UGC NET CSA JUNE 2015 Paper-3
Q1➡ |
i ➥ ii ➥ iii ➥ iv ➥ 11000110
Show Answer With Best Explanation Answer: II
More Discussion Explanation On YouTube Number systems Help-Line
Q2➡ |
i ➥ 6 bytes/secii ➥ 6 bytes/seciii ➥ 6 bytes/seciv ➥ 4 × 10 6 bytes/sec
Show Answer With Best Explanation Answer: II
More Discussion Explanation On YouTube Microprocessor Help-Line
Q3➡ |
i ➥ ii ➥ iii ➥ iv ➥ CALL 003C H
Show Answer With Best Explanation Answer: III
More Discussion Explanation On YouTube Microprocessor Help-Line
Q4➡ |
i ➥ ii ➥ iii ➥ iv ➥ ACABE
Show Answer With Best Explanation Answer: III
More Discussion Explanation On YouTube Number systems Help-Line
Q5➡ |
i ➥ ii ➥ iii ➥ iv ➥ 250 Kbytes/sec
Show Answer With Best Explanation Answer: IV
More Discussion Explanation On YouTube Microprogrammed control unit Help-Line
Q6➡ |
i ➥ ii ➥ iii ➥ iv ➥ 11
Show Answer With Best Explanation Answer: II
More Discussion Explanation On YouTube Sequential circuits Help-Line
Q7➡ | 1 and R 2 are two relationships between E 1 and E 2 where R 1 is one – many and R 2 is many – many. R 1 and R 2 do not have any attributes of their own. How many minimum number of tables are required to represent this situation in the Relational Model?
Show Answer With Best Explanation Answer: II
More Discussion Explanation On YouTube ER-Model Help-Line
Q8➡ |
i ➥ ii ➥ iii ➥ iv ➥
Show Answer With Best Explanation Answer: II
More Discussion Explanation On YouTube Learn Topic Wise Help-Line
Q9➡ |
i ➥ ii ➥ iii ➥ iv ➥ BCNF is stronger than 3NF
Show Answer With Best Explanation Answer: II
More Discussion Explanation On YouTube Normalization Help-Line
Q10➡ |
i ➥ ii ➥ iii ➥ iv ➥ None of the above
Show Answer With Best Explanation Answer: IV
More Discussion Explanation On YouTube Normalization Help-Line
Q11➡ | 1 and R 2 form a Lossless join decomposition of R if and only if:1 ∩ R 2 ↠ (R 1 – R 2 )1 → R 2 1 ∩ R 2 ↠ (R 2 – R 1 )2 → R 1 ) ∩ R 2
i ➥ ii ➥ iii ➥ iv ➥ (b) and (c) happens
Show Answer With Best Explanation Answer: III
More Discussion Explanation On YouTube Functional dependency Help-Line
Q12➡ |
i ➥ ii ➥ iii ➥ iv ➥ Size of Block
Show Answer With Best Explanation Answer: II
More Discussion Explanation On YouTube File system Help-Line
Q13➡ |
i ➥ ii ➥ iii ➥ iv ➥ Only two in the directions J and K
Show Answer With Best Explanation Answer: I
More Discussion Explanation On YouTube Transformations Help-Line
Q14➡ |
Show Answer With Best Explanation Answer: III
More Discussion Explanation On YouTube Co-ordinate geometry Help-Line
Q15➡ |
i ➥ ii ➥ iii ➥ iv ➥ Quantization
Show Answer With Best Explanation Answer: IV
More Discussion Explanation On YouTube Signals Help-Line
Q16➡ |
i ➥ ii ➥ iii ➥ iv ➥ POLYMARKER
Show Answer With Best Explanation Answer: II
More Discussion Explanation On YouTube Graphics Help-Line
Q17➡ |
i ➥ ii ➥ iii ➥ iv ➥ Left – handed coordinate system in which the display area of the virtual display device corresponds to the unit (|x|) square whose lower left-hand corner is at the origin of the coordinate system, is known as normalized device coordinate system.
Show Answer With Best Explanation Answer: IV
More Discussion Explanation On YouTube Co-ordinate geometry Help-Line
Q18➡ |
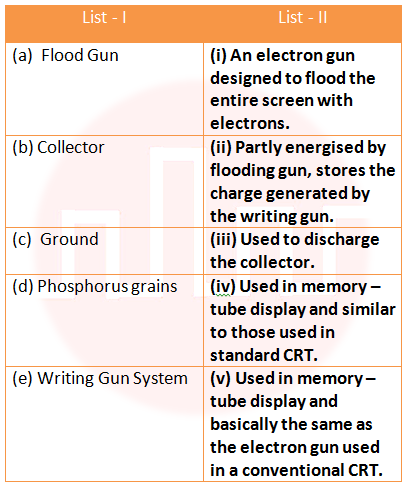
i ➥ ii ➥ iii ➥ iv ➥ (iv), (b)-(v), (c)-(i), (d)-(ii), (e)-(iii)
Show Answer With Best Explanation Answer: I
More Discussion Explanation On YouTube Display system Help-Line
Q19➡ |
i ➥ ii ➥ iii ➥ iv ➥ 5 final states among 6 states
Show Answer With Best Explanation Answer: IV
More Discussion Explanation On YouTube Finite automata Help-Line
Q20➡ |
i ➥ ii ➥ iii ➥ iv ➥ (10 + 01) * 01
Show Answer With Best Explanation Answer: III
More Discussion Explanation On YouTube Regular expression Help-Line
i ➥ 0 and q 0 respectivelyii ➥ 0 and q 1 respectivelyiii ➥ 0 and q 2 respectivelyiv ➥ q 0 and q 3 respectively
Show Answer With Best Explanation Answer: IV
More Discussion Explanation On YouTube Finite automata Help-Line
Q22➡ |
i ➥ ii ➥ iii ➥ iv ➥ A ∧ B ∧ C ∧ D ⇒ false
Show Answer With Best Explanation Answer: I
More Discussion Explanation On YouTube Propositional logic Help-Line
Q23➡ |
i ➥ ii ➥ iii ➥ iv ➥ The scope of a variable in PROLOG is a single query
Show Answer With Best Explanation Answer: II
More Discussion Explanation On YouTube PROLOG Help-Line
Q24➡ |
i ➥ ii ➥ iii ➥ iv ➥ If we resolve a negated goal G against a fact or rule A to get clause C then C has positive literal or null goal
Show Answer With Best Explanation Answer: II
More Discussion Explanation On YouTube Horn clause Help-Line
Q25➡ |
i ➥ ii ➥ iii ➥ iv ➥ Circuit switching
Show Answer With Best Explanation Answer: IV
More Discussion Explanation On YouTube Transmission techniques Help-Line
Q26➡ |
i ➥ ii ➥ iii ➥ iv ➥ PSH
Show Answer With Best Explanation Answer: I
More Discussion Explanation On YouTube TCP/IP Help-Line
Q27➡ |
i ➥ ii ➥ iii ➥ iv ➥ Pre Shared and transport
Show Answer With Best Explanation Answer: II
More Discussion Explanation On YouTube IP header Help-Line
Q28➡ |
i ➥ ii ➥ iii ➥ iv ➥ UEKPNRMROOEWCTT
Show Answer With Best Explanation Answer: III
More Discussion Explanation On YouTube Network security Help-Line
Q29➡ |
i ➥ ii ➥ iii ➥ iv ➥ 256 kbps
Show Answer With Best Explanation Answer: III
More Discussion Explanation On YouTube Signals Help-Line
Q30➡ |
i ➥ ii ➥ iii ➥ iv ➥ 65,475
Show Answer With Best Explanation Answer: III
More Discussion Explanation On YouTube TCP/IP Help-Line
Q31➡ |
i ➥ ii ➥ iii ➥ iv ➥ Floyd-Warshall algorithm
Show Answer With Best Explanation Answer: IV
More Discussion Explanation On YouTube Dynamic programming Help-Line
Q32➡ |
i ➥ ii ➥ iii ➥ iv ➥ Polynomial time using backtracking algorithm
Show Answer With Best Explanation Answer: III
More Discussion Explanation On YouTube Dynamic programming Help-Line
Q33➡ |
i ➥ ii ➥ iii ➥ iv ➥ lg*(n!)
Show Answer With Best Explanation Answer: I
More Discussion Explanation On YouTube Asymptotic complexity Help-Line
Q34➡ |
i ➥ ii ➥ iii ➥ iv ➥ 89
Show Answer With Best Explanation Answer: III
More Discussion Explanation On YouTube Hashing Help-Line
Q35➡ |
i ➥ ii ➥ iii ➥ iv ➥ θ(f(n)+g(n)) = max(f(n), g(n))
Show Answer With Best Explanation Answer: IV
More Discussion Explanation On YouTube Asymptotic complexity Help-Line
Q36➡ | ______
i ➥ ii ➥ h iii ➥ h )⌉iv ➥ ⌈n/z h+1 )
Show Answer With Best Explanation Answer: None of the above
More Discussion Explanation On YouTube Heap tree Help-Line
Q37➡ |
i ➥ ii ➥ iii ➥ iv ➥ Friend
Show Answer With Best Explanation Answer: III
More Discussion Explanation On YouTube Java Help-Line
Q38➡ | __
i ➥ ii ➥ iii ➥ iv ➥
Show Answer With Best Explanation Answer: IV
More Discussion Explanation On YouTube Client server application Help-Line
Q39➡ |
i ➥ ii ➥ iii ➥ iv ➥ Applets are embedded in another applications
Show Answer With Best Explanation Answer: IV
More Discussion Explanation On YouTube Java Help-Line
Q40➡ |
i ➥ ii ➥ iii ➥ iv ➥ -*?
Show Answer With Best Explanation Answer: III
More Discussion Explanation On YouTube XML Help-Line
Q41➡ | __
i ➥ ii ➥ iii ➥ iv ➥ Document type language
Show Answer With Best Explanation Answer: I
More Discussion Explanation On YouTube XML Help-Line
Q42➡ |
i ➥ ii ➥ iii ➥ iv ➥ Abstraction
Show Answer With Best Explanation Answer: III
More Discussion Explanation On YouTube Coupling and cohesion Help-Line
i ➥ ii ➥ iii ➥ iv ➥ both (A) and (B)
Show Answer With Best Explanation Answer: IV
More Discussion Explanation On YouTube Software configuration management Help-Line
Q44➡ |
i ➥ ii ➥ iii ➥ iv ➥ Accuracy
Show Answer With Best Explanation Answer: II
More Discussion Explanation On YouTube Software design Help-Line
Q45➡ |
i ➥ ii ➥ iii ➥ iv ➥ Requirements reviews
Show Answer With Best Explanation Answer: II
More Discussion Explanation On YouTube Software requirements Help-Line
Q46➡ | _______
i ➥ ii ➥ iii ➥ iv ➥ both (2) and (3)
Show Answer With Best Explanation Answer: II
More Discussion Explanation On YouTube Software configuration management Help-Line
Q47➡ |
i ➥ ii ➥ iii ➥ iv ➥
Show Answer With Best Explanation Answer: IV
More Discussion Explanation On YouTube Software reliability Help-Line
Q48➡ |
i ➥ ii ➥ iii ➥ iv ➥ cohesion is functional and coupling is stamp type.
Show Answer With Best Explanation Answer: I
More Discussion Explanation On YouTube Software design Help-Line
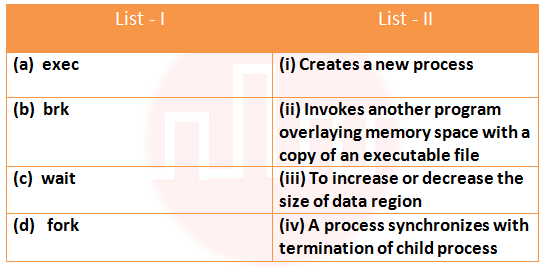
Q49➡ |
i ➥ ii ➥ iii ➥ iv ➥ (a)-(ii), (b)-(iii), (c)-(iv), (d)-(i)
Show Answer With Best Explanation Answer: II
More Discussion Explanation On YouTube Match the following Help-Line
Q50➡ |
i ➥ ii ➥ iii ➥ iv ➥ This algorithm can be configured to match a specific system under design
Show Answer With Best Explanation Answer: III
More Discussion Explanation On YouTube Process scheduling Help-Line
Q51➡ |
i ➥ ii ➥ iii ➥ iv ➥ It is an algorithm to allocate and deallocate main memory to a process
Show Answer With Best Explanation Answer: III
More Discussion Explanation On YouTube Memory management Help-Line
Q52➡ |
i ➥ ii ➥ iii ➥ iv ➥
Show Answer With Best Explanation Answer: II
More Discussion Explanation On YouTube Process synchronization Help-Line
Q53➡ | _____
i ➥ ii ➥ iii ➥ iv ➥ Bitmap
Show Answer With Best Explanation Answer: III
More Discussion Explanation On YouTube File system Help-Line
Q54➡ |
i ➥ ii ➥ iii ➥ iv ➥
Show Answer With Best Explanation Answer: IV
More Discussion Explanation On YouTube Unix operating system Help-Line
Q55➡ |
i ➥ ii ➥ iii ➥ iv ➥
Show Answer With Best Explanation Answer: II
More Discussion Explanation On YouTube Knowledge representation Help-Line
Q56➡ |
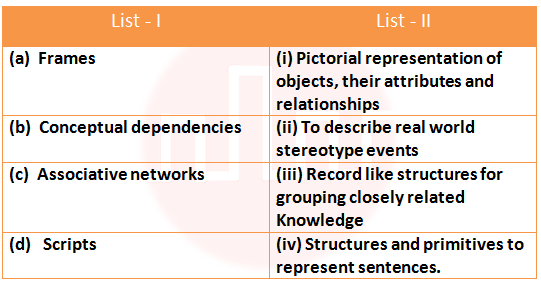
i ➥ ii ➥ iii ➥ iv ➥ (a)-(iv), (b)-(iii), (c)-(ii), (d)-(i)
Show Answer With Best Explanation Answer: I
More Discussion Explanation On YouTube Computer science basics Help-Line
Q57➡ |
i ➥ ii ➥ iii ➥ iv ➥
Show Answer With Best Explanation Answer: II
More Discussion Explanation On YouTube Propositional logic Help-Line
Q58➡ |
i ➥ ii ➥ iii ➥ iv ➥
Show Answer With Best Explanation Answer: None of the above
More Discussion Explanation On YouTube Branch and bound Help-Line
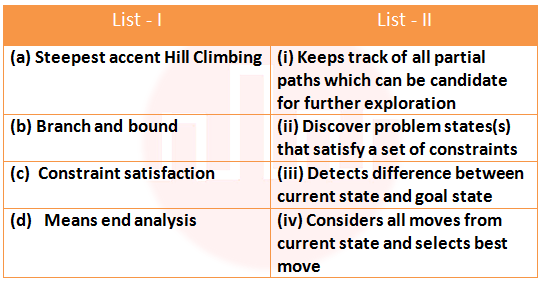
Q59➡ |
i ➥ ii ➥ iii ➥ iv ➥ (a)-(iv), (b)-(ii), (c)-(i), (d)-(iii)
Show Answer With Best Explanation Answer: II
More Discussion Explanation On YouTube Hill climbing algorithm Help-Line
Q60➡ |
i ➥ ii ➥ iii ➥ iv ➥
Show Answer With Best Explanation Answer: II
More Discussion Explanation On YouTube Software design Help-Line
Q61➡ | 0 (w) > n1 (w) } is given by:
i ➥ ii ➥ iii ➥ iv ➥ S → 0 S |1 S | 0 | 1
Show Answer With Best Explanation Answer: III
More Discussion Explanation On YouTube Context free grammar Help-Line
Q62➡ |
i ➥ ii ➥ iii ➥ iv ➥
Show Answer With Best Explanation Answer: IV
More Discussion Explanation On YouTube Recursive and recursive enumerable language Help-Line
Q63➡ |
i ➥ ii ➥ iii ➥ iv ➥ both G 1 and G 2 are unambiguous grammars
Show Answer With Best Explanation Answer: III
More Discussion Explanation On YouTube Context free grammar Help-Line
Q64➡ |
i ➥ ii ➥ iii ➥ iv ➥
Show Answer With Best Explanation Answer: None of the above
More Discussion Explanation On YouTube Greedy approach Help-Line
Q65➡ |
i ➥ ii ➥ iii ➥ iv ➥ image size
Show Answer With Best Explanation Answer: II
More Discussion Explanation On YouTube Graphics Help-Line
Q66➡ |
i ➥ r – 1ii ➥ r – r – 1iii ➥ r – r + 1iv ➥ r + r – 1
Show Answer With Best Explanation Answer: II
More Discussion Explanation On YouTube Number systems Help-Line
Q67➡ |
i ➥ ii ➥ iii ➥ iv ➥ rows + columns + 1
Show Answer With Best Explanation Answer: I
More Discussion Explanation On YouTube Assignment problem Help-Line
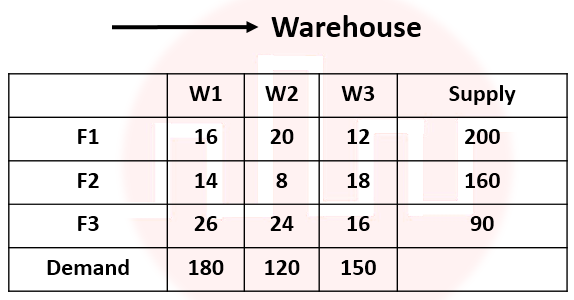
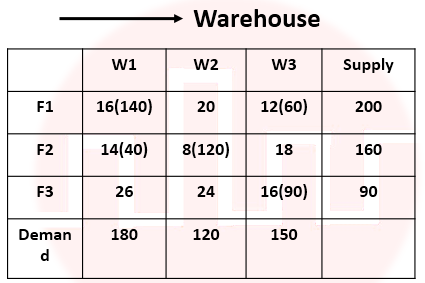
Q68➡ |
i ➥ ii ➥ iii ➥ iv ➥ is infeasible solution
Show Answer With Best Explanation Answer: II
More Discussion Explanation On YouTube Transportation problem Help-Line
Q69➡ |
i ➥ ii ➥ iii ➥ iv ➥ S 1 , S 2 and S 3
Show Answer With Best Explanation Answer: IV
More Discussion Explanation On YouTube Duality Help-Line
Q70➡ |
i ➥ ii ➥ iii ➥ iv ➥ {(11, 0.3), ,(12, 0.5), (13, 0.6), (14, 1), (15, 0.7), (16, 0.5), (17, 0.2)}
Show Answer With Best Explanation Answer: IV
More Discussion Explanation On YouTube Fuzzy logic Help-Line
Q71➡ | 2 + 2.
i ➥ ii ➥ iii ➥ iv ➥ {(2, 0.6), (3, 0.3), (6, 0.6), (11, 0.3)}
Show Answer With Best Explanation Answer: III
More Discussion Explanation On YouTube Fuzzy logic Help-Line
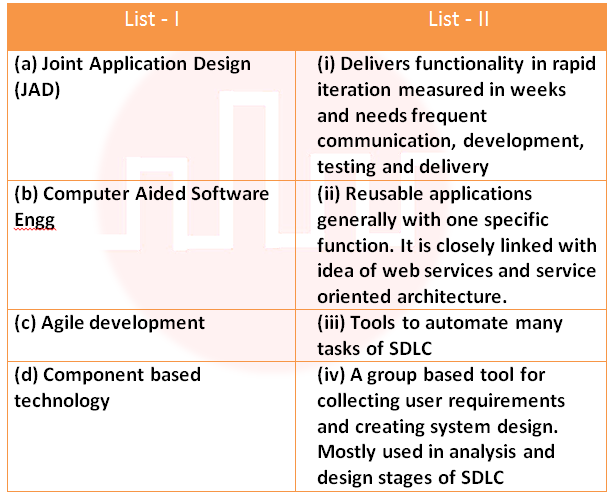
Q72➡ |
i ➥ ii ➥ iii ➥ iv ➥ (a)-(iv), (b)-(iii), (c)-(i), (d)-(ii)
Show Answer With Best Explanation Answer: I
More Discussion Explanation On YouTube Learn Topic Wise Help-Line
i ➥ ii ➥ iii ➥ iv ➥ Special execution environment used to run 16 bit Windows applications on 32 – bit machines.
Show Answer With Best Explanation Answer: IV
More Discussion Explanation On YouTube Win32 Help-Line
Q74➡ |
i ➥ ii ➥ iii ➥ iv ➥ Edits file1 first, saves it and then edits file2
Show Answer With Best Explanation Answer: II
More Discussion Explanation On YouTube Unix operating system Help-Line