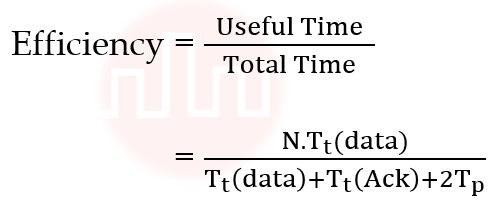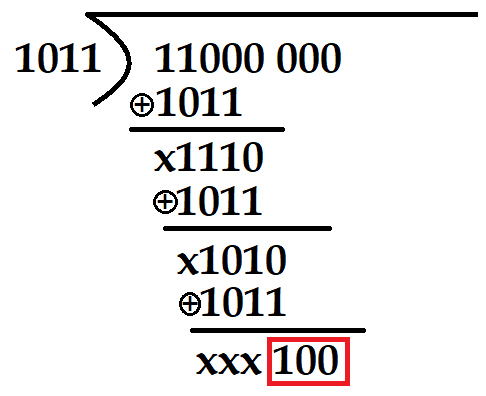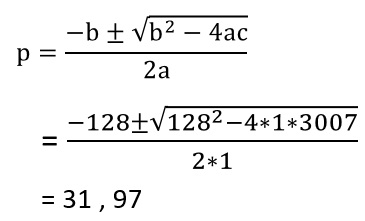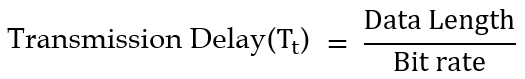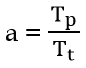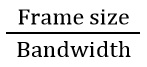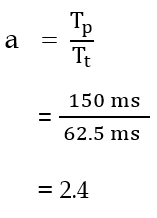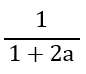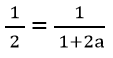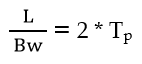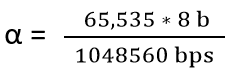GATE CSE Computer Network Previous Year Solutions
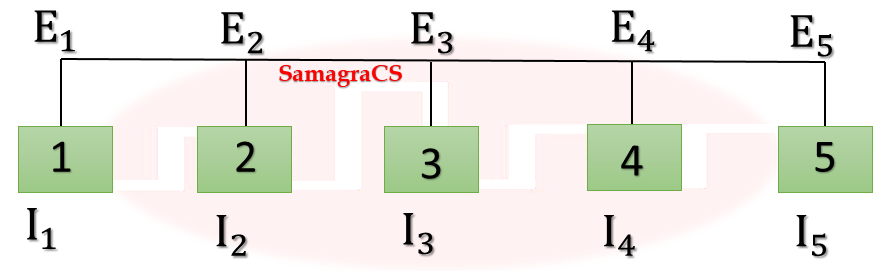
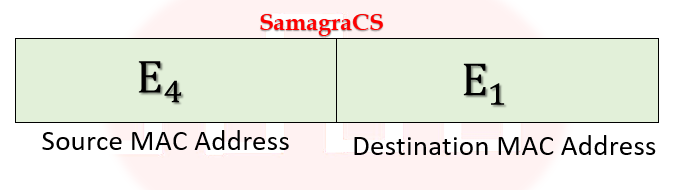
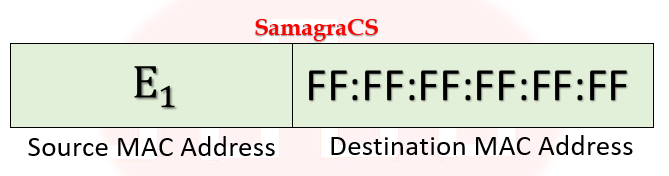
| Q1➡ | GATE 2021 Set-1 Consider the following two statements. S1: Destination MAC address of an ARP reply is a broadcast address. S2: Destination MAC address of an ARP request is a broadcast address. Which of the following choices is correct? |
| i ➥ S1 is true and S2 is false. |
| ii ➥ Both S1 and S2 are false. |
| iii ➥ Both S1 and S2 are true. |
| iv ➥ S1 is false and S2 is true. |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Network Protocols | Help-Line |
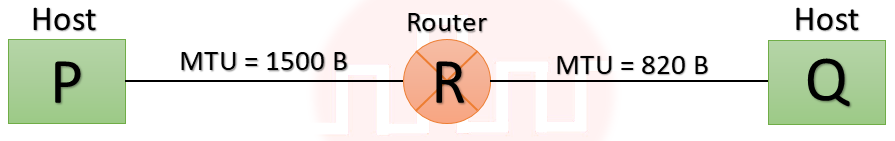
| Q2➡ | GATE 2021 Set-1 Consider two hosts P and Q connected through a router R. The maximum transfer unit (MTU) value of the link between P and R is 1500 bytes, and between R and Q is 820 bytes. A TCP segment of size 1400 bytes was transferred from P to Q through R, with IP identification value as 0x1234. Assume that the IP header size is 20 bytes. Further, the packet is allowed to be fragmented, i.e., Don’t Fragment (DF) flag in the IP header is not set by P. Which of the following statements is/are correct? |
| i ➥ If the second fragment is lost, R will resend the fragment with the IP identification value 0x1234. |
| ii ➥ TCP destination port can be determined by analysing only the second fragment. |
| iii ➥ Two fragments are created at R and the IP datagram size carrying the second fragment is 620 bytes. |
| iv ➥ If the second fragment is lost, P is required to resend the whole TCP segment. |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Fragmentaion | Help-Line |
| Q3➡ | GATE 2021 Set-1 A TCP server application is programmed to listen on port number P on host S. A TCP client is connected to the TCP server over the network. Consider that while the TCP connection was active, the server machine S crashed and rebooted. Assume that the client does not use the TCP keep alive timer. Which of the following behaviours is/are possible? |
| i ➥ If the client sends a packet after the server reboot, it will receive a FIN segment. |
| ii ➥ The TCP server application on S can listen on P after reboot. |
| iii ➥ If the client sends a packet after the server reboot, it will receive a RST segment. |
| iv ➥ If the client was waiting to receive a packet, it may wait indefinitely. |
Show Answer With Best Explanation
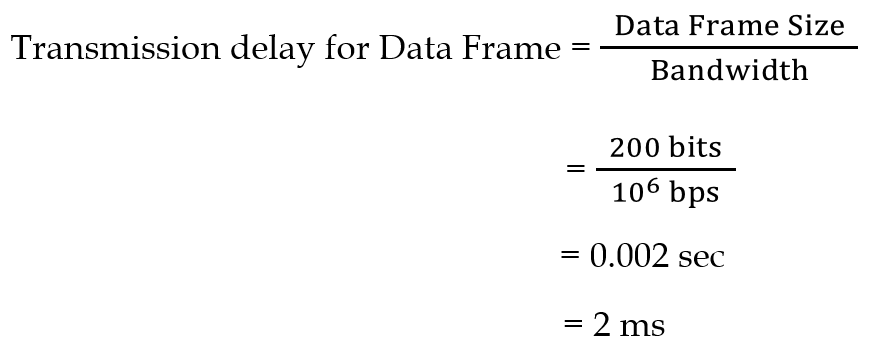
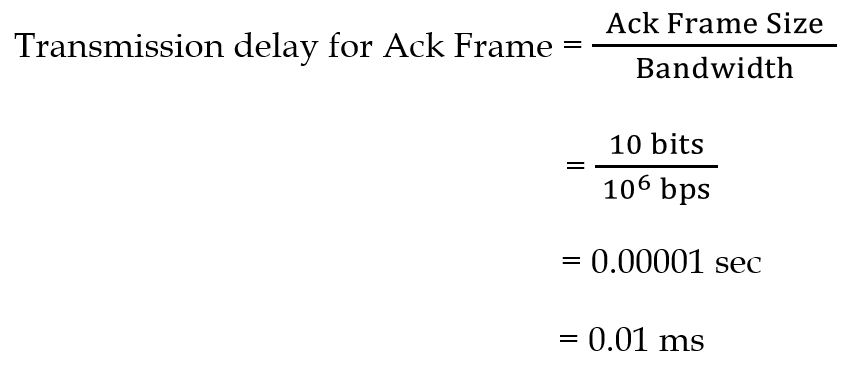
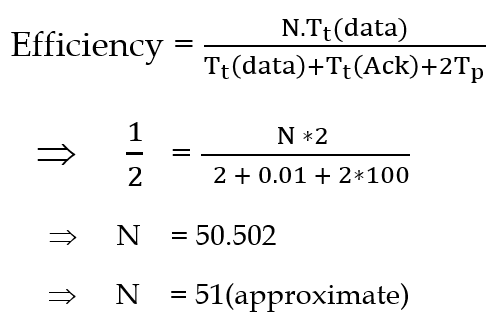
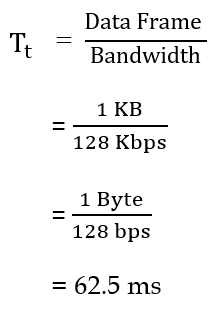
| Q4➡ | GATE 2021 Set-1 Consider the sliding window flow-control protocol operating between a sender and a receiver over a full-duplex error-free link. Assume the following: • The time taken for processing the data frame by the receiver is negligible. • The time taken for processing the acknowledgement frame by the sender is negligible. • The sender has an infinite number of frames available for transmission. • The size of the data frame is 2,000 bits and the size of the acknowledgment frame is 10 bits. • The link data rate in each direction is 1 Mbps (=106bits per second). • One way propagation delay of the link is 100 milliseconds. The minimum value of the sender’s window size in terms of the number of frames, (rounded to the nearest integer) needed to achieve a link utilization of 50% is _____. |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Flow Control | Help-Line |
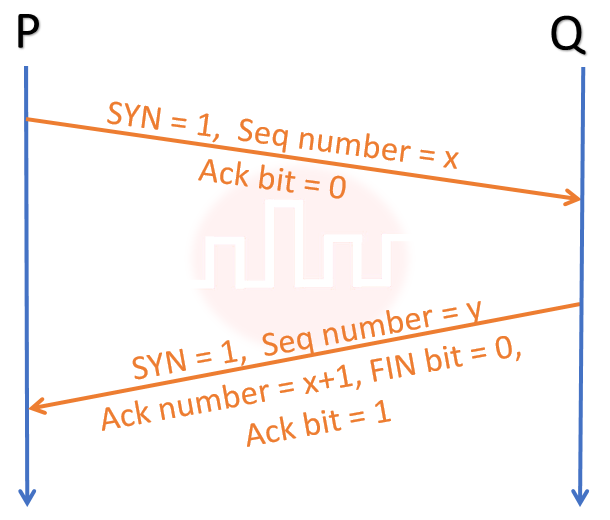
| Q5➡ | GATE 2021 Set-2 Consider the three-way handshake mechanism followed during TCP connection established between hosts P and Q. Let X and Y be two random 32-bit starting sequence numbers chosen by P and Q respectively. Suppose P sends a TCP connection request message to Q with a TCP segment having SYN bit = 1, SEQ number = X, and ACK bit = 0. Suppose Q accepts the connection request. Which one of the following choices represents the information present in the TCP segment header that is sent by Q to P? |
| i ➥ SYN bit = 1, SEQ number = Y, ACK bit = 1, ACK number = X, FIN bit = 0 |
| ii ➥ SYN bit = 1, SEQ number = X+1, ACK bit = 0, ACK number = Y, FIN bit = 0 |
| iii ➥ SYN bit = 1, SEQ number = Y, ACK bit = 1, ACK number = X+1, FIN bit = 0 |
| iv ➥ SYN bit = 0, SEQ number = X+1, ACK bit = 0, ACK number = Y, FIN bit = 1 |
Show Answer With Best Explanation
| Q6➡ | GATE 2021 Set-2 Consider the cyclic redundancy check (CRC) based error detecting scheme having the generator polynomial X3+X+1. Suppose the message m4m3m2m1m0=11000 is to be transmitted. Check bits c2c1c0 are appended at the end of the message by the transmitter using the above CRC scheme. The transmitted bit string is denoted by m4m3m2m1m0c2c1c0. The value of the checkbit sequence c2c1c0 is |
| i ➥ 110 |
| ii ➥ 100 |
| iii ➥ 111 |
| iv ➥ 101 |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Error Control | Help-Line |
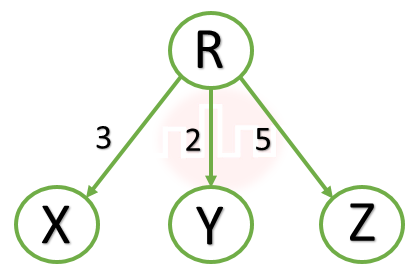
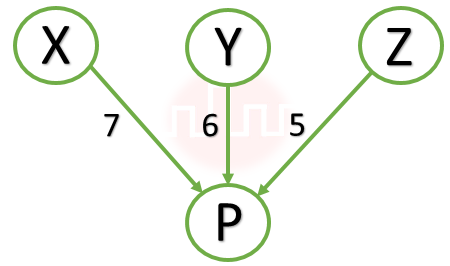
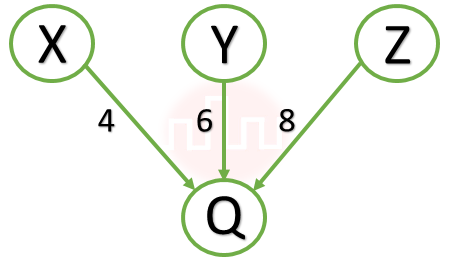
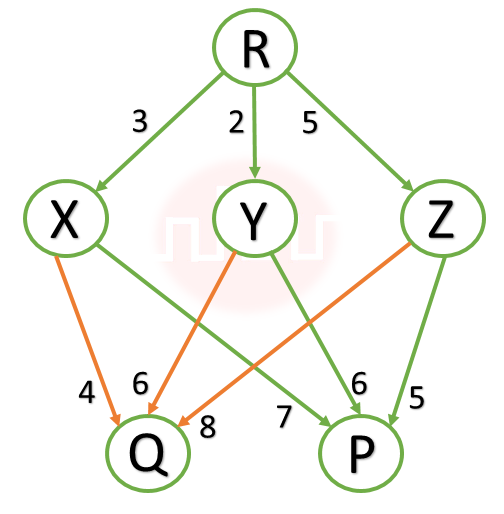
| Q7➡ | GATE 2021 Set-2 Consider a computer network using the distance vector routing algorithm in its network layer. The partial topology of the network is as shown below: 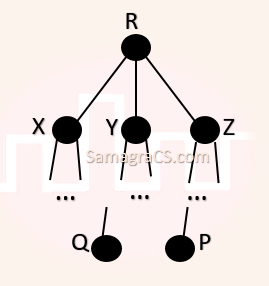 The objective is to find the shortest-cost path from the router R to routers P and Q. Assume that R does not initially know the shortest routes to P and Q. Assume that R has three neighbouring routers denoted as X, Y and Z. During one iteration, R measures its distance to its neighbours X, Y and Z as 3, 2 and 5, respectively. Router R gets routing vectors from its neighbours that indicate that the distance to router P from routers X, Y and Z are 7, 6 and 5, respectively. The routing vector also indicates that the distance to router Q from routers X, Y and Z are 4, 6 and 8, respectively. Which of the following statement(s) is/are correct with respect to the new routing table of R, after updation during this iteration |
| i ➥ The distance from R to P will be stored as 10. |
| ii ➥ The next hop router for a packet from R to Q is Z. |
| iii ➥ The next hop router for a packet from R to P is Y. |
| iv ➥ The distance from R to Q will be stored as 7. |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Routing Algorithm | Help-Line |
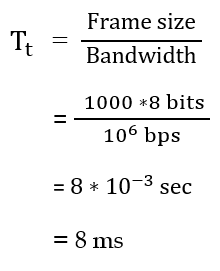
| Q8➡ | GATE 2021 Set-2 Consider a network using the pure ALOHA medium access control protocol, where each frame is of length 1,000 bits. The channel transmission rate is 1 Mbps (= 106bits per second). The aggregate number of transmissions across all the nodes (including new frame transmissions and retransmitted frames due to collisions) is modelled as a Poisson process with a rate of 1,000 frames per second. Throughput is defined as the average number of frames successfully transmitted per second. The throughput of the network (rounded to the nearest integer) is _______. |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Access Control | Help-Line |
| Q9➡ | GATE 2020 Consider the following statements about the functionality of an IP based router. I. A router does not modify the IP packets during forwarding. II. It is not necessary for a router to implement any routing protocol. III. A router should reassemble IP fragments if the MTU of the outgoing link is larger than the size of the incoming IP packet. Which of the above statements is/are TRUE? |
| i ➥ II only |
| ii ➥ I and II only |
| iii ➥ II and III only |
| iv ➥ I only |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Routers | Help-Line |
| Q10➡ | GATE 2020 Assume that you have made a request for a web page through your web browser to a web server. Initially the browser cache is empty. Further, the browser is configured to send HTTP requests in non-persistent mode. The web page contains text and five very small images. The minimum number of TCP connections required to display the web page completely in your browser is _______. |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Application Layer Protocols | Help-Line |
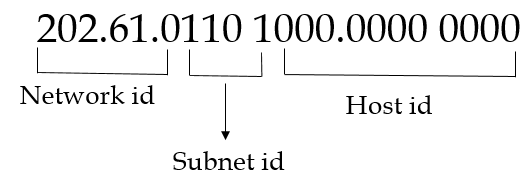
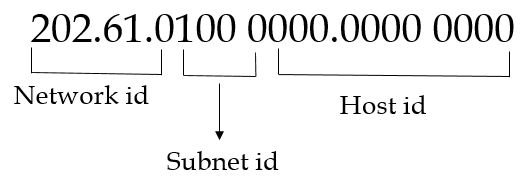
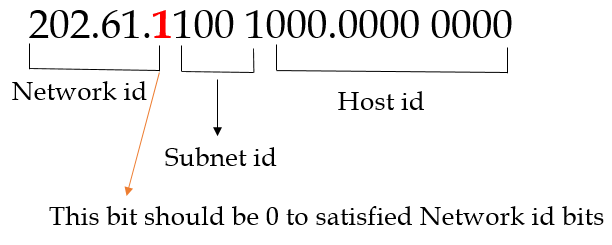
| Q11➡ | GATE 2020 An organization requires a range of IP addresses to assign one to each of its 1500 computers. The organization has approached an Internet Service Provider (ISP) for this task. The ISP uses CIDR and serves the requests from the available IP address space 202.61.0.0/17. The ISP wants to assign an address space to the organization which will minimize the number of routing entries in the ISP’s router using route aggregation. Which of the following address spaces are potential candidates from which the ISP can allot any one to the organization? A. 202.61.84.0/21 B. 202.61.104.0/21 C. 202.61.64.0/21 D. 202.61.144.0/21 |
| i ➥ B and C only |
| ii ➥ A and D only |
| iii ➥ A and B only |
| iv ➥ C and D only |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | IP Address | Help-Line |
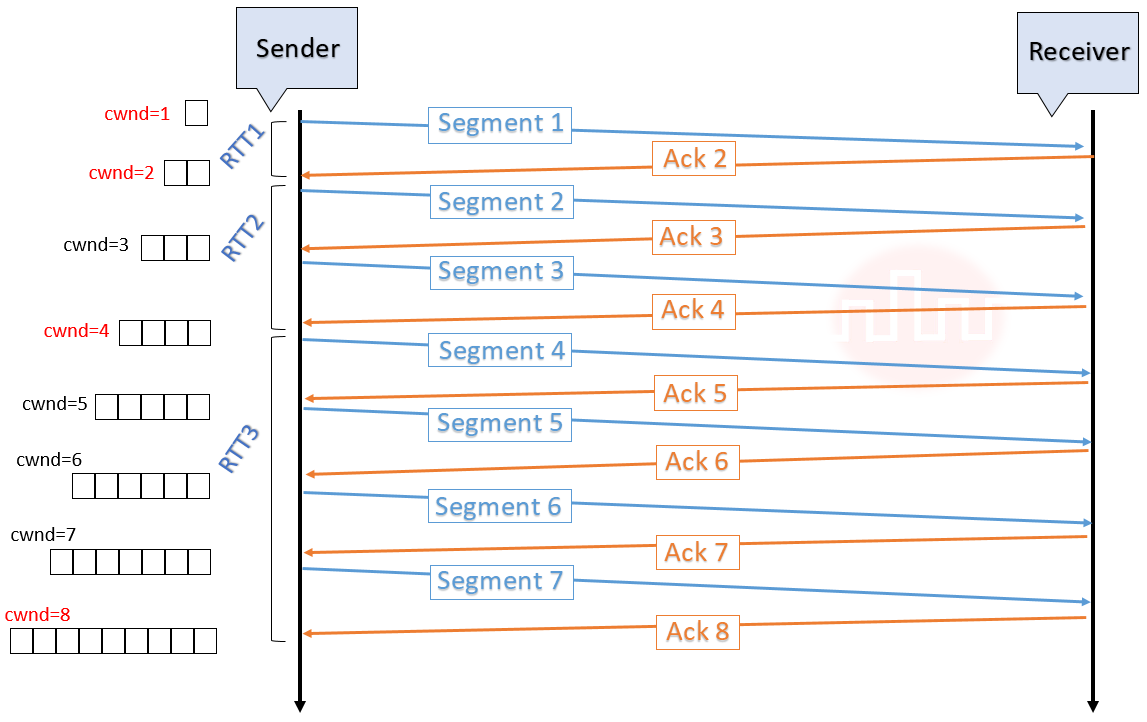
| Q12➡ | GATE 2020 Consider a TCP connection between a client and a server with the following specifications: the round trip time is 6 ms, the size of the receiver advertised window is 50 KB, slow start threshold at the client is 32 KB, and the maximum segment size is 2 KB. The connection is established at time t=0. Assume that there are no timeouts and errors during transmission. Then the size of the congestion window (in KB) at time t+60 ms after all acknowledgements are processed is ________. |
Show Answer With Best Explanation
| Q13➡ | GATE 2019 Which of the following protocol pairs can be used to send and retrieve e-mails (in that order)? |
| i ➥ IMAP, POP3 |
| ii ➥ IMAP, SMTP |
| iii ➥ SMTP, MIME |
| iv ➥ SMTP, POP3 |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Application Layer Protocols | Help-Line |
| Q14➡ | GATE 2019 The value of 351 mod 5 is _______. |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Network Security | Help-Line |
| Q15➡ | GATE 2019 Suppose that in an IP-over-Ethernet network, a machine X wishes to find the MAC address of another machine Y in its subnet. Which one of the following techniques can be used for this? |
| i ➥ X sends an ARP request packet with broadcast IP address in its local subnet |
| ii ➥ X sends an ARP request packet to the local gateway’s MAC address which then finds the MAC address of Y and sends to X |
| iii ➥ X sends an ARP request packet with broadcast MAC address in its local subnet |
| iv ➥ X sends an ARP request packet to the local gateway’s IP address which then finds the MAC address of Y and sends to X |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Network Layer Protocol | Help-Line |
| Q16➡ | GATE 2019 Consider three machines M, N and P with IP addresses 100.10.5.2, 100.10.5.5, and 100.10.5.6 respectively. The subnet mask is set to 255.255.255.252 for all the three machines. Which one of the following is true? |
| i ➥ Only M and N belong to the same subnet |
| ii ➥ Only N and P belong to the same subnet |
| iii ➥ M, N, and P all belong to the same subnet |
| iv ➥ M, N and P belong to three different subnets |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | IP Address | Help-Line |
| Q17➡ | GATE 2019 In an RSA cryptosystem, the value of the public modulus parameter n is 3007. If it is also known that Φ(n) = 2880, where Φ() denotes Euler’s Quotient Function, then the prime factor of n which is greater than 50 is ________. |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Network Security | Help-Line |
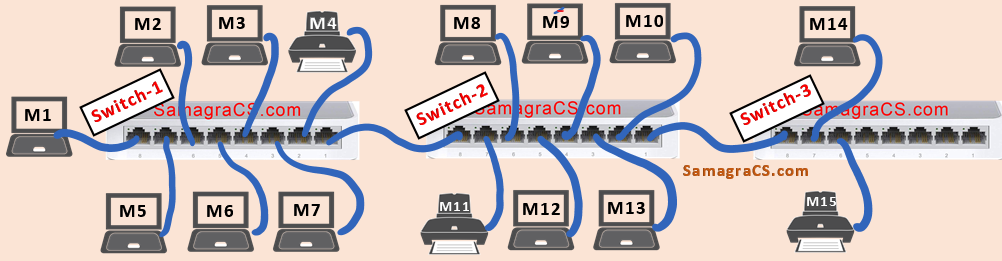
| Q18➡ | GATE 2019 Consider that 15 machines need to be connected in a LAN using 8-port Ethernet switches. Assume that these switches do not have any separate uplink ports. The minimum number of switches needed is ________. |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | LAN Technology | Help-Line |
Q19➡ | GATE 2018 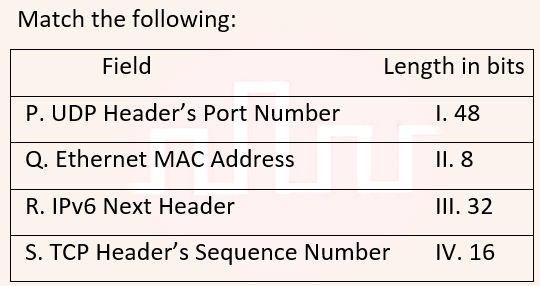 |
| i ➥ P-III, Q-IV, R-II, S-I |
| ii ➥ P-II, Q-I, R-IV, S-III |
| iii ➥ P-IV, Q-I, R-II, S-III |
| iv ➥ P-IV, Q-I, R-III, S-II |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Matching | Help-Line |
| Q21➡ | GATE 2018 Consider the following statements regarding the slow start phase of the TCP congestion control algorithm. Note that cwnd stands for the TCP congestion window and MSS denotes the Maximum Segment Size. (i) The cwnd increase by 2 MSS on every successful acknowledgement. (ii) The cwnd approximately doubles on every successful acknowledgement. (iii) The cwnd increase by 1 MSS every round trip time. (iv) The cwnd approximately doubles every round trip time. Which one of the following is correct? |
| i ➥ Only (ii) and (iii) are true |
| ii ➥ Only (i) and (iii) are true |
| iii ➥ Only (iv) is true |
| iv ➥ Only (i) and (iv) are true |
Show Answer With Best Explanation
| Q22➡ | GATE 2018 Consider a long-lived TCP session with an end-to-end bandwidth of 1 Gbps (= 109 bits/second). The session starts with a sequence number of 1234. The minimum time (in seconds, rounded to the closest integer) before this sequence number can be used again is _______. |
Show Answer With Best Explanation
| Q23➡ | GATE 2018 Consider a simple communication system where multiple nodes are connected by a shared broadcast medium (like Ethernet or wireless). The nodes in the system use the following carrier-sense based medium access protocol. A node that receives a packet to transmit will carrier-sense the medium for 5 units of time. If the node does not detect any other transmission in this duration, it starts transmitting its packet in the next time unit. If the node detects another transmission, it waits until this other transmission finishes, and then begins to carrier-sense for 5 time units again. Once they start to transmit, nodes do not perform any collision detection and continue transmission even if a collision occurs. All transmissions last for 20 units of time. Assume that the transmission signal travels at the speed of 10 meters per unit time in the medium. Assume that the system has two nodes P and Q, located at a distance d meters from each other. P starts transmitting a packet at time t=0 after successfully completing its carrier-sense phase. Node Q has a packet to transmit at time t=0 and begins to carrier-sense the medium. The maximum distance d (in meters, rounded to the closest integer) that allows Q to successfully avoid a collision between its proposed transmission and P’s ongoing transmission is _. |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Ethernet | Help-Line |
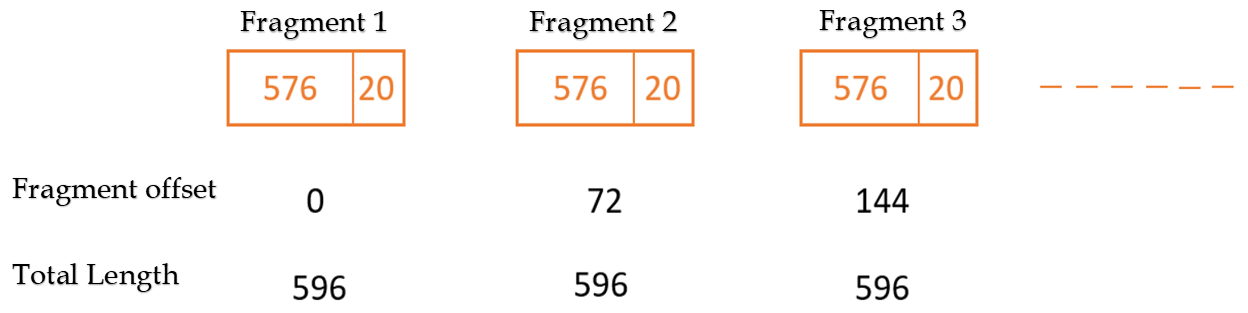
| Q24➡ | GATE 2018 Consider an IP packet with a length of 4,500 bytes that includes a 20-byte IPv4 header and a 40-byte TCP header. The packet is forwarded to an IPv4 router that supports a Maximum Transmission Unit (MTU) of 600 bytes. Assume that the length of the IP header in all the outgoing fragments of this packet is 20 bytes. Assume that the fragmentation offset value stored in the first fragment is 0. The fragmentation offset value stored in the third fragment is ___________. |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Fragmentation | Help-Line |
| Q25➡ | GATE 2017 Set-1 A sender S sends a message m to receiver R, which is digitally signed by S with its private key. In this scenario, one or more of the following security violations can take place. (I) S can launch a birthday attack to replace m with a fraudulent message. (II) A third party attacker can launch a birthday attack to replace m with a fraudulent message. (III) R can launch a birthday attack to replace m with a fraudulent message. Which of the following are possible security violations? |
| i ➥ I only |
| ii ➥ I and II only |
| iii ➥ II and III only |
| iv ➥ II only |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Network Security | Help-Line |
| Q26➡ | GATE 2017 Set-1 Consider a TCP client and a TCP server running on two different machines. After completing data transfer, the TCP client calls close to terminate the connection and a FIN segment is sent to the TCP server. Server-side TCP responds by sending an ACK, which is received by the client-side TCP. As per the TCP connection state diagram (RFC 793), in which state does the client-side TCP connection wait for the FIN from the server-side TCP? |
| i ➥ FIN-WAIT-2 |
| ii ➥ LAST-ACK |
| iii ➥ TIME-WAIT |
| iv ➥ FIN-WAIT-1 |
Show Answer With Best Explanation
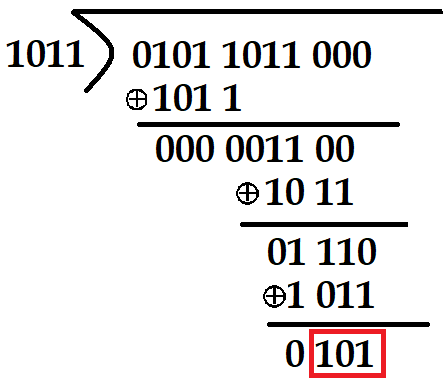
| Q27➡ | GATE 2017 Set-1 A computer network uses polynomials over GF(2) for error checking with 8 bits as information bits and uses x3 + x + 1 as the generator polynomial to generate the check bits. In this network, the message 01011011 is transmitted as |
| i ➥ 01011011100 |
| ii ➥ 01011011010 |
| iii ➥ 01011011101 |
| iv ➥ 01011011011 |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Error Control | Help-Line |
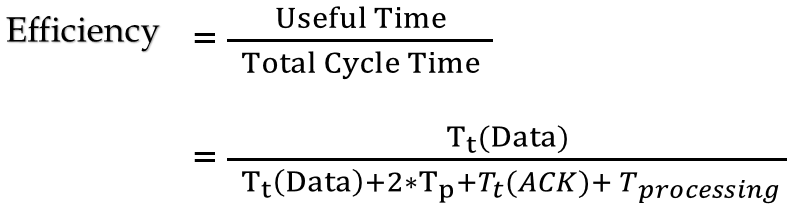
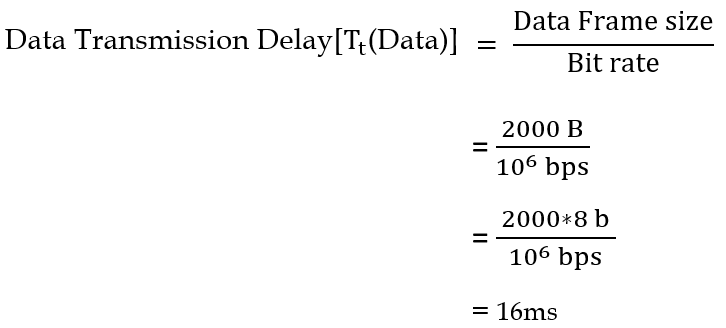
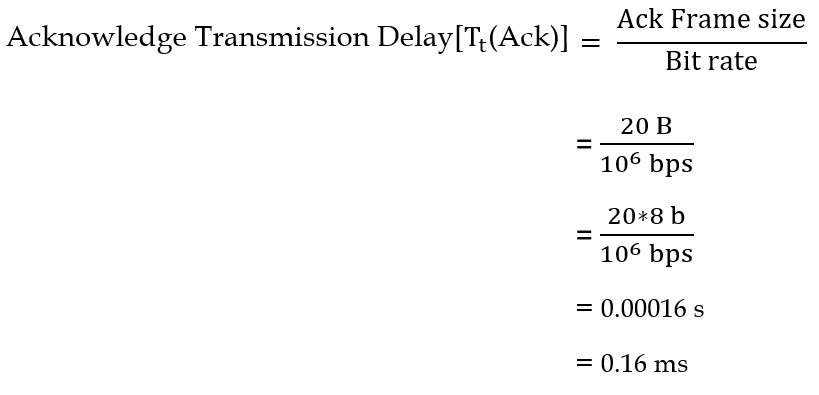
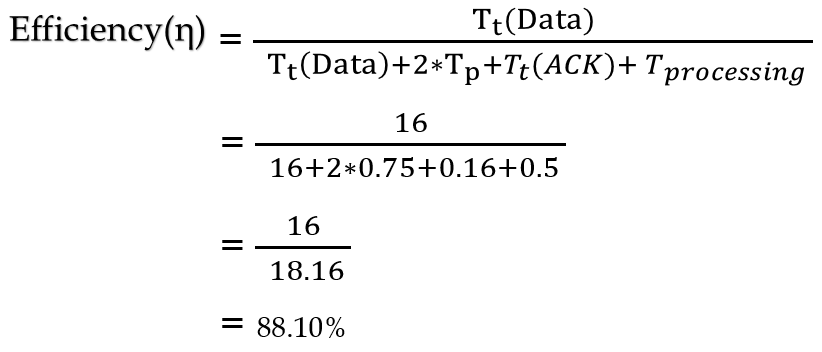
| Q28➡ | GATE 2017 Set-1 The value of parameters for the Stop-and-Wait ARQ protocol are as given below: Bit rate of the transmission channel = 1 Mbps. Propagation delay from sender to receiver = 0.75 ms. Time to process a frame = 0.25 ms. Number of bytes in the information frame = 1980. Number of bytes in the acknowledge frame = 20. Number of overhead bytes in the information frame = 20. Assume that there are no transmission errors. Then, the transmission efficiency (expressed in percentage) of the Stop-and-Wait ARQ protocol for the above parameters is ________. (correct to 2 decimal places). |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Flow Control | Help-Line |
| Q29➡ | GATE 2017 Set-1 In a RSA cryptosystem, a participant A uses two prime numbers p = 13 and q = 17 to generate her public and private keys. If the public key of A is 35, then the private key of A is ____________. |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Network Security | Help-Line |
| Q30➡ | GATE 2017 Set-2 Consider the following statements about the routing protocols, Routing Information Protocol (RIP) and Open Shortest Path First (OSPF) in an IPv4 network. • I: RIP uses distance vector routing • II: RIP packets are sent using UDP • III: OSPF packets are sent using TCP • IV: OSPF operation is based on link-state routing Which of the statements above are CORRECT? |
| i ➥ I, II and III only |
| ii ➥ II, III and IV only |
| iii ➥ I and IV only |
| iv ➥ I, II and IV only |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Routing Protocol | Help-Line |
| Q31➡ | GATE 2017 Set-2 Consider socket API on a Linux machine that supports connected UDP sockets. A connected UDP socket is a UDP socket on which connect function has already been called. Which of the following statement is/are CORRECT? I. A connected UDP socket can be used to communicate with multiple peers simultaneously. II. A process can successfully call connect function again for an already connected UDP socket. |
| i ➥ Both I and II |
| ii ➥ Neither I nor II |
| iii ➥ II only |
| iv ➥ I only |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | UDP | Help-Line |
| Q32➡ | GATE 2017 Set-2 The maximum number of IPv4 router addresses that can be listed in the record route (RR) option field of an IPv4 header is ________. |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | IPV4 Header | Help-Line |
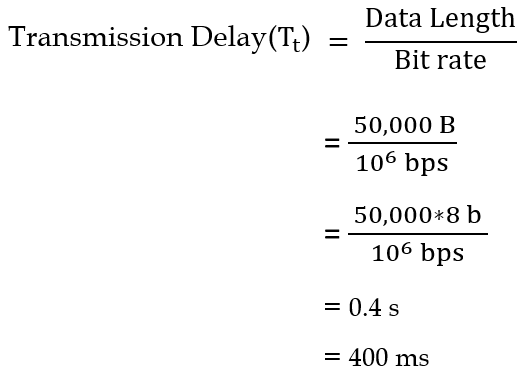
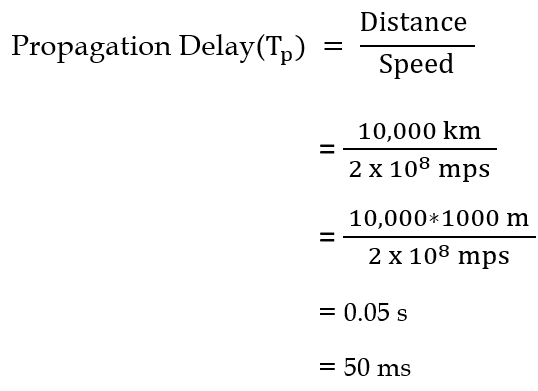
| Q33➡ | GATE 2017 Set-2 Consider two hosts X and Y, connected by a single direct link of rate 106bits/sec. The distance between the two hosts is 10,000 km and the propagation speed along the link is 2×108m/sec. Host X sends a file of 50,000 bytes as one large message to host Y continuously. Let the transmission and propagation delays be p milliseconds and q milliseconds, respectively. Then the values of p and q are |
| i ➥ p=400 and q=50 |
| ii ➥ p=100 and q=50 |
| iii ➥ p=50 and q=400 |
| iv ➥ p=50 and q=100 |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Flow Control | Help-Line |
| Q34➡ | GATE 2016 Set-1 Which one of the following protocols is NOT used to resolve one form of address to another one? |
| i ➥ RARP |
| ii ➥ DHCP |
| iii ➥ ARP |
| iv ➥ DNS |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Protocols | Help-Line |
| Q35➡ | GATE 2016 Set-1 Which of the following is/are example(s) of stateful application layer protocols? (i) HTTP (ii) FTP (iii) TCP (iv) POP3 |
| i ➥ (iv) only |
| ii ➥ (ii) and (iv) only |
| iii ➥ (ii) and (iii) only |
| iv ➥ (i) and (ii) only |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Application Layer Protocols | Help-Line |
| Q36➡ | GATE 2016 Set-1 Consider that B wants to send a message m that is digitally signed to A. Let the pair of private and public keys for A and B be denoted by Kx– and Kx+ for x = A,B, respectively. Let Kx(m) represent the operation of encrypting m with a key Kx and H(m) represent the message digest. Which one of the following indicates the CORRECT way of sending the message m along with the digital signature to A? |
| i ➥ {m , KB+ (H(m)) } |
| ii ➥ {m , KB– (H(m)) } |
| iii ➥ {m , KA– (H(m)) } |
| iv ➥ {m , KA+ (H(m)) } |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Network Security | Help-Line |
| Q37➡ | GATE 2016 Set-1 An IP datagram of size 1000 bytes arrives at a router. The router has to forward this packet on a link whose MTU (maximum transmission unit) is 100 bytes. Assume that the size of the IP header is 20 bytes. The number of fragments that the IP datagram will be divided into for transmission is __________. |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Fragmentation | Help-Line |
| Q38➡ | GATE 2016 Set-1 For a host machine that uses the token bucket algorithm for congestion control, the token bucket has a capacity of 1 megabyte and the maximum output rate is 20 megabytes per second. Tokens arrive at a rate to sustain output at a rate of 10 megabytes per second. The token bucket is currently full and the machine needs to send 12 megabytes of data. The minimum time required to transmit the data is seconds ________. |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Token Bucket | Help-Line |
| Q39➡ | GATE 2016 Set-2 Anarkali digitally signs a message and sends it to Salim. Verification of the signature by Salim requires |
| i ➥ Anarkali’s Public key |
| ii ➥ Salim’s Public key |
| iii ➥ Salim’s Private key |
| iv ➥ Anarkali’s Private key |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Network Security | Help-Line |
| Q40➡ | GATE 2016 Set-2 In an Ethernet local area network, which one of the following statements is TRUE? |
| i ➥ The purpose of the jamming signal is to pad the frames that are smaller than the minimum frame size. |
| ii ➥ The purpose of the jamming signal is to pad the frames that are smaller than the minimum frame size. |
| iii ➥ A station continues to transmit the packet even after the collision is detected. |
| iv ➥ The exponential backoff mechanism reduces the probability of collision on retransmissions. |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Ethernet LAN | Help-Line |
| Q41➡ | GATE 2016 Set-2 Identify the correct sequence in which the following packets are transmitted on the network by a host when a browser requests a webpage from a remote server, assuming that the host has just been restarted. |
| i ➥ HTTP GET request, DNS query, TCP SYN |
| ii ➥ DNS query, HTTP GET request, TCP SYN |
| iii ➥ DNS query, TCP SYN, HTTP GET request |
| iv ➥ TCP SYN, DNS query, HTTP GET request |
Show Answer With Best Explanation
| Q42➡ | GATE 2016 Set-2 The value of the expression 1399(mod 17), in the range 0 to 16, is _________. |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Network Security | Help-Line |
| Q43➡ | GATE 2016 Set-2 A network has a data transmission bandwidth of 20 × 106 bits per second. It uses CSMA/CD in the MAC layer. The maximum signal propagation time from one node to another node is 40 microseconds. The minimum size of a frame in the network is _______ bytes. |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Access Control | Help-Line |
| Q44➡ | GATE 2016 Set-2 For the IEEE 802.11 MAC protocol for wireless communication, which of the following statements is/are TRUE? • I. At least three non-overlapping channels are available for transmissions. • II. The RTS-CTS mechanism is used for collision detection. • III. Unicast frames are ACKed. |
| i ➥ All I, II and III |
| ii ➥ I and III only |
| iii ➥ II and III only |
| iv ➥ II only |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | IEEE 802.11 | Help-Line |
| Q45➡ | GATE 2016 Set-2 Consider a 128 × 103 bits/ second satellite communication link with one way propagation delay of 150 milliseconds. Selective retransmission (repeat) protocol is used on this link to send data with a frame size of 1 kilobyte. Neglect the transmission time of acknowledgement. The minimum number of bits required for the sequence number field to achieve 100% utilization is _________. |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Flow Control | Help-Line |
| Q46➡ | GATE 2015 Set-1 Suppose two hosts use a TCP connection to transfer a large file. Which of the following statements is/are False with respect to the TCP connection? I. If the sequence number of a segment is m, then the sequence number of the subsequent segment is always m+1. II. If the estimated round trip time at any given point of time is t sec, the value of the retransmission timeout is always set to greater than or equal to t sec. III. The size of the advertised window never changes during the course of the TCP connection. IV. The number of unacknowledged bytes at the sender is always less than or equal to the advertised window. |
| i ➥ III only |
| ii ➥ I and III only |
| iii ➥ I and IV only |
| iv ➥ II and IV only |
Show Answer With Best Explanation
| Q47➡ | GATE 2015 Set-1 Suppose that everyone in a group on N people wants to communicate secretly with the (N – 1) others using symmetric Key cryptographic system. The communication between any two person should not be decodable by the others in the group. The numbers of keys required in the system as a whole to satisfy the confidentiality requirement is |
| i ➥ 2N |
| ii ➥ N(N−1) |
| iii ➥ N(N−1) / 2 |
| iv ➥ (N−1) / 2 |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Network Security | Help-Line |
| Q48➡ | GATE 2015 Set-1 Which one of the following fields of an IP header is NOT modified by a typical IP router? |
| i ➥ Checksum |
| ii ➥ Source address |
| iii ➥ Time to Live (TTL) |
| iv ➥ Length |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | IPV4 Header | Help-Line |
| Q49➡ | GATE 2015 Set-1 In one of the pairs of protocols given below , both the protocols can use multiple TCP connections between the same client and the server. Which one is that? |
| i ➥ HTTP, FTP |
| ii ➥ HTTP, TELNET |
| iii ➥ FTP, SMTP |
| iv ➥ HTTP, SMTP |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Protocols | Help-Line |
| Q50➡ | GATE 2015 Set-1 Suppose that the stop-and-wait protocol is used on a link with a bit rate of 64 kilobits per second and 20 milliseconds propagation delay. Assume that the transmission time for the acknowledgment and the processing time at nodes are negligible. Then the minimum frame size in bytes to achieve a link utilization of at least 50% is _________. |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Flow Control | Help-Line |
| Q51➡ | GATE 2015 Set-1 Consider a LAN with four nodes S1, S2, S3 and S4. Time is divided into fixed-size slots, and a node can begin its transmission only at the beginning of a slot. A collision is said to have occurred if more than one node transmit in the same slot. The probabilities of generation of a frame in a time slot by S1, S2, S3 and S4 are 0.1, 0.2, 0.3 and 0.4, respectively. The probability of sending a frame in the first slot without any collision by any of these four stations is _________. |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Access Control | Help-Line |
| Q52➡ | GATE 2015 Set-2 Identify the correct order in which a server process must invoke the function calls accept, bind, listen, and recv according to UNIX socket API. |
| i ➥ listen, accept, bind recv |
| ii ➥ bind, listen, accept, recv |
| iii ➥ bind, accept, listen, recv |
| iv ➥ accept, listen, bind recv |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Sockets | Help-Line |
| Q53➡ | GATE 2015 Set-2 A link has a transmission speed of 106 bits/sec. It uses data packets of size 1000 bytes each. Assume that the acknowledgement has negligible transmission delay, and that its propagation delay is the same as the data propagation delay. Also assume that the processing delays at the nodes are negligible. The efficiency of the stop-and-wait protocol in this setup is exactly 25%. The value of the one-way propagation delay (in milliseconds) is ________. |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Flow Control | Help-Line |
| Q54➡ | GATE 2015 Set-2 Which one of the following statements is NOT correct about HTTP cookies? |
| i ➥ A cookie is a piece of code that has the potential to compromise the security of an internet user |
| ii ➥ A cookie gains entry to the user’s work area through an HTTP header |
| iii ➥ A cookie has an expiry date and time |
| iv ➥ Cookies can be used to track the browsing pattern of a user at a particular site |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | HTTP | Help-Line |
| Q55➡ | GATE 2015 Set-2 Consider the following routing table at an IP router: 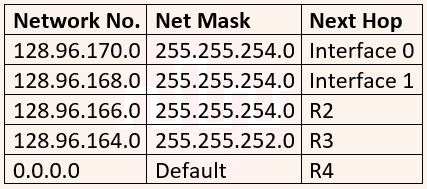 For each IP address in Group I identify the correct choice of the next hop from Group II using the entries from the routing table above. 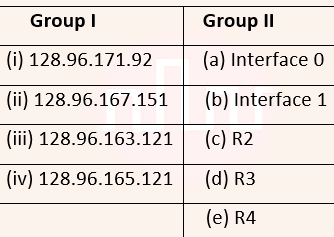 |
| i ➥ i-a, ii-c, iii-e, iv-d |
| ii ➥ i-a, ii-d, iii-b, iv-e |
| iii ➥ i-b, ii-c, iii-d, iv-e |
| iv ➥ i-b, ii-c, iii-e, iv-d |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | IP Address | Help-Line |
| Q56➡ | GATE 2015 Set-2 Host A sends a UDP datagram containing 8880 bytes of user data to host B over an Ethernet LAN. Ethernet frames may carry data up to 1500 bytes (i.e. MTU = 1500 bytes). Size of UDP header is 8 bytes and size of IP heard is 20 bytes. There is no option field in IP header. How many total number of IP fragments will be transmitted and what will be the contents of offset field in the last fragment? |
| i ➥ 6 and 925 |
| ii ➥ 6 and 7400 |
| iii ➥ 7 and 1110 |
| iv ➥ 7 and 8880 |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Fragmentation | Help-Line |
| Q57➡ | GATE 2015 Set-2 Assume that the bandwidth for a TCP connection is 1048560 bits/sec. Let α be the value of RTT in milliseconds (rounded off to the nearest integer) after which the TCP window scale option is needed. Let β be the maximum possible window size the window scale option. Then the values of α and β are |
| i ➥ 63 milliseconds, 65535×214 |
| ii ➥ 63 milliseconds, 65535×216 |
| iii ➥ 500 milliseconds, 65535×214 |
| iv ➥ 500 milliseconds, 65535×216 |
Show Answer With Best Explanation
| Q58➡ | GATE 2015 Set-3 Consider the following statements. I. TCP connections are full duplex. II. TCP has no option for selective acknowledgment. III. TCP connections are message streams. |
| i ➥ Only I is correct |
| ii ➥ Only I and III are correct |
| iii ➥ Only II and III are correct |
| iv ➥ All of I, II and III are correct |
Show Answer With Best Explanation
| Q59➡ | GATE 2015 Set-3 Consider a CSMA/CD network that transmits data at a rate of 100 Mbps (108 bits second) over a 1 km (kilometer) cable with no repeaters. If the minimum frame size required for this network is 1250 bytes, what is the signal speed (km/sec) in the cable? |
| i ➥ 8000 |
| ii ➥ 10000 |
| iii ➥ 16000 |
| iv ➥ 20000 |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Access Control | Help-Line |
| Q60➡ | GATE 2015 Set-3 In the network 200.10.11.144/27, the fourth octet (in decimal) of the last IP address of the network which can be assigned to a host is _______. |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | IP Address | Help-Line |
| Q61➡ | GATE 2015 Set-3 Consider a network connected two systems located 8000 kilometers apart. The bandwidth of the network is 500 × 106 bits per second. The propagation speed of the media is 4 × 106 meters per second. It is needed to design a Go-Back-N sliding window protocol for this network. The average packet size is 107 bits. The network is to be used to its full capacity. Assume that processing delays at nodes are negligible. Then the minimum size in bits of the sequence number field has to be _________. |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Flow Control | Help-Line |
| Q62➡ | GATE 2015 Set-3 Two hosts are connected via a packet switch with 107 bits per second links. Each link has a propagation delay of 20 microseconds. The switch begins forwarding a packet 35 microseconds after it receives the same. If 10000 bits of data are to be transmitted between the two hosts using a packet size of 5000 bits, the time elapsed between the transmission of the first bit of data and the reception of the last bit of the data in microseconds is _. |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Switching | Help-Line |
| Q63➡ | GATE 2014 Set-1 Consider the following three statements about link state and distance vector routing protocols, for a large network with 500 network nodes and 4000 links. [S1] The computational overhead in link state protocols is higher than in distance vector protocols. [S2] A distance vector protocol (with split horizon) avoids persistent routing loops, but not a link state protocol. [S3] After a topology change, a link state protocol will converge faster than a distance vector protocol. Which one of the following is correct about S1, S2, and S3 ? |
| i ➥ listen, accept, bind recv |
| ii ➥ S1, S2, and S3 are all false. |
| iii ➥ S1 and S2 are true, but S3 is false. |
| iv ➥ S1 and S3 are true, but S2 is false. |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Routing algorithms | Help-Line |
| Q64➡ | GATE 2014 Set-1 Which of the following are used to generate a message digest by the network security protocols? (P) RSA (Q) SHA-1 (R) DES (S) MD5 |
| i ➥ P and R only |
| ii ➥ Q and R only |
| iii ➥ Q and S only |
| iv ➥ R and S only |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Network security | Help-Line |
| Q65➡ | GATE 2014 Set-1 Identify the correct order in which the following actions take place in an interaction between a web browser and a web server. 1. The web browser requests a webpage using HTTP. 2. The web browser establishes a TCP connection with the web server. 3. The web server sends the requested webpage using HTTP. 4. The web browser resolves the domain name using DNS. |
| i ➥ 4,2,1,3 |
| ii ➥ 1,2,3,4 |
| iii ➥ 4,1,2,3 |
| iv ➥ 2,4,1,3 |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | HTTP | Help-Line |
| Q66➡ | GATE 2014 Set-1 Consider a token ring network with a length of 2 km having 10 stations including a monitoring station. The propagation speed of the signal is 2×108 m/s and the token transmission time is ignored. If each station is allowed to hold the token for 2 µsec, the minimum time for which the monitoring station should wait (in µsec) before assuming that the token is lost is______. |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Token-Ring | Help-Line |
| Q67➡ | GATE 2014 Set-1 Let the size of congestion window of a TCP connection be 32 KB when a timeout occurs. The round trip time of the connection is 100 msec and the maximum segment size used is 2 KB. The time taken (in msec) by the TCP connection to get back to 32 KB congestion window is _. |
Show Answer With Best Explanation
| Q68➡ | GATE 2014 Set-1 Consider a selective repeat sliding window protocol that uses a frame size of 1 KB to send data on a 1.5 Mbps link with a one-way latency of 50 msec. To achieve a link utilization of 60%, the minimum number of bits required to represent the sequence number field is __. |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Flow Control | Help-Line |
| Q69➡ | GATE 2014 Set-2 Which one of the following is TRUE about the interior gateway routing protocols – Routing Information Protocol (RIP) and Open Shortest Path First (OSPF)? |
| i ➥ RIP uses distance vector routing and OSPF uses link state routing |
| ii ➥ OSPF uses distance vector routing and RIP uses link state routing |
| iii ➥ Both RIP and OSPF use link state routing |
| iv ➥ Both RIP and OSPF use distance vector routing |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Routing protocols | Help-Line |
| Q70➡ | GATE 2014 Set-2 Which one of the following socket API functions converts an unconnected active TCP socket into a passive socket? |
| i ➥ connect |
| ii ➥ bind |
| iii ➥ listen |
| iv ➥ accept |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Socket | Help-Line |
| Q71➡ | GATE 2014 Set-2 In the diagram shown below, L1 is an Ethernet LAN and L2 is a Token-Ring LAN. An IP packet originates from sender S and traverses to R, as shown. The links within each ISP and across the two ISPs, are all point-to-point optical links. The initial value of the TTL field is 32. The maximum possible value of the TTL field when R receives the datagram is . 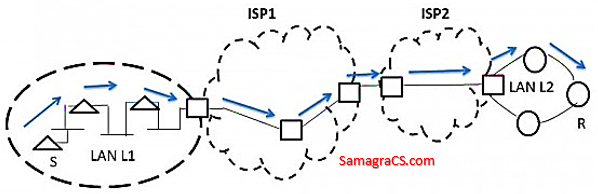 |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Ethernet | Help-Line |
| Q72➡ | GATE 2014 Set-2 Consider the store and forward packet switched network given below. Assume that the bandwidth of each link is 106 bytes / sec. A user on host A sends a file of size 103 bytes to host B through routers R1 and R2 in three different ways. In the first case a single packet containing the complete file is transmitted from A to B. In the second case, the file is split into 10 equal parts, and these packets are transmitted from A to B. In the third case, the file is split into 20 equal parts and these packets are sent from A to B. Each packet contains 100 bytes of header information along with the user data. Consider only transmission time and ignore processing, queuing and propagation delays. Also assume that there are no errors during transmission. Let T1, T2 and T3 be the times taken to transmit the file in the first, second and third case respectively. Which one of the following is CORRECT?  |
| i ➥ T1 < T2 < T3 |
| ii ➥ T1 > T2 > T3 |
| iii ➥ T2 = T3, T3 < T1 |
| iv ➥ T1 = T3, T3 > T2 |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Switching | Help-Line |
| Q73➡ | GATE 2014 Set-2 An IP machine Q has a path to another IP machine H via three IP routers R1, R2, and R3. Q—R1—R2—R3—H H acts as an HTTP server, and Q connects to H via HTTP and downloads a file. Session layer encryption is used, with DES as the shared key encryption protocol. Consider the following four pieces of information: [I1] The URL of the file downloaded by Q [I2] The TCP port numbers at Q and H [I3] The IP addresses of Q and H [I4] The link layer addresses of Q and H Which of I1, I2, I3, and I4 can an intruder learn through sniffing at R2 alone? |
| i ➥ Only I1 and I2 |
| ii ➥ Only I1 |
| iii ➥ Only I2 and I3 |
| iv ➥ Only I3 and I4 |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Network Security | Help-Line |
| Q74➡ | GATE 2014 Set-2 A graphical HTML browser resident at a network client machine Q accesses a static HTML webpage from a HTTP server S. The static HTML page has exactly one static embedded image which is also at S. Assuming no caching, which one of the following is correct about the HTML webpage loading (including the embedded image)? |
| i ➥ Q needs to send at least 2 HTTP requests to S, each necessarily in a separate TCP connection to server S |
| ii ➥ Q needs to send at least 2 HTTP requests to S, but a single TCP connection to server S is sufficient |
| iii ➥ A single HTTP request from Q to S is sufficient, and a single TCP connection between Q and S is necessary for this |
| iv ➥ A single HTTP request from Q to S is sufficient, and this is possible without any TCP connection between Q and S |
Show Answer With Best Explanation
| Q75➡ | GATE 2014 Set-3 In the following pairs of OSI protocol layer/sub-layer and its functionality, the INCORRECT pair is |
| i ➥ Network layer and Routing |
| ii ➥ Data Link Layer and Bit synchronization |
| iii ➥ Transport layer and End-to-end process communication |
| iv ➥ Medium Access Control sub-layer and Channel sharing |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | ISO-OSI Layer | Help-Line |
| Q76➡ | GATE 2014 Set-3 A bit-stuffing based framing protocol uses an 8-bit delimiter pattern of 01111110. If the output bit-string after stuffing is 01111100101, then the input bit-string is |
| i ➥ 0111110100 |
| ii ➥ 0111110101 |
| iii ➥ 0111111101 |
| iv ➥ 0111111111 |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Data Link Layer | Help-Line |
| Q77➡ | GATE 2014 Set-3 Host A (on TCP/IP v4 network A) sends an IP datagram D to host B (also on TCP/IP v4 network B). Assume that no error occurred during the transmission of D. When D reaches B, which of the following IP header field(s) may be different from that of the original datagram D? (i) TTL (ii) Checksum (iii) Fragment Offset |
| i ➥ (i) only |
| ii ➥ (i) and (ii) only |
| iii ➥ (i) and (ii) only |
| iv ➥ (i), (ii) and (iii) |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | IPV4 Header | Help-Line |
| Q78➡ | GATE 2014 Set-3 An IP router implementing Classless Inter Domain Routing (CIDR) receives a packet with address 131.23.151.76. The router’s routing table has the following entries: 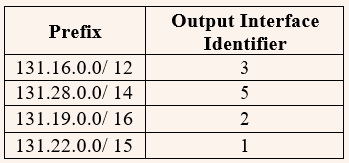 The identifier of the output interface on which this packet will be forwarded is ________. |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | IP Address | Help-Line |
| Q79➡ | GATE 2014 Set-3 Every host in an IPv4 network has a 1-second resolution real-time clock with battery backup. Each host needs to generate up to 1000 unique identifiers per second. Assume that each host has a globally unique IPv4 address. Design a 50-bit globally unique ID for this purpose. After what period (in seconds) will the identifiers generated by a host wrap around? |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | IPv4 Protocol | Help-Line |
| Q80➡ | GATE 2014 Set-3 An IP router with a Maximum Transmission Unit (MTU) of 1500 bytes has received an IP packet of size 4404 bytes with an IP header of length 20 bytes. The values of the relevant fields in the header of the third IP fragment generated by the router for this packet are |
| i ➥ MF bit: 0, Datagram Length: 1444; Offset: 370 |
| ii ➥ MF bit: 1, Datagram Length: 1424; Offset: 185 |
| iii ➥ MF bit: 1, Datagram Length: 1500; Offset: 370 |
| iv ➥ MF bit: 0, Datagram Length: 1424; Offset: 2960 |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Fragmentation | Help-Line |
| Q81➡ | GATE 2013 The transport layer protocols used for real time multimedia, file transfer, DNS and email, respectively are |
| i ➥ TCP, UDP, UDP and TCP |
| ii ➥ UDP, TCP, TCP and UDP |
| iii ➥ UDP, TCP, UDP and TCP |
| iv ➥ TCP, UDP, TCP and UDP |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Trasport Layer Protocol | Help-Line |
| Q82➡ | GATE 2013 Using public key cryptography, X adds a digital signature σ to message M, encrypts <M, σ> , and sends it to Y, where it is decrypted. Which one of the following sequences of keys is used for the operations? |
| i ➥ Encryption: X’s private key followed by Y’s private key; Decryption: X’s public key followed by Y’s public key |
| ii ➥ Encryption: X’s private key followed by Y’s public key; Decryption: X’s public key followed by Y’s private key |
| iii ➥ Encryption: X’s public key followed by Y’s private key; Decryption: Y’s public key followed by X’s private key |
| iv ➥ Encryption: X’s private key followed by Y’s public key; Decryption: Y’s private key followed by X’s public key |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Network Security | Help-Line |
| Q83➡ | GATE 2013 Assume that source S and destination D are connected through two intermediate routers labeled R. Determine how many times each packet has to visit the network layer and the data link layer during a transmission from S to D. 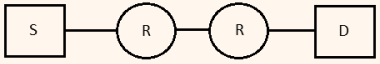 |
| i ➥ Network layer – 4 times and Data link layer – 4 times |
| ii ➥ Network layer – 4 times and Data link layer – 3 times |
| iii ➥ Network layer – 4 times and Data link layer – 6 times |
| iv ➥ Network layer – 2 times and Data link layer – 6 times |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Network Layer | Help-Line |
| Q84➡ | GATE 2013 Determine the maximum length of the cable (in km) for transmitting data at a rate of 500 Mbps in an Ethernet LAN with frames of size 10,000 bits. Assume the signal speed in the cable to be 2,00,000 km/s. |
| i ➥ 1 |
| ii ➥ 2 |
| iii ➥ 2.5 |
| iv ➥ 5 |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Flow Control | Help-Line |
| Q85➡ | GATE 2013 In an IPv4 datagram, the M bit is 0, the value of HLEN is 10, the value of total length is 400 and the fragment offset value is 300. The position of the datagram, the sequence numbers of the first and the last bytes of the payload, respectively are |
| i ➥ Last fragment, 2400 and 2789 |
| ii ➥ First fragment, 2400 and 2759 |
| iii ➥ Last fragment, 2400 and 2759 |
| iv ➥ Middle fragment, 300 and 689 |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Fragmentation | Help-Line |
| Q86➡ | GATE 2013 Consider the store and forward packet switched network given below. Assume that the bandwidth of each link is 106 bytes / sec. A user on host A sends a file of size 103 bytes to host B through routers R1 and R2 in three different ways. In the first case a single packet containing the complete file is transmitted from A to B. In the second case, the file is split into 10 equal parts, and these packets are transmitted from A to B. In the third case, the file is split into 20 equal parts and these packets are sent from A to B. Each packet contains 100 bytes of header information along with the user data. Consider only transmission time and ignore processing, queuing and propagation delays. Also assume that there are no errors during transmission. Let T1, T2 and T3 be the times taken to transmit the file in the first, second and third case respectively. Which one of the following is CORRECT?  |
| i ➥ T1 < T2 < T3 |
| ii ➥ T1 > T2 > T3 |
| iii ➥ T2 = T3, T3 < T1 |
| iv ➥ T1 = T3, T3 > T2 |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Switching | Help-Line |
| Q87➡ | GATE 2012 The protocol data unit (PDU) for the application layer in the Internet stack is |
| i ➥ Segment |
| ii ➥ Datagram |
| iii ➥ Message |
| iv ➥ Frame |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Application Layer | Help-Line |
| Q88➡ | GATE 2012 Which of the following transport layer protocols is used to support electronic mail? |
| i ➥ SMTP |
| ii ➥ IP |
| iii ➥ TCP |
| iv ➥ UDP |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Transport Layer Protocols | Help-Line |
| Q89➡ | GATE 2012 In the IPv4 addressing format, the number of networks allowed under Class C addresses is |
| i ➥ 214 |
| ii ➥ 27 |
| iii ➥ 221 |
| iv ➥ 224 |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | IP Address | Help-Line |
| Q90➡ | GATE 2012 An Internet Service Provider (ISP) has the following chunk of CIDR-based IP addresses available with it: 245.248.128.0/20. The ISP wants to give half of this chunk of addresses to Organization A, and a quarter to Organization B, while retaining the remaining with itself. Which of the following is a valid allocation of addresses to A and B? |
| i ➥ 245.248.136.0/21 and 245.248.128.0/22 |
| ii ➥ 245.248.128.0/21 and 245.248.128.0/22 |
| iii ➥ 245.248.132.0/22 and 245.248.132.0/21 |
| iv ➥ 245.248.136.0/24 and 245.248.132.0/21 |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | IP Address | Help-Line |
| Q91➡ | GATE 2012 Consider a source computer (S) transmitting a file of size 106 bits to a destination computer (D) over a network of two routers (R1 and R2) and three links (L1, L2 and L3). L1 connects S to R1; L2 connects R1 to R2; and L3 connects R2 to D. Let each link be of length 100 km. Assume signals travel over each link at a speed of 108 meters per second. Assume that the link bandwidth on each link is 1Mbps. Let the file be broken down into 1000 packets each of size 1000 bits. Find the total sum of transmission and propagation delays in transmitting the file from S to D? |
| i ➥ 1005 ms |
| ii ➥ 1010 ms |
| iii ➥ 3000 ms |
| iv ➥ 3003 ms |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Switching | Help-Line |
| Q92➡ | GATE 2012 Consider an instance of TCP’s Additive Increase Multiplicative Decrease (AIMD) algorithm where the window size at the start of the slow start phase is 2 MSS and the threshold at the start of the first transmission is 8 MSS. Assume that a timeout occurs during the fifth transmission. Find the congestion window size at the end of the tenth transmission. |
| i ➥ 8 MSS |
| ii ➥ 14 MSS |
| iii ➥ 7 MSS |
| iv ➥ 12 MSS |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Congestion Control | Help-Line |
| Q93➡ | GATE 2011 A layer-4 firewall (a device that can look at all protocol headers up to the transport layer) CANNOT |
| i ➥ block entire HTTP traffic during 9:00PM and 5:00AM |
| ii ➥ block all ICMP traffic |
| iii ➥ stop incoming traffic from a specific IP address but allow outgoing traffic to the same IP address |
| iv ➥ block TCP traffic from a specific user on a multi-user system during 9:00PM and 5:00AM |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Firewall | Help-Line |
| Q94➡ | GATE 2011 Consider different activities related to email: m1: Send an email from a mail client to a mail server m2: Download an email from mailbox server to a mail client m3: Checking email in a web browser Which is the application level protocol used in each activity? |
| i ➥ m1: HTTP m2: SMTP m3: POP |
| ii ➥ m1: SMTP m2: FTP m3: HTTP |
| iii ➥ m1: SMTP m2: POP m3: HTTP |
| iv ➥ m1: POP m2: SMTP m3: IMAP |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Application Layer Protocol | Help-Line |
| Q95➡ | GATE 2011 Statement for Linked Answer Questions 95 and 96: Consider a network with five nodes, N1 to N5 as shown below. 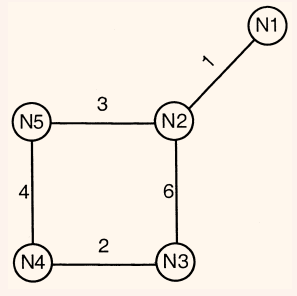 The network uses a Distance Vector Routing protocol. Once the routes have stabilized, the distance vectors at different nodes are as following. N1:(0,1,7,8,4) N2:(1,0,6,7,3) N3:(7,6,0,2,6) N4:(8,7,2,0,4) N5:(4,3,6,4,0) Each distance vector is the distance of the best known path at the instance to nodes, N1 to N5, where the distance to itself is 0. Also, all links are symmetric and the cost is identical in both directions. In each round, all nodes exchange their distance vectors with their respective neighbors. Then all nodes update their distance vectors. In between two rounds, any change in cost of a link will cause the two incident nodes to change only that entry in their distance vectors. The cost of link N2-N3 reduces to 2(in both directions). After the next round of updates, what will be the new distance vector at node, N3. |
| i ➥ (3, 2, 0, 2, 5) |
| ii ➥ (3, 2, 0, 2, 6) |
| iii ➥ (7, 2, 0, 2, 5) |
| iv ➥ (7, 2, 0, 2, 6) |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Routing Protocol | Help-Line |
| Q96➡ | |