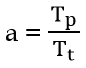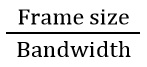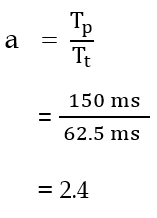GATE 2016 SET-2 CS Computer Science and information technology
[Q1 – Q25 carry ONE mark each ]
| Q1➡ | Engineering Mathematics Consider the following expressions: (i) false (ii) Q (iii) true (iv) P ∨ Q (v) ¬Q ∨ P The number of expressions given above that are logically implied by P ∧ (P ⇒ Q) is _________. |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Propositional Logic | Help-Line |
| Q2➡ | Engineering Mathematics Let f(x) be a polynomial and g(x) = f'(x) be its derivative. If the degree of (f(x) + f(-x)) is 10, then the degree of (g(x) – g(-x)) is _______. |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Calculus | Help-Line |
| Q3➡ | Engineering Mathematics The minimum number of colours that is sufficient to vertex-colour any planar graph is _________. |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Graph Theory | Help-Line |
| Q4➡ | Engineering Mathematics Consider the systems, each consisting of m linear equations in n variables. I. If m < n, then all such systems have a solution II. If m > n, then none of these systems has a solution III. If m = n, then there exists a system which has a solution Which one of the following is CORRECT? |
| i ➥ I, II and III are true |
| ii ➥ Only II and III are true |
| iii ➥ Only III is true |
| iv ➥ None of them is true |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Linear Algebra | Help-Line |
| Q5➡ | Engineering Mathematics Suppose that a shop has an equal number of LED bulbs of two different types. The probability of an LED bulb lasting more than 100 hours given that it is of Type 1 is 0.7, and given that it is of Type 2 is 0.4. The probability that an LED bulb chosen uniformly at random lasts more than 100 hours is __________. |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Probability | Help-Line |
| Q6➡ | Engineering Mathematics Suppose that the eigenvalues of matrix A are 1, 2, 4. The determinant of (A-1)T is _______. |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Boolean Algebra | Help-Line |
| Q7➡ | Digital Logic Design Consider an eight-bit ripple-carry adder for computing the sum of A and B, where A and B are integers represented in 2’s complement form. If the decimal value of A is one, the decimal value of B that leads to the longest latency for the sum to stabilize is ________. |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Combinational Circuits | Help-Line |
| Q8➡ | Digital Logic Design Let, x1⊕x2⊕x3⊕x4 = 0 where x1, x2, x3, x4 are Boolean variables, and ⊕ is the XOR operator. Which one of the following must always be TRUE? |
| i ➥ x1x2x3x4 = 0 |
| ii ➥ x1x3+x2 = 0 |
| iii ➥ x1‘⊕x3‘ = x2‘⊕x4‘ |
| iv ➥ x1 + x2 + x3 + x4 = 0 |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Boolean Algebra | Help-Line |
| Q9➡ | Digital Logic Design Let X be the number of distinct 16-bit integers in 2’s complement representation. Let Y be the number of distinct 16-bit integers in sign magnitude representation. Then X-Y is _____ . |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Number Systems | Help-Line |
| Q10➡ | Computer Organization A processor has 40 distinct instructions and 24 general purpose registers. A 32-bit instruction word has an opcode, two register operands and an immediate operand. The number of bits available for the immediate operand field is _________. |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Machine Instructions | Help-Line |
| Q11➡ | Data Structure Breadth First Search (BFS) is started on a binary tree beginning from the root vertex. There is a vertex t at a distance four from the root. If t is the n-th vertex in this BFS traversal, then the maximum possible value of n is _________. |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | BFS | Help-Line |
| Q12➡ | Programming The value printed by the following program is _________.  |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Program | Help-Line |
| Q13➡ | Algorithms Assume that the algorithms considered here sort the input sequences in ascending order. If the input is already in ascending order, which of the following are TRUE? I. Quicksort runs in Θ(n2) time II. Bubblesort runs in Θ(n2) time III. Mergesort runs in Θ(n) time IV. Insertion sort runs in Θ(n) time |
| i ➥ I and II only |
| ii ➥ I and III only |
| iii ➥ II and IV only |
| iv ➥ I and IV only |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Sorting | Help-Line |
| Q14➡ | Algorithms The Floyd-Warshall algorithm for all-pair shortest paths computation is based on |
| i ➥ Greedy paradigm. |
| ii ➥ Divide-and-Conquer paradigm. |
| iii ➥ Dynamic Programming paradigm. |
| iv ➥ Neither Greedy nor Divide-and-Conquer nor Dynamic Programming paradigm. |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Floyd Warshall Algorithm | Help-Line |
| Q15➡ | Data Structure N items are stored in a sorted doubly linked list. For a delete operation, a pointer is provided to the record to be deleted. For a decrease-key operation, a pointer is provided to the record on which the operation is to be performed. An algorithm performs the following operations on the list in this order: Θ(N) delete,O(logN) insert, O(logN) find, and Θ(N) decrease-key. What is the time complexity of all these operations put together? |
| i ➥ O(log2 N) |
| ii ➥ O(N) |
| iii ➥ O(N2) |
| iv ➥ Θ(N2 logN) |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Linked List | Help-Line |
| Q16➡ | Theory of Computation The number of states in the minimum sized DFA that accepts the language defined by the regular expression (0+1)*(0+1) (0+1)* is_________. |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | DFA | Help-Line |
| Q17➡ | Theory of Computation Language L1 is defined by the grammar: S1 → aS1b|ε Language L2 is defined by the grammar: S2 → abS2|ε Consider the following statements: • P: L1 is regular • Q: L2 is regular Which one of the following is TRUE? |
| i ➥ Both P and Q are true |
| ii ➥ P is true and Q is false |
| iii ➥ P is false and Q is true |
| iv ➥ Both P and Q are false |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Regular Language | Help-Line |
| Q18➡ | Theory of Computation Consider the following types of languages: L1: Regular, L2: Context-free, L3 : Recursive, L4 : Recursively enumerable. Which of the following is/are TRUE?  |
| i ➥ I only |
| ii ➥ I and III only |
| iii ➥ I and IV only |
| iv ➥ I, II and III only |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Closure Property | Help-Line |
Q19➡ | Compiler Design 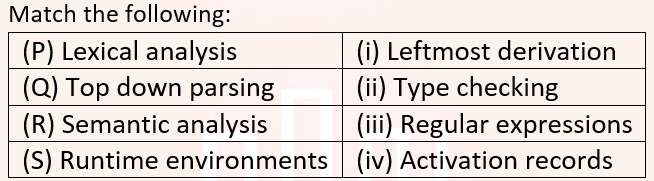 |
| i ➥ P ↔ i, Q ↔ ii, R ↔ iv, S ↔ iii |
| ii ➥ P ↔ iii, Q ↔ i, R ↔ ii, S ↔ iv |
| iii ➥ P ↔ ii, Q ↔ iii, R ↔ i, S ↔ iv |
| iv ➥ P ↔ iv, Q ↔ i, R ↔ ii, S ↔ iii |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Compiler Phases | Help-Line |
| Q20➡ | Operating System In which one of the following page replacement algorithms it is possible for the page fault rate to increase even when the number of allocated frames increases? |
| i ➥ FIFO (First In First Out) |
| ii ➥ MRU (Most Recently Used) |
| iii ➥ OPT (Optimal Page Replacement) |
| iv ➥ LRU (Least Recently Used) |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Page Replacement Algorithm | Help-Line |
| Q21➡ | Database Management System B+ Trees are considered BALANCED because |
| i ➥ The number of records in any two leaf nodes differ by at most 1. |
| ii ➥ The number of children of any two non-leaf sibling nodes differ by at most 1. |
| iii ➥ The lengths of the paths from the root to all leaf nodes differ from each other by at most 1. |
| iv ➥ The lengths of the paths from the root to all leaf nodes are all equal. |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | File Structure | Help-Line |
| Q22➡ | Database Management System Suppose a database schedule S involves transactions T1, …, Tn. Construct the precedence graph of S with vertices representing the transactions and edges representing the conflicts. If S is serializable, which one of the following orderings of the vertices of the precedence graph is guaranteed to yield a serial schedule? |
| i ➥ Ascending order of transaction indices |
| ii ➥ Breadth-first order |
| iii ➥ Depth-first order |
| iv ➥ Topological order |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Transaction Managemnt | Help-Line |
| Q23➡ | Computer Network Anarkali digitally signs a message and sends it to Salim. Verification of the signature by Salim requires |
| i ➥ Anarkali’s Public key |
| ii ➥ Salim’s Public key |
| iii ➥ Salim’s Private key |
| iv ➥ Anarkali’s Private key |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Network Security | Help-Line |
| Q24➡ | Computer Network In an Ethernet local area network, which one of the following statements is TRUE? |
| i ➥ The purpose of the jamming signal is to pad the frames that are smaller than the minimum frame size. |
| ii ➥ The purpose of the jamming signal is to pad the frames that are smaller than the minimum frame size. |
| iii ➥ A station continues to transmit the packet even after the collision is detected. |
| iv ➥ The exponential backoff mechanism reduces the probability of collision on retransmissions. |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Ethernet LAN | Help-Line |
| Q25➡ | Computer Network Identify the correct sequence in which the following packets are transmitted on the network by a host when a browser requests a webpage from a remote server, assuming that the host has just been restarted. |
| i ➥ HTTP GET request, DNS query, TCP SYN |
| ii ➥ DNS query, HTTP GET request, TCP SYN |
| iii ➥ DNS query, TCP SYN, HTTP GET request |
| iv ➥ TCP SYN, DNS query, HTTP GET request |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | TCP | Help-Line |
[Q26 – Q55 carry TWO mark each ]
| Q26➡ | Engineering Mathematics A binary relation R on ℕ × ℕ is defined as follows: (a,b)R(c,d) if a≤c or b≤d. Consider the following propositions: • P: R is reflexive • Q: R is transitive Which one of the following statements is TRUE? |
| i ➥ Both P and Q are true. |
| ii ➥ P is true and Q is false. |
| iii ➥ P is false and Q is true. |
| iv ➥ Both P and Q are false. |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Set Theory | Help-Line |
| Q27➡ | Engineering Mathematics Which one of the following well-formed formulae in predicate calculus is NOT valid? |
| i ➥ (∀x p(x) ⇒ ∀x q(x)) ⇒ (∃x ¬p(x) ∨ ∀x q(x)) |
| ii ➥ (∃x p(x) ∨ ∃x q(x)) ⇒ ∃x (p(x) ∨ q(x)) |
| iii ➥ ∃x (p(x) ∧ q(x)) ⇒ (∃x p(x) ∧ ∃x q(x)) |
| iv ➥ ∀x (p(x) ∨ q(x)) ⇒ (∀x p(x) ∨ ∀x q(x)) |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Propositional Logic | Help-Line |
| Q28➡ | Engineering Mathematics Consider a set U of 23 different compounds in a Chemistry lab. There is a subset S of U of 9 compounds, each of which reacts with exactly 3 compounds of U. Consider the following statements: • I. Each compound in U\S reacts with an odd number of compounds. • II. At least one compound in U\S reacts with an odd number of compounds. • III. Each compound in U\S reacts with an even number of compounds. Which one of the above statements is ALWAYS TRUE? |
| i ➥ Only I |
| ii ➥ Only II |
| iii ➥ Only III |
| iv ➥ None |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | TCP | Help-Line |
| Q29➡ | Computer Network The value of the expression 1399(mod 17), in the range 0 to 16, is _________. |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Network Security | Help-Line |
| Q30➡ | Computer Organization Suppose the functions F and G can be computed in 5 and 3 nanoseconds by functional units UF and UG, respectively. Given two instances of UF and two instances of UG, it is required to implement the computation F(G(Xi)) for 1 ≤ i ≤ 10. Ignoring all other delays, the minimum time required to complete this computation is _ nanoseconds. |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | CPU Organization | Help-Line |
| Q31➡ | Computer Organization Consider a processor with 64 registers and an instruction set of size twelve. Each instruction has five distinct fields, namely, opcode, two source register identifiers, one destination register r identifier, and a twelve-bit immediate value. Each instruction must be stored in memory in a byte-aligned fashion. If a program has 100 instructions, the amount of memory (in bytes) consumed by the program text is _________. |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Machine Instruction | Help-Line |
| Q32➡ | Computer Organization The width of the physical address on a machine is 40 bits. The width of the tag field in a 512 KB 8-way set associative cache is ________ bits. |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Cache Memory | Help-Line |
| Q33➡ | Computer Organization Consider a 3 GHz (gigahertz) processor with a three-stage pipeline and stage latencies τ1, τ2, τ3 and such that τ1 = 3τ2/4 = 2τ3. If the longest pipeline stage is split into two pipeline stages of equal latency, the new frequency is ____________ GHz, ignoring delays in the pipeline registers |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Pipelining | Help-Line |
| Q34➡ | Data Structure A complete binary min-heap is made by including each integer in [1, 1023] exactly once. The depth of a node in the heap is the length of the path from the root of the heap to that node. Thus, the root is at depth 0. The maximum depth at which integer 9 can appear is ________. |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Heap Tree | Help-Line |
| Q35➡ | Programming The following function computes XY for positive integers X and Y. 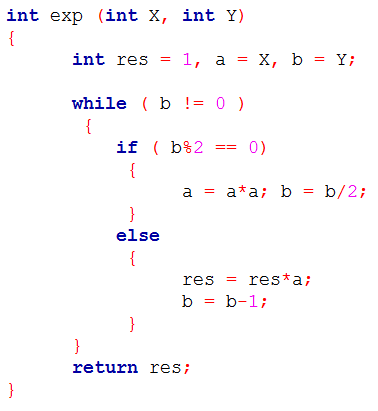 Which one of the following conditions is TRUE before every iteration of the loop? |
| i ➥ XY = ab |
| ii ➥ (res * a)Y = (res * X)b |
| iii ➥ XY = res * ab |
| iv ➥ XY = (res * a)b |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Program | Help-Line |
| Q36➡ | Data Structure Consider the following New-order strategy for traversing a binary tree: • Visit the root; • Visit the right subtree using New-order; • Visit the left subtree using New-order; The New-order traversal of the expression tree corresponding to the reverse polish expression 3 4 * 5 – 2 ˆ 6 7 * 1 + – is given by: |
| i ➥ – 1 6 7 * 2 ˆ 5 – 3 4 * |
| ii ➥ + 1 * 6 7 ˆ 2 – 5 * 3 4 |
| iii ➥ + 1 * 7 6 ˆ 2 – 5 * 4 3 |
| iv ➥ 1 7 6 * + 2 5 4 3 * – ˆ – |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Binary Tree | Help-Line |
| Q37➡ | Programming Consider the following program: 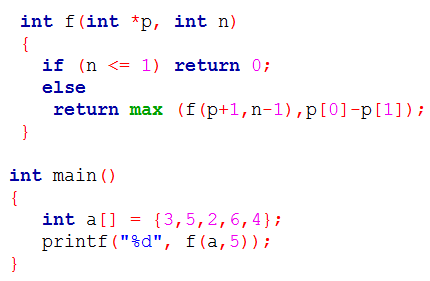 Note: max(x,y) returns the maximum of x and y. The value printed by this program is ________. |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Program | Help-Line |
| Q38➡ | Algorithms Let A1, A2, A3 and A4 be four matrices of dimensions 10 × 5, 5 × 20, 20 × 10, and 10 × 5, respectively. |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Matrix Chain Multiplication | Help-Line |
| Q39➡ | Algorithms The given diagram shows the flowchart for a recursive function A(n). Assume that all statements, except for the recursive calls, have O(1) time complexity. If the worst case time complexity of this function is O(nα), then the least possible value (accurate upto two decimal positions) of α is ______. |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Time Complexity | Help-Line |
| Q40➡ | Data Structure The number of ways in which the numbers 1, 2, 3, 4, 5, 6, 7 can be inserted in an empty binary search tree, such that the resulting tree has height 6, is __________. Note: The height of a tree with a single node is 0. |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Trees | Help-Line |
| Q41➡ | Data Structure In an adjacency list representation of an undirected simple graph G = (V,E), each edge (u,v) has two adjacency list entries: [v] in the adjacency list of u, and [u] in the adjacency list of v. These are called twins of each other. A twin pointer is a pointer from an adjacency list entry to its twin. If |E| = m and |V| = n, and the memory size is not a constraint, what is the time complexity of the most efficient algorithm to set the twin pointer in each entry in each adjacency list? |
| i ➥ Θ(n2) |
| ii ➥ Θ(n+m) |
| iii ➥ Θ(m2) |
| iv ➥ Θ(n4) |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Graph | Help-Line |
| Q42➡ | Theory of Computation Consider the following two statements: I: If all states of an NFA are accepting states then the language accepted by the NFA is Σ*. II: There exists a regular language A such that for all languages B, A∩B is regular. Which one of the following is CORRECT? |
| i ➥ Only I is true |
| ii ➥ Only II is true |
| iii ➥ Both I and II are true |
| iv ➥ Both I and II are false |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Finite Automata and Regular Language | Help-Line |
| Q43➡ | Theory of Computation Consider the following languages: • L1= {an bm cn+m : m,n ≥ 1} • L2= {an bn c2n : n ≥ 1} Which one of the following is TRUE? |
| i ➥ Both L1 and L2 are context-free. |
| ii ➥ L1 is context-free while L2 is not context-free. |
| iii ➥ L2 is context-free while L1 is not context-free. |
| iv ➥ Neither L1 nor L2 is context-free. |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Context Free Language | Help-Line |
| Q44➡ | Theory of Computation Consider the following languages. • L1 = {〈M〉|M takes at least 2016 steps on some input}, • L2 = {〈M〉│M takes at least 2016 steps on all inputs} and • L3 = {〈M〉|M accepts ε}, where for each Turing machine M, 〈M〉 denotes a specific encoding of M. Which one of the following is TRUE? |
| i ➥ L1 is recursive and L2, L3 are not recursive |
| ii ➥ L2 is recursive and L1, L3 are not recursive |
| iii ➥ L1, L2 are recursive and L3 is not recursive |
| iv ➥ L1, L2, L3 are recursive |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Recursive Language | Help-Line |
| Q45➡ | Compiler Design Which one of the following grammars is free from left recursion? |
| i ➥ S → AB A → Aa | b B → c |
| ii ➥ S → Aa | Bb | c A → Bd | ε B → e |
| iii ➥ S → Aa | B A → Bb | Sc | ε B → d |
| iv ➥ S → Aa | Bb | c A → Bd | ε B → Ae | ε |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Left Recursive Grammer | Help-Line |
| Q46➡ | Compiler Design A student wrote two context-free grammars G1 and G2 for generating a single C-like array declaration. The dimension of the array is at least one. For example, int a[10][3]; The grammars use D as the start symbol, and use six terminal symbols int; id[] num. 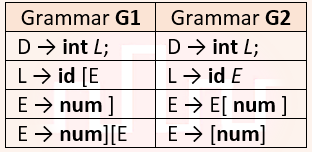 Which of the grammars correctly generate the declaration mentioned above? |
| i ➥ Both G1 and G2 |
| ii ➥ Only G1 |
| iii ➥ Only G2 |
| iv ➥ Neither G1 nor G2 |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Membership Function | Help-Line |
| Q47➡ | Operating Systems Consider the following processes, with the arrival time and the length of the CPU burst given in milliseconds. The scheduling algorithm used is preemptive shortest remaining-time first. Process Arrival Time Burst Time 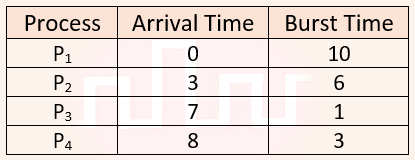 The average turn around time of these processes is _________ milliseconds. |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Process Scheduling | Help-Line |
| Q48➡ | Operating Systems Consider the following two-process synchronization solution.  The shared variable turn is initialized to zero. Which one of the following is TRUE? |
| i ➥ This is a correct two-process synchronization solution. |
| ii ➥ This solution violates mutual exclusion requirement. |
| iii ➥ This solution violates progress requirement. |
| iv ➥ This solution violates bounded wait requirement. |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Process Synchronization | Help-Line |
| Q49➡ | Operating Systems Consider a non-negative counting semaphore S. The operation P(S) decrements S, and V(S) increments S. During an execution, 20 P(S) operations and 12 V(S) operations are issued in some order. The largest initial value of S for which at least one P(S) operation will remain blocked is _________. |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Process Synchronization | Help-Line |
| Q50➡ | Operating Systems A file system uses an in-memory cache to cache disk blocks. The miss rate of the cache is shown in the figure. The latency to read a block from the cache is 1 ms and to read a block from the disk is 10 ms. Assume that the cost of checking whether a block exists in the cache is negligible. Available cache sizes are in multiples of 10 MB. 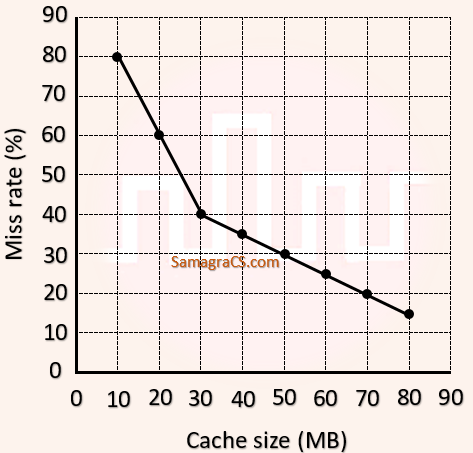 The smallest cache size required to ensure an average read latency of less than 6 ms is ________ MB. |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Cache Memory | Help-Line |
| Q51➡ | Database Management System Consider the following database schedule with two transactions, T1 and T2. • S = r2(X); r1(X); r2(Y); w1(X); r1(Y); w2(X); a1; a2 where ri(Z) denotes a read operation by transaction Ti on a variable Z, wi(Z) denotes a write operation by Ti on a variable Z and ai denotes an abort by transaction Ti. Which one of the following statements about the above schedule is TRUE? |
| i ➥ S is non-recoverable |
| ii ➥ S is recoverable, but has a cascading abort |
| iii ➥ S does not have a cascading abort |
| iv ➥ S is strict |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Transaction Management | Help-Line |
| Q52➡ | Database Management System Consider the following database table named water_schemes : 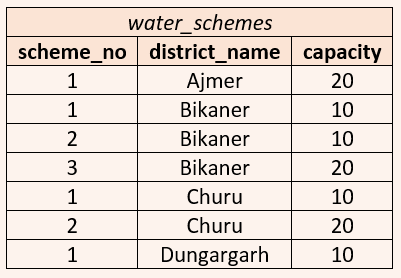 The number of tuples returned by the following SQL query is ___________. 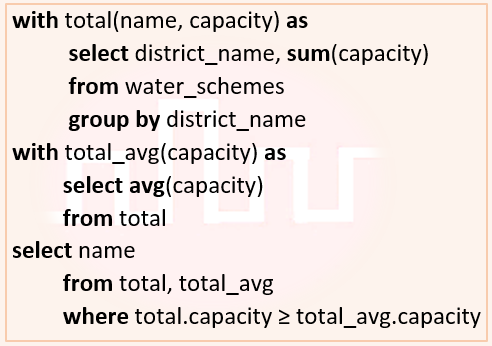 |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | SQL | Help-Line |
| Q53➡ | Computer Network A network has a data transmission bandwidth of 20 × 106 bits per second. It uses CSMA/CD in the MAC layer. The maximum signal propagation time from one node to another node is 40 microseconds. The minimum size of a frame in the network is _______ bytes. |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Access Control | Help-Line |
| Q54➡ | Computer Network For the IEEE 802.11 MAC protocol for wireless communication, which of the following statements is/are TRUE? • I. At least three non-overlapping channels are available for transmissions. • II. The RTS-CTS mechanism is used for collision detection. • III. Unicast frames are ACKed. |
| i ➥ All I, II and III |
| ii ➥ I and III only |
| iii ➥ II and III only |
| iv ➥ II only |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | IEEE 802.11 | Help-Line |
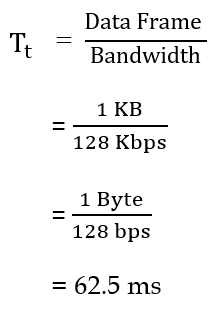
| Q55➡ | Computer Network Consider a 128 × 103 bits/ second satellite communication link with one way propagation delay of 150 milliseconds. Selective retransmission (repeat) protocol is used on this link to send data with a frame size of 1 kilobyte. Neglect the transmission time of acknowledgement. The minimum number of bits required for the sequence number field to achieve 100% utilization is _________. |
Show Answer With Best Explanation
| More Discussion | Explanation On YouTube | Flow Control | Help-Line |