I, II and III |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | DFD | Help-Line |
| Q50➡ | Software Engineering Consider the following statements about the cyclomatic complexity of the control flow graph of a program module. Which of these are TRUE? I.The cyclomatic complexity of a module is equal to the maximum number of linearly independent circuits in the graph II.The cyclomatic complexity of a module is the number of decisions in the module plus one, where a decision is effectively any conditional statement in the module III.The cyclomatic complexity can also be used as a number of linearly independent paths that should be tested during path coverage testing. |
| i ➥ I and II |
| ii ➥ II and III |
| iii ➥ I and III |
| iv ➥ I, II and III |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Cyclomatic Complexity | Help-Line |
| Q51➡ | Computer organization A hard disk has 63 sectors per track, 10 platters each with 2 recording surfaces and 1000 cylinders. The address of a sector is given as a triple c, h, s , where , where c is the cylinder number, h is the surface number and s is the sector number. Thus, the 0th sector is addressed as 0, 0, 0 , the 1st sector as 0, 0,1 , and so on. The address <400, 16, 29> corresponds to sector number: |
| i ➥ 505035 |
| ii ➥ 505036 |
| iii ➥ 505037 |
| iv ➥ 505038 |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Secondary storage | Help-Line |
| Q52➡ | Computer organization A hard disk has 63 sectors per track, 10 platters each with 2 recording surfaces and 1000 cylinders. The address of a sector is given as a triple , where c is the cylinder number, h is the surface number and s is the sector number. Thus, the 0th sector is addressed as <0, 0, 0>, the 1st sector as <0,0,1>, and so on. The address of the 1039th sector is |
| i ➥ (0, 15, 31) |
| ii ➥ (0, 16, 30) |
| iii ➥ (0, 16, 31) |
| iv ➥ (0, 17, 31) |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Secondary storage | Help-Line |
| Q53➡ | Algorithms A sub-sequence of a given sequence is just the given sequence with some elements (possibly none or all) left out. We are given two sequences X[m] and Y[n] of lengths m and n respectively, with indexes of X and Y starting from 0. We wish to find the length of the longest common sub-sequence(LCS) of X[m] and Y[n] as l(m,n), where an incomplete recursive definition for the function l(i,j) to compute the length of The LCS of X[m] and Y[n] is given below: l(i,j) = 0, if either i=0 or j=0 = expr1, if i,j> 0 and X[i-1] = Y[j-1] = expr2, if i,j> 0 and X[i-1] != Y[j-1] Which one of the following options is correct? |
| i ➥ expr1 ≡ l(i-1, j) + 1 |
| ii ➥ expr1 ≡ l(i, j-1) |
| iii ➥ expr2 ≡ max(l(i-1, j), l(i, j-1)) |
| iv ➥ expr2 ≡ max(l(i-1,j-1), l(i,j)) |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Dynamic programming | Help-Line |
| Q54➡ | Algorithms A sub-sequence of a given sequence is just the given sequence with some elements (possibly none or all) left out. We are given two sequences X[m] and Y[n] of lengths m and n, respectively, with indexes of X and Y starting from 0. The values of l(i,j) could be obtained by dynamic programming based on the correct recursive definition of l(i,j) of the form given above, using an array L[M,N], where M = m+1 and N=n+1, such that L[i,j] = l(i,j). Which one of the following statements would be TRUE regarding the dynamic programming solution for the recursive definition of l(i,j)? |
| i ➥ All elements L should be initialized to 0 for the values of l(i,j) to be properly computed. |
| ii ➥ The values of l(i,j) may be computed in a row major order or column major order of L(M,N). |
| iii ➥ The values of l(i,j) cannot be computed in either row major order or column major order of L(M,N). |
| iv ➥ L[p,q] needs to be computed before L[r,s] if either p<=”” div=””> |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Dynamic programming | Help-Line |
| Q55➡ | Database management system Consider the following relational schema: Suppliers(sid:integer, sname:string, city:string, street:string) Parts(pid:integer, pname:string, color:string) Catalog(sid:integer, pid:integer, cost:real) Consider the following relational query on the above database SELECT S.snameAssume that relations corresponding to the above schema are not empty. Which one of the following is the correct interpretation of the above query? |
| i ➥ Find the names of all suppliers who have supplied a non-blue part. |
| ii ➥ Find the names of all suppliers who have not supplied a non-blue part. |
| iii ➥ Find the names of all suppliers who have supplied only blue parts. |
| iv ➥ Find the names of all suppliers who have not supplied only blue parts. |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Normalization | Help-Line |
| Q57➡ | Computer network Frames of 1000 bits are sent over a 106 bps duplex link between two hosts. The propagation time is 25ms. Frames are to be transmitted into this link to maximally pack them in transit (within the link). What is the minimum number of bits (l) that will be required to represent the sequence numbers distinctly? Assume that no time gap needs to be given between transmission of two frames. |
| i ➥ I = 2 |
| ii ➥ I = 3 |
| iii ➥ I = 4 |
| iv ➥ I = 5 |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Sliding window protocol | Help-Line |
| Q58➡ | Computer network Frames of 1000 bits are sent over a 106 bps duplex link between two hosts. The propagation time is 25ms. Frames are to be transmitted into this link to maximally pack them in transit (within the link). Suppose that the sliding window protocol is used with the sender window size of 2l, where l is the number of bits identified in the earlier part and acknowledgements are always piggy backed. After sending 2l frames, what is the minimum time the sender will have to wait before starting transmission of the next frame? (Identify the closest choice ignoring the frame processing time.) |
| i ➥ 16ms |
| ii ➥ 18ms |
| iii ➥ 20ms |
| iv ➥ 22ms |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Sliding window protocol | Help-Line |
| Q59➡ | Data structure Consider a binary max-heap implemented using an array. Which one of the following array represents a binary max-heap? |
| i ➥ {25,12,16,13,10,8,14} |
| ii ➥ {25,14,13,16,10,8,12} |
| iii ➥ {25,14,16,13,10,8,12} |
| iv ➥ {25,14,12,13,10,8,16} |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Heap tree | Help-Line |
| Q60➡ | Data structures Consider a binary max-heap implemented using an array. What is the content of the array after two delete operations on the correct answer to the previous question? |
| i ➥ {14,13,12,10,8} |
| ii ➥ {14,12,13,8,10} |
| iii ➥ {14,13,8,12,10} |
| iv ➥ {14,13,12,8,10} |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Heap tree | Help-Line |
