GATE 2015 SET-3 CS Computer Science and information technology
[Q1 – Q25 carry ONE mark each ]
| Q1➡ | Programming Consider the following C program segment. 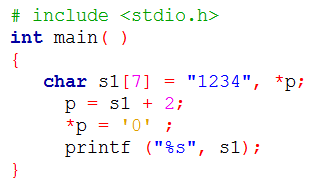 What will be printed by the program? |
| i ➥ 12 |
| ii ➥ 120400 |
| iii ➥ 1204 |
| iv ➥ 1034 |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Program | Help-Line |
| Q2➡ | Engineering Mathematics Suppose U is the power set of the set S = {1, 2, 3, 4, 5, 6}. For any T ∈ U, let |T| denote the number of element in T and T’ denote the complement of T. For any T, R ∈ U, let TR be the set of all elements in T which are not in R. Which one of the following is true? |
| i ➥ ∀X ∈ U (|X| = |X’|) |
| ii ➥ ∃X ∈ U ∃Y ∈ U (|X| = 5, |Y| = 5 and X ∩ Y = ∅) |
| iii ➥ ∀X ∈ U ∀Y ∈ U (|X| = 2, |Y| = 3 and X \ Y = ∅) |
| iv ➥ ∀X ∈ U ∀Y ∈ U (X \ Y = Y’ \ X’) |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Set Theory | Help-Line |
| Q3➡ | Database Management System Consider the relation X(P, Q, R, S, T, U) with the following set of functional dependencies F = { {P, R} → {S,T}, {P, S, U} → {Q, R} } Which of the following is the trivial functional dependency in F+, Where F+ is closure of F? |
| i ➥ {P,R}→{S,T} |
| ii ➥ {P,R}→{R,T} |
| iii ➥ {P,S}→{S} |
| iv ➥ {P,S,U}→{Q} |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Functional Dependency | Help-Line |
| Q4➡ | Operating Systems The maximum number of processes that can be in Ready state for a computer system with n CPUs is |
| i ➥ n |
| ii ➥ n2 |
| iii ➥ 2n |
| iv ➥ Independent of n |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Process Scheduling | Help-Line |
| Q5➡ | Compiler Design Among simple LR (SLR), canonical LR, and look-ahead LR (LALR), which of the following pairs identify the method that is very easy to implement and the method that is the most powerful, in that order? |
| i ➥ SLR, LALR |
| ii ➥ Canonical LR, LALR |
| iii ➥ SLR, canonical LR |
| iv ➥ LALR, canonical LR |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Parsers | Help-Line |
| Q6➡ | Digital Logic Design Let # be a binary operator defined as X # Y = X′ + Y′ where X and Y are Boolean variables. Consider the following two statements. S1: (P # Q) # R = P # (Q # R) S2: Q # R = R # Q Which of the following is/are true for the Boolean variables P, Q and R? |
| i ➥ Only S1 is True |
| ii ➥ Only S2 is True |
| iii ➥ Both S1 and S2 are True |
| iv ➥ Neither S1 nor S2 are True |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Boolean Algebra | Help-Line |
| Q7➡ | Software Engineering Consider a software project with the following information domain characteristic for calculation of function point metric. Number of external inputs (I) = 30 Number of external output (O) = 60 Number of external inquiries (E) = 23 Number of files (F) = 08 Number of external interfaces (N) = 02 It is given that the complexity weighting factors for I, O, E, F and N are 4, 5, 4, 10 and 7, respectively. It is also given that, out of fourteen value adjustment factors that influence the development effort, four factors are not applicable, each of he other four factors have value 3, and each of the remaining factors have value 4. The computed value of function point metric is _________. |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Function Points | Help-Line |
| Q8➡ | Web Technology In a web server, ten WebPages are stored with the URLs of the form http://www.yourname.com/var.html; where, var is a different number from 1 to 10 for each Webpage. Suppose, the client stores the Webpage with var = 1 (say W1) in local machine, edits and then tests. Rest of the WebPages remains on the web server. W1 contains several relative URLs of the form “var.html” referring to the other WebPages. Which one of the following statements needs to be added in W1, so that all the relative URLs in W1 refer to the appropriate WebPages on the web server? |
| i ➥ |
| ii ➥ |
| ii ➥ |
| iv ➥ |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Web Technology | Help-Line |
| Q9➡ | Computer Network Consider the following statements. I. TCP connections are full duplex. II. TCP has no option for selective acknowledgment. III. TCP connections are message streams. |
| i ➥ Only I is correct |
| ii ➥ Only I and III are correct |
| iii ➥ Only II and III are correct |
| iv ➥ All of I, II and III are correct |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | TCP | Help-Line |
| Q10➡ | Theory of Computation consider the equality 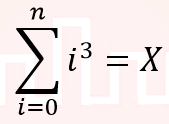 and the following choices for X and the following choices for XI. θ(n4) II. θ(n5) III. Ο(n5) IV. Ω(n3) The equality above remains correct if X is replaced by |
| i ➥ Only I |
| ii ➥ Only II |
| iii ➥ I or III or IV but not II |
| iv ➥ II or III or IV but not I |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Decidability and Undecidability | Help-Line |
| Q11➡ | Data Structure Consider a binary tree T that has 200 leaf nodes. Then, the number of nodes in T that have exactly two children are ________. |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Binary Tree | Help-Line |
| Q12➡ | Data Structure Given a hash table T with 25 slots that stores 2000 elements, the load factor α for T is ___________. |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Hashing | Help-Line |
| Q13➡ | Engineering Mathematics In the given matrix 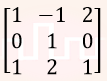 , one of the eigenvalues is 1. The eigenvectors corresponding to the eigenvalue 1 are , one of the eigenvalues is 1. The eigenvectors corresponding to the eigenvalue 1 are |
| i ➥ |
| ii ➥ |
| iii ➥ |
| iv ➥ |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Linear Algebra | Help-Line |
| Q14➡ | Engineering Mathematics The value of is 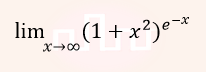 |
| i ➥ 0 |
| ii ➥ 1/2 |
| iii ➥ 1 |
| iv ➥ ∞ |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Calculus | Help-Line |
| Q15➡ | Engineering Mathematics The number of 4 digit numbers having their digits in non-decreasing order (from left to right) constructed by using the digits belonging to the set {1, 2, 3} is _________. |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Combinatorics | Help-Line |
| Q16➡ | Engineering Mathematics In a room there are only two types of people, namely Type 1 and Type 2. Type 1 people always tell the truth and Type 2 people always lie. You give a fair coin to a person in that room, without knowing which type he is from and tell him to toss it and hide the result from you till you ask for it. Upon asking, the person replies the following: “The result of the toss is head if and only if I am telling the truth.” Which of the following options is correct? |
| i ➥ The result is head |
| ii ➥ The result is tail |
| iii ➥ If the person is of Type 2, then the result is tail |
| iv ➥ If the person is of Type 1, then the result is tail |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Propositional Logic | Help-Line |
| Q17➡ | Data Structure While inserting the elements 71, 65, 84, 69, 67, 83 in an empty binary search tree (BST) in the sequence shown, the element in the lowest level is |
| i ➥ 65 |
| ii ➥ 67 |
| iii ➥ 69 |
| iv ➥ 83 |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Heap Tree | Help-Line |
| Q18➡ | Data Structure The result evaluating the postfix expression 10 5 + 60 6 / * 8 – is |
| i ➥ 284 |
| ii ➥ 213 |
| iii ➥ 142 |
| iv ➥ 71 |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Postfix Expression | Help-Line |
| Q19➡ | Database Management System Consider the following relation Cinema (theater, address, capacity) Which of the following options will be needed at the end of the SQL query SELECT P1. address FROM Cinema P1 Such that it always finds the addresses of theaters with maximum capacity? |
| i ➥ WHERE P1.capacity >= All (select P2.capacity from Cinema P2) |
| ii ➥ WHERE P1.capacity >= Any (select P2.capacity from Cinema P2) |
| iii ➥ WHERE P1.capacity > All (select max(P2.capacity) from Cinema P2) |
| iv ➥ WHERE P1.capacity > Any (select max(P2.capacity) from Cinema P2) |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | SQL | Help-Line |
| Q20➡ | Operating System Consider the following array of elements. 〈89, 19, 50, 17, 12, 15, 2, 5, 7, 11, 6, 9, 100〉. The minimum number of interchanges needed to convert it into a max-heap is |
| i ➥ 4 |
| ii ➥ 5 |
| iii ➥ 2 |
| iv ➥ 3 |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Deadlock | Help-Line |
| Q21➡ | Operating System Two processes X and Y need to access a critical section. Consider the following synchronization construct used by both the processes 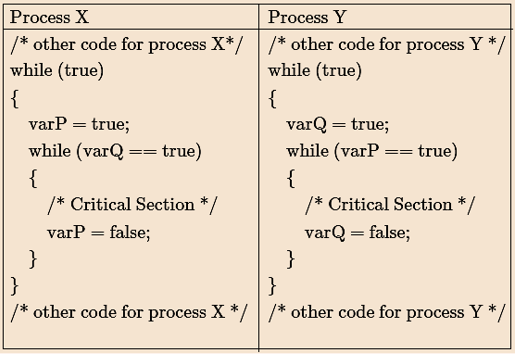 Here varP and varQ are shared variables and both are initialized to false. Which one of the following statements is true? |
| i ➥ The proposed solution prevents deadlock but fails to guarantee mutual exclusion |
| ii ➥ The proposed solution guarantees mutual exclusion but fails to prevent deadlock |
| iii ➥ The proposed solution guarantees mutual exclusion and prevents deadlock |
| iv ➥ The proposed solution fails to prevent deadlock and fails to guarantee mutual exclusion |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Transaction Management | Help-Line |
| Q22➡ | Theory of Computation Let L be the language represented by the regular expression Σ*0011Σ* where Σ = {0,1}. What is the minimum number of states in a DFA that recognizes L’ (complement of L)? |
| i ➥ 4 |
| ii ➥ 5 |
| iii ➥ 6 |
| iv ➥ 8 |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Regular Expression | Help-Line |
| Q23➡ | Software Engineering Consider a software program that is artificially seeded with 100 faults. While testing this program, 159 faults are detected, out of which 75 faults are from those artificially seeded faults. Assuming that both are and seeded faults are of same nature and have same distribution, the estimated number of undetected real fault is ______. |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Testing | Help-Line |
| Q24➡ | Computer Organization Consider a machine with a byte addressable main memory of 220 bytes, block size of 16 bytes and a direct mapped cache having 212 cache lines. Let the addresses of two consecutive bytes in main memory be (E201F)16 and (E2020)16. What are the tag and cache line address (in hex) for main memory address (E201F)16? |
| i ➥ E, 201 |
| ii ➥ F, 201 |
| iii ➥ E, E20 |
| iv ➥ 2, 01F |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Cache Memory | Help-Line |
| Q25➡ | Computer Network Consider a CSMA/CD network that transmits data at a rate of 100 Mbps (108 bits second) over a 1 km (kilometer) cable with no repeaters. If the minimum frame size required for this network is 1250 bytes, what is the signal speed (km/sec) in the cable? |
| i ➥ 8000 |
| ii ➥ 10000 |
| iii ➥ 16000 |
| iv ➥ 20000 |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Access Control | Help-Line |
[Q26 – Q55 carry TWO mark each ]
| Q26➡ | Engineering Mathematics The velocity v (in kilometer/minute) of a motorbike which starts from rest, is given at fixed intervals of time t(in minutes) as follows: 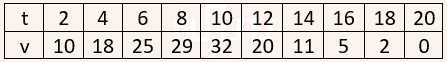 The approximate distance (in kilometers) rounded to two places of decimals covered in 20 minutes using Simpson’s 1/3rd rule is ______. |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Simpson’s 1/3rd Rule | Help-Line |
| Q27➡ | Algorithms Assume that a mergesort algorithm in the worst case takes 30 seconds for an input of size 64. Which of the following most closely approximates the maximum input size of a problem that can be solved in 6 minutes? |
| i ➥ 256 |
| ii ➥ 512 |
| iii ➥ 1024 |
| iv ➥ 2048 |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Merge Sort | Help-Line |
| Q28➡ | Programming Consider the following recursive C function. 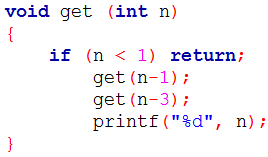 If get(6) function is being called in main() then how many times will the get() function be invoked before returning to the main()? |
| i ➥ 15 |
| ii ➥ 25 |
| iii ➥ 35 |
| iv ➥ 45 |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Program | Help-Line |
| Q29➡ | Database Managemnt System Consider a B+ tree in which the search key is 12 bytes long, block size is 1024 bytes, record pointer is 10 bytes long and block pointer is 8 bytes long. The maximum number of keys that can be accommodated in each non-leaf node of the tree is ______. |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | File Structure | Help-Line |
| Q30➡ | Database Management System Given the function F=P′+QR, where F is a function in three Boolean variables P,Q and R and P′=!P, consider the following statements. (S1)F=∑(4,5,6) (S2)F=∑(0,1,2,3,7) (S3)F=Π(4,5,6) (S4)F=Π(0,1,2,3,7) Which of the following is true? |
| i ➥ (S1)-False, (S2)-True, (S3)-True, (S4)-False |
| ii ➥ (S1)-True, (S2)-False, (S3)-False, (S4)-True |
| iii ➥ (S1)-False, (S2)-False, (S3)-True, (S4)-True |
| iv ➥ (S1)-True, (S2)-True, (S3)-False, (S4)-False |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Relational Algebra | Help-Line |
| Q31➡ | Algorithms Language L1 is polynomial time reducible to language L2. Language L3 is polynomial time reducible to L2, which in turn is polynomial time reducible to language L4. Which of the following is/are True? I. If L4 ∈ P, L2 ∈ P II. If L1 ∈ P or L3 ∈ P, then L2 ∈ P III. L1 ∈ P, if and only if L3 ∈ P IV. If L4 ∈ P, then L1 ∈ P and L3 ∈ P |
| i ➥ II only |
| ii ➥ III only |
| iii ➥ I and IV only |
| iv ➥ I only |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Complexity Class | Help-Line |
| Q32➡ | Programming Consider the following C program. 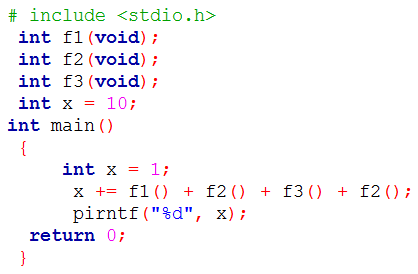 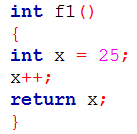 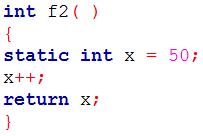 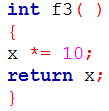 The output of the program is ______. |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Program | Help-Line |
| Q33➡ | Programming Consider the following C program. 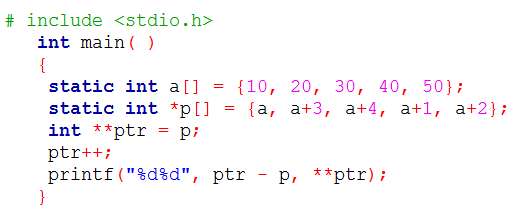 The output of the program is ______. |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Program | Help-Line |
| Q34➡ | Theory of Computation Which of the following languages are context-free? L1 = {ambnanbm ⎪ m, n ≥ 1} L2 = {ambnambn ⎪ m, n ≥ 1} L3 = {ambn ⎪ m = 2n + 1} |
| i ➥ L1 and L2 only |
| ii ➥ L1 and L3 only |
| iii ➥ L2 and L3 only |
| iv ➥ L3 only |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Context Free Language | Help-Line |
| Q35➡ | Operating System Consider the following policies for preventing deadlock in a system with mutually exclusive resources. I. Processes should acquire all their resources at the beginning of execution. If any resource is not available, all resources acquired so far are released. II. The resources are numbered uniquely, and processes are allowed to request for resources only in increasing resource numbers. III. The resources are numbered uniquely, and processes are allowed to request for resources only in decreasing resource numbers. IV. The resources are numbered uniquely. A process is allowed to request only for a resource with resource number larger than its currently held resources. Which of the above policies can be used for preventing deadlock? |
| i ➥ Any one of I and III but not II or IV |
| ii ➥ Any one of I, III, and IV but not II |
| iii ➥ Any one of II and III but not I or IV |
| iv ➥ Any one of I, II, III, and IV |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Deadlock | Help-Line |
| Q36➡ | Computer Network In the network 200.10.11.144/27, the fourth octet (in decimal) of the last IP address of the network which can be assigned to a host is _______. |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | IP Address | Help-Line |
| Q37➡ | Computer Network Consider a network connected two systems located 8000 kilometers apart. The bandwidth of the network is 500 × 106 bits per second. The propagation speed of the media is 4 × 106 meters per second. It is needed to design a Go-Back-N sliding window protocol for this network. The average packet size is 107 bits. The network is to be used to its full capacity. Assume that processing delays at nodes are negligible. Then the minimum size in bits of the sequence number field has to be _________. |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Flow Control | Help-Line |
| Q38➡ | Computer Organization Consider the following reservation table for a pipeline having three stages S1, S2 and S3. The minimum average latency (MAL) is _______. |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Pipelining | Help-Line |
| Q39➡ | Computer Organization Consider the following code sequence having five instructions I1 to I5. Each of these instructions has the following format. OP Ri, Rj, Rkwhere operation OP is performed on contents of registers Rj and Rk and the result is stored in register Ri. I1 : ADD R1, R2, R3Consider the following three statements: S1: There is an anti-dependence between instructions I2 and I5. S2: There is an anti-dependence between instructions I2 and I4. S3: Within an instruction pipeline an anti-dependence always creates one or more stalls.Which one of above statements is/are correct? |
| i ➥ Only S1 is true |
| ii ➥ Only S2 is true |
| iii ➥ Only S1 and S3 are true |
| iv ➥ Only S2 and S3 are true |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Microprosessor | Help-Line |
| Q40➡ | Operating System Consider the following two C code segments. Y and X are one and two dimensional arrays of size n and n × n respectively, where 2 ≤ n ≤ 10. Assume that in both code segments, elements of Y are initialized to 0 and each element X[i][j] of array X is initialized to i + j. Further assume that when stored in main memory all elements of X are in same main memory page frame. 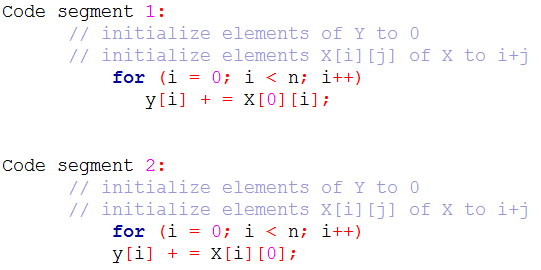 Which of the following statements is/are correct? S1: Final contents of array Y will be same in both code segments. S2: Elements of array X accessed inside the for loop shown in code segment 1 are contiguous in main memory. S3: Elements of array X accessed inside the for loop shown in code segment 2 are contiguous in main memory. |
| i ➥ Only S2 is correct |
| ii ➥ Only S3 is correct |
| iii ➥ Only S1 and S2 are correct |
| iv ➥ Only S1 and S3 are correct |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Main Memory | Help-Line |
| Q41➡ | DataBase Management System Consider the following partial Schedule S involving two transactions T1 and T2. Only the read and the write operations have been shown. The read operation on data item P is denoted by read(P) and the write operation on data item P is denoted by write(P). 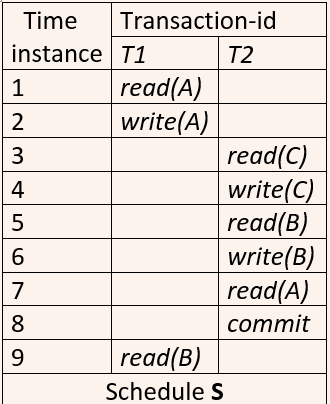 Suppose that the transaction T1 fails immediately after time instance 9. Which of the following statements is correct? |
| i ➥ T2 must be aborted and then both T1 and T2 must be re-started to ensure transaction atomicity |
| ii ➥ Schedule S is non-recoverable and cannot ensure transaction atomicity |
| iii ➥ Only T2 must be aborted and then re-started to ensure transaction atomicity |
| iv ➥ Schedule S is recoverable and can ensure atomicity and nothing else needs to be done |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Secant mathod | Help-Line |
| Q42➡ | Engineering Mathematics If the following system has non-trivial solution, px + qy + rz = 0 qx + ry + pz = 0 rx + py + qz = 0 then which one of the following options is True? |
| i ➥ p – q + r = 0 or p = q = –r |
| ii ➥ p + q – r = 0 or p = –q = r |
| iii ➥ p + q + r = 0 or p = q = r |
| iv ➥ p – q + r = 0 or p = –q = –r |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Linear Algebra | Help-Line |
| Q43➡ | Programming Language Consider the following C program: 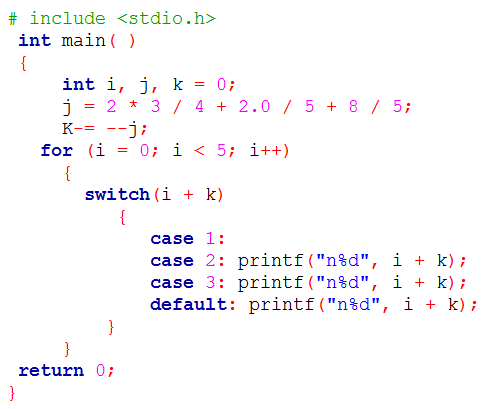 The number of times printf statement is executed is __. |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Programming in C | Help-Line |
| Q44➡ | Engineering Mathematics If for non-zero x, 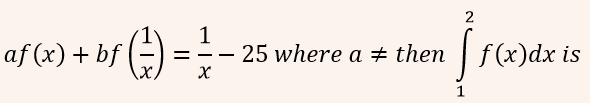 A: 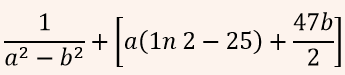 B: 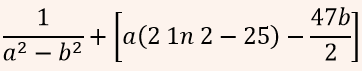 C: 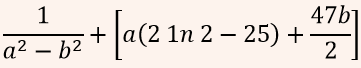 D: 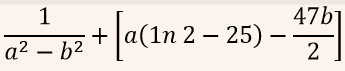 |
| i ➥ A |
| ii ➥ B |
| iii ➥ C |
| iv ➥ D |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Calculus | Help-Line |
| Q45➡ | Algorithms Let G be a connected undirected graph of 100 vertices and 300 edges. The weight of a minimum spanning tree of G is 500. When the weight of each edge of G is increased by five, the weight of a minimum spanning tree becomes__________. |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Spanning Tree | Help-Line |
| Q46➡ | Computer Network Two hosts are connected via a packet switch with 107 bits per second links. Each link has a propagation delay of 20 microseconds. The switch begins forwarding a packet 35 microseconds after it receives the same. If 10000 bits of data are to be transmitted between the two hosts using a packet size of 5000 bits, the time elapsed between the transmission of the first bit of data and the reception of the last bit of the data in microseconds is _. |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Switching | Help-Line |
| Q47➡ | Operating System For the processes listed in the following table, which of the following scheduling schemes will give the lowest average turnaround time? 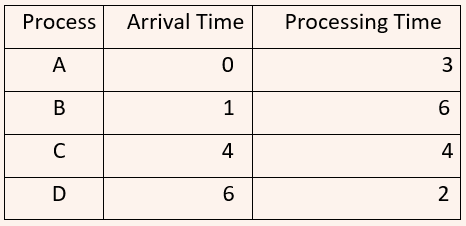 |
| i ➥ First Come First Serve |
| ii ➥ Non-preemptive Shortest Job First |
| iii ➥ Shortest Remaining Time |
| iv ➥ Round Robin with Quantum value two |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | CPU Scheduling | Help-Line |
| Q48➡ | Software Engineering Consider three software items: Program-X, Control Flow Diagram of Program-Y and Control Flow Diagram of Program-Z as shown below 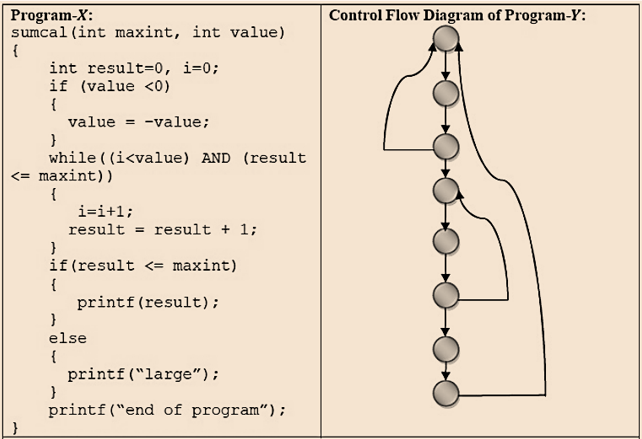 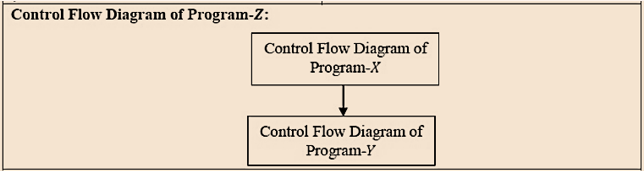 The values of McCabe’s Cyclomatic complexity of Program-X, Program-Y and Program-Z respectively are |
| i ➥ 4, 4, 7 |
| ii ➥ 3, 4, 7 |
| iii ➥ 4, 4, 8 |
| iv ➥ 4, 3, 8 |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Cyclomatic complexity | Help-Line |
| Q49➡ | Digital Logic Design Consider the equation (43)x = (y3)8 where x and y are unknown. The number of possible solutions is_______. |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Number System | Help-Line |
| Q50➡ | Engineering Mathematics Let R be a relation on the set of ordered pairs of positive integers such that ((p,q),(r,s)) ∈ R if and only if p – s = q – r. Which one of the following is true about R? |
| i ➥ Both reflexive and symmetric |
| ii ➥ Reflexive but not symmetric |
| iii ➥ Not reflexive but symmetric |
| iv ➥ Neither reflexive nor symmetric |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Relation | Help-Line |
| Q51➡ | Engineering Mathematics Suppose Xi for i = 1, 2, 3 are independent and identically distributed random variables whose probability mass functions are Pr[Xi = 0] = Pr[Xi = 1]=1/2 for i = 1, 2, 3. Define another random variable Y = X1X2 ⊕ X3, where ⊕ denotes XOR. Then Pr[Y = 0|X3 = 0] =_______, |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Probability | Help-Line |
| Q52➡ | Digital Logic design The total number of prime implicants of the function f(w,x,y,z) = Σ(0, 2, 4, 5, 6, 10) is________. |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Boolean Algebra | Help-Line |
| Q53➡ | Algorithms Suppose c = 〈c[0], … , c[k – 1]〉 is an array of length k, where all the entries are from the set {0, 1}. For any positive integers a and n, consider the following pseudocode. 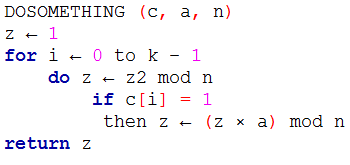 If k = 4, c = 〈1, 0, 1, 1〉, a = 2 and n = 8, then the output of DOSOMETHING(c, a, n) is __. |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Program | Help-Line |
| Q54➡ | Algorithms Let f(n) = n and g(n) = n(1+sin n), where n is a positive integer. Which of the following statements is/are correct? I. f(n) = O(g(n)) II. f(n) = Ω(g(n)) |
| i ➥ Only I |
| ii ➥ Only II |
| iii ➥ Both I and II |
| iv ➥ Neither I nor II |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Complexity | Help-Line |
| Q55➡ | Compiler Design Consider the following grammar G. S → F ⎪ H F → p ⎪ c H → d ⎪ c Where S, F and H are non-terminal symbols, p, d and c are terminal symbols. Which of the following statement(s) is/are correct? S1: LL(1) can parse all strings that are generated using grammar G. S2: LR(1) can parse all strings that are generated using grammar |
| i ➥ Only S1 |
| ii ➥ Only S2 |
| iii ➥ Both S1 and S2 |
| iv ➥ Neither S1 nor S2 |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Parsers | Help-Line |